
A few days ago, the Justice Department announced that it had recovered around $2.3 million in Bitcoin that was paid to the extortionists group DarkSide who hit the Colonial Pipeline with a ransomware attack last month. “Today, we turned the tables on DarkSide,” said U.S. Deputy Attorney General Lisa Monaco.
While this appears to be a victory for justice, many questions remain unanswered. But in order to get a better understanding of the events, let’s first examine what happened.
Last month the Colonial Pipeline got hit with a major attack on their IT networks, and the company’s operations were forced to shut down. Colonial Pipeline was instructed to pay a ransom payment of 75 BTC, calculated to be worth around $4.3 million at the time of the attack. The company paid the ransom under great pressure and received the decryption tool to restore its system.
Joseph Blount, CEO of Colonial Pipeline, stated in a Wall Street Journal report that the decryption tool was too slow and ineffective to restore the system. Additionally, he paid the ransom because of the uncertainty of how badly the cyberattack had breached its systems, and consequently, how long it would take to bring the pipeline back.
What is ransomware and who is responsible?
Ransomware is a form of malicious software that encrypts a victim’s files and basically holds their computer or network hostage until the victim pays a fee to regain their access. In order to get the payment, hackers often threaten the victims by stating that they will leak their sensitive information or keep attacking the company’s networks.
The FBI confirmed that the criminal group named “DarkSide”, which allegedly originates from Eastern Europe or Russia, was responsible for the Colonial Pipeline attack.
DarkSide is a platform that sells “Ransomware as a Service” (RAAS). This platform is operated by the developers creating malware, and then the ransomware affiliate is the one who infects companies by using the malware and negotiating the payment with the victim.
DarkSide states that their motivation is to make money, and not create problems for society. Therefore they only target big companies who are able to afford it, and will not target certain industries, including healthcare, education, and the Government Sector.
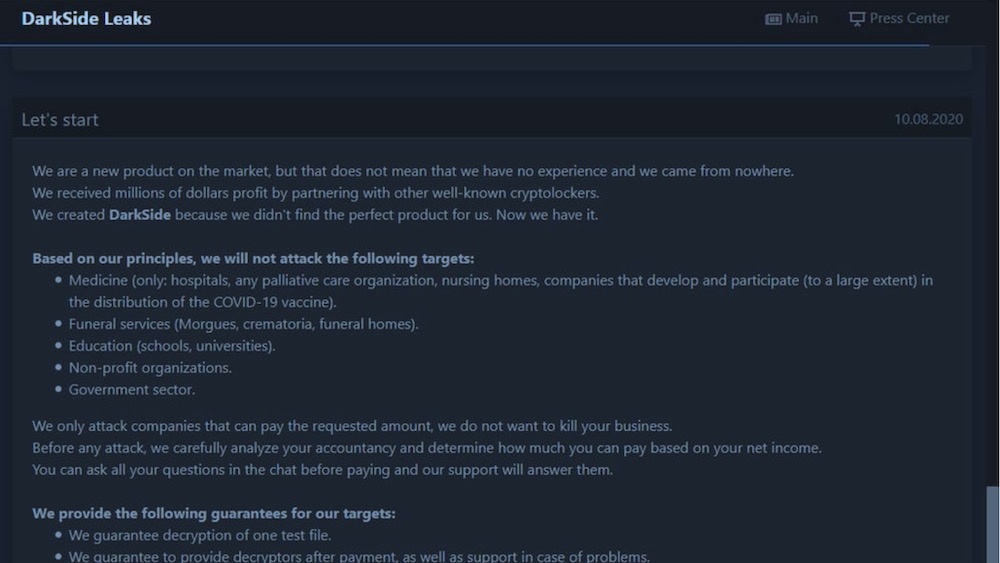
On may 13th, the DarkSide group announced to call it quits and immediately cease all existing operations of the group, after their servers were seized and losing part of their infrastructure by an unknown law enforcement agency.
How did the Justice Department gain access to the cryptocurrency?
“Following the money remains one of the most basic, yet powerful tools we have,” said DOJ Deputy Attorney General Lisa Monaco.
