
A VPN is a must-have tool for UK residents and also UK expats abroad. Not only will it help you to stay safe, private, and secure online, a VPN will unblock websites and content that may be restricted. But here’s the problem: choosing the best VPN for the UK amongst a vast ocean of mediocre VPNs is challenging.
But not to worry, we did the work for you and tested all of the most popular VPN providers. This guide highlights the best UK VPN services, while also showing you a few bad apples to avoid.
Top VPNs for the UK
- NordVPN – Best VPN for the UK, excellent for streaming UK TV, with fast speeds, reliable and secure apps, plus extra privacy features (with a 69% off coupon)
- Surfshark – A budget VPN that works great for UK streaming
- ExpressVPN – A reliable VPN for the UK with user-friendly apps
Why you need a VPN for the UK
So why are so many UK residents and expats looking to find the best UK VPN? Here are a few reasons:
- Privacy – Internet providers in the UK are forced to record the browsing activity of their customers and provide this to government agencies on demand under the Investigatory Powers Act. A VPN encrypts and anonymizes your activity so your internet provider can’t see anything you’re doing online.
- Streaming British TV and unblocking websites – Many websites are blocked in the UK. A VPN changes your IP address and virtual location to get around these blocks. UK expats who want access to BBC iPlayer, Netflix, and other UK media
- Security – Anyone who wants more security when connecting to public WiFi hotspots or questionable networks should use a VPN.
- UK IP address – UK expats living abroad will need a UK IP address to stream UK-specific media, such as BBC iPlayer. A VPN is the solution for this.
We’ll examine each of these trends more carefully below – but first let’s examine the best UK VPNs.
How we rank the top UK VPNs
This guide ranks the best VPNs for the UK based on the following criteria:
- Located in a good privacy jurisdiction to keep user data safe
- Passed all tests with no leaks found (no IP address leaks or DNS leaks)
- Good performance throughout the server network (fast speeds and good reliability)
- High-quality VPN apps with all features working correctly
- Supports secure VPN protocols with strong encryption standards
- Offers a money-back guarantee
- Trustworthy and well-established VPN provider with a good track record
Here are the best VPNs for the UK:
NordVPN – Best VPN for UK in 2023
| VPN | NordVPN |
| Based in | Panama |
| Logs | No logs (audited) |
| Price | $3.09/mo. |
| Support | 24/7 live chat |
| Refund | 30 days |
| Website | NordVPN.com |
NordVPN tops the list as the best VPN for the UK. It is based in Panama (a great privacy jurisdiction) and is a verified no logs VPN provider with a good track record. It performed well for the NordVPN review without any leaks or problems identified.
NordVPN is one of the fastest VPNs we have tested. It now supports the WireGuard VPN protocol, which is much faster than other VPN protocols. With excellent speeds and strong security, NordVPN is currently the best VPN for torrenting. Below is a recent speed test with NordVPN where we hit 445 Mbps:
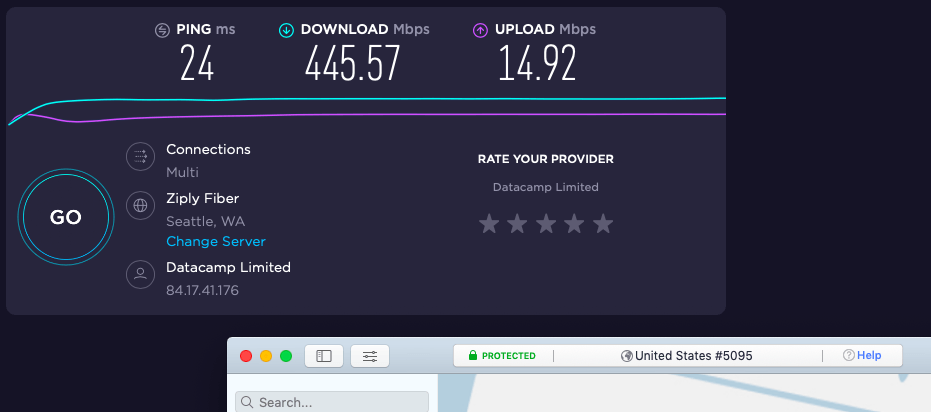
The fast server network and WireGuard support give NordVPN a serious performance advantage over other VPNs. You can see this for example in the IPVanish vs NordVPN comparison. Even when going head-to-head against other VPNs with WireGuard, NordVPN still comes out on top. You can see this in our CyberGhost vs NordVPN report.
