
This guide tracks privacy issues with antivirus software and is periodically updated with new information.
It goes without saying that reliable antivirus software plays a crucial role in IT security. As malware continues to become more sophisticated and prolific (more than 450,000 malware samples are released every single day), home users and business owners alike need to have protection in place to stop these modern digital threats.
However, antivirus products are not immune to privacy problems. While the antivirus industry is ostensibly on the side of good, many antivirus products behave in a way that infringes on users’ privacy. Whether they intercept web traffic, sell browser history data, or allow backdoor access to government agencies, many antivirus products are guilty of jeopardizing the very thing they are designed to protect: your data.
Here are five ways antivirus software may interfere with your privacy.
1. Selling your data to third-party advertisers
To provide you with the protection you need to keep your system safe, your antivirus software needs to know a lot about you. It keeps an eye on the programs you open to ensure you’re not accidentally executing malicious software, and it monitors your web traffic to stop you accessing dodgy websites that might try to steal your login credentials. It might even automatically take suspicious files it finds on your computer and upload them to a database for further analysis. This means your antivirus software could collect and process an awful lot of your personal data if it wanted to.
With great power comes great responsibility.
While some antivirus providers are quite conscientious with their users’ data and only use it when absolutely necessary, others are much less scrupulous.

AVG – A few years ago AVG came under fire when the company announced changes to its privacy policy that would allow it to sell its users’ search and browser history data to third parties (i.e. advertisers) in order to monetize its free antivirus software. Of course, AVG isn’t the only antivirus company to monetize its users’ data.
Avast – Avast’s popular free android app sends personally identifiable information such as your age, gender and other apps installed on your device to third-party advertisers. As an AVG spokesperson explained to Wired, “Many companies do this type of collection every day and do not tell their users.”
From free VPN services to free antivirus, the old adage rings true: if you’re not paying for the service, you’re probably the product.
2. Decrypting encrypted web traffic
Most modern antivirus products include some sort of browser protection that prevents you from accessing known phishing and malware-hosting websites. However, doing so is easier said than done due to the fact that so much data is now transferred via Hypertext Transfer Protocol Secure (HTTPS).
HTTPS is the protocol your web browser uses when communicating with websites. The “S” in HTTPS stands for “secure” and indicates that the data being sent over your connection is encrypted, which protects you against man-in-the-middle attacks and spoofing attempts. Today, 93 percent of all websites opened in Google Chrome are loaded over HTTPS, up from 65 percent in 2015. If you want to know if a website uses HTTPS, simply check the URL or look for a padlock icon in the address bar.
The rapid adoption of HTTPS has helped to make the web a more secure place, but it has also introduced an interesting problem for antivirus companies. Normally when you visit an HTTPS website, your browser checks the website’s SSL certificate to verify its authenticity. If everything checks out, a secure connection is established, your website loads, and you can browse away to your heart’s content, secure in the knowledge that the website is legitimate.
But there’s just one problem. Because the connection is encrypted, there’s ultimately no way for antivirus software to know if the website you are trying to visit is safe or malicious.
Most antivirus products use HTTPS interception to overcome this issue. This involves installing a local proxy server that creates fake SSL certificates. When you visit an HTTPS website, your connection is routed through your antivirus’ proxy server, which creates a new SSL certificate and checks the safety of the site you’re trying to access. If your antivirus software judges the website to be safe, the site loads as normal. If the website is unsafe, the proxy will display a warning in your browser.
By redirecting your data through a proxy, your antivirus is decrypting the data you send on encrypted connections – data that is only meant to be visible to you and the HTTPS website.
There are a few ramifications here:
- Because your antivirus is faking SSL certificates, there’s no way to be 100 percent certain that the website displayed in your browser is the real deal. In late 2017, Google Project Zero researcher Tavis Ormandy discovered a major bug in Kaspersky’s software. In order to decrypt traffic for inspection, Kaspersky was presenting its own security certificates as a trusted authority, despite the fact that the certificates were only protected with a 32-bit key and could be brute forced within seconds. This meant that all 400 million Kaspersky users were critically vulnerable to attack until the company patched the flaw.
- Most antivirus products query the safety of a URL server side, which means the company could potentially track your browsing habits if they wanted to.
- It increases the risk of phishing attacks and man-in-the-middle exploits.
