
Mozilla Firefox is one of the best browsers available that combines strong privacy protection features, good security, active development, and regular updates. The newest version of Firefox is fast, light-weight, and packed full of privacy and security features.
It is for this reason that I consider Firefox to be the best all-around browser for privacy and security. It remains a solid alternative to some of the other options, such as Google Chrome, Microsoft Edge, and Safari.
Another great aspect of Firefox is that it is highly customizable, which is the point of this guide. Below we will go over how you can customize Firefox to give you the security and privacy you desire, while still working well for day-to-day browsing.
But before we jump in, let’s cover some important details.
Important considerations before starting
There are many factors to consider when configuring Firefox to meet your needs, including your threat model and browsing preferences. In other words, there is no “one-size-fits-all” configuration that will work for everyone. This guide is a basic overview covering some of the different configurations options.
Before you start modifying Firefox and installing a bunch of add-ons, it’s important to consider browser fingerprinting.
Browser fingerprinting
The issue of browser fingerprinting (or device fingerprinting) is a big topic that covers all the different ways you can be tracked and identified by your system and various settings. All of the different add-ons you install and preference modifications you make to Firefox are inputs that can potentially be used to identify and track you.
Herein lies the catch-22: the more browser add-ons you install and settings you modify, the more likely you will stand out from the crowd and be easier to track. There are solutions for this and the latest version of Firefox does offer some fingerprinting protection. I discuss this problem and also provide solutions in the browser fingerprinting guide.
And that leads us to the next point that…
More is not always better
When it comes to browser add-ons and modifications, you don’t want to be like that kid who puts every topping imaginable on his ice cream. Similarly, more is not always better with Firefox browser add-ons.
Aside from the issue of browser fingerprinting, having too many add-ons may slow down performance and break things. Many of the popular Firefox add-ons also fulfill the same functions and are redundant when used together.
Therefore it is best to strike a balanced approach. Install and modify only what you think will be useful and necessary for your specific situation.
Proceed with caution
Modifying some of these settings may interfere with your browsing experience and break some websites (they won’t load properly). Therefore taking an incremental approach may be the best way to proceed. You can continue to install add-ons and adjust your settings as you see what works best for your needs.
This allows you to modify the settings, create exceptions, or add sites to a whitelist.
Firefox privacy tweaks
Before you get going with Firefox you may want to adjust the following settings for better privacy.
Note: if you are a Mac OS user, you will see the word “Preferences” in your menu rather than “Options” as it is listed below.
Disable Firefox telemetry
With the latest version of Firefox, it is configured to share “technical and interaction data” with Mozilla. This includes the ability to “install and run studies” on your computer. You can learn more about these studies and data collection practices, but I’d recommend disabling these settings.
To disable go to Open Menu (three bars at the top right corner of the browser) > Options > Privacy & Security > Firefox Data Collection and Use and then uncheck the boxes as you see below:
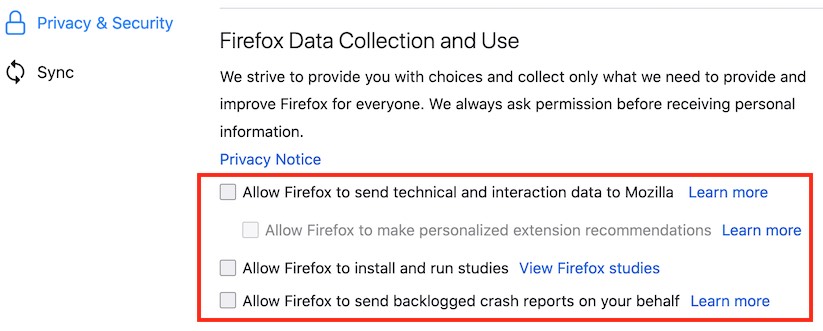
You can also disable data sharing with Firefox for Android by going to Menu > Options > Privacy > Data Choices and then uncheck all three categories for Telemetry, Crash Reporter, and Mozilla Location Service.
Note: You can also disable this in the About:Config settings with toolkit.telemetry.enabled set to false.
Change the default search engine in Firefox
Firefox now uses Google as the default search engine, but there are other private search engines you can use instead.
To do this, go to Menu > Options > Search > Default Search Engine. Firefox does not provide you with very many alternatives directly in the settings area. However, you can view more options by going down to One-Click Search Engines and then click Find more search engines to see the other alternatives.
See our guide on private search engines to dive into this topic more.
Firefox also has a guide on modifying your search engine preferences.
Firefox Content Blocking
Another great new feature with Firefox is Content Blocking. This customizable feature will automatically block “content that tracks the sites you visit and profiles you.” You can choose between Standard, Strict, and Custom modes, which allow you to block:
- Cookies
- Tracking content
- Cyrptominers
- Fingerprinters
To adjust the Firefox Content Blocking settings, go to Menu > Options > Privacy and Security > Content Blocking and then select which mode you want to use.

