
One of the growing problems for computer users today is a swelling flood of tech support scammers trying to cheat people out of our money. Perhaps you have received phone calls and emails from these “tech support specialists” who try to establish trust in order to get the private information they need to scam you. While their ideal targets are less-experienced computer users and trusting senior citizens, even experienced computer users can fall victim.
Today’s world of lockdowns and social isolation is the perfect environment for tech support scammers. People working at home generally have less security in place. Additionally, people are also more exposed, with less access to legitimate technical support and corporate gatekeepers like receptionists who would prevent telephone scammers from even reaching us.
Law enforcement is on the case, but the crooks are running way ahead of the law in this area. For example, on March 3, 2021, the Consumer Financial Protection Bureau (CFPB) filed a lawsuit in federal court against BrightSpeed Solutions Inc. (BrightSpeed) and its former CEO, Kevin Howard. Why? Because the company knowingly processed payments for companies engaged in internet-based technical-support fraud.
This is good news. However, the crimes alleged against the defendants took place between 2015 and 2019! It falls to each of us to identify and avoid tech support scams ourselves. Fortunately, as you are about to learn, it isn’t that hard to do, once you know the tricks the scammers use.
How to spot tech support scams
While tech support scammers can be very creative with their specific scams, they tend to fall into one of three broad categories:
- Phone calls
- Pop-ups
- Search results and ads
Spotting these tactics will help you avoid falling for the scam. So let’s look at each one in some detail.
1. Phone calls offering support services
To pull off this caper, tech support scammers cold call people pretending to be computer technicians from big-name companies like Microsoft or Apple. They’ll claim that they have somehow identified a problem with your computer.
Assuming you don’t hang up on them immediately, they’ll launch into a prepared script designed to convince you that there really is a problem with your computer. Scammers are often skilled at social engineering (also known as social hacking or simply manipulating people).
One common approach is to try to convince you to give them remote access to your computer. Once you do that, they will run some kind of fake diagnostic test. After they ‘fix’ your system, they’ll try to get you to pay them for fixing your system.
While you are arguing with the scammer about money, they’ll probably be installing some kind of malware on your computer which will make your life miserable and potentially send the scammers your private data. This, in turn, can lead to other financial fraud and identity theft. Nothing good will ever come from dealing with these guys.
How you can avoid getting taken in by tech support phone scams
First, realize that these creeps are good at what they do. They can trick your caller ID to make it look like they are calling from Microsoft, Apple, or any other company. They are skilled at talking people into doing things they really shouldn’t. You really don’t want to interact with them at all.
So don’t.
If you get a surprise phone call from someone who says there’s a problem with your computer, hang up on them. It isn’t rude. It’s smart.
Think of it this way: No reputable company is going to call you on the phone to tell you they’ve been snooping around on your computer without your permission and spotted a problem they want to fix.
2. Pop-up warnings about some kind of “problem”
Another attack vector for tech support scammers is through pop-up windows that suddenly appear on your computer screen. They frequently look like error messages from your operating system or anti-malware software. They might include the logo and color scheme of a big-name company or of some software you have installed on the computer. In other words, they look legitimate (at least at first).
Besides the error message, the pop-up will include a phone number you can call for technical support. In other words, it will probably look like the image below. It’s an example of a technical support scam pop-up from the United States Federal Trade Commission (FTC) website:
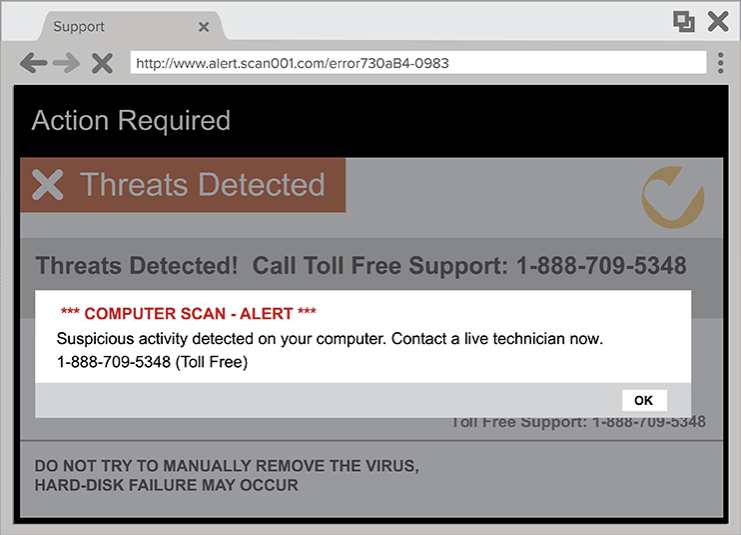
If you call the phone number shown in the pop-up, you’ll find yourself talking to the same kind of scammer that cold calls innocent victims. A smooth, skilled manipulator who is going to do his or her best to talk you into doing something you will really regret later.
