
Your personal data might be the most valuable commodity in today’s world. Microsoft (and most other big tech companies) likes to collect as much data as they can about how you use your computer. We want to keep as much of our data private as possible. They do this, often without your express permission, relying on long, confusing privacy policies and terms of service that most of us don’t read and wouldn’t understand anyway. By default, Windows 10 gathers large amounts of your personal information. If you value your privacy, it only makes sense to take what steps you can to minimize the amount of information they can gather.
For this article, I used Windows 10 Home, version 1909, the Windows 10 Anniversary Update.
Almost everything we will do today takes place in Windows Settings. Let’s not waste any time and head directly over to Windows Settings. To get there, click Start, then Settings.
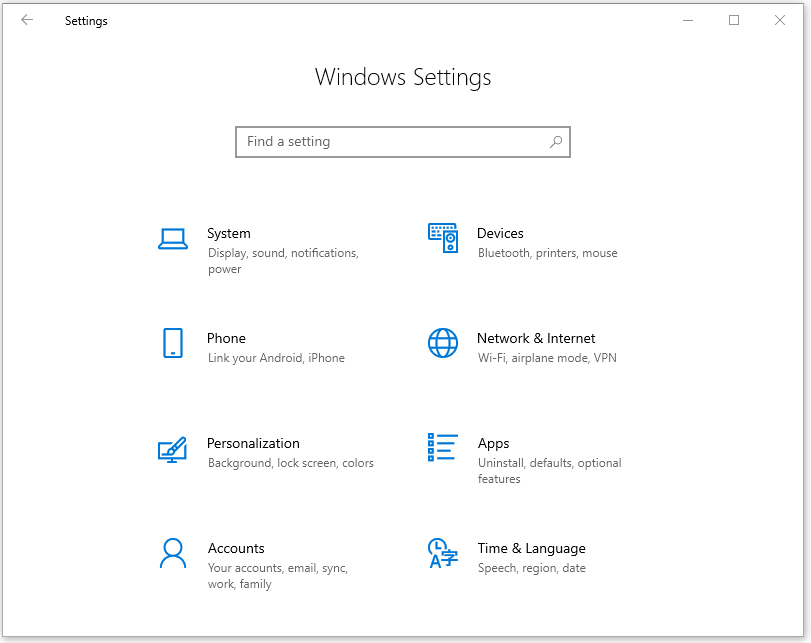
From here we can make the following changes, which we will methodically cover below.
- Put limits on Cortana
- Make privacy-friendly apps the default apps
- Eliminate unwanted startup apps
- Tweak Sign-in options
- Adjust General privacy settings
- Practice safe Wi-Fi
- Control Diagnostics & feedback
- Limit Delivery optimization
- Keep your activity history to yourself
- Set app permissions for maximum privacy
- Make Windows stop hiding stuff from you
We’ll also discuss using Windows in virtual machines (VMs) for more privacy and security.
1. Put Limits on Cortana
Cortana is the digital assistant built into Windows 10. It is also perhaps the feature most hated by privacy advocates. Why? Because of the huge amounts of personal data that Cortana scoops up and the way it shares your personal data with Microsoft. I’m not here to bash Cortana. I’ll simply say that most people who value their privacy want to shut Cortana down completely.
Unfortunately, one of the changes Microsoft made in the Windows 10 Anniversary Update was to eliminate the option to shut Cortana down completely. It seems that they really want us to use Cortana, whether we want to or not. While there are some technical tricks to completely disable Cortana, they are beyond the scope of this article.
What we are going to do here is everything we can do to prevent Cortana from functioning, without resorting to hacking the registry or creating local group policies.
On the Windows Settings page, enter Cortana into the Find a setting box. You should see a list of search results that looks something like this:
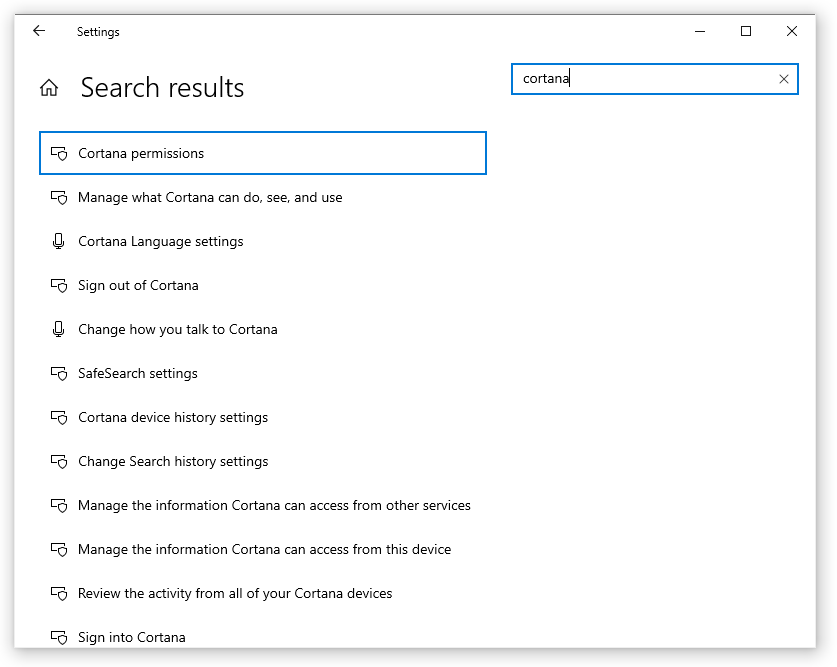
Select Cortana permissions. On the Permissions page that appears, click the Manage the information Cortana can access from this device link. On the page that appears, you can cut down on what information Cortana can see and use. Since we want to disable Cortana to the maximum extent possible, I suggest you turn off everything: Location; Contacts, email, calendar & communication history; and Browsing history.
Next, scroll down the page and click the Speech privacy settings link. While it is very cool that Windows 10 can understand spoken commands, the way speech recognition works is a privacy risk. Cortana and some other apps rely on online speech recognition capabilities provided by Microsoft. That means that they listen to what you say and send it to Microsoft to be analyzed. Indeed, Microsoft says that they, “will use your voice data to help improve our speech services.”