The Standard setting may be the best balance for regular users. Firefox warns that Strict mode may “cause some websites to break.” However, you can still…
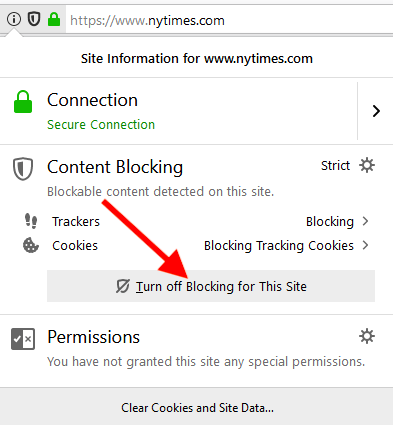
Disable content blocking for specific sites
It’s easy to disable content blocking for certain trusted sites. Simply enter the website URL, then click the “i” icon to the left of the address bar, then click the grey button to “Turn off Blocking for This Site.”
Another benefit of Firefox’s Content Blocking feature is that it can save your data and improve page load speeds.
The “Do Not Track” request
Firefox also has an option to request that websites “do not track” you online. This is simply an HTTP header field that you can easily enable. However, the key word here is request, because this is not actually blocking anything. We have also learned that many websites simply ignore these requests.
In addition to being ignored by most sites, this is also a value that can be used for browser fingerprinting purposes, as explained here. Therefore I no longer recommend enabling or modifying the Do Not Track settings, which you’ll find in the Content Blocking settings area.
You can learn more about the Do Not Track feature here.
Firefox About:Config settings
Aside from the general Menu settings we used above, you can also make a number of different modifications using about:config.
Note: If you made all of the changes above, you may notice that some of these settings are already updated in about:config. We will still cover the different about:config since some people prefer to modify settings in this area, rather than through the general Menu.
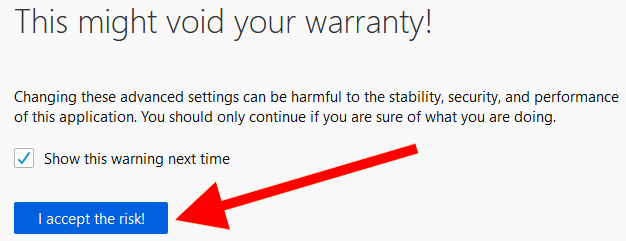
To access these configuration settings, simply enter about:config into the URL bar and hit enter. You will then be prompted with a warning screen stating “This might void your warranty.” Just click “I accept the risk” to continue.
After proceeding, you will see a large list of preferences, which each include a status, type, and value.
These preferences will be listed in alphabetical order and are easily searchable from the search bar near the top.
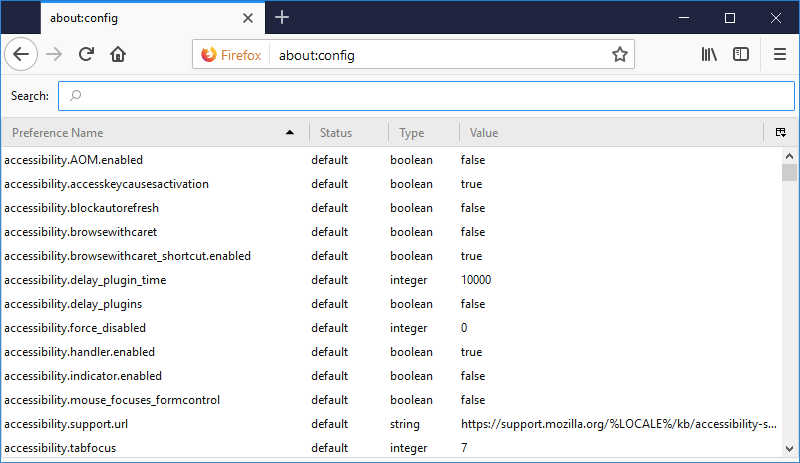
Modifying preferences – You can modify any of these Firefox preferences by simply double clicking the preference name. If the preference is a “boolean” type, then double clicking will change the value to true or false. If the preference is an “integer” or “string” type, double clicking will open a box to change the value.
Here are my recommended changes:
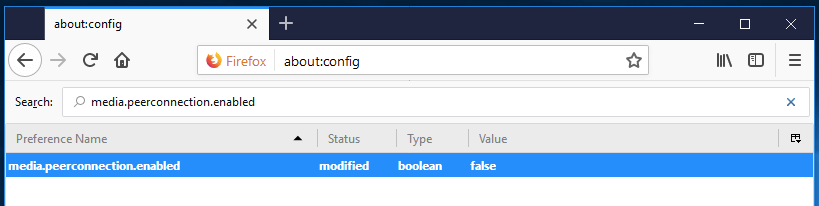
Disable WebRTC:
media.peerconnection.enabled (WebRTC) = false
WebRTC stands for “Web Real-Time Communication” and it allows for voice, video chat, and P2P sharing through your browser. Unfortunately, this capability can also expose your real IP address through browser STUN requests, even if you are using a good VPN service. (This is called a WebRTC leak.)
To disable WebRTC in Firefox simply enter media.peerconnection.enabled into the search bar and then double click the value to change it to false.
Aside from Firefox, the WebRTC vulnerability also affects Chrome, Opera, Brave, and other Chromium-based browsers. Safari is also in the process of implementing WebRTC.