According to the DarkSide affidavit, the investigator followed the money by using blockchain explorer – to eventually figure out the single address that held 63.7 bitcoins from the ransomware payment.
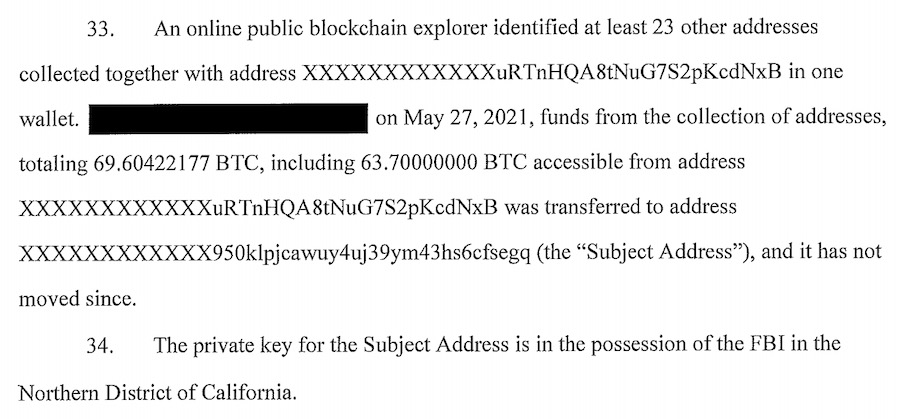
During the press conference on Monday, law enforcements explained that the funds were recovered by a new Digital Task Force. In the official press release, the DOJ stated that “proceeds of the victim’s ransom payment, had been transferred to a specific address, for which the FBI has the ‘private key,’ or the rough equivalent of a password needed to access assets accessible from the specific Bitcoin address.”
However there is one unexplained factor that was of utmost importance for the success behind this operation. How did they obtain the private key?
How did the FBI get DarkSide’s private key?
There are multiple theories about how the private key was obtained by the FBI. However, it seems most likely that the FBI seized the money from the DarkSide affiliate and not the developers.
Experts of the blockchain analytics company Elliptic, came to the conclusion that the address that held the funds was the 85% share of the ransom payment that went to the affiliate of the DarkSide group. The remaining 15% that has not been seized was funneled through addresses controlled by DarkSide developers. According to Elliptic’s co-founder Tom Robinson’s blog post, “Any ransom payment made by a victim is then split between the affiliate and the developer.” In the case of the Colonial Pipeline ransom payment, 85% (63.75 BTC) went to the affiliate and 15% went to the DarkSide developer. According to the warrant there has been a US server seized that could have possibly contained the credentials of the private key stored by the affiliate himself.
According to the warrant here, there was a US server seized that could have possibly contained the credentials of the private key stored by the affiliate. Therefore this appears to be a legal action of physically taking a server, rather than an elaborate “hack” by the US government.

And while there were reports of the FBI obtaining the private key by going through Coinbase’s servers, these claims were invalidated by Coinbase’s chief security officer Philip Martin. He stated on Twitter, “Coinbase was not the target of the warrant and did not receive the ransom or any part of the ransom at any point. We also have no evidence that the funds went through a Coinbase account/wallet.”
Whatever the correct theory is, the attack on Colonial Pipeline has put the Biden Administration under serious pressure to do more about increasing ransomware threats to critical infrastructure and the ability to better respond better to attacks.
“Although the Department has taken significant steps to address cybercrime, it is imperative that we bring the full authorities and resources of the Department to bear to confront the many dimensions and root causes of this threat,” Acting Deputy Attorney General John Carlin wrote to DOJ department heads, US attorneys and the FBI on Tuesday.
Additionally, in the wake of these events, some are claiming that Bitcoin is built on an unsafe network that can be compromised. We find these statements to be false and inaccurate. Nonetheless, there are inherent drawbacks with Bitcoin and privacy, given the permanent record of all transactions in the blockchain, as we noted in our guide on private and anonymous payments.

 Privacy Concerns with Google\’s FLoC (Federated Learning of Cohorts)
Privacy Concerns with Google\’s FLoC (Federated Learning of Cohorts)
Leave a Reply