Unless you want to trust Microsoft not to misuse your voice data, I suggest you disable online speech recognition. This will prevent Cortana and some other apps from responding to voice commands, but eliminates a major privacy risk. Note that the Windows Speech Recognition app and some other speech services will still work, since they don’t rely on online speech recognition.
Hide the Cortana button
We’re almost done. Since we don’t want Cortana to do anything, it only makes sense to remove the Cortana button from the Windows taskbar. Here’s how you do that:
- On the Windows desktop, right-click the taskbar.
- In the menu that appears, clear the Show Cortana button option.
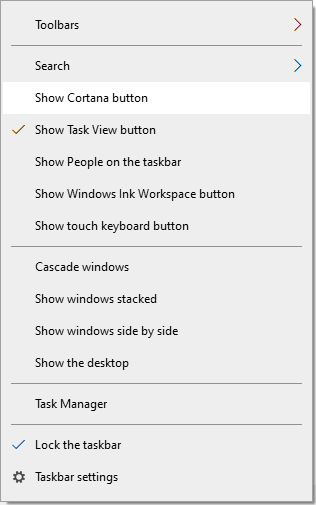
While Cortana will still be there, these simple changes should minimize the privacy risk she poses.
2. Make privacy-friendly apps the default apps
Not surprisingly, Windows 10 comes with Microsoft apps set as the default for various functions, including email and browsing the web. If you’ve started using privacy-friendly apps for these functions, you can tell Windows to use them as the defaults for these functions. To see how this is done, let’s configure Windows to use Firefox as my default browser, instead of Microsoft Edge. Note that the desired app needs to already be installed on your computer. Privacy-friendly apps tend not to be available in the Microsoft Store.
To change a default app, follow these steps:
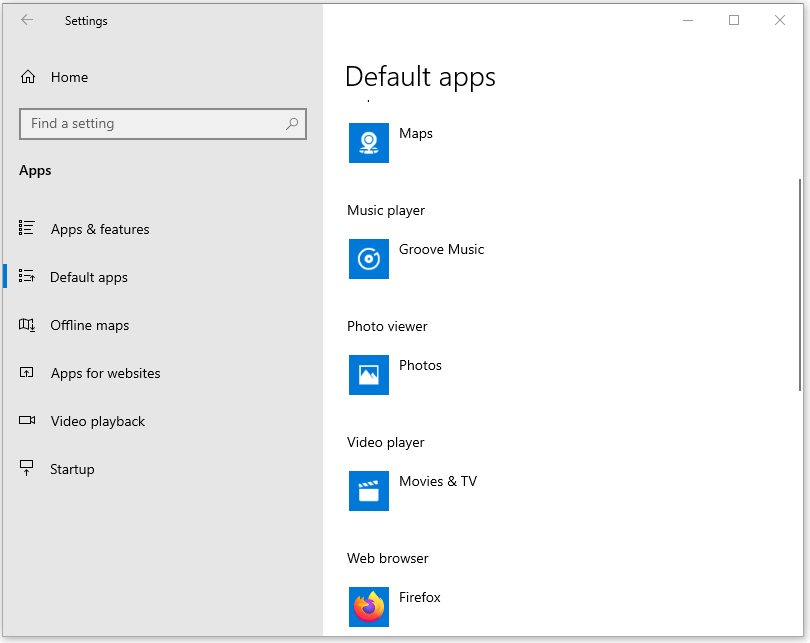
- In Windows Settings, select Apps. This opens Apps & features.
- In the menu on the left side of the window, select Default apps.
- Under Default apps, scroll down and select Microsoft Edge (the current web browser). This opens the Choose an app list.
- The list displays all the installed web browsers. Select Firefox from the list and wait a moment. Firefox will now appear in the Default apps list.
Note: We like Firefox because it is a privacy-respecting browser that is also highly customizable. See our Firefox privacy modifications guide.
3. Eliminate unwanted startup apps
Some apps automatically start when you start Windows. Let’s make sure that you are in control of the apps that start automatically when Windows starts, since the odds are excellent there will be at least one that is not privacy-friendly.
To control which apps start automatically when Windows starts, select Startup in the menu on the left side of the Apps window. A list of the apps that are currently starting automatically appears on the right side of the window.
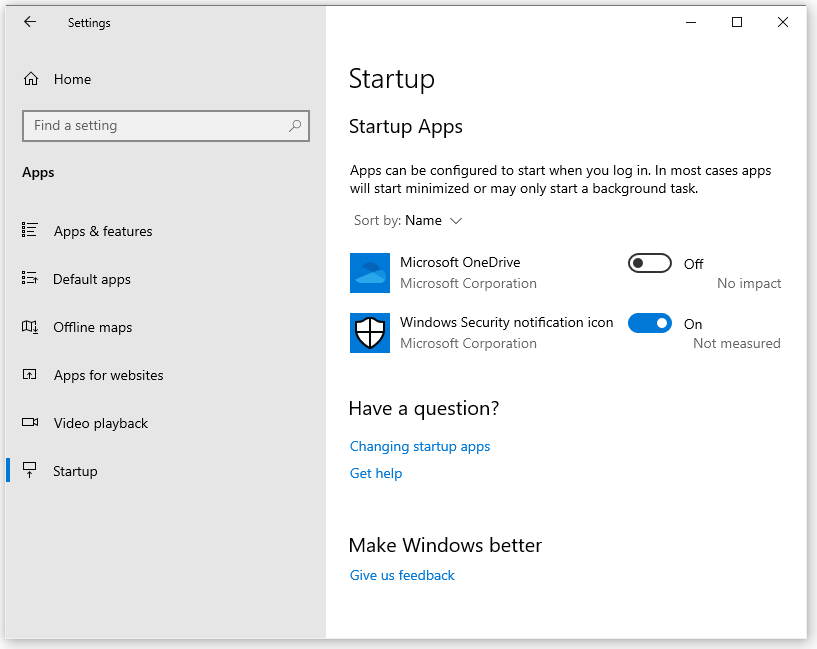
One startup app I suggest you always disable is Microsoft OneDrive (I did so in the image above). If you need OneDrive style (cloud) storage, I suggest you install a privacy-friendly cloud storage app like MEGA or Tresorit, and use that in place of OneDrive. (We have other cloud storage reviews as well.)
4. Tweak Sign-in options
Windows does a couple of things here that are not great for privacy. Follow these steps to tweak the Sign-in options:
- In Windows Settings, select Accounts. This opens Your info.