Note: If you disable WebRTC, services like Google Meet and Whereby may not work.
Resist Fingerprinting:
privacy.resistFingerprinting = true
Changing this preference to true will help to make Firefox more resistant to browser fingerprinting.
Note: There are many factors that go into browser fingerprinting and the ability of an adversary to identify you. See the browser fingerprinting guide for additional details.
privacy.trackingprotection.fingerprinting.enabled = true
This is a new preference with Firefox 67+ to block fingerprinting.
privacy.trackingprotection.cryptomining.enabled = true
Another new preference with Firefox 67+, this will block cryptominers.
First party isolate
privacy.firstparty.isolate = true
Changing this to true will isolate cookies to the first party domain, which prevents tracking across multiple domains. First party isolation also does much more than isolating cookies, it affects: cookies, cache, HTTP Authentication, DOM Storage, Flash cookies, SSL and TLS session resumption, Shared Workers, blob URIs, SPDY and HTTP/2, automated cross-origin redirects, window.name, auto-form fill, HSTS and HPKP supercookies, broadcast channels, OCSP, favicons, mediasource URIs and Mediastream, speculative and prefetched connections.
This preference was added in late 2017 as part of the Tor Uplift Project.
Tracking protection
privacy.trackingprotection.enabled = true
Another new update, this is Mozilla’s built-in tracking protection feature. This will use a Disconnect.me filter list, but may be redundant if you are using uBlock Origin 3rd party filters.
Disable geolocation tracking
geo.enabled = false
Setting this to false will disable geolocation tracking, which may be requested by a site you are visiting. As explained by Mozilla, this preference is enabled by default and utilizes Google Location Services to pinpoint your location. In order to do that, Firefox sends Google:
- your computer’s IP address
- information about nearby wireless access points
- a random client identifier, which is assigned by Google (expires every two weeks)
Before this data is sent to Google, you would first get a request by the site you are visiting. Therefore you do have control over this, even if geo remains enabled.
media.navigator.enabled = false
Setting this preference to false will block websites from being able to track the microphone and camera status of your device.
network.cookie.cookieBehavior
This is an integer type preference with different values. Here are the cookie preference options:
- 0 = Accept all cookies by default
- 1 = Only accept from the originating site (block third-party cookies)
- 2 = Block all cookies by default
- 3 = Block cookies from unvisited sites
- 4 = New Cookie Jar policy (prevent storage access to trackers)
Any selection between 1 and 4 would improve privacy. The New Cookie Jar policy (value 4) offers more protection, but it may also break the functionality of some websites. Ghacks has a discussion of the New Cookie Jar policy here.
network.cookie.lifetimePolicy = 2
This is another integer type preference that you should set to a value of 2. This preference determines when cookies are deleted. Here are the different options:
- 0 = Accept cookies normally
- 1 = Prompt for each cookie
- 2 = Accept for current session only
- 3 = Accept for N days
With a value of 2, websites you visit should work without any problems, and all cookies will be automatically deleted at the end of the session.
network.dns.disablePrefetch = true
Setting this preference to true will disable Firefox from “prefetching” DNS requests. While advanced domain name resolution may slightly improve page load speeds, this also comes with some risks, as described in this paper.
network.prefetch-next = false
Similar to prefetching DNS requests above, setting this preference to false will prevent pages from being prefetched by Firefox. Mozilla has deployed this feature to speed up web pages that you might visit. However, it will use up resources and poses a risk to privacy. This is another example of performance at the price of privacy.
Disable WebGL:
webgl.disabled = true
WebGL is a potential security risk, which is why it is best disabled by setting webgl.disabled to true. Another issue with WebGL is that it can be used to fingerprint your device.
You can get more information on the WebGL issue here and here.
dom.event.clipboardevents.enabled = false
This prevents websites from getting notifications if you copy, paste, or cut something from the page.
media.eme.enabled = false
This disables the playback of DRM-controlled HTML5 content. See details here.
Firefox “safe browsing” preferences
There are many recommendations to disable the Safe Browsing feature in Firefox due to privacy concerns and potential Google tracking. However, these concerns are based on an older version of the Safe Browsing feature, which would utilize “real-time lookup” of website URLs. This method has not been in use since 2011 – explained further here.
If a URL is needed, Firefox takes the following precautions to protect user privacy, as explained by François Marier, a security engineer for Mozilla:
- Query string parameters are stripped from URLs we check as part of the download protection feature.
- Cookies set by the Safe Browsing servers to protect the service from abuse are stored in a separate cookie jar so that they are not mixed with regular browsing/session cookies.
- When requesting complete hashes for a 32-bit prefix, Firefox throws in a number of extra “noise” entries to obfuscate the original URL further.
Therefore I would conclude that disabling Safe Browsing would give you no tangible privacy benefits, while also being a security risk. That being said, if you still want to disable this feature, here’s how in the about:config area:
- browser.safebrowsing.phishing.enabled = false
- browser.safebrowsing.malware.enabled = false
Firefox privacy and security add-ons
There are some great Firefox browser add-ons that will give you more privacy and security. With that being said, many of the add-ons we previously recommended are no longer necessary thanks to Firefox’s upgraded privacy and security settings.