A team of researchers even published a paper on the troubling security implications of HTTPS interception by popular antivirus companies, where they noted:
As a class, interception products [antivirus solutions that intercept HTTPS] drastically reduce connection security. Most concerningly, 62% of traffic that traverses a network middlebox has reduced security and 57% of middlebox connections have severe vulnerabilities. We investigated popular antivirus and corporate proxies, finding that nearly all reduce connection security and that many introduce vulnerabilities (e.g., fail to validate certificates). While the security community has long known that security products intercept connections, we have largely ignored the issue, believing that only a small fraction of connections are affected. However, we find that interception has become startlingly widespread and with worrying consequences.
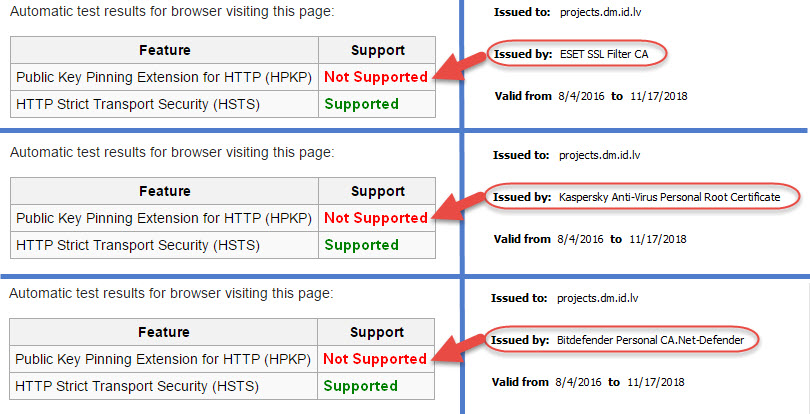
VPN.ac examined the issue as well and discovered that antivirus suites carrying out HTTPS interception also break HTTP Public Key Pinning (HPKP):
HPKP is a technology enabling website operators to “remember” the public keys of SSL certificates in browsers, enforcing the use of specific public keys for specific websites. This reduces the risk of MiTM attacks using rogue/non authorized SSL certificates. But HTTPS scanning and HPKP can’t work together, therefore if a website has HPKP enabled, when you access it the support for HPKP for that site will be disabled in the browser.
VPN.ac found this to be the case with ESET, Kaspersky, and Bitdefender:
Tip: Avoid antivirus software that utilizes HTTPS interception/scanning, or just disable this “feature” within your antivirus.
3. Installing potentially unwanted programs on your computer
Even if your antivirus doesn’t pose a direct threat to your privacy, it may come bundled with software that does. As the name suggests, potentially unwanted programs, or PUPs for short, are applications that you may not want on your computer for various reasons.
While they’re technically not malicious, they usually change the user experience in some way that is undesirable, whether that’s displaying advertisements, switching your default search engine, or hogging system resources.
Many free antivirus products come with PUPs such as browser toolbars, adware, and plugins that you may inadvertently allow to be installed while quickly clicking through the installation process.
For example, free versions of Avast and Comodo try to install their own Chromium-based web browsers, which you may or may not want on your computer. Meanwhile, AVG AntiVirus Free automatically installs SafePrice, a browser extension that claims to be able to help you find the best prices while shopping online. Unfortunately, it can also read and change all your data on the websites you visit.
A few years back Emsisoft found that most free antivirus suites were bundled with PUPs. Here were the culprits:
- Comodo AV Free
- Avast Free
- Panda AV Free
- AdAware Free
- Avira Free
- ZoneAlarm Free Antivirus + Firewall
- AVG Free
PUPs aren’t inherently malicious, but they can seriously encroach on your privacy. Some PUPs will track your search history or browser behavior and sell the data to third parties, while others may compromise your system’s security, affect system performance, and hinder productivity. Keep unwanted applications off of your computer by carefully reading installation options during the setup process and only install the software and features that you need.
4. Cooperating with governments
It’s theoretically possible that antivirus software could be leveraged to help government agencies collect information on users. Most security software has very high access privileges and can see everything that’s stored on a computer, which is necessary in order for the software to keep the system to safe. It’s easy to see how this power could be used by nefarious parties to spy on individuals, businesses, and governments.
Kaspersky Lab, a Russia-based cybersecurity company whose products account for about 5.5 percent of antivirus software products worldwide, was embroiled in a major privacy scandal a couple of years ago. According to the Washington Post, Kaspersky software used a tool that was primarily for protecting users’ computers, but also could be manipulated to collect information not related to malware. Kaspersky is the only major antivirus company that routes its data through Russian Internet service providers, which are subject to Russia’s surveillance system.