- In the menu on the left side of the window, select Sign-in options.
- Under Sign-in options on the right side of the window, scroll down to Privacy.
- Set both Privacy options to Off.
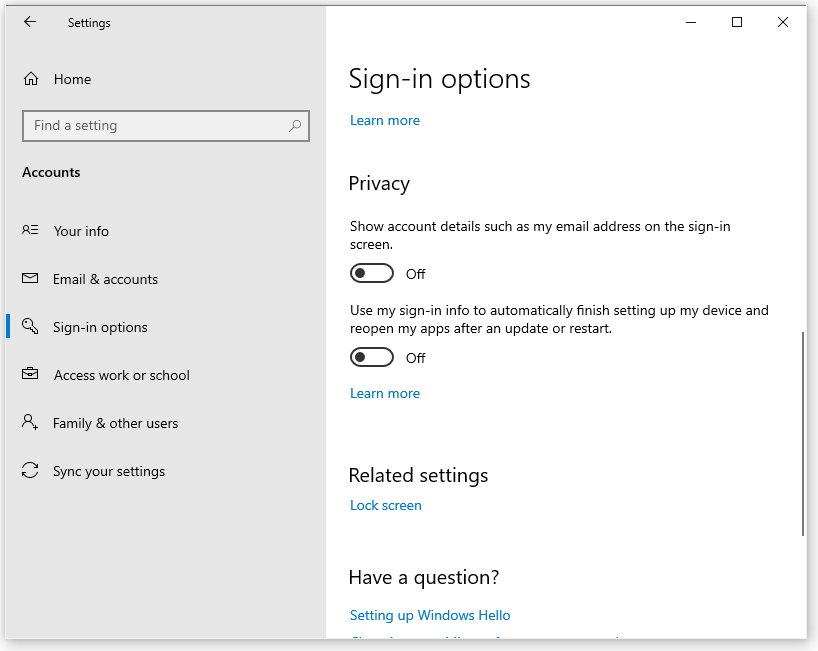
The Show account details… option should be off by default. You want to turn off the Use my sign-in info to automatically finish setting up… option to prevent Windows from signing you in on its own. With that option set to On, you could be away from your computer and Windows could sign-in and launch apps on its own, leaving you totally exposed to anyone who happens to be passing by.
5. Adjust General privacy settings
Now we need to get into the Privacy section of Windows Settings. We’ll just start at the top with the General privacy settings.
To adjust Windows 10 General privacy options:
- In Windows Settings, select Privacy. This opens the General privacy page.
- The best thing to do here is simply to turn off all of these options. They all involve allowing Microsoft to gather information about what you do while in Windows 10. You don’t need any of these to use the product. Leaving any of them turned on simply helps Microsoft build a bigger profile on you.
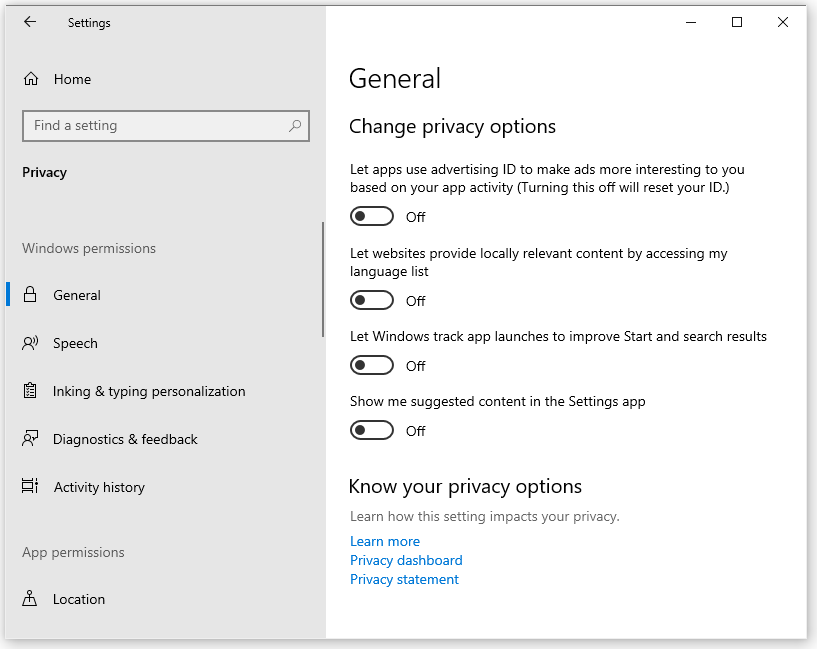
If you would like to learn more about what each of these options does, you can check out this General privacy settings in Windows 10 page.
6. Practice safe Wi-Fi
Do you remember the days before Wi-Fi? The bad old days when our computers needed to be connected to the rest of the world by wires? Wi-Fi makes life much more convenient. But it also can be a privacy risk. Here are the changes I suggest you make to Windows 10 Wi-Fi settings to maximize your privacy.
Settings on the Wi-Fi page
There are a few changes to make on the main Wi-Fi page. We want to enable the use of random hardware addresses and disable Hotspot 2.0 networks. One of the things that Wi-Fi transmits while looking for available networks is your system’s physical MAC address. In some places (a shopping mall, for example), the MAC address could be used to track your movements, when you visit the place, and so on. Random hardware addresses, if supported by your Wi-Fi hardware, send out fake MAC addresses when scanning for networks. This would make it much harder to track you.
Hotspot 2.0 is a standard that is meant to make using wireless hotspots more like using your mobile phone. As you move around in the world, your phone automatically selects new cellphone towers so you can stay connected. Hotsport 2.0 is meant to do the same for wireless hotspots that support the standard. This standard hasn’t become widely accepted yet, and I’m not convinced that it is a safe way to use Wi-Fi. I suggest you shut it off.
To change these settings on the Wi-Fi page:
- In Windows Settings, select Network & Internet.
- In the left-hand menu, select Wi-Fi. This opens the Wi-Fi page.
- Turn on Use random hardware addresses.
- Scroll down to Hotspot 2.0 networks and turn that Off.