Note: When looking for Firefox add-ons, be sure to consider what you need in relation to the preferences you modified above. Some add-ons will be redundant and not necessary depending on your Firefox preferences and the other add-ons you are using.
uBlock Origin
uBlock Origin is an efficient, light-weight blocker that filters both ads and tracking. It has risen to popularity as a powerful alternative to Adblock Plus, which allows “acceptable ads” that many users disdain. One added benefit of uBlock Origin is that it can significantly improve performance and page load speed.
Another great feature with uBlock Origin is the ability to whitelist certain websites. Given that many sites will block access if they detect an ad-blocker, the ability to whitelist will come in handy. uBlock Origin is free and entirely open source.
NoScript
NoScript is a script-blocker that allows you to identify/block scripts running on websites. While it does give you control, NoScript can be a pain to get configured properly. It breaks many websites, which requires you to tweak and configure the options. If you are already using uBlock Origin, then you probably don’t need to be using NoScript.
This is definitely not an add-on for the casual user or those who don’t have the patience to devote some time into configuration.
Using a VPN with Firefox
Firefox currently offers a VPN (virtual private network) called Mozilla VPN. However, this is just a rebranded version of Mullvad and I have seen many users complaining on various forums about the lack of support when things go wrong.
Note that while some VPNs offer browser extensions for Firefox, these are fundamentally different from a full VPN. A VPN will run on your operating system (not just your browser) and encrypt all internet traffic on your operating system. This is different from a browser extension that only wraps your browsing traffic inside an additional layer of encryption.
Additionally, some Firefox VPN extensions are actually just an extension of the desktop VPN application. These “extensions” literally just extend control of the VPN to a convenient browser interface. We discuss this and more in our guide on the best VPNs for Firefox.
Firefox DNS over HTTPS (DoH) is not a great idea
Just like with Firefox Private Network, the implementation of DNS over HTTPS also relies on Cloudflare infrastructure. In fact, it makes Cloudflare the central processing point for all DNS requests in the Firefox browser by default.
While DNS over HTTPS may sound advantageous in some respects, there are also potential concerns. Rather than going over why, you can read the article, Centralised DoH is bad for privacy, in 2019 and beyond, which concludes:
Centralised DoH is currently a privacy net negative since anyone that could see your metadata can still see your metadata when DNS is moved to a third party. Additionally, that third party then gets a complete log per device of all DNS queries, in a way that can even be tracked across IP addresses.
Even if further privacy leaks are plugged, DoH to a third party remains at best a partial solution, one that should not be relied upon as a serious security layer, since it will be hard to plug everything, especially if non-CDN content providers survive.
Encrypting DNS is good, but if this could be done without involving additional parties, that would be better.
And for actual privacy on untrusted networks, nothing beats a VPN, except possibly not using hostile networks.
Many people also assume that encrypted third-party DNS will somehow offer privacy and anonymity. This is a false assumption. Your IP address and location remains exposed with everything you do online, while your ISP will still be able to see the websites you visit (IP addresses) even if it’s no longer handling DNS requests. In conclusion, a good VPN will offer much more protection than DoH through Cloudflare.
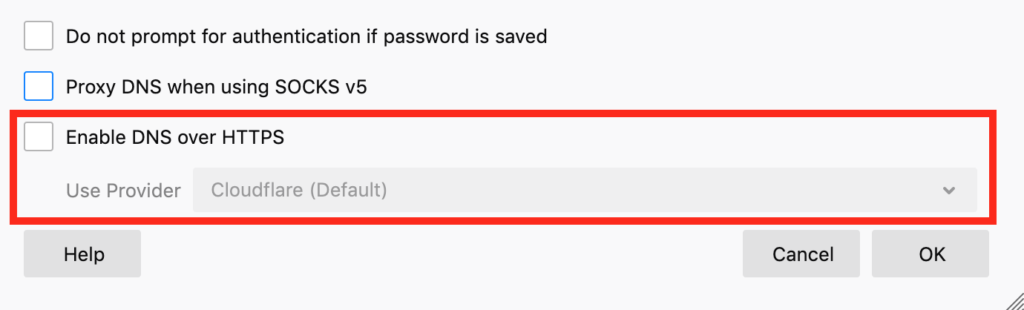
To disable DNS over HTTPS (DoH) in Firefox go to Menu > Options > General and then scroll down to Network Settings and click the Settings button. In the box that opens, scroll down to Enable DNS over HTTPS, where it can be enabled or disabled.
user.js Firefox hardening
For more information and resources on Firefox hardening, see here: user.js Firefox hardening.
As explained on their GitHub page, this is a “configuration file that can control hundreds of Firefox settings. For a more technical breakdown and explanation, you can read more on the overview wiki page.”
Their Wiki page is also full of great information.
Firefox privacy conclusion
In my opinion, Firefox remains the best all-around, mainstream browser on the market for privacy when it is modified as recommended above.
