
Perfect Privacy is a Switzerland-based VPN service that caters to the privacy-focused crowd. As we learned in this Perfect Privacy review, this VPN offers some very robust privacy and security features — but it also comes with a Swiss price tag. We purchased a subscription and tested out this VPN for our in-depth and updated review.
At about $9 per month with a 2-year plan, the big question is whether Perfect Privacy is worth the price — and also how it compares to other leading VPN services. While it earns high marks in the privacy and security category, we found a few drawbacks in our tests.
So let’s start with an overview and then dive into the detailed test results and analysis.
| Website | Perfect-Privacy.com |
| Based in | Switzerland |
| Logs | No logs |
| Price | $8.95/mo. |
| Support | |
| Refund | 7 days |
Perfect Privacy has built a name for itself as a long-standing authority in the VPN market.
It was the first VPN to offer self-configurable multi-hop VPN chains with the OpenVPN protocol. Many VPNs have followed their lead with multi-hop VPNs, as we can also see in our Surfshark vs NordVPN comparison. Then, in 2017, Perfect Privacy released a feature called NeuroRouting, which dynamically routes traffic across multiple hops in the VPN network, corresponding to the location of the site you are visiting (explained more below).
In 2016, Perfect Privacy was one of the first VPNs to offer a customizable filter to block advertisements, trackers, and even malware, phishing, and social media domains. This feature is called the TrackStop filter and it goes beyond most other VPN ad blockers. Once again, various VPNs have followed Perfect Privacy’s lead with this feature as well.
The Perfect Privacy team is on the cutting edge of privacy technology. They have been continuously developing their no-logs VPN service since 2008 and are one of the more established providers in the industry.
Here are the main Pros and Cons we found for this Perfect Privacy review.
+ Pros
- Multi-hop VPN chains, up to 4 servers (self-configurable)
- Zero logs with an unlimited number of connections
- Dedicated bare-metal servers with full IPv6 support
- Obfuscation support (Stealth VPN)
- Customizable firewall and port-forwarding options
- TrackStop filter to block ads, trackers, malware, and more
– Cons
- Expensive
- Does not work well with streaming sites, such as Netflix and Disney Plus
- No iOS VPN app
Perfect Privacy price and refund policy
When you examine the pricing options, it’s clear that Perfect Privacy is on the higher end of the scale. This is definitely not the cheapest VPN you will find.
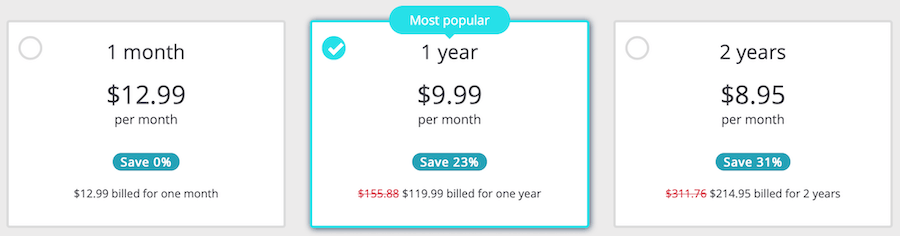
In 2019, Perfect Privacy dropped their prices slightly and began accepting payments in US dollars. The cheapest plan is for the two-year subscription at $8.95 per month. This is indeed more expensive than other top-rated VPN services.
In terms of price, Perfect Privacy does offer some unique advantages over most other VPN providers:
- Unlimited – Your subscription gives you an unlimited number of simultaneous connections and unlimited bandwidth. This is a major benefit of Perfect Privacy – most VPN services limit you to between three and six connections.
- TrackStop – Part of your VPN subscription. It is a customizable screening system that blocks malicious domains, phishing websites, and ads, as well as Google and Facebook domains. It blocks thousands of hazardous domains at the VPN server level. This makes it more secure and efficient than browser additions like uBlock Origin.
- Multi-hop + NeuroRouting – With Perfect Privacy you can create a multi-hop cascade of VPN servers (up to 4), to give you more privacy and security. Additionally, Perfect Privacy offers the NeuroRouting feature. This is a server-side feature that dynamically routes all traffic across numerous hops in the VPN network. NeuroRouting is very similar to the Tor network.
Note: We also covered another VPN with unlimited connections in our Surfshark VPN review. However, unlike Perfect Privacy, Surfshark is really affordable at around $3 per month.
Payment options – You can pay with PayPal and major credit cards, along with Bitcoin and Paymentwall. In previous years, you could send cash in an envelope, but it looks like that option has been discontinued. There are providers that still offer this — check out our OVPN review to learn more.
Refund Policy – Perfect Privacy offers a full 7-day money-back guarantee on all subscriptions. There are no exceptions or hidden clauses with the refund policy, as you can see in the Terms. Most VPNs we have covered offer a larger refund window, such as 30 days. For example, two other VPNs with a 30-day refund window are NordVPN and IPVanish.
Company information and jurisdiction
Unlike all the new VPNs flooding onto the market in the past few years, Perfect Privacy has been offering premium privacy solutions since 2008. It is based in Switzerland and is one of the few VPNs with no logs that has been verified.