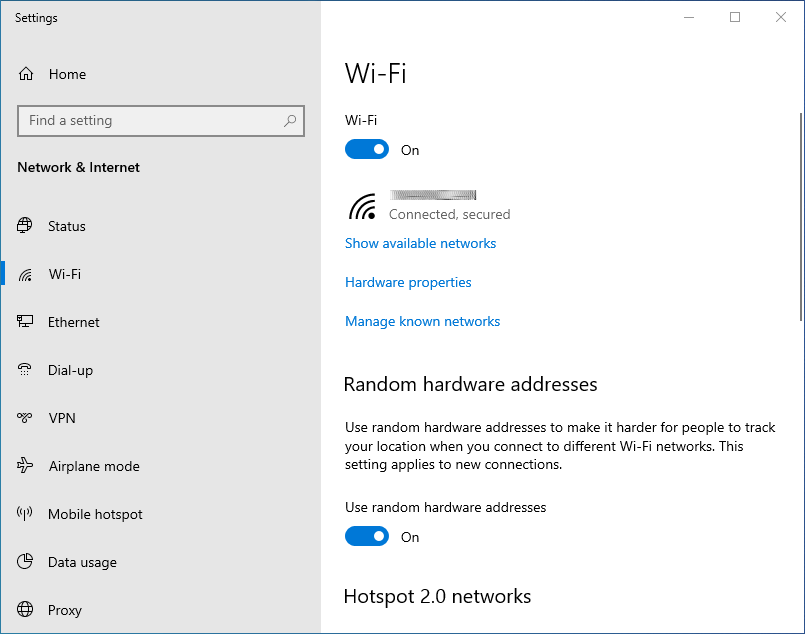
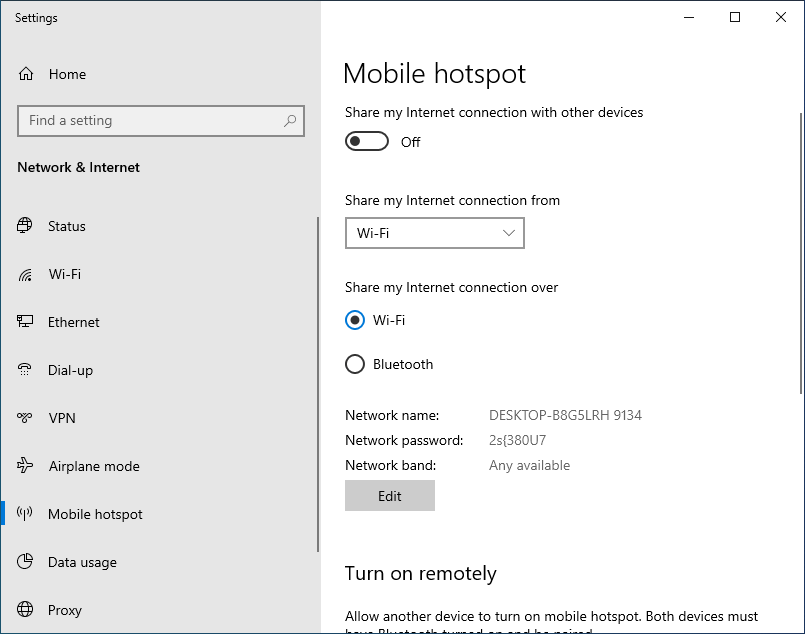
Next, I suggest you make sure that the Mobile hotspot feature is turned off. When on, this turns your computer into a hotspot that other devices can log into for Internet access. This makes it another point of attack for a hacker. Normally, this feature will be off by default, but it will only take a second to check.
Select the Mobile hotspot menu option on the left side of the page and make sure it is set to Off.
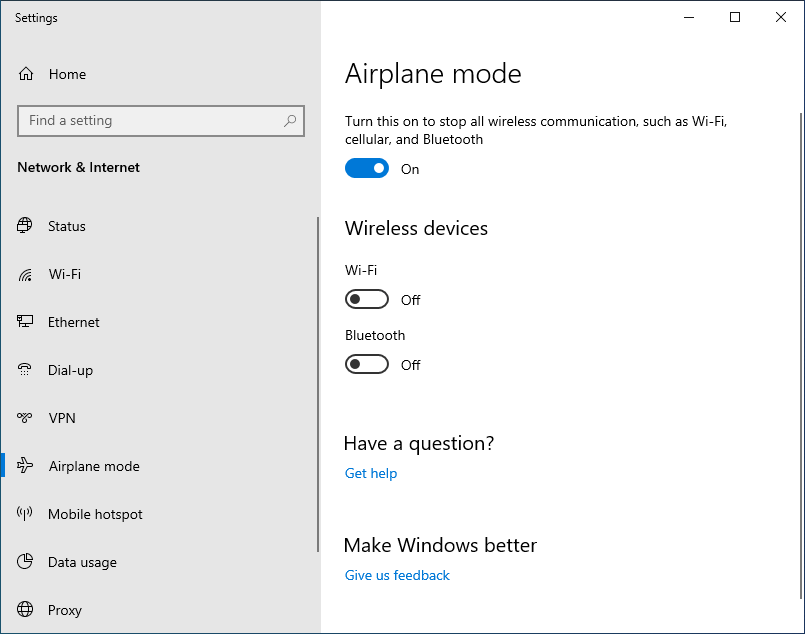
If you are using a wired connection to the Internet you can really fortify your system by turning on Airplane mode. In this mode, all your system’s radios are turned off, making it impossible for anyone to get into your system wirelessly. The radios this affects include not only Wi-Fi, but Bluetooth, and if your device has the ability, cellular access.
To go into Airplane mode, simply select that option on the left side of the window and turn it On.
