
A large-scale malware distribution campaign uses YouTube videos to direct viewers to websites that pretend to offer installers for over 100 games and apps but instead infect them with information stealers.
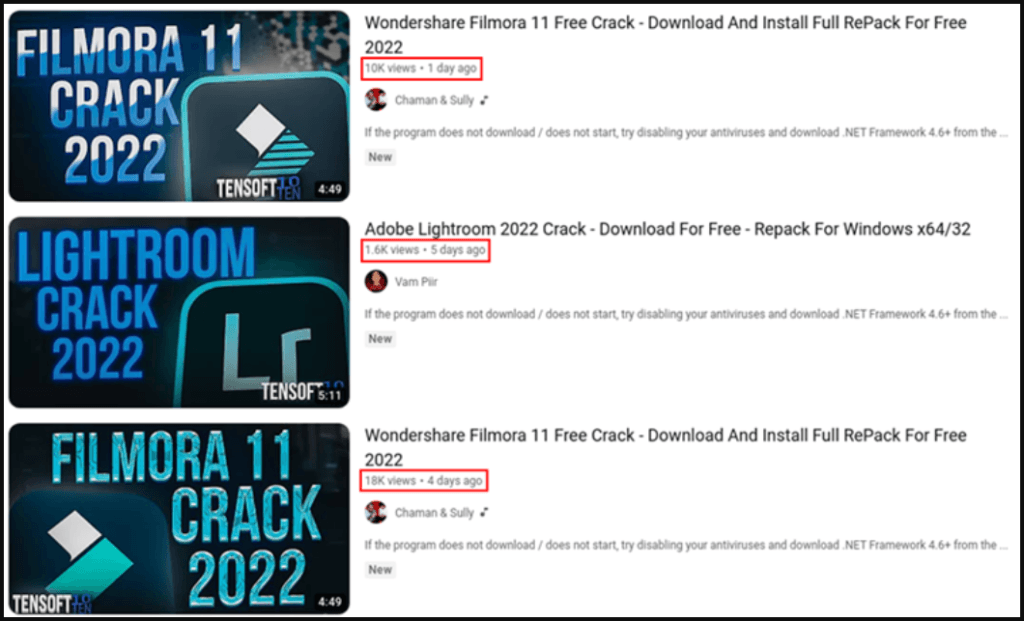
Using YouTube videos to infect people with malware isn’t a novel technique, but on previous occasions, the threat actors included the download link in the video description.
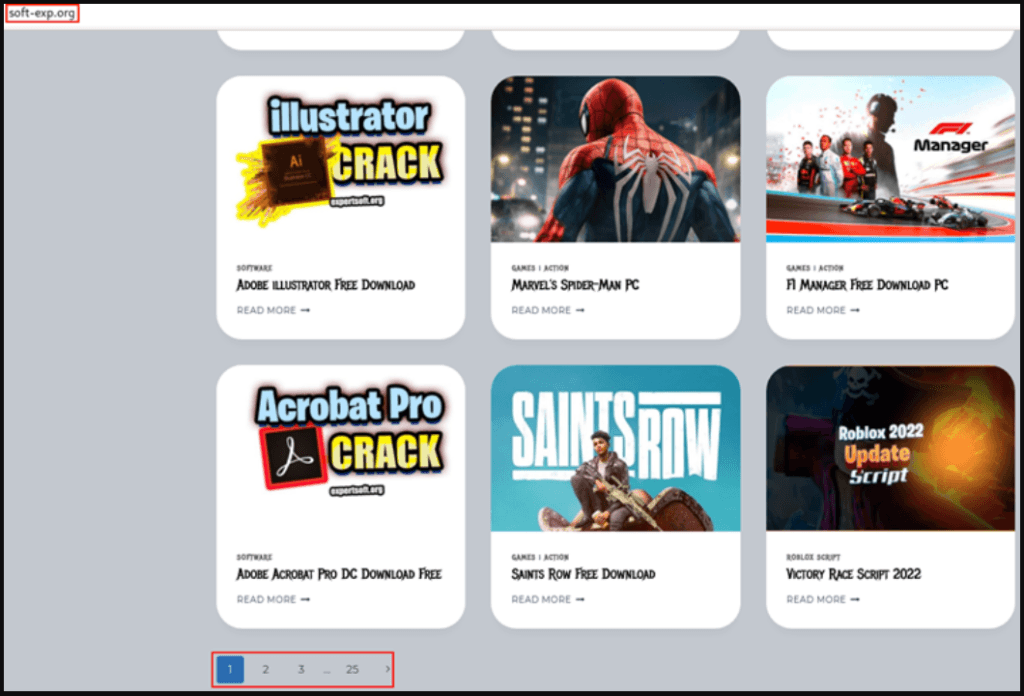
In this campaign, spotted first by researchers at Cyble, the link on the video description doesn’t lead to downloading the executable but on a site that features a galore of software options.