According to their website, the parent company is Vectura Datamanagement Limited Company, based in Zug, Switzerland. As we have discussed before, Switzerland is a great privacy-friendly jurisdiction. Privacy is guaranteed under the Swiss Federal Data Protection Act (DPA) and the Swiss Federal Data Protection Ordinance (DPO). This legal framework offers further protection for Perfect Privacy customers and their data.
They also claim the “Technical Implementation” part of the company is based in Panama under the name “Webinvest International SA.” This is also good because Panama is a solid choice for privacy and is not a close partner with any surveillance alliances. Other VPNs also incorporate in Panama due to the privacy-friendly laws, as we covered in the NordVPN review.
This legal/corporate setup, plus a strong zero logs policy, is a solid combination for protecting customer privacy and data.
Supported platforms and VPN apps
The unlimited number of connections, plus support for all different devices and platforms, allows you to use your VPN subscription with everything (no restrictions or limitations).
Perfect Privacy supports all devices and platforms. You can find detailed step-by-step installation guides on their website. With every platform, you will be given different setup options, allowing you the freedom to use the VPN in the best way to suit your needs.
Custom applications – Perfect Privacy offers custom applications for:
- Windows
- Linux (full GUI app, Ubuntu distros)
- Android
- macOS
Full support – In addition to using the custom Perfect Privacy clients (listed above), you can also use Perfect Privacy with third-party clients or natively with many operating systems:
- Windows – OpenVPN GUI, Viscosity, and native IPSec/IKEv2
- Mac OS – Tunnelblick and native IPSec/IKEv2
- Linux – OpenVPN on Linux Terminal
- Android – OpenVPN Connect app and native IPSec/L2TP
- iOS – OpenVPN Connect app and native IPSec/IKEv2
Perfect Privacy VPN Router support
You can also install Perfect Privacy VPN software on your router to protect every device that connects to your network. We’ve tested Perfect Privacy on the Vilfo router. The Vilfo router comes with many VPN services pre-installed, including Perfect Privacy. See the VPN router guide for other options.
Perfect Privacy is ideally suited for use on a router because of the server-side features you can activate (no need for extra software). This provides blanket protection for every device that connects to your router. You can also enable the server-side features on your account which will be applied to the entire network, such as TrackStop and NeuroRouting.
Perfect Privacy feature
Perfect Privacy basically offers two different kinds of features. I will refer to these as server-side features and application features.
Server-side features – Whenever you connect to the VPN network, three main server-side features are enabled: TrackStop (with seven individual filters), NeuroRouting, and port forwarding.
We will cover TrackStop and NeuroRouting in detail below.
Application features – Perfect Privacy also offers many different features and settings that are controlled from within the application. We will discuss these in the Windows, Mac OS, and Android sections further below.
No WireGuard support
The world of virtual private networks (VPNs) is rapidly evolving, and WireGuard is emerging as a top choice. This protocol has the potential to provide users with faster speeds than traditional VPNs, in addition to improved security and encryption.
At this time, Perfect Privacy offers no support for WireGuard. Instead, they are sticking to only using OpenVPN and IPSec. However, in our OpenVPN vs WireGuard speed tests, OpenVPN was much slower. Therefore if speed is a big consideration, you should consider going with a VPN that supports WireGuard.
TrackStop filter
One major advantage of Perfect Privacy is the built-in advertisement, tracking, and malware blocker, which is called TrackStop. Using a VPN with an ad blocker is a smart choice due to the growing dangers of malicious ads and tracking.
Ads can now affect many devices, even if you don’t click anything:
- Tracking – Think of every ad as a digital surveillance camera. These ads are quietly recording your browsing history, keystrokes, and page views, and then sending this data off to third parties. Advertisement domains are building up vast amounts of information on your activities to target you with specific ads based on your profile and history.
- Malware – Online ads, which are usually fed in through third-party domains, are an increasingly common attack vector for delivering malware. For example, malware hidden in the pixels of an image can infect your device in seconds when a website loads (this is even happening to major websites, including the New York Times and BBC).
- Data – Ads are also a huge drain on your data and CPU – slowing down your device and burning up your data. This is especially true since many ads now include video and/or sound.
Many people use browser-based ad blockers, but this is inefficient and often ineffective. Browser extensions can also be a privacy risk since you are relying on the extension to analyze all your browsing data to determine what to block.
Aside from the annoyance and tracking dangers, online ads can also use up a huge amount of bandwidth and processing power from your computer. Blocking ads (and all this other junk) can significantly improve overall performance and also save you money on mobile data.
You can activate the following filters directly in your membership dashboard:
- Tracking and Advertisement filter: block over 30,000 tracking and ad domains
- Fraud filter: block over 45,000 known malware domains and 20,000 phishing domains
- Facebook filter: block Facebook domains and their data trackers
- Google filter: block Google domains (over 400 different domains)
- Social Media filter: block all large social media domains
- Parental filter: block pornographic, gambling, and violent websites and ads that are not suitable for children
- Fake news filter: this filter blocks a list of websites and is published on GitHub (which anyone can contribute to).