7. Control Diagnostics & feedback
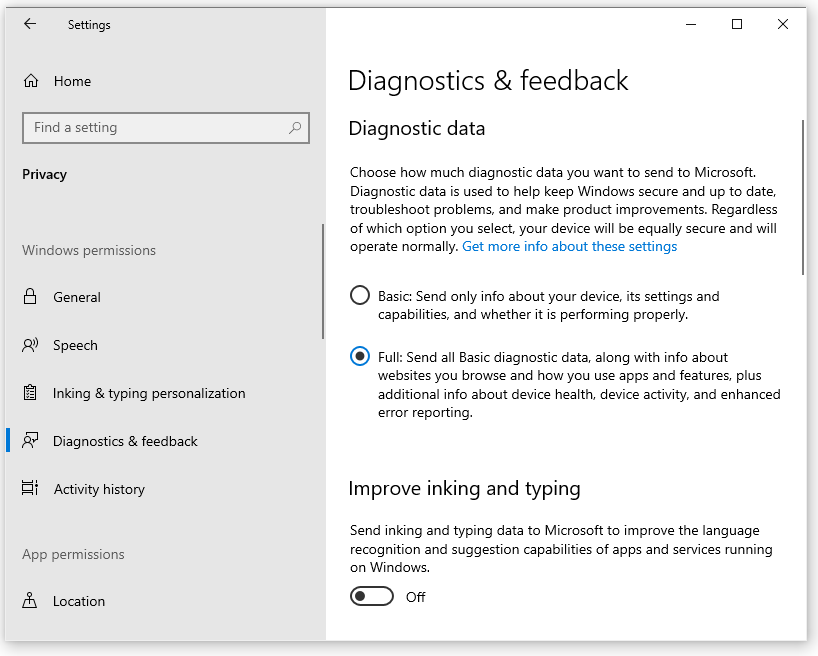
As much as possible we want to limit the information we send to Microsoft. To do that, we need to change a couple of settings on the Diagnostics & feedback tab. Here’s what you need to do:
- In Windows Settings, select Privacy.
- In the menu on the left side of the window, select Diagnostics & feedback. This opens the Diagnostics & feedback page.
- Under Diagnostic data, select Basic. This prevents Windows from sending Microsoft personal data like the websites you visit and which apps you run.
- Under Improve inking and typing, turn off the option to send inking and typing data to Microsoft.
The less data you send the better.
8. Limit Delivery Optimization
Windows 10 can do some tricks to possibly download updates faster. It does this by pulling update information from locations other than the Microsoft website. Specifically, it can pull updates from other machines on the local network, as well as other computers on the Internet. The idea is to share the load of downloading Windows updates.
I am not a fan of this approach. You should have your Windows installation well-protected from viruses and malware, but downloading updates from other computers on the network or even random machines on the Internet is just an invitation for trouble.
Add in the fact that allowing downloads in this manner also means that others can download parts of their updates from your computer. Windows should handle all of this automatically and safely, but you have to trust that they will do it right. The potential for privacy and security problems isn’t worth the possible time savings.
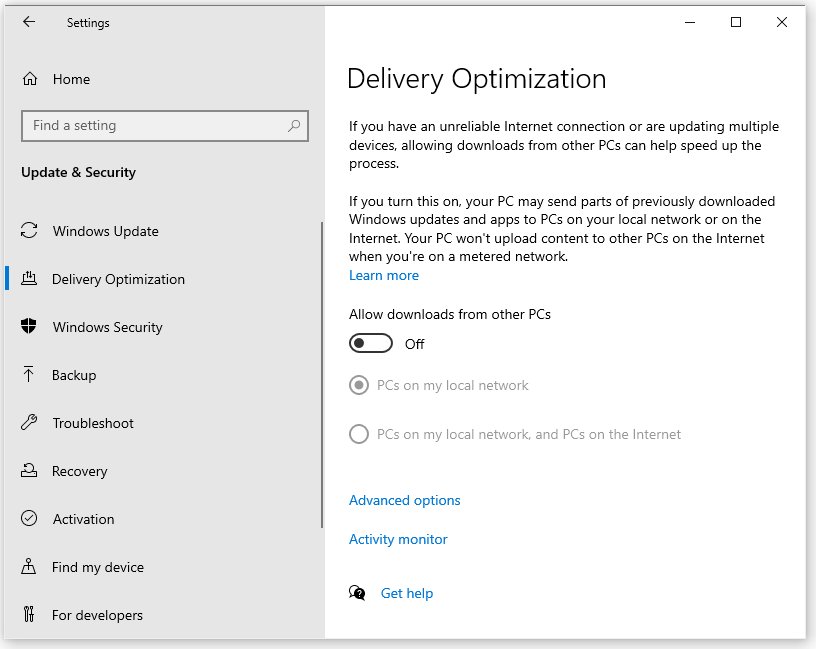
To make sure Windows 10 only takes updates directly from Microsoft, follow these steps:
- In Windows Settings, select Updates & Security. This opens the Windows Update page.
- In the menu on the left side of the window, select Delivery Optimization.
- Under Allow downloads from other PCs, set Allow downloads from other PCs to Off.
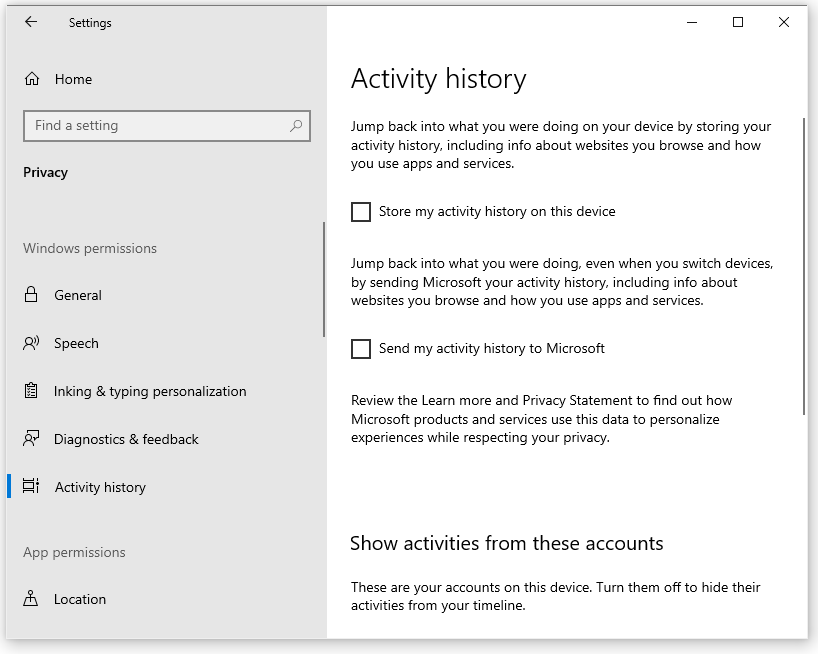
9. Keep your activity history to yourself
Windows 10 can keep track of your activities for you. This “activity history” includes things like information about the web sites you visit and the apps and services you use. This information gets fed into the Timeline, and gives you a way to go back to what you were doing in the past 30 days. By default, Windows tracks your activity history. It also sends your activity history to Microsoft so you can use it on other devices.