Another factor that separates NordVPN from other services is the server network. It has 5,500 servers in 60 countries. Every server runs in RAM-disk mode (without hard drives) making it impossible for data to be stored on any server. NordVPN is rolling out high-speed colocated (self-owned) servers and replacing all rental servers. These colocated servers will run on 10 Gbps bandwidth channels for even faster speeds.
NordVPN has also passed third-party audits. First, they passed an independent security audit conducted by Versprite, which examined all apps and VPN infrastructure. Additionally, they have passed two separate no-logs audits conducted by PWC AG, making NordVPN one of only a few verified no-logs VPN providers.
NordVPN’s offers a great lineup of VPN apps for all major operating systems and devices. This includes Windows, Mac OS, Linux, Android, and iOS mobile devices, as well as browser extensions. If you need a VPN for Firestick, NordVPN has a dedicated VPN app in the Amazon App Store. Below is the NordVPN Windows VPN app we tested:
And for those UK residents that want features for maximum privacy and security, look no further. NordVPN offers these features:
- CyberSec feature to block ads, tracking, and malware domains
- Double-VPN servers that encrypt traffic over two different locations
- Tor-over-VPN servers that encrypt traffic with both the VPN server and the Tor network
- Obfuscated servers that will conceal your VPN traffic as regular HTTPS encryption (a useful feature if you need a VPN for China)
- Split tunneling feature that allows you to route certain apps or websites outside the VPN
> (opens in a new tab)”>See all NordVPN features here >>
And maybe you are a UK expat and want to watch UK Netflix? NordVPN supports a huge selection of Netflix libraries, including the UK, US, Canada, Australia, and many more. It is also one of the few VPNs that work with BBC iPlayer on a consistent basis. Below I’m streaming an episode of MasterChef from the BBC iPlayer through a NordVPN server in the UK:
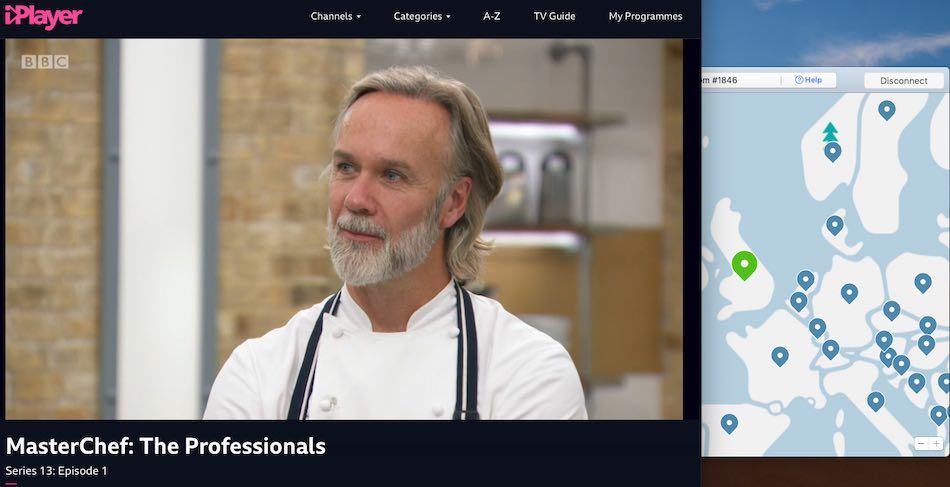
If you want to give this VPN a test drive, you will have a 30-day money-back guarantee on all subscription plans. You will also get 24/7 live chat support to help you if any issues come up, in addition to numerous guides and video tutorials on their website. Lastly, check out the coupon below for the best savings.