TrackStop will protect every device that connects to the VPN – without having to install separate ad-blocking software, add-ons, or browser extensions. It is simple and powerful.
The main drawback with TrackStop is that there’s no whitelist option – but you can easily toggle the different filter settings on/off from the member dashboard.
Perfect Privacy multi-hop VPN
One unique feature of Perfect Privacy is the “multi-hop cascade” option. You can use this feature directly within the VPN Manager app on Windows and Mac OS. This feature allows you to create custom VPN cascades utilizing up to four servers at the same time.
Each consecutive hop re-encrypts your traffic and assigns a new IP address before exiting to the regular internet.
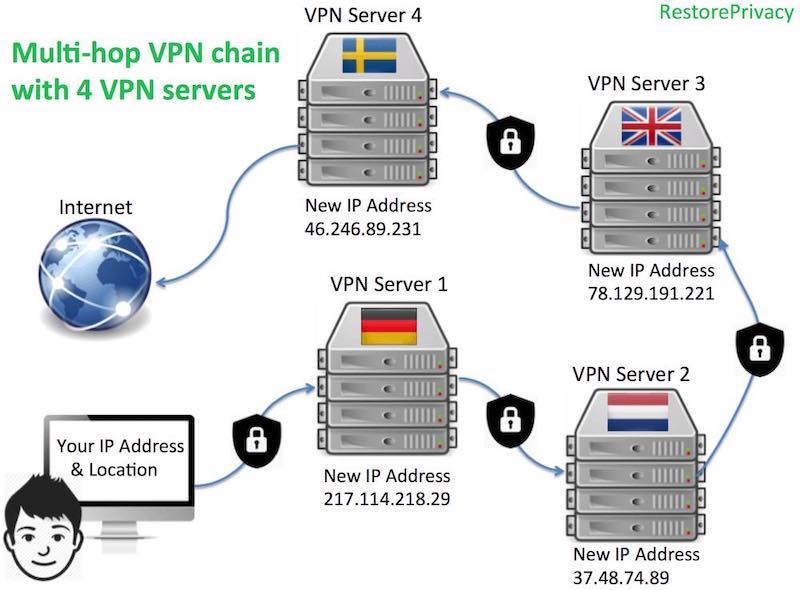
While there are other VPNs that offer multi-hop VPN cascades, these are usually limited to only two servers (double-hop). You can see this, for example, in our ProtonVPN review.
Perfect Privacy is the only VPN we’ve seen that allows you to dynamically create custom VPN cascades directly through the VPN client, adding or removing up to four different servers.
I’ve also found performance can still be quite good when creating a chain of nearby servers (speed tests below).
Why use a multi-hop VPN cascade?
Even if a VPN service doesn’t keep logs and works hard to protect user privacy, VPN servers can still be monitored (logged) for incoming/outgoing traffic by external authorities, third parties, or perhaps even the data center itself. This is explained further in the multi-hop VPN guide.
A VPN cascade gives you multiple layers of encrypted protection against these adversaries.
To enable the multi-hop feature with Perfect Privacy, simply select the cascading option within Settings and then choose how many “hops” you want to have (up to 4).
From there, you can begin selecting the different VPN cascade servers from the main window, one at a time. The order of the cascade will be shown by the numbers on the far left (1-4). You can also modify the encrypted VPN server chain without dropping your connection – simply add or remove servers. Below I am using a VPN cascade with four servers:
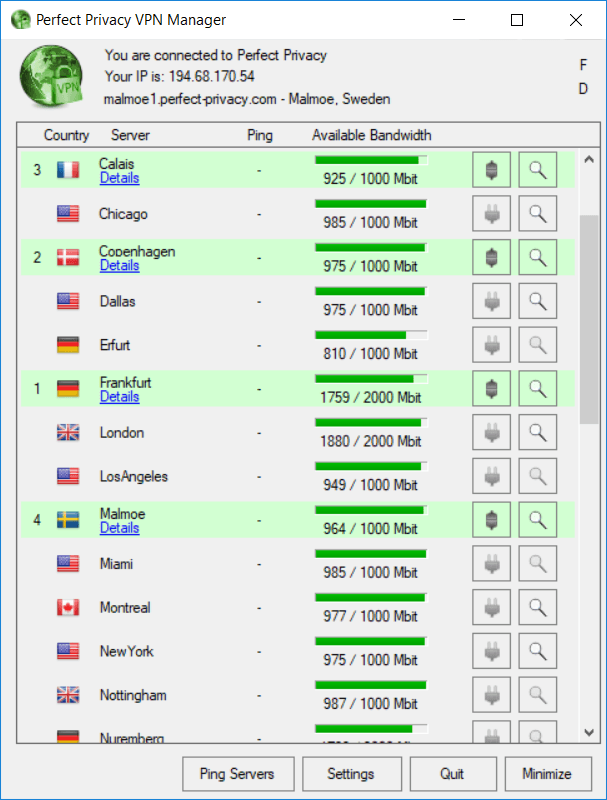
These advanced privacy features are slightly more complex to use, but they offer a very high level of security and online anonymity for those wanting it.
