
Mozilla Firefox is one of the best browsers available that combines strong privacy protection features, good security, active development, and regular updates. The newest version of Firefox is fast, light-weight, and packed full of privacy and security features.
It is for this reason that I consider Firefox to be the best all-around browser for privacy and security. It remains a solid alternative to some of the other options, such as Google Chrome, Microsoft Edge, and Safari.
Another great aspect of Firefox is that it is highly customizable, which is the point of this guide. Below we will go over how you can customize Firefox to give you the security and privacy you desire, while still working well for day-to-day browsing.
But before we jump in, let’s cover some important details.
Important considerations before starting
There are many factors to consider when configuring Firefox to meet your needs, including your threat model and browsing preferences. In other words, there is no “one-size-fits-all” configuration that will work for everyone. This guide is a basic overview covering some of the different configurations options.
Before you start modifying Firefox and installing a bunch of add-ons, it’s important to consider browser fingerprinting.
Browser fingerprinting
The issue of browser fingerprinting (or device fingerprinting) is a big topic that covers all the different ways you can be tracked and identified by your system and various settings. All of the different add-ons you install and preference modifications you make to Firefox are inputs that can potentially be used to identify and track you.
Herein lies the catch-22: the more browser add-ons you install and settings you modify, the more likely you will stand out from the crowd and be easier to track. There are solutions for this and the latest version of Firefox does offer some fingerprinting protection. I discuss this problem and also provide solutions in the browser fingerprinting guide.
And that leads us to the next point that…
More is not always better
When it comes to browser add-ons and modifications, you don’t want to be like that kid who puts every topping imaginable on his ice cream. Similarly, more is not always better with Firefox browser add-ons.
Aside from the issue of browser fingerprinting, having too many add-ons may slow down performance and break things. Many of the popular Firefox add-ons also fulfill the same functions and are redundant when used together.
Therefore it is best to strike a balanced approach. Install and modify only what you think will be useful and necessary for your specific situation.
Proceed with caution
Modifying some of these settings may interfere with your browsing experience and break some websites (they won’t load properly). Therefore taking an incremental approach may be the best way to proceed. You can continue to install add-ons and adjust your settings as you see what works best for your needs.
This allows you to modify the settings, create exceptions, or add sites to a whitelist.
Firefox privacy tweaks
Before you get going with Firefox you may want to adjust the following settings for better privacy.
Note: if you are a Mac OS user, you will see the word “Preferences” in your menu rather than “Options” as it is listed below.
Disable Firefox telemetry
With the latest version of Firefox, it is configured to share “technical and interaction data” with Mozilla. This includes the ability to “install and run studies” on your computer. You can learn more about these studies and data collection practices, but I’d recommend disabling these settings.
To disable go to Open Menu (three bars at the top right corner of the browser) > Options > Privacy & Security > Firefox Data Collection and Use and then uncheck the boxes as you see below:
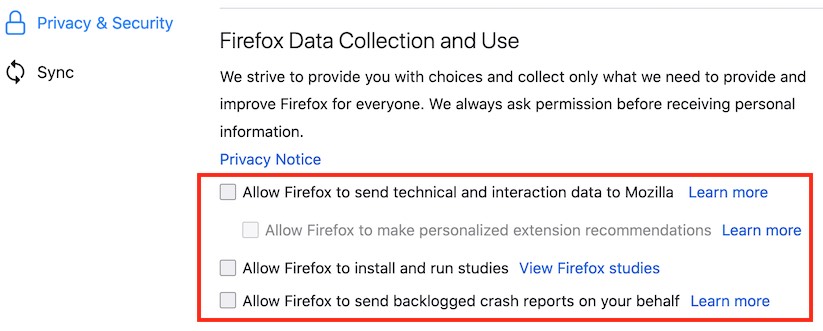
You can also disable data sharing with Firefox for Android by going to Menu > Options > Privacy > Data Choices and then uncheck all three categories for Telemetry, Crash Reporter, and Mozilla Location Service.
Note: You can also disable this in the About:Config settings with toolkit.telemetry.enabled set to false.
Change the default search engine in Firefox
Firefox now uses Google as the default search engine, but there are other private search engines you can use instead.