While many of the configurations and add-ons discussed in this guide will go a long way to giving you more privacy, there is one issue that remains: concealing your IP address and location. To do this, a good VPN service is necessary. The Tor network also achieves this end, but it comes with the drawbacks of slow speeds, risks, and limitations (only works in a browser).
For more options in addition to Firefox, see the secure browser guide.
This Firefox Privacy article was last updated on January 19, 2024.

What is option 5 in (network.cookie.cookieBehavior) you mention options 1-4 does that mean 5 is bad to use or was 5 not an option when you updated the guide – the ghacks page you link to regards firefox#65 from 2018
You should update this info…. I can not get into about:config with an android phone with android 13.
use the firefox beta one for andriod. you can do the about:config from there.
This is an excellent “how to do” list for making web browsing more private.
HATS OFF to Sven and restoreprivacy for their invaluable contribution to privacy.
Hi guys!
So, I am running down the checklist of things to help with Firefox Privacy and I am in the about:config section. It is so hard to stay up to date on so many things, which I totally understand. So, anyway, on your HowTo Checklist, it gives a range of 1-4. And then you explain what each one was, and the last one, #4 was the Cookie Jar thing. So, I saw that my version was none of the choices ( lol, Firefox[^1] updates faster than I change underwear, and I am just shy of fanatical OCD about being clean, sorry about the TMI[^2] bomb). So, being unsure, I left it at 5 until I read otherwise. Out of curiosity, the next setting in the config list is very similar and didn’t know if you were familiar with that one (listed below) and really, I mention it more for it also possibly having an as-yet unknown setting of 5. Anyway, thanks for all of your hard work! I really appreciate you and this site. I tell everyone I can about it.
network.cookie.cookieBehavior = 5
network.cookie.cookieBehavior.pbmode = 5
[1] – Firefox Browser(desktop) version 106.0 (64-bit) Mozilla Firefox Snap for Ubuntu canonical-002 – 1.0
[2] – TMI = Too Much Information 🙂 (With so many abbreviations, best to avoid confusion/unintended insults.
Running Kubuntu 22.10 on an HP laptop: AMD Ryzen 5 3500U w/ Radeon Vega Mobile Gfx
About Adblock Plus.
I see that alot of users get them selfs hung up on “acceptable ads”. This can be turned off.
I myself have never really understood the popularity of uBlock Origin. The GUI is really hard to understand.
network.cookie.cookieBehavior = 5 is not updated here.
this
Here it is: https://securityboulevard.com/2022/01/easy-firefox-fix-of-the-day-disable-http3/ (configure firefox to delete http3 use)
Http3 and QUIC are not addressed, although Salesforce has already come up with a way to ID people using the ID and more information. https://www.youtube.com/watch?app=desktop&v=RCUKGn6F9ac
Does the advice about DoH change for Canadians, who have the option of CIRA Canadian Shield? Do we know if this would be a better option than DoH with the aforementioned American companies?
How does one install user.js on win 11 and 10? so confusing
Excellent! guide Sven. Thanks a lot for your time and great content. I just optimized Firefox Quantum, which does not look a bad option.
@Firefox DNS over HTTPS (DoH) is not a great idea…
Sven, this is not not necessarily true. Like with VPN, if you use some of the great nad proven services, like Cloud9 DNS or AdGuard DNS, without DNS leaks, this encryption is excellent for privacy!
“Delete cookies at any time” and “camera & microphone disabled”
Other than these two, the others are being used.
Very good guide, thanks.
I’m trying to harden a fresh install of firefox on ios 15. Cannot get about:config to work. I see the same complaint by others on Mozilla help ‘blank screen only’. And no answers provided. Next I tried FF Focus, and found google trackers are now allowed/ enforced, so not what I want. Can you recommend a safe workaround? Maybe arkenfox?
For iOS, every browser works through their WebKit rendering engine. You can’t modify Firefox. But, if you want their browser on iOS, use Focus. You can simply block any of these trackers with a DNS blocker, like AdGuard…
Thanks. Sorry to hear that. I allways used hardened firefox on my win7 desktop. Very successful for me, at my ‘dummies guide’ skill level. I was appalled to see the huge load of spyware the current Firefox dumped on my phone. (What gives with Mozilla?) Looks like I need a factory reset to get rid of it. Besides adguard, can other help be added to Focus? I’m just a citizen who believes in privacy for individuals and to preserve democracy. So I’m likely not a target unless too much time on privacy sites qualifies me as one. Please offer advice for a good setup after the reset.
DNSCloak
This is another very good piece of app for iOS. If you want to block various trackers in apps, this is very simple and free application.
A note: I did disparage Mozilla. I also visited a French ‘privacy’ products
site called Murena. The GDPR opt out was easy. And the list of spyware involved was eye popping, easily five+ times the amount from Mozilla. Changes my perspective. Plus, does a GDPR opt out actually take effect if you are a USA data subject using it?
There are a lot of experimental webkit settings with toggles available on the ios 15. I don’t know which would help/ harm me for privacy. Also it might just make me unique if I mess with them. I have willing ears for knowledge you may offer.
Thank you the the very in depth converage of how to further protect myself using Mozilla… I have not seen these settings and ways to protect myself ANYWHERE else…
THANK YOU AND KEEP UP THE GOOD WORK!