NordVPN UK server locations
- London
- Manchester
Overall, NordVPN stands out as the best UK VPN in our opinion. Here are the pros and cons of this service:
+ Pros
- User-friendly and reliable apps
- Double-VPN and Tor-over-VPN servers
- Passed numerous 3rd-party audits
- Strong encryption standards with full support for WireGuard
- Works with Netflix and many streaming sites
- Threat Protection feature to block ads, trackers, and malware
- Professional 24/7 live chat support
- Consistently fast speeds
- Dedicated RAM-servers with 10 Gbps bandwidth channels
– Cons
- Big discounts only available with 2-year plans
NordVPN’s Cyber Deal is live:
Get 69% Off NordVPN two-year subscriptions plus 3 months extra:
(Coupon is applied automatically; 30 day money-back guarantee.)
See the updated NordVPN review for test results and analysis.
Surfshark – A low-cost, fully-featured VPN for the UK
| Website | Surfshark.com |
| Based in | The Netherlands |
| Logs | No logs (audited) |
| Price | $2.29/mo. |
| Support | 24/7 live chat |
| Refund | 30 days |
| Deal | 85% Off Coupon |
Surfshark is another great VPN for the UK that is really getting some attention. It is a no-logs VPN based in the British Virgin Islands that also gives users an unlimited number of connections. And of all the options in this guide, it is one of the cheapest VPNs available at only $3.09 per month with the discount below.
Surfshark VPN uses strong encryption with an AES-256 cipher for the OpenVPN and IKEv2 VPN protocols. Like NordVPN, Surfshark also supports the WireGuard VPN protocol. It has a VPN ad blocker option called CleanWeb, along with a lineup of double VPN servers. Additionally, it has a split tunneling feature that allows you to route certain applications or websites outside of the VPN tunnel.
Surfshark also does well in the streaming category. Like the other UK VPNs we’ve discussed, Surfshark works well with UK Netflix and officially supports 15 other global Netflix regions. It is a good option if you need a VPN for Kodi streaming and they do not limit or restrict torrenting in any way. Below I’m streaming UK Netflix through a Surfshark server in London:
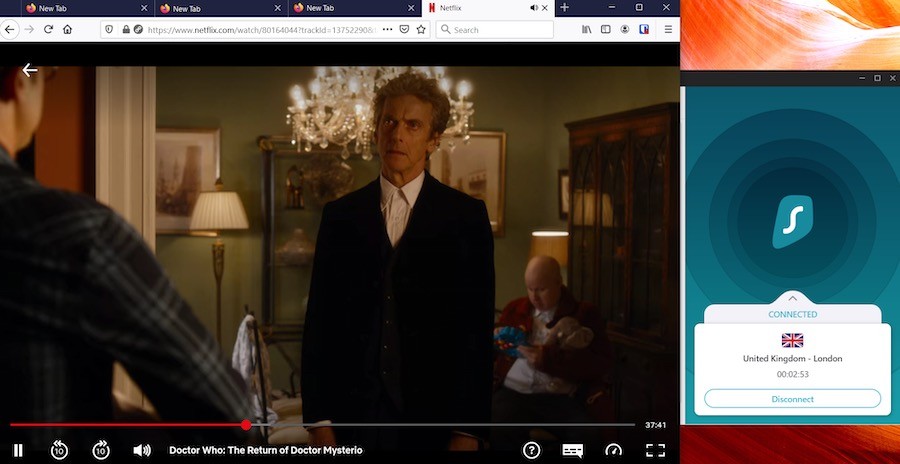
Surfshark comes with a large selection of applications for all types of devices. Aside from desktop and mobile operating systems, Surfshark also supports Smart TVs, gaming systems, and VPN routers (like NordVPN).