In September 2017, the U.S. government banned federal agencies from using Kaspersky Labs software following allegations about cooperation between Kaspersky and Russian intelligence agencies. Shortly after, the FBI began pressuring retailers in the private sector to stop selling Kaspersky products, and the British government issued a warning to government departments about the security risks of using Kaspersky software.

Of course, it would be naive to think this issue is limited to Russian software. Similar concerns have been raised recently about Huawei equipment with “hidden backdoors” installed.
“Antivirus is the ultimate back door,” explained Blake Darché, a former N.S.A. operator and co-founder of Area 1 Security, as quoted by The New York Times. “It provides consistent, reliable and remote access that can be used for any purpose, from launching a destructive attack to conducting espionage on thousands or even millions of users.”
5. Undermining security and giving hackers access to private data
Sometimes, security software does the opposite of its desired intent by undermining your security.
One such case occurred with the Royal Bank of Scotland (RBS), which was offering Thor Foresight Enterprise to its business banking customers. In March 2019, Pen Test Partners discovered an “extremely serious” security flaw with the software that left RBS customers vulnerable:
Security Researcher Ken Munro told the BBC: “We were able to gain access to a victim’s computer very easily. Attackers could have had complete control of that person’s emails, internet history and bank details.”
“To do this we had to intercept the user’s internet traffic but that is quite simple to do when you consider the unsecured public wi-fi out there, and it’s often all too easy to compromise home wi-fi set ups.
“Heimdal Thor is security software that runs at a high level of privilege on a user’s machine. It’s essential that it is held to the highest possible standards. We feel they have fallen far short.”
While Heimdal was quick to patch the vulnerability within a few days, it does raise an interesting point. That is when your security software is actually undermining your security.
Choose your antivirus software wisely
In the best case scenario, antivirus companies use your data responsibly to refine their products and provide you with the best malware protection possible.
In the worst case scenario, they sell your data to third-party advertisers, install annoying software on your system, and cooperate with government agencies to spy on your personal information.
So, how do you sort the best from the rest?
- Pay for your antivirus software. Most free antivirus products will be far more liberal with your data than premium software as the company ultimately needs to monetize their services in some way.
- Read the end user license agreement. Know what you’re getting yourself into before you install the product. Take a moment to read the license agreement and/or the company’s privacy policy to find out what the organization intends to do with your data.
- Read installation options: It’s easy to blindly click through “Next” when installing new software. This can result in the installation of browser toolbars, adware, and all sorts of other PUPs, which can encroach on your privacy in various ways.
- Customize privacy settings. Some antivirus software will allow you to customize privacy settings such as usage statistics, browsing behavior, and whether to upload malicious files for analysis. Adjust these settings to maximize your privacy.
- Read AV reports. Some independent analysts release reports on how antivirus companies handle your data. Take the time to read these reports and reviews to get a better understanding of a company’s reputation and how it handles privacy matters.
It’s important to note that this article isn’t a rallying call to abandon all antivirus software in the name of privacy, because there are some good players out there.
Antivirus software is an essential part of modern IT security and plays a critical role in protecting your data against malware, phishing, and a plethora of other digital attacks that pose a real threat to everyday users.
While some antivirus providers are invasive and should be avoided, there are still some companies that strive to protect their users’ privacy. Emsisoft, for example, has earned itself a reputation for providing reliable protection without compromising its users’ privacy. ClamAV is another privacy-friendly option that is completely open source.
So do your homework, weigh up your options carefully and remember that not all antivirus solutions are created equal when it comes to respecting your privacy.
This antivirus privacy guide was last updated on April 28, 2024.

As it turns out, Biden banned Kaspersky not for Kremlin ties (there weren’t any) but because the company’s antivirus software worked too well, including preventing spyware used by the U.S. government.
https://www.wired.com/story/us-kaspersky-ban-evidence/
Wow, good find Mike. This is definitely not surprising.
Philip,
I’ve used ESET for years but now I’m looking to switch, as ESET has not done quite as well in recent test results as others, and I am also more mindful of privacy issues. Bitdefender scores very well on tests, but I’m worried about how much of the scanning is done on the cloud, plus it appears that their Anti-Tracker add-on for browsers itself tracks the websites you visit! You write, “Emsisoft, is really just Bitdefender.” I read elsewhere that Emsisoft uses Bitdefender’s scanning engine (as well as Emsisoft’s own scanner), but does Emsisoft use Bitdefender’s scanner on the user’s own device, rather than uploading information to the cloud for processing there? If so, is Emsisoft providing the advantages of Bitdefender’s highly rated scanner without the downside of sharing information with Bitdefender?