To do this, go to Menu > Options > Search > Default Search Engine. Firefox does not provide you with very many alternatives directly in the settings area. However, you can view more options by going down to One-Click Search Engines and then click Find more search engines to see the other alternatives.
See our guide on private search engines to dive into this topic more.
Firefox also has a guide on modifying your search engine preferences.
Firefox Content Blocking
Another great new feature with Firefox is Content Blocking. This customizable feature will automatically block “content that tracks the sites you visit and profiles you.” You can choose between Standard, Strict, and Custom modes, which allow you to block:
- Cookies
- Tracking content
- Cyrptominers
- Fingerprinters
To adjust the Firefox Content Blocking settings, go to Menu > Options > Privacy and Security > Content Blocking and then select which mode you want to use.

The Standard setting may be the best balance for regular users. Firefox warns that Strict mode may “cause some websites to break.” However, you can still…
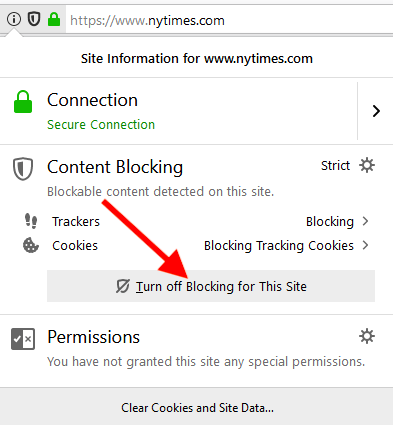
Disable content blocking for specific sites
It’s easy to disable content blocking for certain trusted sites. Simply enter the website URL, then click the “i” icon to the left of the address bar, then click the grey button to “Turn off Blocking for This Site.”
Another benefit of Firefox’s Content Blocking feature is that it can save your data and improve page load speeds.
The “Do Not Track” request
Firefox also has an option to request that websites “do not track” you online. This is simply an HTTP header field that you can easily enable. However, the key word here is request, because this is not actually blocking anything. We have also learned that many websites simply ignore these requests.
In addition to being ignored by most sites, this is also a value that can be used for browser fingerprinting purposes, as explained here. Therefore I no longer recommend enabling or modifying the Do Not Track settings, which you’ll find in the Content Blocking settings area.
You can learn more about the Do Not Track feature here.
Firefox About:Config settings
Aside from the general Menu settings we used above, you can also make a number of different modifications using about:config.
Note: If you made all of the changes above, you may notice that some of these settings are already updated in about:config. We will still cover the different about:config since some people prefer to modify settings in this area, rather than through the general Menu.
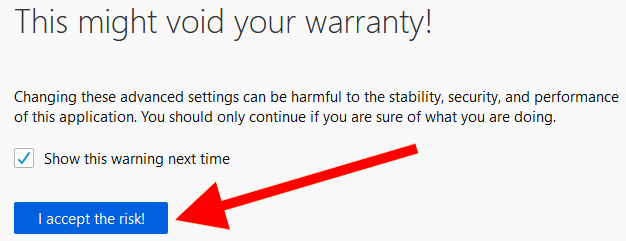
To access these configuration settings, simply enter about:config into the URL bar and hit enter. You will then be prompted with a warning screen stating “This might void your warranty.” Just click “I accept the risk” to continue.
After proceeding, you will see a large list of preferences, which each include a status, type, and value.
These preferences will be listed in alphabetical order and are easily searchable from the search bar near the top.
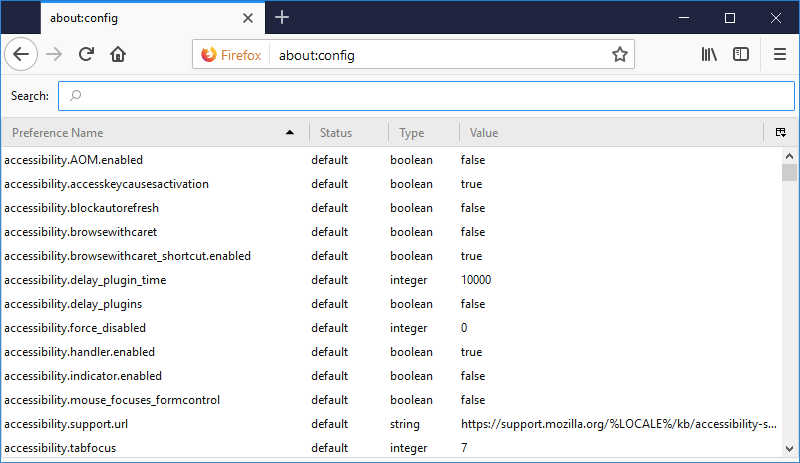
Modifying preferences – You can modify any of these Firefox preferences by simply double clicking the preference name. If the preference is a “boolean” type, then double clicking will change the value to true or false. If the preference is an “integer” or “string” type, double clicking will open a box to change the value.