Perhaps you are wondering how the bad guys get these pop-ups to appear on your screen? There are two ways.
The first is when you visit a website that has links to a malware site that displays the pop-ups. The link will look like something useful, probably related to the content on the web page. You click the link to get something useful, and instead you get scammed.
Scam pop-ups can also appear if the website you are visiting has been infected with malware, or if your computer has. If you see one of these pop-ups, something bad is definitely going on.
How you can avoid tech support pop-ups
While seeing one of these pop-ups is a bad sign, it doesn’t necessarily mean that your computer is compromised. To avoid problems, first realize that legitimate companies will never pop up an error message with a phone number for you to call. So don’t call the phone number!
Second, realize that any link in a technical support scam pop-up is unlikely to lead to anything good. So never click any links in a scam pop-up!
Doing those two things should protect you from additional problems. What I would do is make note of the website you were visiting when the pop-up appeared. Don’t visit that site anymore. It is either infected with something bad, or careless about who it lets post ads on the site, or somehow benefiting from letting the scammers do their dirty deeds on the site.
So make a note not to visit that site anymore, then close the browser window. Finally, reboot your computer and run a virus scan to make sure nothing nasty got past your defenses and into your machine.
Scan a site (or file) for malware
While we’re on the topic of malware on websites, let’s discuss a great tool you can add to your digital toolbox. That is VirusTotal. This is a website that allows you to scan websites or files for malware.
Simply go to the VirusTotal website, enter the website’s URL (or file) and then click scan.

VirusTotal will then scan the file or website with a large selection of security vendors to reveal any positive test results. You may find some false positives when using VirusTotal. I have seen some security researchers identify a file as malicious if it is flagged by three or more vendors in the VirusTotal test.
3. Online ads and listings in search results pages
This scam is slightly different in that you initiate the action. If you have a problem with your computer, you might think to do a search, or to call the number in some tech support ad that you happen to see. While dealing with a problem on your computer is of course a very good idea, dealing with it by dialing a phone number from some ad or search result is probably a bad idea.
You might think that search engines would prevent tech support scammers from appearing in their search results. But this is not the case. Similarly, ad networks also do not do a good job filtering out the scammers. The details vary, but in every case, the scammers provide a phone number for you to call for help.
We’ve already seen how things go if you call the phone number they provide. Some snake will get to work trying to convince you to do something that’s going to hurt.
How to avoid support scams from ads or search results
The answer is once again the same: don’t ever call the phone number that shows up in an ad or search results.
- If you think you have a problem with your computer, contact the manufacturer or the store you bought it from through their official website or support channel.
- Likewise, if you think you have a problem with the software on your computer, contact the publisher through their official website.
As long as you are on a company’s official website, you should be safe from tech support scams regardless of the listed contact methods you choose to use.
Conclusion: You can identify and avoid tech support scams
Scammers are really happy that so many people are being forced to work at home. This makes them more vulnerable to various types of attacks, including all sorts of tech support scams. In this article we looked at the three main types of tech support scams: phone calls, pop-up boxes, and online ads or search results.
We covered how you can identify each type of scam and how you can avoid being taken in by them. Follow the advice we’ve given you to avoid becoming one of the thousands of people who fall victim to tech support scams every year.

Leave a Reply