I was also interested in G Data, but they don’t do as well on testing as Bitdefender does. This table from AV Comparatives seems to show that Bitdefender is more effective: https://www.av-comparatives.org/wp-content/uploads/2024/01/avc_sum_2023_overview_levels-1536×634.png I wonder if Emsisoft would perform as well as Bitdefender, but I don’t see Emsisoft listed in most comparative testing reports.
“is Emsisoft providing the advantages of Bitdefender’s highly rated scanner without the downside of sharing information with Bitdefender?”
Yes, I believe that is correct. You may verify by emailing Emsisoft support for confirmation.
And also its privacy policy is one of the worst that I have read. The ESET one is much better.
@Philip, all, “It is so sad we are not allowed to have anything nice they have got to constantly be looking over our shoulder watching our every move.”
Well said.
However, that may have been the point all along.While we watch the shiny things, they watch US.
Creepers.
Hello, also can you tell me please: does F-Secure Internet Security utilize HTTPS interception/scanning? If yes, can you please say how to disable it? Thank you.
Are you using Emsisoft and F-Secure Internet Security on the same computer ?
If so, to me that is not needed.
If you are a casual browser or gamer;
emails, facebook, instagram, news, youtube,
the antivirus that comes with Windows should be good enough.
For added privacy and security,
use the web browsers Brave or Firefox ( modified )
You can also add these web browsers ad blockers;
AdGuard ( extension or full version ) or Ublock Origin.
Extra protection, a good vpn with many good reviews.
( ivpn, Mullvad, Nord, Pia, Proton, Surfshark )
No, I am not running both on the same computer. I wouldn’t advise anyone to run two AVs at the same time. Besides being unnecessary, it could create problems.
Yes, I use Firefox, Brave, uBO, and a VPN.
Hello Agathon. Thank you for taking the time to answer my comment. Have a lovely day 🙂
Thank you for this excellent information. My question is: does Emsisoft Anti-Malware utilize HTTPS interception/scanning? If yes, would disabling the “web protection” component disable the HTTPS interception/scanning? Thank you.
I have confirmed with Emsisoft support that neither Emsisoft Anti-Malware nor the Emsisoft browser extension utilize HTTPS interception/scanning.
I tried ClamAv and after three hours or so I gave up, because you have to be a rocket scientist to install it. Does anyone have a script or know-how to install ClamAv? I seem to remember that a few years back you could just downoad, extract and run the program with no problems.
Hi. You can download ClamAv Portable which is a much easier package to use on Windows. Check it out 🙂
tianxia I can’t find the source of your findings about SuperAntiSpyware…can you please send me a link?
Update for SuperAntiSpyware…I disabled both incoming/outgoing connections via firewall and use the offline updates to keep it up to date, but I think it’s a shame I have to do this. I have not really seen any bad reviews about SAS so I’m gonna keep the service and it does work though and will give update once hearing from SAS
Don`t use SuperAntiSpyware! They are trackers 100%.
they cooperate with:
#Facebook – tracking > facebook.com
# Google – FingerprintingGeneral > doubleclick.net
# Microsoft – Content > bing.com
# Hotjar – Analytics > hotjar.com
great text…I think it’s best to use TAILS so there are no problems of that kind (which doesn’t mean there aren’t problems there too)
I have a lifetime subscription to Superantispyware since 2009 ( in 2014 they tried to make me buy the subscription again and it took around 9 months before my lifetime subscription was reinstalled ) and after setting up my preferences I never paid much attention to it until about 8 days ago.
I got bored that day and was making checks on my laptop and woe behold…the SASP disable threat reportong box is no longer there! I contacted Superantispyware but they have not answered yet. My question is are they sending my data to Avira ( who owns them ) without my consent or has it started a journey to being spyware?
Most anti-malware companies sell scareware and they would if they could get away with it sell you an anti-malware product for your washing machine. The most intrusive anti-malware products is probably Trend Microis, they even share their data with Google analytics and they are open about how many people they share your data with in their terms and conditions they highlight just how much they collect which is frightening. The anti-malware companies especially in the U.S. are virtually scamming their customers if you buy the products from their websites. They will charge you a small fee for their product and then set that to auto renew at a ridiculous extortionist price. The majority of anti-malware companies are now using such a scam on their customers especially in the U.S. they have no respect for their customers.