Here are my recommended changes:
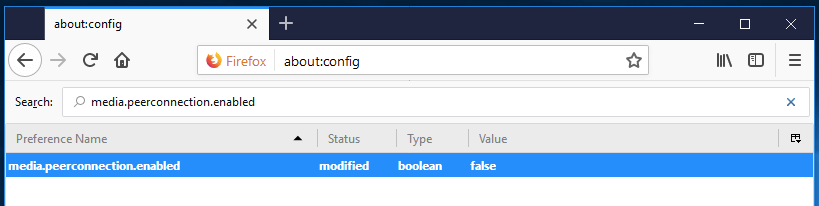
Disable WebRTC:
media.peerconnection.enabled (WebRTC) = false
WebRTC stands for “Web Real-Time Communication” and it allows for voice, video chat, and P2P sharing through your browser. Unfortunately, this capability can also expose your real IP address through browser STUN requests, even if you are using a good VPN service. (This is called a WebRTC leak.)
To disable WebRTC in Firefox simply enter media.peerconnection.enabled into the search bar and then double click the value to change it to false.
Aside from Firefox, the WebRTC vulnerability also affects Chrome, Opera, Brave, and other Chromium-based browsers. Safari is also in the process of implementing WebRTC.
Note: If you disable WebRTC, services like Google Meet and Whereby may not work.
Resist Fingerprinting:
privacy.resistFingerprinting = true
Changing this preference to true will help to make Firefox more resistant to browser fingerprinting.
Note: There are many factors that go into browser fingerprinting and the ability of an adversary to identify you. See the browser fingerprinting guide for additional details.
privacy.trackingprotection.fingerprinting.enabled = true
This is a new preference with Firefox 67+ to block fingerprinting.
privacy.trackingprotection.cryptomining.enabled = true
Another new preference with Firefox 67+, this will block cryptominers.
First party isolate
privacy.firstparty.isolate = true
Changing this to true will isolate cookies to the first party domain, which prevents tracking across multiple domains. First party isolation also does much more than isolating cookies, it affects: cookies, cache, HTTP Authentication, DOM Storage, Flash cookies, SSL and TLS session resumption, Shared Workers, blob URIs, SPDY and HTTP/2, automated cross-origin redirects, window.name, auto-form fill, HSTS and HPKP supercookies, broadcast channels, OCSP, favicons, mediasource URIs and Mediastream, speculative and prefetched connections.
This preference was added in late 2017 as part of the Tor Uplift Project.
Tracking protection
privacy.trackingprotection.enabled = true
Another new update, this is Mozilla’s built-in tracking protection feature. This will use a Disconnect.me filter list, but may be redundant if you are using uBlock Origin 3rd party filters.
Disable geolocation tracking
geo.enabled = false
Setting this to false will disable geolocation tracking, which may be requested by a site you are visiting. As explained by Mozilla, this preference is enabled by default and utilizes Google Location Services to pinpoint your location. In order to do that, Firefox sends Google:
- your computer’s IP address
- information about nearby wireless access points
- a random client identifier, which is assigned by Google (expires every two weeks)
Before this data is sent to Google, you would first get a request by the site you are visiting. Therefore you do have control over this, even if geo remains enabled.
media.navigator.enabled = false
Setting this preference to false will block websites from being able to track the microphone and camera status of your device.
network.cookie.cookieBehavior
This is an integer type preference with different values. Here are the cookie preference options:
- 0 = Accept all cookies by default
- 1 = Only accept from the originating site (block third-party cookies)
- 2 = Block all cookies by default
- 3 = Block cookies from unvisited sites
- 4 = New Cookie Jar policy (prevent storage access to trackers)
Any selection between 1 and 4 would improve privacy. The New Cookie Jar policy (value 4) offers more protection, but it may also break the functionality of some websites. Ghacks has a discussion of the New Cookie Jar policy here.