Cyble
This tactic has several advantages for the campaign operators, including that:
YouTube is less likely to delete those videos since they don’t link directly to a malicious resource,
there can be multiple videos with varying lures pointing to the same website,
visitors are likely to spot other stuff they’re interested in, ending up installing multiple files and creating redundancy for the attackers.
The software lures used in these sites include expensive productivity tools like Adobe Lightroom 2022, Sony Vegas Pro, and AutoCAD, or games like Saints Row, NBA 2K23, and Marvel’s Spider-Man.
Cyble
In many cases, there are also plugins, cracks, ROBLOX scripts, and hacks/cheats for games promising unlimited in-game money, feature unlocking, etc.
The two info-stealers dropped by this campaign are Vidar Stealer and RecordBreaker Stealer (aka Raccoon stealer v2.0), two malware strains rented to independent operators for a subscription.

Cyble
Vidar is a relatively aged but still potent info stealer that targets the victim’s browser for any information saved in the local database, including saved logins, history, cryptocurrency wallets, and more.
Raccoon stealer is a newer (2022) malware that exfiltrates basic system info, browser passwords, cookies, and autofill data, and also targets cryptocurrency wallets either in extension or desktop app form.
Additionally, Raccoon can capture screenshots from the victim’s desktop to snap passwords and other sensitive information and can exfiltrate entire files located on any disk on the breached system.
The malware-hosting sites identified by Cyble this time are:
- allsoftware[.]cloud
- appshigha[.]com
- autosoftware[.]pw
- bebrasoft[.]com
- free-crack-soft[.]com
- hacksoftware[.]fun
- softload[.]tech
- softwarecloud[.]space
- wh1tesoftware[.]me
- free-warez[.]site
- kokoasoft[.]com
If you happen to land on any of the above websites, you should avoid downloading the promised software as, in reality, it’s all just malware.
It should be noted that the threat actors can easily switch to new domains now that Cyble has blown their cover, so avoid browsing questionable sites in general.
Finally, keep in mind that YouTube moderation relies on user reports. Many malicious videos amass tens of thousands of views before they are removed from the platform, so none of them should be blindly trusted.

 Abuse of IPFS to Host Malware and Phishing Kits on the Rise
Abuse of IPFS to Host Malware and Phishing Kits on the Rise
i’ve experienced wh1tesoftware, downloaded the adobe lightroom, please get these dirty bastards.
Sven Sir which antivirus do you use on your personal computer?
Thank you for the article.
I tested these links on my smartphone and Avast mobile antivirus as well as ESET Parental control blocked all these links.
Avast may not be privacy friendly, and it may try to upsell hard, but when it comes to offering strong protection against malware Avast is a force to be reckoned with.
YouTube and TikTok are the two most reliable sites on the net to obtain facts about everything. It’s used by far right extremists and “conspiracy theorists” everywhere to promote their ideologies! If they rely on it, you know it’s got to be good. /s
Hi, Great article!
I ran the links through VirusTotal and it flagged them all as malicious.
How much trust should one place on VirusTotal?
Is it recommended?
VirusTotal is a great resource to use.