NeuroRouting
What is Perfect Privacy’s NeuroRouting feature?
NeuroRouting is basically a dynamic, simultaneous, server-side, multi-hop VPN configuration. This feature enables you to utilize the entire VPN server network to route all traffic dynamically. Since the concept may seem a bit complex, we’ll break it down more:
- Dynamic – Your internet traffic is dynamically routed across multiple hops in the VPN server network to take the most secure route. The routing path is based on TensorFlow, an open source software for machine learning. Your data remains secured and encrypted in the network as long as possible before exiting onto the regular internet. Being based on TensorFlow, the network continually learns the best and most secure route for a given website/server.
- Simultaneous – Each website/server you access will take a unique path. Accessing multiple different websites will give you numerous, unique multi-hop configurations and different IP addresses at the same time. Each different IP address you broadcast to a website will correspond with the last hop in the server chain for a given URL.
- Server-side – This feature is activated server-side, meaning whenever you access the VPN network, regardless of the device or app you’re using, NeuroRouting will be active (unless you disable it from the member dashboard). This also means it will work on any device – from routers to Mac OS and Android. Finally, NeuroRouting works with OpenVPN (any configuration) as well as IPSec/IKEv2 (a built-in VPN protocol for the Mac OS and Windows operating systems, as well as iOS).
Again, this will work with any device you use with your VPN account.
Perfect Privacy Windows VPN
Although the appearance feels a bit dated, the Perfect Privacy Windows client is powerful and full of features.
To optimize speed and connect to the closest server, you can run a real-time ping test and then rank order the servers by the fastest ping. Ping is important if you need a good VPN for gaming. Real-time bandwidth for every server is also displayed right in the application.
Here is a screenshot of the Windows client where I’m connected to the Basel, Switzerland server:
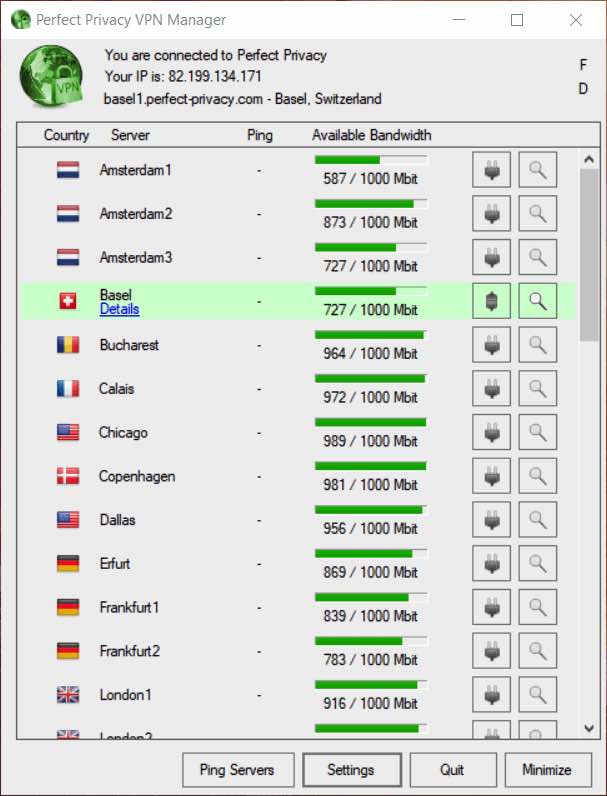
Note: As you can see in the screenshot above, there is a lot of available bandwidth. (You can see the real-time bandwidth available on Perfect Privacy servers here.)
From the Settings tab, you can also configure different startup options and features. You can configure the client to start with Windows and connect to a designated server.
VPN kill switch
The Perfect Privacy Windows client offers advanced leak protection features (also known as a VPN kill switch). In the image below, you can see that the Windows client gives you three levels for both the firewall and DNS leak protection:
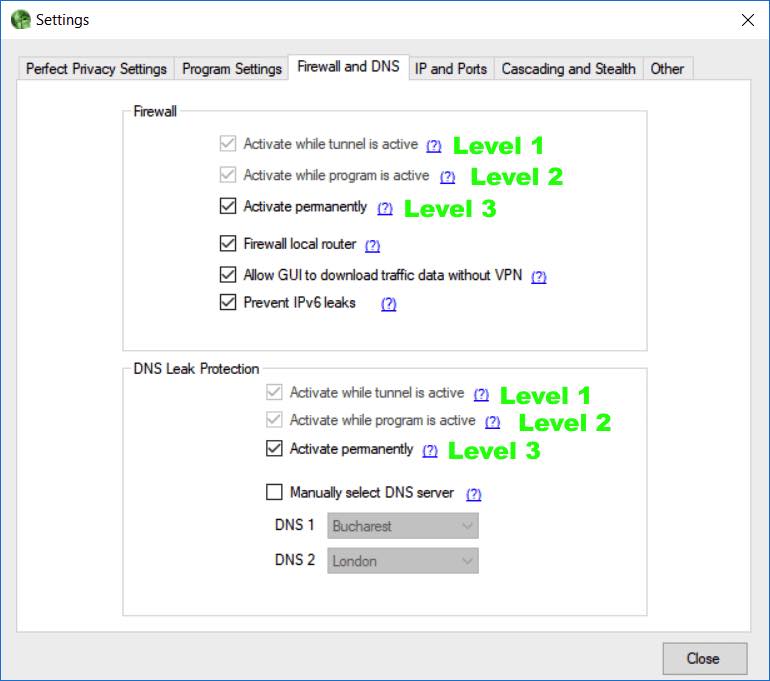
Most VPNs offer a level 1 or level 2 kill switch. Perfect Privacy gives you the highest protection with a level 3 kill switch, which will block all non-VPN traffic whether the VPN is active or not. In essence, the software makes a change to the Windows firewall, to only allow traffic through the VPN.