While Surfshark does offer good speeds with the WireGuard VPN protocol, it’s not quite on the level of NordVPN, as you can see in the NordVPN vs Surfshark comparison. With that being said, we could still hit speeds of 397 Mbps using nearby Surfshark servers with the WireGuard VPN protocol.
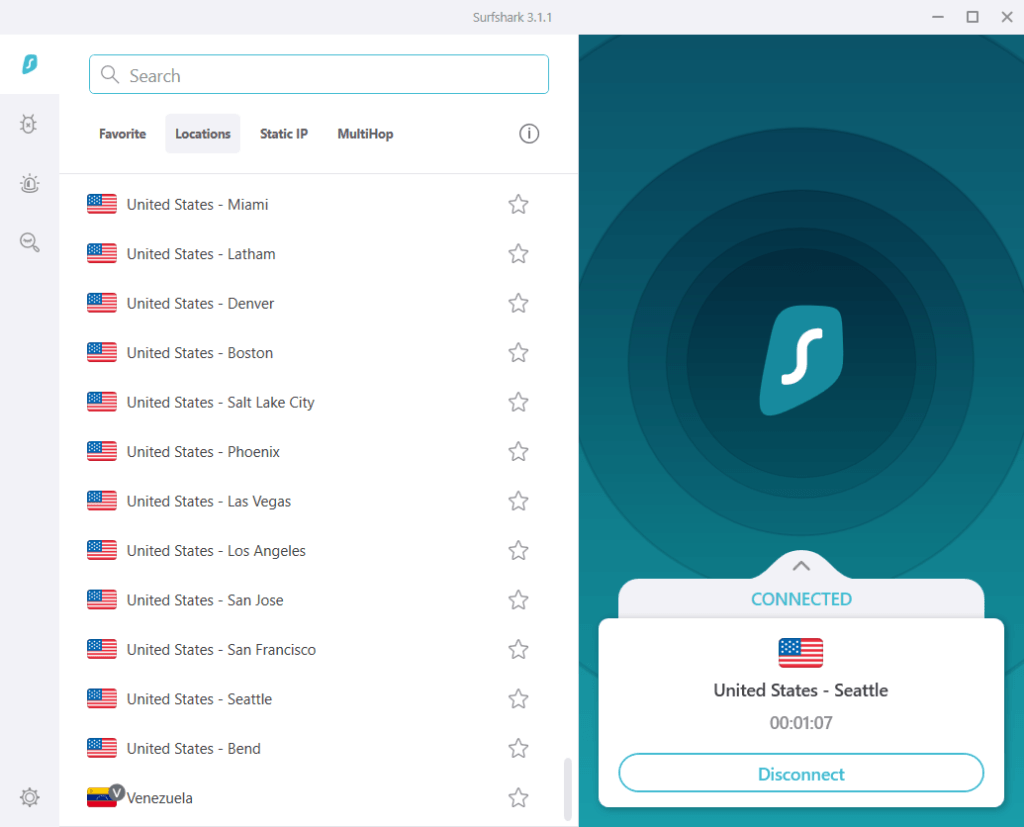
Whether you need a VPN for privacy, security, streaming, or anything else, Surfshark will probably fit the bill — and there will be money left over.
Surfshark UK server locations
- London
- Manchester
- Glasgow
Here are the pros and cons we found with Surfshark VPN:
+ Pros
- Unlimited connections
- User-friendly apps for all devices and operating systems
- CleanWeb feature to block ads, trackers, and malware
- Works great with Netflix and many other streaming services
- 24/7 live chat support
- Strong encryption and security features (audited)
– Cons
- Limited support for VPN routers
- Above average monthly prices
Surfshark VPN Coupon:
Get 85% off Surfshark VPN plus an additional 2 months FREE with the coupon below:
(Coupon is applied automatically; 30 day money-back guarantee)
Our new Surfshark VPN review has more info and test results.