Kaspersky is becoming very aggressive with its installation there are so many options you have to opt out of when installing Kaspersky, if you do not the pop-up messages and advertise months of their products will drive you crazy. The other anti-malware products you mentioned on here have all been purchased by Norton AntiVirus, and Norton AntiVirus, become famous for helping the U.S., spy agency and the FBI and whitelisted Magic Lantern, and keylogger.
Nowadays you have to set up an account and log onto their website for cloud base protection cloud base being a new phrase for servers. The way people are given away their privacy is shocking and what Microsoft are now up to with windows 10 and 11 should not be allowed. We are now at a stage with cancel culture political opinions dissidents and so on can have their windows system deactivated by Microsoft and that one is very nearly here waiting to be used. Emsisoft, is really just Bitdefender. Sophos was bought by a U.S. private equity firm.
The only one which seems to collect not so much data is an overpriced product but incredibly cheap if purchased from third-party company is G data a virtually unknown not very good German anti-malware product. I am afraid if you really want privacy then you have to go for a Linux desktop which programs looked like they come from Noah’s Ark. And then again Linux had a NSA backdoor that remained undetected for 10 years unto Chinese security company found it and it is called Bvp47 Linux backdoor.
It is so sad we are not allowed to have anything nice they have got to constantly be looking over our shoulder watching our every move.
I am kinda disappointed that Sven Taylor did not include any personal favorites…..come on hook me up!
We’re going to be doing antivirus reviews and recommendations in the near future. So stay tuned!
Windows 10 and windows 11 is spyware. I had a problem with Kaspersky “Kaspersky Premium Total Security” I purchased the activation key from Amazon at a fraction of the price I was going to use it on Windows 7 pro windows 10 pro and Windows 7. Because the activation code is too long to remember i typed it into LibreOffice. So basically I use copy and paste to paste in the activation code from the document. Everything went O.K. and then Kaspersky wiped the document with the activation code it did not delete it it just wiped out the code. It must have assumed that the activation code in the document was pirating Kaspersky’s product and thus wiped out the code. I contacted them and they suggested that it was malware doing it and I told them it was not and I uploaded the document to VirusTotal and some of the other documents all negative. I then run an independent virus scan all clean. Kaspersky asked me to send them a zip copy and password protected and send it to them which I did do.
They then had nothing to say for themselves so they sent me the same e-mail again like a robotic reply. So I remove Kaspersky from the 3 computers. Pity Kaspersky is the best antivirus anti-malware product. too intrusive over the top..
Hi, the same thing happenedto me,he deleted my activation key even from my gmail imbox
Great article.
Regarding selling data to third-party advertisers I’m participating in a Dutch class-action suite against Avast. I would advise being careful using products with aggressive marketing and bundling PUP’s such as Avast, Norton and more recently Avira. Same goes for “I don’t care about cookies” browser plugin now owned by Avast. I haven’t used/researched the other products mentioned that bundle PUP’s.
I found this article research up to date information about decrypting encrypted web traffic. There’s not much updated info to be found and HPKP has become obsolete. Remains that this can impact performance on slow systems and potential privacy issues. My policy is to choose a product that allows me to disable this feature, without nagging error messages that the antivirus is no longer working correctly (yes I’m talking to you Avast).
I don’t see any issues using free software from trusted companies such as Kaspersky, BitDefender, MalwareBytes or Sophos
I could really use some updated information on the details of which antivirus companies collect data, whether the data is to be sold on or not.
I appreciate the team at RP are extremely busy with other privacy items but as full access is needed to our machines by the antivirus programs, surely privacy is as much of an issue with this software as it is with VPNs, browsers etc.
I have done a little digging of my own & have decided that only Emsisoft & F-Secure respect the privacy of the user & keep the data grabbing to a minimum.
Any other opinions would be appreciated.
Thanks for the article. This information also applies to our Firewalls, Browsers, Mobile Devices, and OS’s. 🙁
Anyone tested the abovementioned ClamAV? Is it competitive? Updated often? Does it detect on par with the big boys? Thanks.
Which antivirus is good in terms of not collecting user info the most. Not necessarily in dectection rates.. The less amount of user data collection-the better.