network.cookie.lifetimePolicy = 2
This is another integer type preference that you should set to a value of 2. This preference determines when cookies are deleted. Here are the different options:
- 0 = Accept cookies normally
- 1 = Prompt for each cookie
- 2 = Accept for current session only
- 3 = Accept for N days
With a value of 2, websites you visit should work without any problems, and all cookies will be automatically deleted at the end of the session.
network.dns.disablePrefetch = true
Setting this preference to true will disable Firefox from “prefetching” DNS requests. While advanced domain name resolution may slightly improve page load speeds, this also comes with some risks, as described in this paper.
network.prefetch-next = false
Similar to prefetching DNS requests above, setting this preference to false will prevent pages from being prefetched by Firefox. Mozilla has deployed this feature to speed up web pages that you might visit. However, it will use up resources and poses a risk to privacy. This is another example of performance at the price of privacy.
Disable WebGL:
webgl.disabled = true
WebGL is a potential security risk, which is why it is best disabled by setting webgl.disabled to true. Another issue with WebGL is that it can be used to fingerprint your device.
You can get more information on the WebGL issue here and here.
dom.event.clipboardevents.enabled = false
This prevents websites from getting notifications if you copy, paste, or cut something from the page.
media.eme.enabled = false
This disables the playback of DRM-controlled HTML5 content. See details here.
Firefox “safe browsing” preferences
There are many recommendations to disable the Safe Browsing feature in Firefox due to privacy concerns and potential Google tracking. However, these concerns are based on an older version of the Safe Browsing feature, which would utilize “real-time lookup” of website URLs. This method has not been in use since 2011 – explained further here.
If a URL is needed, Firefox takes the following precautions to protect user privacy, as explained by François Marier, a security engineer for Mozilla:
- Query string parameters are stripped from URLs we check as part of the download protection feature.
- Cookies set by the Safe Browsing servers to protect the service from abuse are stored in a separate cookie jar so that they are not mixed with regular browsing/session cookies.
- When requesting complete hashes for a 32-bit prefix, Firefox throws in a number of extra “noise” entries to obfuscate the original URL further.
Therefore I would conclude that disabling Safe Browsing would give you no tangible privacy benefits, while also being a security risk. That being said, if you still want to disable this feature, here’s how in the about:config area:
- browser.safebrowsing.phishing.enabled = false
- browser.safebrowsing.malware.enabled = false
Firefox privacy and security add-ons
There are some great Firefox browser add-ons that will give you more privacy and security. With that being said, many of the add-ons we previously recommended are no longer necessary thanks to Firefox’s upgraded privacy and security settings.
Note: When looking for Firefox add-ons, be sure to consider what you need in relation to the preferences you modified above. Some add-ons will be redundant and not necessary depending on your Firefox preferences and the other add-ons you are using.
uBlock Origin
uBlock Origin is an efficient, light-weight blocker that filters both ads and tracking. It has risen to popularity as a powerful alternative to Adblock Plus, which allows “acceptable ads” that many users disdain. One added benefit of uBlock Origin is that it can significantly improve performance and page load speed.
Another great feature with uBlock Origin is the ability to whitelist certain websites. Given that many sites will block access if they detect an ad-blocker, the ability to whitelist will come in handy. uBlock Origin is free and entirely open source.
NoScript
NoScript is a script-blocker that allows you to identify/block scripts running on websites. While it does give you control, NoScript can be a pain to get configured properly. It breaks many websites, which requires you to tweak and configure the options. If you are already using uBlock Origin, then you probably don’t need to be using NoScript.
This is definitely not an add-on for the casual user or those who don’t have the patience to devote some time into configuration.
Using a VPN with Firefox
Firefox currently offers a VPN (virtual private network) called Mozilla VPN. However, this is just a rebranded version of Mullvad and I have seen many users complaining on various forums about the lack of support when things go wrong.
Note that while some VPNs offer browser extensions for Firefox, these are fundamentally different from a full VPN. A VPN will run on your operating system (not just your browser) and encrypt all internet traffic on your operating system. This is different from a browser extension that only wraps your browsing traffic inside an additional layer of encryption.