I tested the kill switch extensively with the Windows client and it did block all regular (non-VPN) traffic, even when the VPN client was closed.
Stealth VPN (obfuscation)
Perfect Privacy has added a powerful lineup of obfuscation features, which they refer to as Stealth VPN.
Obfuscation conceals your VPN traffic, which is necessary with restricted networks or any location that does not allow (or discourages) VPN use. This is a must-have feature if you need a VPN for China or with various work or school networks that do not allow VPNs.
Stealth VPN masks packets to look like normal HTTPS traffic, thereby concealing your use of a VPN while also defeating restrictions and deep packet inspection (DPI).
Perfect Privacy macOS VPN app tests
There are basically three different options for using Perfect Privacy with Mac OS:
- IPSec/IKEv2 – This is the native (built-in) Mac OS VPN configuration that offers a simple, stable, leak-proof setup.
- Third-party VPN clients – These include Tunnelblick and Viscosity. The main drawback with third-party clients is that they do not offer any kill switch.
- Mac OS client – The Mac OS VPN client has been released and it performed well in testing. It offers all client features, including multi-hop functionality, obfuscation, and advanced leak protection settings.
IPSec/IKEv2 – The first option using the IPSec/IKEv2 encryption cipher is a good, simple setup. The advantage of this option is that it integrates the VPN directly with the Mac OS firewall. When you enable the “connect on demand” setting, you get a 100% leak-proof, always-on VPN. All apps will be forced through the VPN, and if the VPN connection drops, nothing will get through the Mac OS firewall.
You can get step-by-step installation instructions here. While IKEv2 is not quite as strong of an encryption cipher as OpenVPN, it is still secure, fast, lightweight (less CPU-intensive than OpenVPN), and can be used natively (no apps required).
Third-party clients – Two popular third-party clients for Mac OS users are Tunnelblick (free) and Viscosity (one-time $9 license fee). Both of these clients work with the OpenVPN protocol, rather than the IKEv2 option above.
The main drawback of using third-party OpenVPN clients is that they don’t always have a kill switch. This creates a data leak risk whenever you interrupt the VPN connection, such as with switching servers or your system going to sleep/waking up. However, you can create a kill switch with firewall rules or a third-party firewall/traffic monitor, such as Little Snitch.
macOS VPN app – You can also try the Perfect Privacy Mac OS client, which was released and supports all features, including multi-hop cascades, obfuscation, and advanced leak protection.
This is a good all-around VPN service for macOS users that is very secure.
Perfect Privacy Android app
There are three different ways to use Perfect Privacy with Android devices:
- Built-in IPSec VPN configuration (an always-on, leak-proof setup that establishes a VPN connection whenever you have internet connectivity)
- Third-party OpenVPN apps
- Perfect Privacy Android client (based on the Strongswan VPN client)
I tested out the Perfect Privacy Android client for this review. It performed well, did not have any leaks, and was very easy to set up and use.
Below is a screenshot of our tests with the Perfect Privacy Android VPN app:
Note: While the Android client works well, those who want an always-on VPN configuration (level three kill switch) could instead use the built-in IPSec Android configuration (no app).
If you want an Android VPN with more features and options for protocol selection, check out our guide on the best VPN for Android.
Perfect Privacy Linux tests
Perfect Privacy has a nice Linux GUI client that works with Ubuntu. I tested it out on Ubuntu and it worked well.
The Perfect Privacy Linux client does not offer all the features you get with the Windows and Mac OS clients, such as multi-hop functionality and built-in obfuscation features. Nonetheless, their website states:
Please note that the VPN Manager for Linux is still under development and more features will be available in the future.
If you want a cascaded (multi-hop) connection, there are detailed instructions for how to do this in the member’s area. The same goes for setting up obfuscation on Linux.
The Linux client does offer startup options and it also shows real-time bandwidth stats. Overall it’s a great option for anyone wanting a GUI Linux client, although it’s limited to Ubuntu distributions. See other Linux VPNs here.
Perfect Privacy servers
When you examine the Perfect Privacy server page, you can see that the network is smaller than other leading VPNs. Currently, Perfect Privacy offers servers in 26 different countries.