ExpressVPN – A user-friendly UK VPN service
| Website | ExpressVPN.com |
| Based in | British Virgin Islands |
| Logs | No logs (audited) |
| Price | $6.67/mo. |
| Support | 24/7 live chat |
| Refund | 30 days |
| Deal | 49% Off Coupon |

Rounding out our list of the best VPN services for the UK, we have in third place ExpressVPN. Like Surfshark, ExpressVPN is based in the British Virgin Islands with a strong focus on privacy and security. ExpressVPN is also a verified no-logs VPN service that has passed both security and privacy audits, as well as real-world tests. A few years back, Turkish government officials tried compelling ExpressVPN to give up logs. When this failed, they seized an ExpressVPN server, but still came up empty-handed.
If you need a VPN with the highest levels of security, ExpressVPN has you covered. It offers very secure VPN apps that encrypt traffic using 256-bit AES encryption. Traffic is further secured against any leaks with the Network Lock feature to prevent IP address leaks or DNS leaks. Here is the ExpressVPN Windows desktop app we tested:
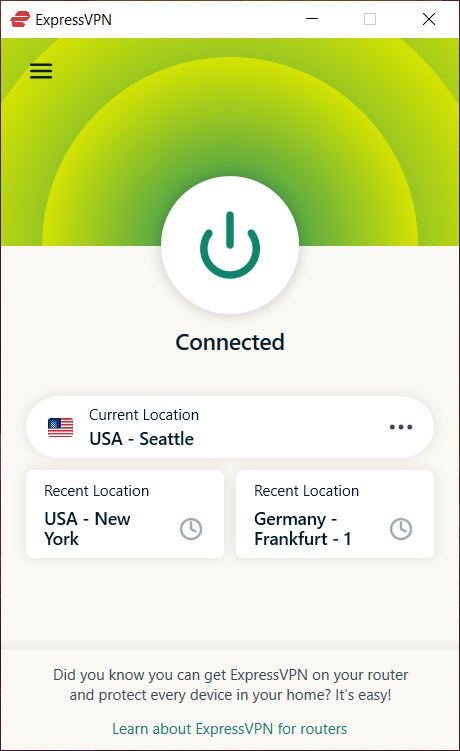
ExpressVPN does well in the performance category and supports the OpenVPN, IKEv2, and Lightway protocols. Lightway is a self-developed protocol that is very similar to WireGuard, with many performance benefits. However, in the ExpressVPN vs NordVPN comparison, we found that ExpressVPN’s Lightway is still not as fast as NordVPN’s WireGuard. Below is one such test result:
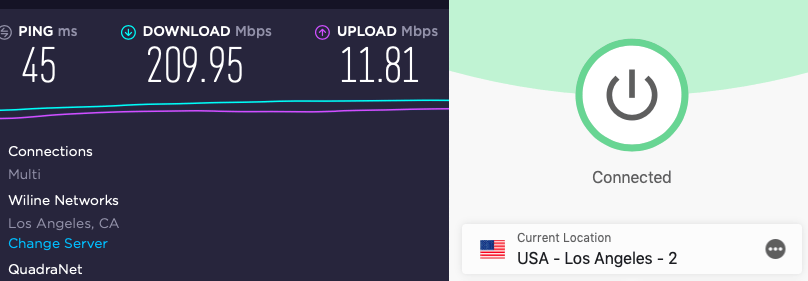
ExpressVPN operates a large network of high-bandwidth servers throughout the world, with secure self-hosted DNS. Like NordVPN and Surfshark, ExpressVPN also runs all servers in RAM-disk mode — see the TrustedServer feature.
If you enjoy streaming or torrenting, ExpressVPN is also one of the top choices. It currently ranks as one of the best VPNs for Netflix, providing 24/7 access to all major Netflix regions, including UK, Australia, and American Netflix. ExpressVPN also works well with other streaming services, such as if you need a VPN for Hulu, Disney Plus, and more.
Note: We have found that ExpressVPN is getting blocked recently with BBC iPlayer. If you want to use this service, we’d recommend going with NordVPN or Surfshark. See our guide on the best VPNs that work with BBC iPlayer for more on this topic.