From the privacy perspective, I’m not sure I would want Windows 10 to record all my activities in this way, but you might find it useful. But I’m sure I wouldn’t want it sending this data to Microsoft. Follow these steps to control your activity history;
- In Windows Settings, select Privacy.
- In the menu on the left side of the window, select Activity history. This opens the Activity history page.
- Uncheck the Store my activity history on this device option unless you have a good use for it.
- Uncheck the Send my activity history to Microsoft option.
- Scroll down to the Clear activity history section and click the Clear button for any accounts that don’t need their activity history saved by Windows.
10. Set app permissions for maximum privacy
Windows apps often need (or simply want) access to data that many people would consider private. For example, one app might want access to location information so it can provide you with ads for nearby restaurants. Another might want to see your contacts, or control your webcam, or look at your call history. Apps may have perfectly legitimate reasons for the permissions they request, but you need to decide whether you want any particular app to have access to the private data it requests.
In this section of the guide, we’re going to hit the various types of app permissions that are available. I’ll tell you how to turn them on and off, and give recommendations as necessary.
But before we do, let me clear up one thing. As we work our way through the settings, you are going to see references to “desktop apps.” Microsoft distinguishes between desktop apps and other types of apps. Among other things, desktop apps may not be controlled by the Windows 10 privacy settings we are about to look at. So what is a desktop app? Here’s what Microsoft says:
What are desktop apps? They’re usually downloaded from the internet or installed with some type of media (such as a CD, DVD, or USB storage device). They’re launched using an .EXE or .DLL file, and they typically run on your device, unlike web-based apps (which run in the cloud).
Desktop apps play by different rules than other apps when it comes to privacy. That means you’ll need to scrutinize the privacy policies of each one individually. It also means that Windows privacy settings may not protect you if you install desktop apps from dubious sources. To learn more desktop apps and privacy, check out this page.
Control access to location data
When turned on, Windows uses your computer’s capabilities to determine your location. Microsoft uses this information to improve its location services. Windows uses this information for various features, as well as sharing it with apps. At times it can be useful for Windows and certain apps to know your location. But do you really want Windows constantly checking your location and sending it to Microsoft?
Happily, Microsoft gives you a good bit of control over when, how, and by whom location data is used. You can:
- Turn off location completely, meaning Windows doesn’t use your computer’s capabilities to figure out your location, period.
- Control which apps, if any, have access to location data.
- Set a default location for use when better data is not available
- Clear the location history stored on your device
You do all this from one page, so let’s go there.
In Windows Settings, select Privacy. In the menu on the left side of the window, select Location. This opens the Location page.
- If you want to prevent Windows, Microsoft, and any apps from calculating your actual location, under Allow access to location on this device, click the Change button, and set Location access for this device to Off.
- If you left location on, you can still prevent apps from using the data. Under Allow apps to access your location, set the switch to Off. Desktop apps may ignore this setting.
- If you wish, you can set a default location that Windows, apps, and services can use when they don’t have any better data. Under Default location, click the Set default button and select a location.
- Scroll down a bit more to see the Location history section. If you want to erase the location history information that is currently stored by Windows 10, hit the Clear button.
- Finally, if you are allowing apps to have access to location data, you can still select which apps have access. Scroll down a bit more and you will see a list of apps, along with switches that tell you whether that app has access to location data. Unless you can think of a specific reason why an app should have access to your location, set the switch for that device to Off.
Windows 10 location settings can be confusing. If you want more information on location and the privacy implications, visit this page.
Control access to the camera and microphone
You control permissions for access to the computer’s camera and microphone the same way you control access to location data. The pages are laid out the same, except that there is an additional switch for each of these. You use that switch to prevent desktop apps from using the camera or microphone.
However, even if you turn this off, some desktop apps may still use the camera or microphone. Note also that it has long been reported that the NSA and others have the ability to turn on your computer’s camera and microphone remotely. So is there a way to really prevent the use of the built-in camera and microphone on your Windows 10 computer? Maybe.
You may not be able to prevent a hacker from turning on your computer’s camera, but you can keep it from being useful to them. How? Cover the camera lens. Putting a piece of opaque tape or some sort of sticker over the camera means it won’t be useful for spying on you.
The microphone is a bit more tricky since blocking sound from reaching it isn’t as easy as putting a piece of tape over the input. I’m not an expert on this, but I have seen one suggestion that seems like it might work. The trick is to cut the microphone jack off an old headset or another device, then plug that jack into the microphone input on your computer. Reportedly, inserting this (now non-functional) jack into the microphone input will physically disconnect your computer’s internal microphone.
Control other types of app permissions
There are lots of other things that apps might do to violate your privacy. Controlling app permissions for these things works very much like controlling app permissions for location data. I don’t want to waste your time repeating virtually identical steps over and over for each type of permission. Besides, Microsoft provides pretty detailed explanations of what the permission is for and what each individual control does on each page. Instead, I will list each permission type, and give my suggestions on what to do about them to maximize your Windows 10 privacy.
When in doubt, I suggest you disable a permission completely by clicking the relevant Change button and setting the switch that appears to Off. If an app that is important to you complains, you can always turn the general permission back On, then under the Choose which app can access your… heading, turn Off the permission for every app except the one you need.
- Voice activation – Allows you to activate speech recognition without having to first hit a key or click the mouse. I would turn this off and rely on the keyboard and mouse instead of having Windows constantly listening in case you happen to be talking to it.
- Notifications – Shut it down completely.
- Account info – If you are using any of the default Windows apps such as Microsoft Edge, I suggest you use the Choose which apps can access your account info option and turn On only the specific apps you use. An even better move would be to stop using any default Windows apps, and instead choose privacy-friendly ones like those listed in the Restore Privacy Recommended Privacy Setup on the bottom of this page. (See also our best password managers guide.)
- Contacts – Lots of default Windows apps want access to your contacts, although I don’t know why apps like Maps and Microsoft Photos would need this information. Check the list of apps looking for this permission, and if you aren’t using any of them, completely disable this permission.
- Calendar – Check the list of apps looking for this permission, and if you aren’t using any of them, completely disable this permission.