Additionally, some Firefox VPN extensions are actually just an extension of the desktop VPN application. These “extensions” literally just extend control of the VPN to a convenient browser interface. We discuss this and more in our guide on the best VPNs for Firefox.
Firefox DNS over HTTPS (DoH) is not a great idea
Just like with Firefox Private Network, the implementation of DNS over HTTPS also relies on Cloudflare infrastructure. In fact, it makes Cloudflare the central processing point for all DNS requests in the Firefox browser by default.
While DNS over HTTPS may sound advantageous in some respects, there are also potential concerns. Rather than going over why, you can read the article, Centralised DoH is bad for privacy, in 2019 and beyond, which concludes:
Centralised DoH is currently a privacy net negative since anyone that could see your metadata can still see your metadata when DNS is moved to a third party. Additionally, that third party then gets a complete log per device of all DNS queries, in a way that can even be tracked across IP addresses.
Even if further privacy leaks are plugged, DoH to a third party remains at best a partial solution, one that should not be relied upon as a serious security layer, since it will be hard to plug everything, especially if non-CDN content providers survive.
Encrypting DNS is good, but if this could be done without involving additional parties, that would be better.
And for actual privacy on untrusted networks, nothing beats a VPN, except possibly not using hostile networks.
Many people also assume that encrypted third-party DNS will somehow offer privacy and anonymity. This is a false assumption. Your IP address and location remains exposed with everything you do online, while your ISP will still be able to see the websites you visit (IP addresses) even if it’s no longer handling DNS requests. In conclusion, a good VPN will offer much more protection than DoH through Cloudflare.
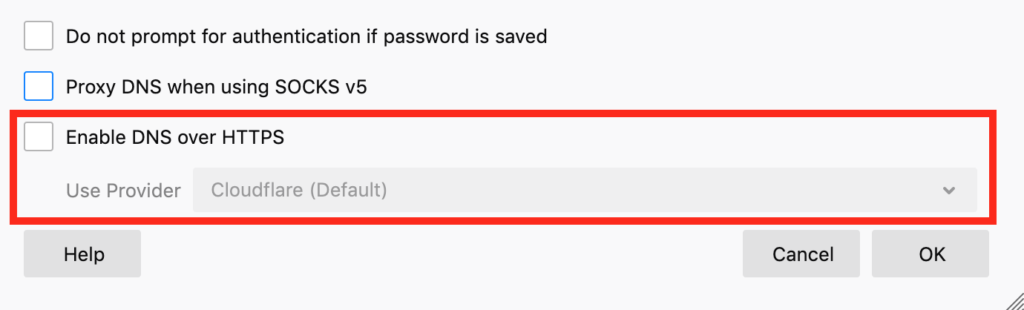
To disable DNS over HTTPS (DoH) in Firefox go to Menu > Options > General and then scroll down to Network Settings and click the Settings button. In the box that opens, scroll down to Enable DNS over HTTPS, where it can be enabled or disabled.
user.js Firefox hardening
For more information and resources on Firefox hardening, see here: user.js Firefox hardening.
As explained on their GitHub page, this is a “configuration file that can control hundreds of Firefox settings. For a more technical breakdown and explanation, you can read more on the overview wiki page.”
Their Wiki page is also full of great information.
Firefox privacy conclusion
In my opinion, Firefox remains the best all-around, mainstream browser on the market for privacy when it is modified as recommended above.
While many of the configurations and add-ons discussed in this guide will go a long way to giving you more privacy, there is one issue that remains: concealing your IP address and location. To do this, a good VPN service is necessary. The Tor network also achieves this end, but it comes with the drawbacks of slow speeds, risks, and limitations (only works in a browser).
For more options in addition to Firefox, see the secure browser guide.
This Firefox Privacy article was last updated on January 19, 2024.

Sir
Should I enable privacy.firstparty.isolate as FF have dFPI ?
LibreWolf didn’t set true to privacy.firstparty.isolate as their opinion is, it hampers the function of dFPI.
What is your view?
Question: since following your guide to enhance privacy, Firefox now opens a window about half the size it used to be, quite maddening. This is on Ubuntu 22.04.4 LTS using the current v. of Firefox, v,130. Any idea how to fix that?