ExpressVPN UK server locations
You can get a UK IP address with any of these ExpressVPN servers:
- Docklands
- East London
- London
- Wembley
Overall ExpressVPN is another great VPN for UK expats and residents alike. And while the prices are higher than the other two UK VPNs we examined, ExpressVPN remains a reliable and secure choice to consider.
+ Pros
- User-friendly and secure apps
- Split tunneling feature (for macOS, Windows, and routers)
- Works with Netflix and most streaming services
- 24/7 live chat support
- Passed independent third-party audits for security and no-logs
- Very large server network
– Cons
- Above average prices
- Fewer features than other leading VPNs
ExpressVPN Coupon:
Sign up for the 12-month plan and get 3 months added to your subscription for free.
(Coupon is applied automatically.)
See our ExpressVPN review for detailed test results and analysis.
Should you use a VPN based in the UK?
As a general rule of thumb, we here at RestorePrivacy do not recommend VPNs that are legally based in the UK — or the US for that matter.
The reason for this is that the UK is a bad jurisdiction for privacy, especially for companies that handle private data. Authorities in the UK have enormous power to coerce companies to collect and hand over customer data, which was greatly expanded with the Investigatory Powers Act. This means that a UK VPN service could be forced to log customer data, while also being prohibited from disclosing this to their users.
The UK is also an official member of the Five Eyes alliance, along with the US, Australia, Canada, and New Zealand. As a member, data collected by UK authorities is also available to the other Five Eyes member countries.
The risk of UK VPN providers logging customer data and handing it over to authorities is very real and should not be taken lightly. One noteworthy example of this was with HideMyAss (HMA VPN review), a VPN based in the UK that provided data logs to US authorities for a criminal investigation:
It appears that the FBI traced a hack into Sony back to an IP address owned by HMA and promptly got a UK court order, demanding logs from HMA an incident HMA dubbed the “LulzSec Fiasco” in a post on their blog on September 23rd, 2011.
This issue is discussed more in the HideMyAss vs NordVPN comparison.
When selecting the best VPN for the UK, jurisdiction is an important consideration. All of the providers in this guide are located in safe jurisdictions with strong privacy protections in place.
Four reasons to use a VPN for the UK
There are many reasons to use a VPN for the UK. Here are just a few we will cover:
- Privacy concerns and internet provider snooping
- Accessing UK media (BBC iPlayer and UK Netflix)
- Blocked websites
- Torrenting, filesharing, and Kodi streaming
1. Online privacy in the UK requires a VPN
Leaked documents about the PRISM program in the United States illustrate the degree to which corporate and government agencies work closely together to monitor, track, and record your online activities. This alarming development is also unfolding in the UK as well.

In November 2016, the Investigatory Powers Act (also called the Snooper’s Charter) officially became law. This bill massively expanded both monitoring and data collection of all UK residents, as well as persons of interest abroad (such as UK expats):
- Internet Service Providers (ISPs) and phone companies are now required to record every website you visit and how long you were on the website over a period of 12 months and provide that information to various agencies. (This information will be stored in a giant centralized database with everything under your name.)
- Legalizes bulk data collection of all personal communications (phone/text and internet)
- Legalizes real-time monitoring of everyone inside the UK, as well as large populations of people outside the UK.
- Requires tech companies to record data from apps and devices, such as iMessage and WhatsApp.
- Allows the government to force tech companies to hack into their customer’s devices (phones, computers, tablets) to steal private information.
- Allows for the targeted hacking of individuals, technology infrastructure, or even entire towns – if deemed necessary by UK officials.
We have documented that ISPs record browsing history throughout the world — not just in the UK. The UK is also regularly in the news over various privacy abuses that are carried out by various agencies. One recent court trial brought these abuses to new light.
Just like in the UK, Australia also ushered in massive data retention laws, which is discussed more in the best VPNs for Australia guide. This is a Western-wide trend we see unfolding.
Most people assume they have some degree of anonymity when they are online. As you can see with the developments above, this assumption is false.