Hi,
Which anti-viruses should i use then? Thank you
@ John Doe I recommend one of these – ESET Internet Security, Emsisoft, Sophos Home and Kaspersky. Kaspersky is definitely Russian and it depends on whether one wants to trust it or not. Many do trust. I use and can easily recommend ESET Internet Security, very light on system too, feather light. Emsisoft and Sophos Home are also Great. Sophos is good if one has multiple PCs in house, otherwise Emsisoft. Others are problematic because they generate a lot of popup notifications and try to upsell hard their other products which one does not need or are too much heavy on system resources like Bitdefender.
@John Doe Other security and privacy tools also go hand in hand with Antivirus, like Adblockers, VPN, Password Manager, DNS Filter, Private Search, Secure Email and Secure Messenger, Secure Browser, Backup, Network Monitor tool, Up to date OS and private and secure alternatives to apps like office, navigation, notes etc.
Hi Sven Sir,
Please also review Antivirus softwares, specially for Windows PC.
Just like in VPN industry domain there is a lot of malpractice and bad ethics amongst many VPN review websites and overnight VPN experts, similar story goes for antivirus Softwares. A simple Google search about best antivirus Softwares is enough to indicate that these reviews are kind of sponsered or something in that line. While Antivirus companies perhaps do not own review websites like Kape, they most likely purchase or pay for top spot on Antivirus review websites. This was also confirmed in comment section by a Youtuber who previously worked in antivirus industry and told how they would pay to websites for top spots in their list of Antiviruses or websites would themselves used to come to them.
[Nico knows Tech https://youtube.com/@NicoKnowsTech%5D
An antivirus has privileged access to system including all the files on the system and even internet traffic as antivirus checks for malicious traffic and websites and so just like a VPN which has access to all our browsing history, an antivirus is a sensitive piece of software and trust is a major factor along with the kind and quality of protection it offers.
Personally as a user I recommend ESET and Emsisoft. Kaspersky is also a good antivirus if trust issues are not involved. Bitdefender offers great protection but try hard to upsell. Same for Avast and AVG and Norton, to make more money they try to upsell and nag users. McAfee and Avira have poor advance threat protection and leaving a few alright antivirus Softwares like FSecure or Sophos, list goes down hill from here. While Windows Defender has improved over last couple of years, it still is not good enough.
Can you list the antivirus programs that are safe to use with ranking?
Hi there, when it comes to antivirus Softwares based on my experience as well as experience of others, ESET and Emsisoft are the only Antivirus softwares I recommend.
I would have also recommend Kaspersky, it is a top tier product, but due to ongoing geopolitical situation, thought I might use it personally as allegations are not proven, but hesitate to recommend it wholeheartedly. But I certainly recommend ESET or Emsisoft.
Windows Defender is okish but there are many instances when it fails to protect against malware irrespective of what results from AV Comparatives and other testing labs say.
For highly risky work I recommend running Windows user account without administrative privileges and using virtual machine.
I don’t recommend Avast and AVG (both same) and Norton, Bullguard, Avira (All five consolidated), as well as Bitdefender, and McAfee primarily because they are nagwares and always disturb user through their sales practices and always try to upsell something and also because they are resource heavy, so not recommended. Otherwise protection wise they are not bad but rather good, but as I said they are resource heavy and themselves act like adwares.
There are few other good enough options too like Malwarebytes and F Secure.
There are some other half decent antivirus like Panda Dome, Trend Micro, K7 Security, Comodo, but I don’t recommend them as there are better options which offer better protection with less false positives.
Other popular options like 360 Total Security and few others whom I don’t want to name are bad and your security actually takes a hit when you install and use them over the already average and default Windows Defender.
.
Also a good cyber security hygiene is essential other than using a good antivirus. Never install and use cracked apps and softwares on PC and Android, otherwise neither a Virus Total Scan not an antivirus will help prevent possible infections and consequent heavy losses.
Again, prevention is the best cure, malware generally comes from advertisement heavy bad websites, specially adult website and similar such websites, through infected USB sticks, clicking on malware links in emails and SMS or chat applications or social media and redirects on browsers, and also compromised websites and programs on your system which otherwise have good reputation. Modern malware are very sophisticated and highly advance piece of software which takes lots of resources and time to develop and often state actors are involved. It is best to avoid them as sometimes they can Infect windows and Android devices so deeply that even a system reset won’t solve the problem as drives and motherboard firmware get infected.
1.g-data
2.f-secure
3.emsisoft
Can you please justify this?