Server Quality – Perfect Privacy uses only dedicated (bare-metal) servers, instead of virtual servers that are often logged by the data center (server host). Many VPN services maintain huge networks of virtual servers (VPS), which is much cheaper than using dedicated, physical servers.
We’ve examined and compared many VPNs with large server networks. See for example our ExpressVPN vs NordVPN comparison, where each VPN has a large global network.
Another important consideration for server speed and reliability is the user-per-server ratio. You can see that real-time bandwidth with Perfect Privacy is good, even at peak traffic times.
To provide additional protections for customer privacy, all of Perfect Privacy’s servers run in a continuous RAM disk mode. This is an additional security measure that protects customer data if anything were to ever happen to the servers. (We also see this with Surfshark and ExpressVPN.)
If the power goes, all data is gone. Additionally, running VPN servers on RAM (rather than hard drives) makes it impossible to store any data on the server (a true no-logs policy). This was very important when their servers were seized in the Netherlands – but no customer data was affected.
Perfect Privacy is also one of the few VPN services on the market today that offers full IPv6 support on their network.
Advantages of the Perfect Privacy server network:
- High bandwidth/speed (Gigabit channels)
- Full IPv6 support (you get both an IPv4 and IPv6 address)
- Excellent users-per-server ratio
- Good server selection in 26countries
- All Perfect Privacy’s servers operating in RAM disk mode (absolutely no saved data or logs)
- Network consists entirely of dedicated bare-metal servers (no virtual servers)
- Highest level of network security
You can read more about the server network here.
Perfect Privacy Speed
For this review, I tested out Perfect Privacy speeds on a 160 Mbps connection using the Linux GUI client with 256-bit OpenVPN. (My physical testing location was in Europe.) Overall the speeds were good with the servers I tested.
Here’s a nearby server in Denmark: 141 Mbps
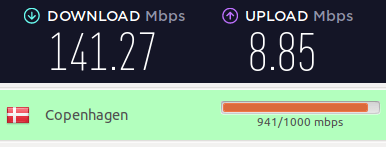
And a server in Sweden: 125 Mbps
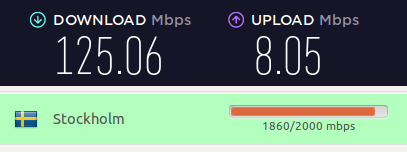
And a server in London, UK: 133 Mbps
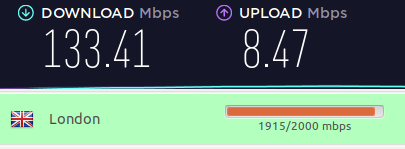
These are good speeds if you need fast UK VPN servers. In addition to nearby servers in Europe, I also tested a handful of VPN servers in the US and Canada.
Here’s a Perfect Privacy VPN server in Miami: 131 Mbps
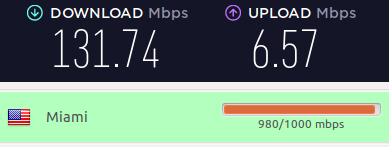
And a VPN server in New York: 117 Mbps
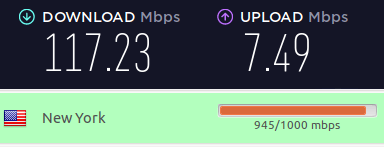
Overall speeds with Perfect Privacy were very good on all the VPN servers I tested.
Speeds with NeuroRouting or Multi-hop
If you are using the NeuroRouting or Multi-Hop features, you should expect some tradeoffs with speeds. Because you are adding latency and extra encrypted hops to your connection, the speeds will be slower than if you are using a nearby single VPN server.
Therefore if download speed is your top priority (torrenting), then you should not use NeuroRouting or the multi-hop features.
Zero logs, zero restrictions
When it comes to customer privacy and logs, Perfect Privacy is tough to beat.
They keep absolutely no logs and do not enforce any restrictions on bandwidth or the number of connections. They clearly state their logging policy on their website:
No logging of any user specific data or activity. No data is kept. We do not monitor, review, log or store your communication/connection data.
On none of our servers are any logs which would enable a de-anonymization.
On the ‘no logs’ page, Perfect Privacy further clarifies:
Perfect Privacy built its infrastructure on this philosophy: All our services are running within strongly encrypted RAM disks so that it is technically impossible for data to be stored on hard drives. That also means that no data can be recovered if the power is disconnected.
Nobody can force us to log your data. If that were the case, we would rather discontinue Perfect Privacy than to record your data and compromise your privacy.
Additionally, Perfect Privacy’s no logs policies were verified in a real-world case when their VPN servers were seized in Rotterdam. As they explained here, no customer data was affected or compromised (due to no logs and secure RAM disk server implementation).