I think it was the change to privacy.resistFingerprinting to true that had this effect. 🙂 Try it out.
Thanks Bosse J – found that way down in the thread just now as well. Appreciate your post!
LibreWolf browser is far better than Firefox. Its open source, and by default configured for secure browsing experience. If you use privacy addons like: ublock, cleanURL, ghostery, privacy badger, decentraleyes and 7 more with your own VPN and disabling PC trackers, you will be free bird. 🙂
Brave browser is the ONLY browser I trust for privacy. No amount of changes in Firefox will make it as good as Brave. Firefox has weak fingerprinting protection, which means your still tracked (even behind a vpn). Only Brave has fingerprint randomization. The best solution.
More and more people are switching to Brave for real privacy. If it wasn’t for Google funding, Firefox would be gone by now.
ok first of all you know nothing about business
second of all all brave also spys on you
ok bye
👍👏
ah yes, brave, the “private” and “user-first” browser that is automatically opt out instead of opt in, and it doesn’t even prompt you with some telementry (to disable it). Firefox is superior in privacy customization and hardening, while yes, the default brave vs the default firefox, brave wins.
Little homework needed.
Scratch that, a lot of homework needed.
Sorry, but @IDK is right….
Tor Browser is solid. Rather than hunting and pecking your way through guides and trying to find the perfect set of about:config entries, give Tor a try. Tails Linux is easy to use, too, and uses Tor Browser.
It is a private and secure browser, but it’s certainly not solid for any activity that requires bandwidth, such as streaming. It’s also no all-star when it comes to unblocking geo-restricted content, or using the internet without go through reCAPTCHA authentication hell.
reCAPTCHA should die as quick as possible.
How would you review or advise on the use of Firefox sync, related to keeping privacy. Would it be a good idea, for syncing bookmarks, add-ons, and settings across devices, NO-passwords/history/tab?
Yes, it is a safe and secure option, but it will not have as many features as some of the top password managers.
As a user of Robolinux 12+ with Librewolf and SRware Iron I seem to be safe.
I did the config here then tested Firefox and abover browsers on several testing sites.
None are perfect but overall I feel secure with all 3.
Windows X-lite 11 or 10 (reuse your key or buy another) in a VM when needed with open shell hover mode for the GUI (speed)
Ghost browser (NOT as secure) for special use then close and reload the starting image.
can i change my firefox browser settings on my iPad? i noticed some browsers Eg Brave with VPN isn’t available on iPad even if i try installing browser version. this is why i hate Apple products. I tried to do direct download from the uBlock Origin website and it doesn’t let you because I guess the company didn’t pay dues into APPLE store apps so its not availabe, iPad is different than macbook itself.
Theres no about:config in latest version of firefox and its hard to find secure download for older version. Is there any use for firefox without about config. Your page is out of date
Not sure where you’re getting the info that about:config is not available. You need to type that into your search bar. It’s still there. I’m using it today.
This may be a foolish question since we want things to be private. If we sign into Firefox to get all settings to sync, it will kind of know who we are. Does anyone think that it would be okay to do this if we use a throwaway email address? I want to be sure since I have followed many of the steps on this site, but I did not see anything that mention this. If there is a link someone can point me to I would greatly appreciate it. Another Firefox question I have is do you think that it is okay to be logged into Grammarly using a primary email address since that is where my subscription is
Firefox v122 for mac – the DNS over HTTP settings are now moved to the “Privacy and Security” section. It now allows On or Off (this is already set).
However, below that there is also a few more options listed under Enable DNS over HTTPS using:
Default Protection (this is default option already enabled by Firefox);
Increased Protection;
Max Protection
and Off.
Which one should be chosen here – Off?
Using safebrowsing (even, sadly, in Firefox) is like having a bodyguard that is always with you wherever you go.
So, he is standing next to you when you are in the toilet doing your necessities, and when you are in your bedroom doing your private stuff.
That, although creepy, could be acceptable if you could trust that said bodyguard will respect your privacy.
But in this case, the bodyguard is provided by google.
The bodyguard is actively monitoring what you do in your bedroom and sending that information to google.
No thanks. I’ll take my chances with running into malware. I’ll use common sense to protect myself from phishing. And I am using Firefox on Linux (KDE Neon), so I am not defenseless against malware.