Yes! Now I want to use Kaspersky!!
Does it have any major problems??
No need to worry as their data processing happens in Switzerland, it’s better than all other av out there in terms of speedy performance and lab test ratings.
Bit defender IS Spyware they tried to recruit me to sell
It and install it on devices with a fake email.
Antivirus software is also being used to censor websites that don’t support the official government narrative. And when I tried to dispute the way Norton categorized a certain website I got an error message, “we are unable to process your request.” How do we find antivirus software that doesn’t support fascism?
So, what do we use now then?
For antivirus, which deosnt collect ip address or data?
don’t really know anymore, even webroot makes it imperative that they are collecting and using your cookies their way and if you are not fine with this stop using their software…ah duh, i just paid for it. they are working with the fbi and collecting data from everyone
even that clamav, the immunet one has real time protection, very light. But its cisco base.
G data doesnt sell to 3rd party tho. But they collect some some
Emisoft also collects ip addy. If reading through privacy policy.
This is an excellent article.
Also, do leave the political hysteria alone: Kaspersky is just another commercial enterprise that is no worse than any Eastern or Western-based software companies in general. Kaspersky isn’t out there to serve your privacy on a golden platter to KGB or whatever. Watch and read less psychotic political propaganda and your ability for critical thinking will be back in no time.
Thank you, Comrade. Nothing to see here – Don’t fear Russian bear!
Guys, Sven, PLEASE Make a review of Avira Phantom VPN.
It’s such a disaster!
While using Avira Phantom VPN, websites are redirected to a Russian phishing link.
You can’t believe it, this VPN promises: “Ultra-secure: Top, Bank-Grade Encryption” (you can read it on Avira Phantom VPN website). I changed VPN and then no redirects were anymore.
I am curious what your results will be.
Some strange connection with Russia, or redirecting to the Russian Phishings websites, appears regularly by Avira Phantom VPN, but Avira says they are from Germany..
Best regards
I just downloaded ClamAVNet for Mac OS. I was surprised to find that it’s not in my App Folder. Reading the documentation, I see that it’s a command line (Terminal) accessed program. And there were additional steps involved in activating the software–including removing and adding command line inputs. Even after following their documentation instructions, I still get error messages (directories not writable by me, my machine’s admin) and can’t use the software. And yes, I have Homebrew installed on my machine. This is why so many people use GUI version software. I realize many tech aficionados prefer command-line interaction, but many of us don’t want to waste hours learning about each software we download just to use our machines. We already have exhausting jobs and just want our machines to work.
I read through the TOS and PP of BitDefender & Norton AV and was repulsed they collect so much personal info and have such a deep level access to our machines and data. The other privacy-respecting option mentioned in this article, EmsiSoft, is available only for Windows. So I guess that leaves me without AV protection since I can’t figure out how to get ClamAVNet to work. Ironically, their website claims their main goal is to make AV “easy” for the average person. HA!
I recently theorized the threat & possibility of “man in the middle” with those antivir certs after i came across the cert issues people had reported on a forum. Did a search and found your page about it too. I agree, its a security issue and can be used for snooping (its already used for that most likely). But for most people, they have no security issues to hide on that level really, its of no real concern to them, but yeah definately a potential privacy intrusion annoyance.
[I haven’t had any antivir installed on any of my systems in the last 10 years (I use my own special methods, and only install antivir/antitrojan for removing stuff if I catch something I can’t manually disassemble/unarm for my own curiosity (then uninstall). A year ago, I installed an antivir to checkup for fun (curious after 3 years with sensing no problems by my daily usage). But it found nothing! Got kinda annoyed & bored that there was nothing new & juicy to research/pry into (lol zzz).]
Telling people to pay for their AV is foolish. That’s like saying pay more for a diamond or house, because that means it will be better. That is not necessarily so. Like you said elsewhere, READ THE AGREEMENT. If the agreement for the paid version offers more privacy than the free version, then MAYBE the paid version is worth it.
If you select Settings > Network settings > Encrypted connection scanning > Do not scan encrypted connections > Save, in a Kaspersky Lab Product, Safe Money will be disabled.
https://twitter.com/doctorow/status/1478479483585933312
As if it doesn’t get worse, Norton now deals on crypto. Luckily it’s an opt-in, not opt-out, but this is unethical and not financially worthy in that Norton gets 15% cut while you pay for electricity to mine, of which your 85% cut likely would not cover for.