Privacy and security test results
I ran the Perfect Privacy VPN clients through a number of VPN tests and checks to examine:
- IP address leaks (both IPv4 and IPv6)
- DNS leaks
- Kill switch protection
- Features (do the privacy and security features work as advertised)
Here are the test results with the VPN Manager app on Windows 10. Notice IPv4, IPv6, and DNS addresses are all being supplied by the VPN server (no third parties). No leaks:
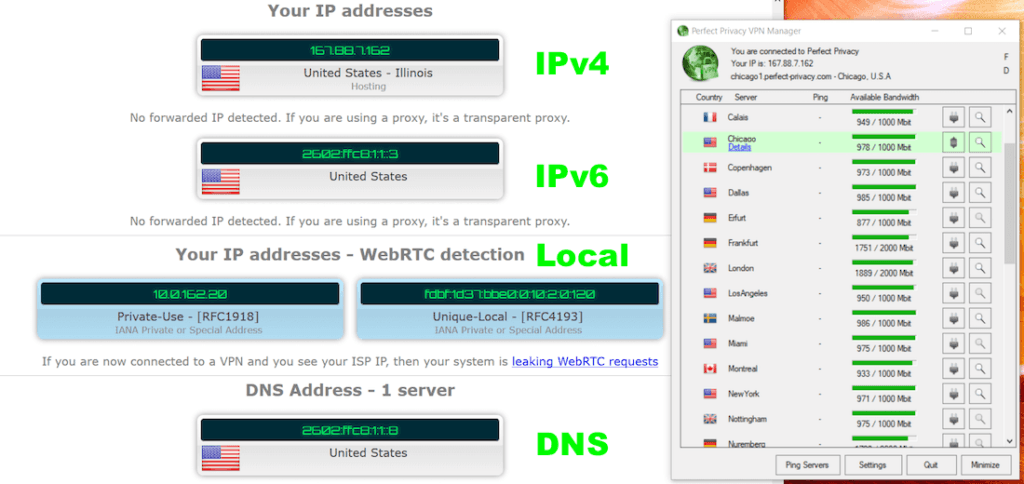
Tests with the Perfect Privacy VPN Manager client on Mac OS also did not reveal any leaks or problems.
The Linux client currently does not block traffic via the firewall when the connection is not active, although it does install with a package to protect against DNS leaks. If you want to be 100% sure there are no leaks on Linux, Perfect Privacy recommends using firewall rules, and they have a detailed instruction guide for that.
Perfect Privacy also has a warrant canary on its website – see here. This page keeps people updated on any government actions that may affect user privacy, such as warrants, court orders, gag orders, or other law enforcement actions.
Most VPNs do not provide this information, as doing so would be illegal in the United States and many other countries. Here is further clarification from their website:
Note that Perfect Privacy is based in Switzerland we are not subject to US-based laws. Furthermore all Perfect Privacy employees are located in countries where there are no laws that would prevent us from disclosing any kind of incident with full transparency. This warrant canary is purely in the interest of transparency and accountability.
This is another reason why jurisdiction is important when choosing a VPN service.
VPN support
Perfect Privacy offers different channels for support, namely email and also through their forum.
One drawback with Perfect Privacy support is that there is no live chat option. However, in my experience, I’ve found email support to be fast and professional.
There is also a user forum, which you can access from their website. The most active part of the forum is in German.
Tip: If you have an issue, I would recommend emailing the support department directly rather than posting a question in the forums (for a faster response).
Is Perfect Privacy VPN worth the high price?
Perfect Privacy is geared mostly toward those who are seeking a high level of security and online anonymity.
Given all the advancements in surveillance technology over the years, many people are looking for more advanced privacy solutions, above and beyond a basic VPN provider. Perfect Privacy delivers in the areas of advanced security and anonymity with multi-hop VPN chains, NeuroRouting, TrackStop, and obfuscation features.
That being said, it may not be the best choice for everyone.
Some people want a basic VPN for streaming Netflix and other services. (See the best VPNs for Netflix guide for other options.)
If cost is your primary concern, you can find cheaper solutions as well, especially with these VPN coupons.
There’s no getting around the fact that Perfect Privacy is an expensive VPN service (and they don’t offer any discounts). Nonetheless, Perfect Privacy offers the following justification for their above-average prices on their FAQ page:
Perfect Privacy understands itself as a premium VPN provider and in particular, provides the following core features:
- All services are running on dedicated root-servers
- Servers with up to 1000Mbps bandwidth
- Protocols: OpenVPN, IPsec, PPTP, SSH2, HTTP- and SOCKS5-proxies on all VPN servers
- 50+ servers distributed worldwide
- No bandwidth limitations
- Cascading possible / Multi-Hop VPN
- Full support included
- Unlimited connections
- Comfortable user interfaces/clients for many operating systems
- Additional advanced features: TrackStop, NeuroRouting, Stealth VPN
When taking these points into consideration, it will get hard to find a comparably extensive VPN offer for a lower price.
Perfect Privacy Review FAQ – Frequently Asked Questions about the Perfect Privacy VPN
Here are several important questions about the Perfect Privacy VPN–along with the answers.
Where is Perfect Privacy based?
The Perfect Privacy VPN is based in Switzerland. This is one of the better locations for a VPN. And it is a far better location for a VPN than the United States.
Who owns Perfect Privacy VPN?
The parent company or the Perfect Privacy VPN is Vectura Datamanagement Limited Company, based in Zug, Switzerland. The Technical Implementation (Engineering) part of the company is Webinvest International SA, which is based in Panama.