- Phone calls & Call history – If you have a phone linked to this computer, these permissions allow apps to make phone calls using your computer and to look at your call history. The People and Messaging apps built into Windows 10 always have permission to at least make phone calls, so I would disable this permission completely to prevent other random stuff from using your telephone.
- Email & Tasks – Disable both of these completely. The Windows 10 Mail and Calendar apps have access to this information whether you disable permissions or not. Few types of data contain more private information than your email. (Use one of our recommended secure email services that respect your privacy.)
- Messaging – Similar to the Phone calls setting, enabling this allows apps to send and receive text or MMS messages using a phone connected to your computer.
- Radios – You really don’t want random apps to be able to turn your computer’s radios (typically WiFi and Bluetooth) on and off. I would disable this permission completely, and turn the radios on and off manually. (See our guide on Controlling Communication Channels for a deep dive on this topic.)
- Other devices – Unless you wirelessly connect your computer to your Xbox One or some other device, disable this completely. If you do connect to other devices, don’t turn this off but check the list of devices that want this permission to make sure you don’t allow some rogue app to wirelessly talk to who knows what device within radio range.
- Background apps – This one you probably will not want to disable completely. This permission allows apps to run in the background. That is, allows them to run when you are working in another app. If you disable this completely, apps like your music player, Skype, and your mobile data plan won’t work in the background. This is one permission I suggest you leave enabled, but turn off for any individual apps you don’t want running in the background.
- App diagnostics – This allows apps to access diagnostic data from other apps. I would disable this completely.
- Automatic file downloads – This controls whether Windows can automatically download files from your online storage provider for apps that request them. If you are using online (cloud) storage, I suggest you start by switching to one of our recommended secure cloud storage services. Once that is done, return to this option. Leave this permission enabled, but turn it off for any app that requests it except for the secure cloud storage service you are using.
- Documents – This gives apps access to your documents library. I wouldn’t disable this completely, because if you do, Windows Defender won’t be able to scan the documents library for infections. I suggest you leave it enabled, and turn off access to individual apps, being sure to leave it turned on for Windows Defender.
- Pictures & Videos – These two permissions grant apps access to your pictures library and videos library respectively. I would disable both completely and see if anything you actually use squawks about it.
- File system – This one gives apps access to all of your files and libraries. If you use Microsoft Office, you need to leave it enabled and turn off access to individual apps, being sure to leave it turned on for Office.
11. Make Windows stop hiding stuff from you
By default, Windows 10 hides many things from you. It hides the extension on some types of files, it hides certain programs, and it hides entire folders. I think the idea is to save you from worrying about the extensions, and to keep you from poking around at Windows 10 stuff Microsoft doesn’t want you messing with.
There are various problems with this approach, including a potential privacy issue. If an attacker penetrates your computer’s defenses, they are likely to install malware on the machine. Allowing hidden files and folders on your system could give the malware a place to hide.
Another way to hide stuff on your computer is to give it the same name as a legitimate file, but with a different extension. For example, this might be an executable file on your system named, “happy-birthday.jpg.exe.” With file extensions turned off, that would look like, “happy-birthday.jpg,” possibly making you think it was a nice birthday photo. Instead of seeing a photo, double-clicking it would run the program, “happy-birthday.jpg.exe,” which could do something bad to your computer.
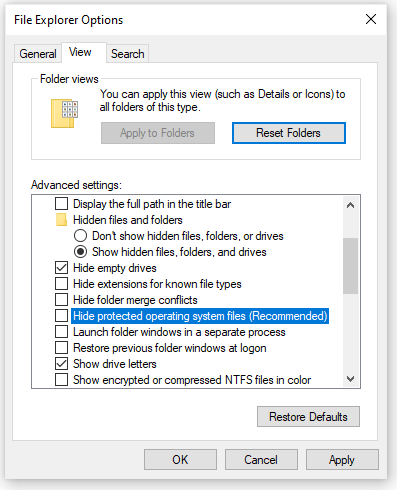
Follow these steps to make Windows stop hiding stuff from you:
- Using the Windows search box, search for and open: file explorer options. This opens the File Explorer Options dialog box.
- Select the View tab.
- Under Advanced settings, set the Show hidden files, folder, and drives option.
- Uncheck Hide extensions for known file types.
- Uncheck Hide folder merge conflicts.
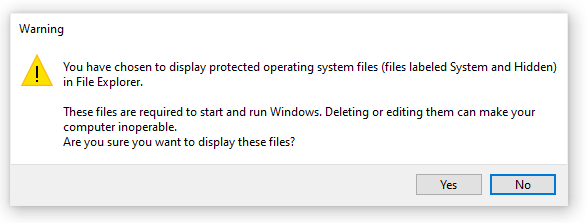
- Uncheck Hide protected operating system files (Recommended). Windows will object to you doing this by displaying the following warning.
- Go ahead and do it anyway (select Yes). Just remember not to mess with the files that are revealed unless your computer is compromised and you have no other choice.
- Click OK to exit.
Using Windows in a virtual machine for more privacy and security
Many people need to use Windows for work or to access specific applications. Therefore the “Switch to Linux!” advice may not hold water for Windows-critical tasks. With that being said, there are still some good options for this situation.
One recommendation we often stress here on Restore Privacy is to use virtual machines (VMs). A VM is basically a virtual operating system running on your (host) computer. This is very easy to do, and it’s also free with Virtualbox.

One of the big advantages of using VMs is that it gives you a strictly isolated environment to run Windows, which is separate from the rest of your system. This allows you to run Windows in a VM on a host computer, which could be running a privacy-respecting operating system, such as Linux.
You can get started by simply downloading Virtualbox for your host operating system (available for Windows, Mac OS, and Linux). Then, download the operating system you want to use, in this case, Windows 10. Then you can go about setting up your Windows 10 VM (there are many tutorials for this).
Note: Both Windows 10 and Virtualbox are free, and you don’t need to register your Windows 10 version. Then, whenever you need Windows for specific tasks, simply fire up your Windows 10 VM.
With this method, Windows will be safely secured and isolated from the rest of your operating system, data, and files.
Conclusion on Windows and privacy
As you can see, there are many things you can do to improve your privacy when using the latest version of Windows 10. While users of the home edition can no longer turn off Cortana without fooling around in the Registry, we can rein in Cortana to some extent, thereby minimizing her access to our personal data. We’ll have to wait and see the impact that the upcoming changes to Cortana have, but hopefully they will give us back a little more control over her.