I comment Librewolf browser. Seems like Firefox but is different and better for the privacy!
Very cool! Mozilla has released a new add-on for Firefox to translate webpages.
https://techcrunch.com/2022/06/02/mozilla-brings-free-offline-translation-to-firefox/
Henry at Techlore on YouTube has done a video on hardening Firefox and he reveals that a lot of changes to the browser and using many extensions are not required anymore since Mozilla is building in many privacy features to prevent problems extensions were made to address. He also briefly discusses Arkenfox and how to install it in the browser.
https://youtu.be/F7-bW2y6lcI
what about Premium Proton VPN and can you expand on Password apps like Last Pass…?
So when using Mozilla Firefox, to log into Privacy apps, then use what app to browse?
I would suggest using an open source password manager, like Bitwarden, and not use proprietary ones like LastPass. However, Firefox can be your account browser but you can have another browser, like Firefox focus, to surf the web. You don’t have to limit yourself to just one browser.
this change in about:config privacy.resistFingerprinting changes the size of every web page. I resized them to full screen but when I closed down a site and then reopened it the size went right back to small and I’m not computer smart enough to figure out how to fix this issue
any suggestions on how to fix this?
The reason being is because the browser window size is fingerprintable. Forcing it to be the same size as others who enable privacy.resistFingerprinting will make everyone’s browsers harder to fingerprint. The only way to fix it is to disable privacy.resistFingerprinting but you lose the privacy advantages of it.
It appears that setting “privacy.resistFingerprinting = true” does not allow you to use the Bitwarden plugin in Firefox.
solution to this fingerprinting problem is solved very easily thanks to GOLOGIN with a promo code for a two-week free period PERSONAX, it can be activated after downloading, a little life hack
@Sergey,
There is some interesting tech for providing privacy solutions in the site you reference.
I looked at said site and they are clearly promoting to affiliate marketers.
These sites that promote a service to affiliate marketers have very little to do with privacy ethics.
They have a lot to do with violation of terms of service and avoiding detection of this.
Basically, affiliate marketers are creating multiple accounts (Facebook etc) and pretending to be multiple persons advocating the same advertisement and earning multiple commissions. Yes affiliate marketing is an industry and yes providing software to that industry is a service.
To the software developers, they would be much better employing their skill to the privacy concerned.
Regards,
BoBeX
After these modifications, I’m not able to use Jupyter Notebook anymore. I’m redirected to a page saying “Token authentication is enabled “.
Does someone know what did that ?
Your browser’s settings may be breaking websites and you might have done too much too soon. As it turns out, Mozilla is slowing implementing changes to Firefox build in in features may extensions or internal changes outlined on sites like this. So you may not have had to done everything at once if that is what you did. If so, in the interim you can probably just use uBlockOrigin.
Here is an advanced user’s guide to using uBlockOrigin:
https://www.maketecheasier.com/ultimate-ublock-origin-superusers-guide/
Liked!
Great link!
Good luck all
While there are ways you can avoid this identifier, but Mozilla are such hypocrites.
https://www.ghacks.net/2022/03/17/each-firefox-download-has-a-unique-identifier/
@Mike, nice pickup. These things would be preferably opt-in only.
It is very unfortunate, if not outright sad, that Mozilla would politicize their signature product, Firefox. In short, their removing specific search providers and social media platforms, that happen to be Russian, demonstrates they not only do not respect their user’s privacy but people’s ability to comprehend and interpret information. Firefox and Mozilla’s other products are now useless.
https://www.bleepingcomputer.com/news/software/mozilla-firefox-removes-russian-search-providers-over-misinformation-concerns/
They all have fear to be put into camp if they don’t obey. Total cowards.
What Browser do you recommend now?
@Arthur sorry for the late reply. Despite this development, I am still using FIrefox and you could too. However, other options may be Brave or Ghostery Dawn (which is Firefox fork). I do not think what Mozilla has done is as serious as what DuckDuckGo has done or is doing, It is still concerning, but there is a Yandex add-on or extension that is still available on the Firefox Add-On repository.
Hi, I have implemented all your suggestions but now my I am automatically logged out of my accounts on restart. What can I do to stay logged in?
Hi Sven,
I followed these recommendations, and now NordPass refuses to fill in any fields. I’m going back thru undoing everything. Maybe a comment for which of the above breaks NordPass functionality would be great.
Thanks
Thanks for the info, for me as an average user this has given me a lot of insight which would probably cost me days to figure out. One question I have is the following. When I was checking FF on the new Panopticlick website (directing me to coveryourtracks.eff.org, I was still unique among more than 250 000 tests run. What I noticed was, that it was possible that a server can request the fonts installed, accounting for about 20% of identifying information. Is there a way to prevent this?
Without tweaking advanced preferences in about:config manually or with Arkenfox etc… you can not enjoy the full privacy features Firefox offers. It was very intimidating for me at first but I figured out tweaking manually.