Anyone in the UK who is not using a VPN is exposing their private data and online activities to third parties.

Perhaps more alarming is a law that makes it illegal to view any “terrorist propaganda” online. What exactly qualifies as “terrorist propaganda”? Who knows. This legislation is truly frightening when you consider that punishments for visiting the wrong site – even just once – can include up to 15 years in jail.
While these trends are concerning, we also see the same unfolding in Australia as well as the United States. I highlighted the worst policies when discussing VPNs for USA and the growing need for data privacy.
2. Using a VPN to watch BBC iPlayer, UK Netflix, and other UK TV streams
Many UK expats and residents abroad are looking for a safe and reliable way to access UK media. This is especially true for watching UK Netflix or streaming BBC iPlayer with a VPN. mm
A VPN is the best way to unblock UK media because it will provide you with a UK IP address, thereby making you appear to be in the UK. Simply connect to a VPN server in the UK (from anywhere in the world) and then stream any UK media as normal.
As mentioned above, the best VPN for streaming UK media is ExpressVPN. All three of the VPNs in this guide work well for streaming UK media.
Of course, be careful with free VPN services, free proxies, and shady browser extensions, which usually function as insecure data collection tools. (This is how the free services pay for themselves, by collecting your private data and selling it to third parties.)
3. Accessing blocked websites in the UK
There are now over 775,000 websites being actively blocked in the UK.
What types of websites are getting blocked? There are many different website categories getting blocked: torrenting, streaming, sports, adult content, music, videos, and more.
These website blocks in the UK are being carried out by UK internet providers. To block websites, UK internet providers simply block the DNS request, which is the translation request your computer sends to your internet provider to look up the specific IP address of a website you want to visit. If companies do not comply with blocking demands, they could face massive fines.
Here are the most popular UK internet providers that are blocking websites:
- BT Internet: 9+ million users
- Sky Broadband: 6+ million users
- Virgin Media: 5+ million users
- TalkTalk: 4+ million users
Additionally, there are also now age verification filters in place, which expose your identity and the sites you visit to third parties. This is yet another reason to use a good VPN service if you are in the UK.
The growing problem of blocked websites is also unfolding in Canada, as I pointed out when discussing the best VPNs for Canada.
Solution: When you use a VPN service, however, your DNS requests are processed by your VPN provider and all your traffic is encrypted and anonymized with other users on that server. Not only will your UK internet provider not be able to block any website you’re visiting, but it also won’t be able to see anything you’re up to online.
Any of the VPNs in this guide will work for unblocking websites. However, Surfshark and ExpressVPN have the largest networks, although NordVPN is close behind.
A VPN encrypts internet traffic and data, which makes it unreadable to your internet provider and other third parties.
4. Torrenting, file sharing, and Kodi streaming in the UK
In the United Kingdom, the punishments for copyright violations are getting downright absurd. These include massive fines and jail time for simply downloading, sharing, or torrenting copyrighted media. While some torrent clients offer encryption options, this will not keep you safe as your IP address can be exposed, especially with media companies actively monitoring torrent swarms and logging data.
Under the current law, people in the UK who are found guilty of pirating copyrighted material could face up to 10 years in jail.
The UK government is also cracking down on streaming sites and streaming platforms, such as Kodi. Because television programs are big business for media companies and advertisers, unauthorized third-party streams fall under copyright infringement laws. This means that even if you don’t download anything, you can still face the heavy consequences of copyright infringement for accessing third-party streams.
While there may be a small performance tradeoff when using a VPN (due to encryption) a premium VPN service will still provide excellent speeds for torrenting, streaming, and any other online activity.
Are VPNs legal in the UK?
Perhaps you are thinking, “Sounds good, but are VPNs legal in the UK?”
The answer to that question is yes. VPNs are perfectly legal in the UK, and all Western countries, for that matter.
In fact, VPNs are legal and necessary encryption technology that most businesses use for network security. Additionally, companies with remote workers also rely on VPN technology to securely access internal servers. Even in China, where VPNs are regularly blocked (for censorship reasons), VPN technology is still perfectly legal for all users.