While this guide was mainly focused on configuring your Windows settings for more privacy, there are other considerations as well. For example, a good VPN service will encrypt internet traffic between your Windows computer and a VPN server, while also hiding your IP address and location. We cover the best VPNs in detail on this site. There are also other privacy tools worth considering as well.
What Windows 10 privacy tricks have I missed? Let me know in the comments.

I’m waiting on updating my PCs from Windows 10 to 11 until I read what you have on it. (And believe me, they’re both nagging me to update!) Hoping that a Windows 11 overview finally comes out sometime this year.
Good Buy Windows 7pro you were 1 sweet sailin surf board – especialy enjoyed these last couple years @ no anti virus since emsisoft ended their 7 support. Both my daily drivers ran 7pro +Defender +mod FireFox +Proton +Nord +AdGuard +Bitwarden = 0 virus, 0 malware, 0 issues gotta say i am gonna mis only accepting the 1 quick 2-3mb update every few days…. I almost set updates to automatic…. almost(woulda worked & been even sweeter)but good habits die hard. Started the process last month dual bootin 7+10 on pc1 & 7+Mint on pc2.
Mint is feelin better Win10 made me hate B Gates a lil more every day.. lol ThankGOD right about the time i learned Firefox & Brave are finally set to end their support of win7 i discovered *RevoUninstallerPro5-Portable* & presto 10 is now sleek&shiny new win surfboard – took just a few clicks & was “by by” one drive, “addyOs” cortana, “out ya go” edge…. literally 1click to pic Uninstall, 1 sets a restorepoint & 1 backs up full registry! Then after uninstall 1click starts a full scan for any leftover registryfiles & cleans up everything else related on its way out leaving nothing behind. Next up i used Revo with INSTALL (yes it’s all that & a bag-o-chips) SafingPortmaster for a “glasswire-on-steriods” total network monitor-advanced-control firewall built ground up around the vpn’s new replacement…………..enter *SPN* O YA! Thats right! “Rock out with with your **** out!” hang 10 on a win10 😉 all is good i got this – SURF IT NAKED BABY! ………………… ok ok ok im awake back to reality its a big ocean w big fn fish! game on players
There is also a tool called O and O [https://www.oo-software.com/en/shutup10]. , and it helps with disabling those features of windows that you don’t want. Also to monitor and block apps that you don’t want to have pc network activity you could use [https://safing.io/portmaster/].
same. but you can also get there by going to Apps > Apps & features
I’m surprised not to see a discussion of local versus Microsoft.com accounts for logging into Windows. To me, that’s the first step — don’t log into a cloud account that lets Microsoft track you across devices. (Actually, same thing for e.g. Canonical and Ubuntu, Mozilla and Firefox, etc). Yes, you lose cross-platform interoperability but I have only one desktop computer.
You also lose the ability to get “store” apps, but you shouldn’t be using them anyway — they’re just another way to track you.
Could this guide be updated for windows 11? I have the update ready but, I dont feel ready to do it. I really care about privacy.
Yep, it’s on the 2022 To Do list.
This site is mandatory one to followed by each and every net user.
What is your opinion about ‘O&O ShutUp10++’ and ‘SimpleWall’.
Please let us know.
Thanks Sven and Heinrich.
I was finding it more and more difficult to deal with Windows’ 10. I’m in my 70’s & didn’t want to figure out my way around trying to get updates to stop and mange every roadblock that was put in my way. I loaded Windows’ 8.1 and until I can figure out Linux, I would like to find out which version of Windows’ (like 1809, 1909, etc) is considered the best. I want it to still easily allow me to stop Updates, Cortana, and Microsoft making me agree to let them use my info, etc. Even if it lets me just pretend I can check a “no box” for awhile I’ll be happier than I was with the recent evolution’s. Unfortunately with Window’s 8.1, I would have to add more drivers to get additional wifi adapters to work and it would just be easier to move to a slightly better update that was easy to put your security recommendations on. I would really appreciate any help I can get… Thank You!!
Hey Melly, have you ever thought of going with Mac OS and picking up a Macbook? Mac OS is much easier, faster, simpler, and more secure and private than Windows. It just works better. I recommended it for my parents who also struggle with Windows.
I would never recommend using an outdated version of any operation system. Maybe you get enhanced privacy by using an older version, but you might miss important security fixes. You have to ask yourself if you’d rather have a company having access to your data or a criminal. I’d recommend using a beginner friendly linux distribution. Try Linux Mint or Zorin OS. The last one is actually pretty similar to Windows.
Sorry this comes late:
https://www.askwoody.com/forums/forum/askwoody-support/windows/
It’s a website providing news, tips, advice, and support for Microsoft-related software and hardware. The primary focus is on Windows and Microsoft 365, with an emphasis on the complexities of patches and feature updates to Windows and Microsoft applications. Coverage of cross-platform systems is expanding as Microsoft products extend their reach to Apple, Android, and even Linux users. A special emphasis is placed on security and privacy, especially in today’s consumer settings.
They state: Our website and its associated forums are accessible to anyone, no registration required. Readers may register for the forums, sign up for the free newsletter, or make a donation to receive the full Plus Newsletter. Plus subscribers get all content, access to all previous issues, emailed MS-DEFCON alert notifications (plus access to our MS-DEFCON text alert system), other alerts, “Plus” status in the forums, and customer support. Our newsletter has an illustrious history. Our roster of writers is distinguished, with decades of experience in technology.
On privacytools.io saw this mentioned:
[https://www.oo-software.com/en/shutup10] (calling itself a free antispy tool for Windows 10 and 11)
and
[https://safing.io/portmaster/] (to monitor and control all of one’s network activity).
Portmaster is in alpha, also available for Ubuntu Linux, free and open-source. Any opinion on either of those whether it would be beneficial to use on Windows? – Haven’t been on Windows 10 for several weeks. Reading about Windows 10 on Wikipedia, it looks like the Home edition will be supported until October 14, 2025, so I and others don’t seem to have to be in a rush to install Windows 11. Hopefully in the meantime I’ll be able to find and learn to use more alternatives besides Trisquel.
Thank you very much to the ones from RP who have taken time and care to go over and update important guides on this website!! Your work is appreciated!!