I do remember reading that there is a privacy settings add on for FireFox but I am not sure if it is still around or currently maintained or for that matter if it will improve your fingerprint
I am Firefox user with Arkenfox user.js and some plugins and Qutebrowser. On amiunique and panopticlick I am with Firefox unique but with mine settings of Qutebrowser I am NOT UNIQUE and I am feeling more secure and not less privacy than on Firefox. Im am on FreeBSD.
“privacy.resistFingerprinting = TRUE” cause FF to forget the previous window size and always open in a “small windows”
If “privacy.resistFingerprinting = FALSE” FF open with the same size of window it has in the previous use.
Any solution to use the TRUE value and allow FF to open with the same size of window it has before?
Thanks, Lucio
Ummmm……dude. You do realize that part of resisting fingerprinting is having every single user have the same size browser window, right? If you’re going to resize your window, they you should NOT have resistFingerprinting set to TRUE.
If you do have resistFingerprinting set to TRUE, then you should NEVER, EVER resize your window for any reason whatsoever. That’s the whole point of resisting fingerprinting! (facepalm)
Looks to me like you’re missing the point. A browser shouldn’t be sending my window size to the server to begin with.
Well, dumb me just asked that same question as Lucio asked and NO I didn’t realize resistFingerprinting did that. No need for you to be sarcastic to those of us with lesser computer knowledge, thank you very much!
If I make these changes in my firefox browser for mac, will they sync with firefox for iOS?
On Android, use uBlock Origin Firefox add-on and set it to block 3rd parties and disable JS by default. Use a device firewall to ban Mozilla adresses you’d rather not let Firefox use, but make sure you keep the fox updated manually and don’t fall behind the pace if you do.
I’m hoping RethinkDNS (an Android firewall) will soon let us ban domain names rather than inconvenient IPs only though.
The people behind the website Privacy Guides (formerly known as Privacy Tools) state there’s no need to configure Firefox desktop using i.e. about:config any more.
https://privacyguides.org/blog/2021/12/01/firefox-privacy-2021-update/
My friend, look go to Privacytools.io and go the guides button at top right and read the article about “Jonah Aragon”
Mozilla, the group behind the Firefox browser, is asking for people’s help in conducting a study called the “Facebook Pixel Hunt” that will analyze Facebook’s “tracking pixels” that track user actions across the internet using a special browser add-on.
https://gizmodo.com/mozilla-is-going-to-track-facebook-tracking-you-1848338946
Brave has a similar feature — it allows you to have multiple profiles with different extensions open simultaneously, and distinguishes them by changing the window background color. You can easily open one of your other profiles from the profile switcher menu on the right side. Its not identical to Firefox containers but is better integrated and does not require an extension. If you wanted to stay logged into a site but did not want to risk any cross-site tracking, or did not want an extension to have access to every site, you could create a separate profile and whitelist the site in Cookie Autodelete.
“In some ways this is actually better than FF + Containers.”
https://community.brave.com/t/equivalent-of-multi-account-containers-or-temporary-containers-extension-ff/135573/13
Thanks for the tip. I realized that Cloudflare DNS/DoH was still enabled in the router when I saw a half-dozen servers in the test after changing this Ublock setting. If the router is configured to proxy everything through a VPN, and DoH is disabled, it uses the DNS provided by the VPN service. If you are not using Mullvad DNS, the test will still indicate a “leak”, but only 1 “leak” is shown (which is the DNS provided by the VPN, so not a real leak.) You can confirm this at https://dnsleaktest.com/
I believe that Brave integrates Ublock, and you can control the filter list here:
brave://adblock/
___
https://www.ghacks.net/2021/02/10/brave-browser-adds-native-support-for-ublock-and-fanboy-annoyances-lists-and-social-list/
Maybe you have Brave Rewards enabled so you are seeing the privacy-protecting ads?
Aw come on with the misleaded hype, it’s a bit too frequent with that browser for some reason. Brave doesn’t include uBlock Origin, uBO is a add-on way more powerful and flexible than built in functionality of any browser. Brave just includes a list of things to block named uBlock, it’s a completely different thing.
One could install uBO in Brave and other tweaked Google/Microsoft Chromium browsers, but it’s most powerful in Firefox as the author details here:
https://github.com/gorhill/uBlock/wiki/uBlock-Origin-works-best-on-Firefox
Many of these privacy settings are enabled by default in Firefox 95, but some are not. And
‘network.cookie.cookieBehavior’ now has a value of “5”, which is unexplained here. I performed this test on Mac OS, with all telemetry supposedly disabled, Firefox continually writes to the following telemetry file (the “datareporting” folder within your profile):
/Users/{username}/Library/Application Support/Firefox/Profiles/{profilename}.default-release/datareporting/glean/db/data.safe.bin
I presume this information is being transmitted, since there is no reason to log reporting data otherwise. It seems like Brave is more secure in the default configuration, and Firefox really chews up the SSD. Session backups occur every 15 seconds when it should be 15 minutes. Wish there was an easier way to suspend tabs automatically & cache stuff in RAM.
[https://12bytes.org/articles/tech/the-mozilla-monster/]
There are extensions for unloading tabs such as Unload Tabs and Auto Tab Discard etc..