Yes, I read all the explanation at the linked site. It may seem convincing, but in the end, it admits that safebrowsing is sending information about your online activity to google. And it asks you to believe in google’s privacy policies, which is the same as believing in politician promises.
If you use anything somehow related to google, you can be certain that your privacy will be violated one way or another.
Firefox is a real private browser, not that “Google in disguise” called Brave. This guide is perfect for maximizing the anonymity of Firefox, while also using a VPN, of course.
I just installed a new version of Firefox on Windows 11, and I noticed some small differences. Main ones:
– The DNS over HTTP settings are now moved to the “Privacy and Security” section (it is no longer in “General”)
– The network.cookie.lifetimePolicy setting is no longer available (or, at least, I could not find it)
Weird, I just checked this setting on Firefox 120.0.1 – Windows 11 and it’s there
Thanks for this helpful article. An update would be great. I encountered the same change Dell Inspiron 7430 noted in November 2023, and I’m wondering whether to change the network.cookie.cookieBehavior.pbmode numerical value to other than 5 as well, but have not found sufficient information in a Web search to mess with it.
Hi. Thank you for the amazing info on your site.
My knowledge of technology is very limited, but I am trying toteach myself how to go about things in a more mindful way.
I installed ublock origin on my pc browser. Another ad blocker called Ad Guardian was also mentioned, where I first read about these extensions.
However, I have just come across this, on a pc security site.
Would you be able to let me know what you think about it?
Below is the copied text.
Thank you.
“Ad Guardian is advertised as a tool that blocks annoying advertisements whilst browsing the web, however, it is classified as adware, a potentially unwanted application (PUA).
Apps of this type display unwanted ads and record browsing data. Furthermore, most people download and install PUAs accidentally. We recommend that you uninstall Ad Guardian and any other PUAs installed on your browser or computer.
Ad Guardian adware
Typically, PUAs target browsers such as Google Chrome, Mozilla Firefox, and Internet Explorer. When installed, Ad Guardian feeds users with unwanted ads that conceal underlying content of visited web pages. Adware-type apps often display pop-up ads, coupons, banners, surveys, and others.
Clicking these causes redirects to dubious sites, which are often used to advertise potentially unwanted, untrustworthy applications. Additionally, some of these ads (if clicked) might execute scripts that trigger download and installation of dubious apps.
Note that most PUAs gather information relating to users’ browsing activity such as IP addresses, geolocations, URLs of visited pages, entered search queries, and other similar details. Some PUAs also record sensitive details. The people responsible for these apps (developers) share all data with other parties who might be cyber criminals.
These people misuse private data to generate revenue. Therefore, having adware-type apps installed can lead to unwanted downloads, installations, or other problems relating to privacy, browsing safety, and so on”.
how does one disable “auto-update?” It’s my computer, and I want to view change logs before I do anything.
enterprise policy generator addon
could you not set up a virtual? browser that appears like the same fingerprint for everyone and filter/tweak it to your own preferred settings once it is retrieved.
a one size fits all that is tailor made after it arrives past your firewall…
an alias for your computer that looks exactly like all the other computers online
Firefox: despite setting it up to max privacy as far as I can tell (eg STRICT), loads of intrusive (eg geolocation) cookies get through…not sure its ok any more
I do not have proof, but based on the ever increasing look, feel, marketing, extra product offerings, etc. I would have to believe that there are a lot of developers that either actively work for Google on Chrome or have in the past. Each month the difference between the browsers seems to blur more and more. I recently installed the Mullvad Browser based on Firefox and what a difference. That is much closer to the goal Firefox should be working as far as security and privacy. Look at the Opera browser. It used to be a great alternative, but today it’s an eyesore of candy looks as it completely abuses any sense of security or privacy either one. I would never install that on my system these days.
@PShell, unfortunately there is no portable version of Mullvad Browser. I have several portable versions of browsers installed such as Firefox, Palemoon, Brave and more.
I think any recommendations for the Brave needs to be pulled from this site. If you read the [negative] comments online, here, and everywhere you won’t install Brave except in a virtual environment.
You’re so right about Opera!
@CSum Brave is the only browser that gives you fingerprint randomization, something Mullvad Browser doesn’t do, which means you are still being tracked.