How secure is Perfect Privacy VPN?
Perfect Privacy is one of the top VPN services when it comes to security (privacy too). The basic system is solid, with a kill switch built in and no leaks. Add in advanced server-side features like TrackStop and NeuroRouting and Perfect Privacy is one of the most secure VPNs available today.
Does Perfect Privacy work in China?
While we haven’t been able to test this ourselves, Perfect Privacy’s Stealth VPN feature should work in China.
How is Perfect Privacy’s Customer Service?
We have not had any trouble with Perfect Privacy’s Customer Service. However, since we first reviewed Perfect Privacy, users have posted a number of complaints about Perfect Privacy Customer Service.
We recommend you read the comments below and decide for yourself how these complaints affect your opinion about Perfect Privacy.
Perfect Privacy review conclusion
After testing numerous VPN services over the past few years, Perfect Privacy remains the top VPN for privacy and security. Since I first tried their service in 2016, I have been personally using it every day with computers and mobile devices. The server-side features of TrackStop and NeuroRouting provide maximum protection for all devices – whether you’re using an Android mobile with the IPSec/L2TP configuration, Mac OS with IKEv2, Windows, or Linux.
Over the last few years, I’ve tested many VPNs. Perfect Privacy is still a leader for privacy and security. I’ve used it daily on my computers and phones since 2016. The TrackStop and NeuroRouting functions offer maximum protection for all gadgets, including those running Android with IPSec/L2TP setup, Windows, Linux, and Mac OS with IKEv2.
While the NeuroRouting feature showed that Perfect Privacy was on the cutting edge of privacy and security technology, but there has been little improvement in the service over the last year. With mass surveillance and tracking technologies continuing to advance throughout the world, it’s important to use a VPN that evolves and remains at the forefront of these developments. While this was once a strength of Perfect Privacy, you may now want to consider alternatives that have not stagnated.
All subscription plans come with a 7-day money-back guarantee.
Alternatives to Perfect Privacy
Click the VPN name below to read our full review – or grab the discount for the best savings. All three of these VPNs have a 30-day money-back guarantee.
You can also check out our review of the Best VPN Services for other recommendations.
If you have used Perfect Privacy, feel free to share your honest review (good or bad) below.
This Perfect Privacy VPN review was last updated on January 12, 2024.

I tried perfect privacy in China on the airport and I was able to access anything I can access in europe. So yes perfect privacy works in China. Tested it with my Iphone.
Hello, after a few years of using PerfectPrivacy with great satisfaction, it has now become almost unusable on recent Debian(based) Linux distributions for me (and before that already required openvpn configuration and activation over the command line). From the forums, it seems that there is not much motivation to update the Linux interface. I had paid a 2 year plan, but I have asked for reimbursment. It works very well on Linux Mint 20 (not 21) with its GUI (if one does not want streaming, e.g. access to UK channels like the BBC or My5 from abroad).
Why were the old comments removed? weird and suggestive. regarding this vpn, as a result, despite all the minuses and the angry review that was deleted, I continue to use this vpn. moreover, again paid several years in advance. I didn’t find an alternative for myself, or rather I couldn’t replace this vpn. the rest were less suitable.
Comments that were years old (2+) got purged across the site because things change fast in this space and old comments are generally not relevant to the here and now.
Hi Sven,
Appreciate your review on PP, could you please do an update on it.
Now PP has moved to Germany, so wanted your thought on it.
Also the Windows Client has changed as well, its now a cumbersome monstrosity of a client.
Thanks in advance.
Yep, will do.
Perfect Privacy is horrible. I could not connect to the internet at all. I asked for a refund, and they don’t answer. You all should check out the bad reviews on trust pilot.
Now PP is based in Germany.
Hello Mr. Sven Taylor, I have read your other news, but I wonder about all countries, including the EU, and the so-called “Swiss privacy”. The reason is that in my country some “politicians” on TV or in elections have been arrested or exposed for putting money in Swiss banks.
Or some of the criminal members do crack, piracy, bad things, also arrested in Switzerland. Can you tell us why you chose Switzerland? Not countries like China, Russia, Iceland. I doubt the privacy of Switzerland.
Respond politely again. Mr. Sven Taylor, would you please answer, if you use more than one VPN company to provide multi-hop service (connect two VPNS at the same time), what is the specific use? . I’m assuming it’s a simplified version of Tor with only two servers. But both servers are run by a VPN company.
So if the second VPN receives court and police letters, does it make no sense to have more than two VPNS? Because it is the same company, as long as contact one can directly break the front vpn defense
I saw some reviews of PP that said the Windows app was buggy. That was my experience, as well. With PP open, I tried to download Nord VPN, and my PC crashed. This was at a coffee shop Wifi, in case that makes a difference. I ended up having to Restore the PC that night.
The neuroring thing seems interesting, but how does it determine which route is the ‘safest’? If its all internalised within the PP network then isn’t it all equally secure? I understand it learning the fastest route like tor does but the safety judgement is confusing. Its a shame they don’t accept cash payments also