@Private 1: about ‘network.cookie.cookieBehavior’ now has a value of “5”
I was wondering about this too; I tried to look it up but at first couldn’t find the info.
When you enquired again I had another look.
I believe I found a useful resource (this link was supplied on reddit):
https://developer.mozilla.org/en-US/docs/Web/Privacy/State_Partitioning
“Dynamic Partitioning
To prevent JavaScript accessible storage APIs being used for cross-site tracking, Firefox partitions accessible storage by top-level site. This mechanism ieans(sic) that, generally, a third-party embedded in one top-level site cannot access data stored under another top-level site.
However, unlike Network Partitioning, this boundary is dynamic and access to a third-party’s unpartitioned storage can be granted”
“Disable Dynamic State Partitioning
To disable dynamic storage partitioning for all sites you can use the network.cookie.cookieBehavior pref:
Value Description
5 Reject (known) trackers and partition third-party storage.
4 Only reject trackers (Storage partitioning disabled).
0 Allow all”
My reading of the document is that FF tries to determine which 3rd party cookies etc are trackers and which are neccessary for web functionality;
The feature they use to do this is called, “Dynamic Partitioning.”
If a user wants to switch off Dynamic Partitionaing they can and block all(3rd Party)
Please read the article yourself, I am a learner.
If anyone in the RP community has a better resource or better reading please comment.
https://github.com/fork-maintainers/iceraven-browser
Hi @Dennis,
I believe you are asking the right questions. It is a very good question.
I recently went through Sven’s guide for Android:
https://restoreprivacy.com/secure-android-privacy/
And it was a good lesson for me on allowing permissions – be it extensions or apps.
@George from Canada’s (GFC) reply was a very good one. I would add that Ublock Origin is open source and recommended by Mozilla; this point is only extends the previous remarks by @GFC on trust; and adds a suggestion on how to form a ‘trusting’ point of view. With open source the trust is audited and distributed.
For the first time in over 10 years FF is not my default browser…been using LibreWolf for a couple months now and using Metager search. More hardened out of the box than FF it still needs some tweaks for more privacy. You have said often don’t install too many addons but I noticed some sites like AT&T really try to track you, with about 82 cookies. 17 Blocks from ClearURL’s, Adblock Ultimate screaming, Decentraleyes plus Privacy Pussum blowing up! Then I chexk out leak test/whats my ip type sites and get no leaks, browsers blocks pretty much all tracking, and I don’t stand out either. Not saying this is good thing to do but it works for me (have 15 addons) To that guy that says his window keeps resizing he should try Default Zoom addon he’ll be okay.
Hi @Ykcir,
I am keenly waiting on a RP LibreWolf review – I believe Sven said somewhere he said this was being considered.
With the addons, I believe some addons behave in a manner that can leave a signature. For example, have you ever encountered a site that detects that you are using an add-blocker and asks you to white-list their site? If you are using 15 extensions you maybe very unique because not many people are using those same 15 extensions – you maybe very unique.
The testing sites do not have the resources available to them that the tracking corps have to them;
Testing is great, I learn a lot from testing, but this is not necessarily proof against well resourced adversaries – it isn’t apples and apples. Do any testing sites test for your extensions?
I believe this is the basis of the caution against many addons.
Can they detect your extensions? I believe they can (not all).
Using many extensions to block trackers? I believe this may make you more unique.
I am very keen for a LibreWolf review;
Though I believe hypervisors are the only answer.
If you go to ip check at Jondo you really get to see what is showing on your browser to trackers, and there I do pretty good. Actually I been using FF hardening guides from Github, and make sure to read the ENTIRE guide, as there will be some good tips near the bottom. Check out any addons before installing them, and some don’t allow in private browsing mode. One thing I do like about LibreWolf is they don’t all the millions of updates like FF, because FF uses some of those updates to increase telemetry or some other form of tracking ( like activity history…thats part of a secure browser? ). Anyway I stand out as 1 in 8 browsera which is probaly about normal.
And on Youtube yes there are issues but I never allow cookies from them, just copy the URL’s and download the video or content from other apps or browsers.
You know I tried LibreWolf for awhile it’s a great browser but I was having some issues with YouTube where videos 720p and above would drop massive amounts of frames (seen under “stats for nerds”. This doesn’t happen on Brave, or Firefox… not exactly sure what that is all about but since I spend a lot of time on YouTube this was pretty depressing.
An interesting effort known as Arkenfox has been undertaken for a little over a year to make enhancements to Firefox using a user .js template in order to configure and harden the browser.
I am unsure how far along this project is and checked Firefox’s add-on repository. So far there is nothing that I can see or find out that has been produced. This may be in the early Beta or testing stages.
https://github.com/arkenfox/user.js
@Mike a very interesting read. You helped on my years resolution: to learn JS this year.
It’s aeons old, and up to date. You could hardly call it anything but mature.
The JS file itself is the “product”, it’s a set of about:config tweaks that are expected to be used with a few recommended add-ons to shield the user from fingerprinting and other tracking methods including vendor telemetry.
Though above all, it’s a comprehensive repository of Firefox about:config flags related to privacy and security. It’s the best the web has to offer on that front.