Firefox has never been a “private” browser, every add-on you install makes your fingerprint stand out, and many add-ons collect your browsing history and sell it. So much for “privacy”.
Brave has everything built into the browser, like a REAL private browser would. You will not get privacy from Firefox or Mullvad browser.
Any advice on Avast taking over “I don’t care about cookies”? I see the code has already been forked into a community version.
Hi Sven.
First, thank you for putting all of this together. I’m about to move to Canada, so looking up and understanding things like this have become a priority for me before I actually move and this (and many other section on this site) have been a major help to me. Not just in setting things up, but also with understanding how things work under the hood to some extent.
Second, I had a question regarding the HTTPS. Firefox has an option to use HTTPS-only mode in either all windows, private windows only, or never. The default option seems to be to “Don’t enable HTTPS-only mode”. Would turning it on be a good idea? Thank you in advance.
DNS over HTTPS is now located in Settings>Privacy and Security
Hello Sven,
First I wanted to thank restoreprivacy team for your work. It’s invaluable. Since I found the site, I have changed many habits and relied upon your advises for many software choices (mail, messenger, browser, system).
This guide is my first step whenever I have access to a new system. Install Firefox, follow the guide.
I see it’s been updated a few times, but you never mentioned the default parameter of the network.cookie.cookieBehavior rule. It’s set to 5 by default, is that a new new cookie jar policy of some sort ?
Cheers
Hi Sven/Valentin.
I have the same query network.cookie.cookieBehavior rule. It’s set to 5 by default, is that a new new cookie jar policy of some sort ?
I can’t seem to find any documentation identifying this value. Firefox 110.
I’d also echo Ventin in this: Thanks, many, many thanks for all advice and information.
Dod
“Reject (known) trackers and partition third-party storage.”
https://developer.mozilla.org/en-US/docs/Web/Privacy/State_Partitioning
Hi, what breaks timezone?
Some sites display wrong time. I tried webgl.disabled and geo.enabled to turn back, but it didn’t affect.
Any idea?
Thanks.
This is because of “privacy.resistFingerprinting”, which spoofs your timezone to UTC. I recommend turning it off and instead using something like Chameleon if you want to use another time zone.
webgl.disabled breaks some things (IIRC WWE2K Upload) and privacy.firstparty.isolate breaks login stuff like google pop up stuff. So if you wanna use them, may want to toggle the fixes off for a bit. I know the dom clipboard one breaks twitter image pasting.
Hi Sven
Thanks for updated info.
In ‘network.cookie.cookieBehavior’, by default it is set to number 5.
It was not before with past version.
What is this means ?
Should we stick to changing it to 4 ?
I think with the new firefox updates, set to 5 should be the safest value. (I think).
Mozilla is going to implement support for Firefox add-ons designed to comply with Google’s Manifest V3. While Apple has even endorsed the standards, Mozilla may have little choice to do this resulting from Chromium browsers making up most of the browser market. It is looking like extensions, like uBlockOrigin, will not be affected.
https://www.theregister.com/2022/11/17/mozilla_next_week_will_begin/
Hi Sven Taylor,
Thank you for this guide. It helped me set up Firefox even better 🙂
Though I think I have found a unexpected (and for me: unwanted) result on this setting:
privacy.resistFingerprinting = true
I like Firefox to open maximized when I start it. But with this setting it starts in a small window.
I have now tested this couple of times, and every time I apply this setting, close Firefox, and reopen it,
it then opens in a small window in stead of a maximized window.
My OS is Xubuntu 22.04.1
with Firefox 103.0.1 (64-bits) (installed via snap)
My “solution” for now is to leave this setting on “False”. I am not sure how vulnerable my privacy is this way, but the unexpected window-behaviour is too annoying for me.
Thank you for all other settings anyway, most of them were new to me!
Regards,
Steven
I use the little add-on: ” Maximize All Windows” (minimalist version).
@ Rens
Thank you for your reply.
For me a third-party add-on sounds not safer than [privacy.resistFingerprinting = false].
And I would rather have less add-ons (though I reckon that the addons are part of the strength of Firefox).
Phew! Wish I had seen your post before going through a couple hours of shenanigans! I’m on Ubuntu and ran into the same glitch, have now posted here there and everywhere and tried all kinds of fixes. Many thanks!