In short, there’s nothing to worry about when using a VPN for the UK, especially since VPN services are becoming mainstream for all types of users. Unlike Tor, VPNs no longer come with any “stigma” of shady business, since they are now standard for streamers, torrenters, and average users who simply want more privacy and security online. Just be sure to pick a secure, fast, and reputable provider.
How to get a UK IP address with a VPN
If you are a UK expat living abroad, or just someone who wants to access British streaming platforms, then a VPN is the ticket you need. Here’s how to access UK streaming platforms like the BBC from anywhere in the world.
To watch your favorite British streaming platforms you’ll need a UK IP address. To get a UK IP address from anywhere in the world, follow these steps:
- Purchase one of the VPNs in this guide
- Download and install the VPN software on your device
- Connect to a UK VPN server
- Access the British streaming site like normal and enjoy your show
Unfortunately, some VPNs are getting detected and blocked by British media sites like the BBC. On a positive note, there are some great VPNs that are still getting through to BBC iPlayer, UK Netflix, and more.
Where can I watch UK TV for free?
Surprisingly, there are many services that let you stream British shows in US without paying a dime. For one, BBC iPlayer lets you watch 8 BBC channels, including BBC 1, BBC 2, and BBC4. There, you can find shows like Killing Eve, Blue Planet, and Eastenders. (We also have a guide on the best VPNs for BBC iPlayer.)
ITV is an independent British network that offers 6 of its channels for free, providing that your IP is from the UK. We are talking about ITV 1 – 4, ITVBe, and CITV. These channels have a wide-variety of content, spanning from news and talk shows, to comedies, dramas, and cartoons.
Channel 4 is a public and completely free netwok that you can access from anywhere, along with Sky News, a popular British news channel. They even have a Sky News YouTube channel that lets you watch content live without using VPN.
If you are more into UK sports, we recommend Eleven Sports, not to be confused with Eleven Sports Network, which is a US service. If you have a Pluto TV, you will be able to stream Eleven Sports without connecting to a UK server.
Note that we recommend paying for a premium VPN if you want a smooth streaming experience.
How can I get UK TV channels in the USA?
British services like Channel 4, BBC, and Sky all have geo-blocking, so you will need to use VPN to start streaming UK shows.
1. Find a VPN service that suits your budget
We highly recommend using Surfshark, ExpressVPN, or NordVPN since they have a large network of UK servers and are easy to use. For our top recommendation, you can get this deal: 69% off NordVPN >>
2. Download VPN
Each provider on our list will work on PCs, Macs, Androids, iPhone, SmartTVs, and other popular devices.
Note: If you want to stream British TV in the USA with a mobile device, you will first need to make a mobile hotspot by installing a VPN on your router or computer.
3. Connect to a server that’s in the UK
You will get the best performance by choosing the server that is closest to you.
4. Log–in or register to a British streaming service
Note that these services are not free, so you will still need to buy a subscription. When registering, make sure that you type in a UK zip code or you will get blocked.
5. Find favorite shows and movies and stream British TV in US
You can watch UK TV live or browse through huge libraries of services like BBC.
Conclusion on UK VPNs
On a positive note, privacy awareness seems to be growing in the UK. However, this is in large part to various privacy scandals, such as with Facebook being sued for losing control of user data.
As a brief recap, be careful when selecting your VPN, especially since there have been cases where UK VPN services provided logs to authorities. Our top recommendation is NordVPN. It performs the best at streaming UK shows with fast speeds and reliable apps.
Aside from streaming UK TV, a VPN is a very useful tool for privacy and security in general.
This UK VPN guide was last updated on July 28, 2023.



I use TotalAv VPN service which constantly cuts itself off. My reporting/complaining to them has been , more or less, ignored. When I asked to cancel and have a partial refund, they merely advised that I can only cancel within first 30days, with no comments at all regarding breach of contract in failing to provide a working service. Is there a regulatory body I can report them to?