Keybase is a secure messaging and file-sharing service. It is a centralized system that applies end-to-end (E2E) encryption to every message you send and every file you store.
You don’t need to trust Keybase. You only need to trust math. — Chris Dixon, in his message announcing a $10.8 million investment in Keybase.
Keybase was designed to make public key cryptography more accessible to regular people. Used properly, public key cryptography can eliminate most of the problems we have with hackers and unwanted government surveillance of the Internet.
But the tools for using this kind of encryption are generally too complicated for all but the most hard-core privacy aficionados. Keybase is meant to eliminate most of the geek work required to use public key encryption. In this Keybase review you will get a sense of how well they have succeeded.
While Keybase can do everything from encrypted chats to providing a massive amount of free cloud storage, to storing your cryptocurrencies, we are going to concern ourselves primarily with Keybase’s role as a secure messaging service. Let’s start by looking at the pros and cons of Keybase messenger capabilities.
UPDATE: Shortly after publishing this review, Keybase announced it was acquire by Zoom. This is bad news, and we have updated this review (below) to explain why. With the new ownership change, and the privacy-abusing practices of Zoom, Keybase is no longer recommended.
+ Pros
- End-to-end (E2E) PGP encryption for messaging and file sharing
- Encryption algorithms: XSalsa20, Poly1305, Ed25519, SHA512
- Open source apps
- Self-destructing (exploding) messages
- Users can be logged in on multiple devices simultaneously
- 250GB of encrypted cloud storage
- Blockchain-based to protect against tampering
- Completely free of charge.
– Cons
- Now owned by Zoom with ties to China (privacy concerns)
- Complicated to install and configure
- Confusing for regular users
- Chat not as easy to use or full featured as competition
- Server code is not open source
- Small user base (~450,000 users)
Now that we’ve touched on the pros and cons we found in this Keybase review, let’s cover some of the major features.
Keybase features summary
Here are some key features to consider when deciding whether the Keybase is right for you:
- Secure, end-to-end encryption protects the contents of your messages and files
- Keybase security was independently reviewed in 2018/2019
- Clients for Android, iOS, Mac OS, Windows, Linux, and browser extensions
- Keybase is a complicated suite of encrypted services that includes individual instant messaging and team chat
Keybase company background information
I haven’t been able to find much information on Keybase, Inc. the company behind the Keybase app and service. The company was co-founded in 2014 by Max Krohn and Chris Coyne, the founders of the OKCupid dating service. In 2015, the company raised $10.8 million in a Series A round led by a16z.
Zoom acquires Keybase
One major update to this Keybase review is the change in ownership. On May 7th, 2020, news broke that Zoom had acquired Keybase. Many longtime Keybase users vented their frustration on Twitter with the announcement.
Why is this concerning?
First, Zoom has been in the news a lot lately for privacy and security concerns:
- Zoom iOS App Sends Data to Facebook Even if You Don’t Have a Facebook Account
- New York Attorney General Looks Into Zoom’s Privacy Practices
- ‘Zoom is malware’: why experts worry about the video conferencing platform
- Zoom is Leaking Peoples’ Email Addresses and Photos to Strangers
- Zoom needs to clean up its privacy act
That’s just a short reading list. There are many articles covering the privacy and security concerns of Zoom, but you get the point.
The second problem is that Zoom has ties to China, which is a very bad jurisdiction for privacy.
This article details Zoom’s “surprising links to China” that were discovered by a team of researchers in Canada.
The report points out that Zoom may be legally obligated to share encryption keys with Chinese authorities if the keys are generated on a key management server hosted in China. If the Chinese authorities or any other hypothetical attacker with access to a key wants to spy on a Zoom meeting, they also need to either monitor the internet access of a participant in the meeting, or monitor the network inside the Zoom cloud. Once they collect the encrypted meeting traffic, they can use the key to decrypt it and recover the video and audio.
Given the widely-documented background of Zoom, it is no wonder that so many Keybase users have closed their accounts and moved on to another secure messaging platform.
Where is your Keybase data stored?
Your Keybase data is stored on servers located in the United States. This is not ideal, since the US government runs mass surveillance and intelligence operations against companies and systems located in their territory.
The US is also a member of the Five Eyes surveillance alliance and shares data with other member states. Much of the privacy risk this would otherwise entail is reduced because Keybase uses end-to-end encryption on all your messages and files.
Keybase third-party testing and audits
When you are looking for a secure messaging service, or even a secure email service, it would be ideal to be able to verify that the code does what the publisher claims it does. In the real world, that’s virtually impossible. Even when the service’s code is open source, do you have the expertise or the time to review it? Even at that, verifying that the code should work doesn’t mean that it actually will in the real world.
This all argues for any secure service (especially ones like Keybase that are based in the United States) be thoroughly audited by a qualified third party. Not all “secure” services can show you the results of this kind of audit, but Keybase can.
Keybase Protocol Security Review
In October 2018, the NCC Group published version 1.0 of their Protocol Security Review for Keybase. This review found five issues in the design of Keybase. The company subsequently fixed all of these issues prior to the release of the final report in February 2019.
Many VPNs are also undergoing security audits and reviews, including NordVPN and now also Surfshark.
Keybase hands-on testing
For purposes of this Keybase review, I tested with the Windows and Linux desktop apps, along with the Android mobile app.
Installing the Keybase desktop app
Keybase officially supports the following desktop platforms:
- Windows
- Mac OS
- Linux (common 64-bit and 32-bit distros)
The process for installing Keybase and getting it ready to run is more complicated than for most messenger products. Let’s walk through it now.
- Create an account – Go to Keybase.io and click the Login link at the top of the home page. This opens the Login dialog box.
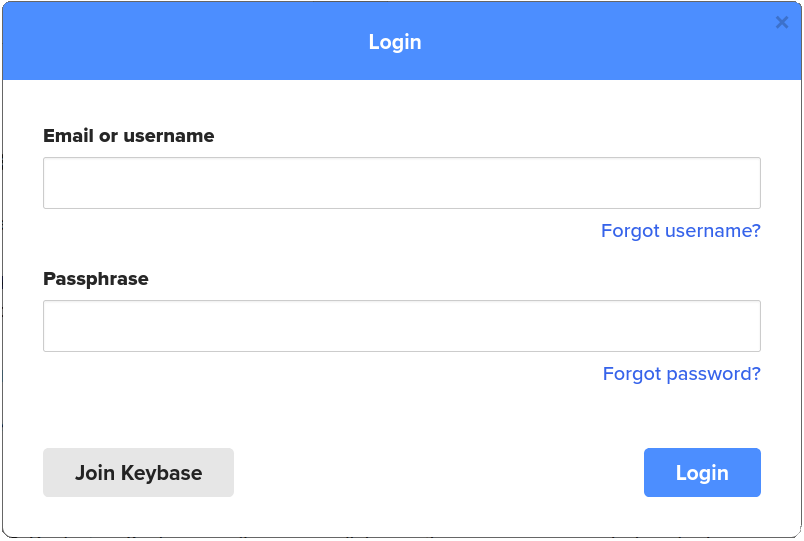
- Ignore everything else in this dialog box and click the Join Keybase button to create your account. This opens the Quick! Join Keybase dialog box.
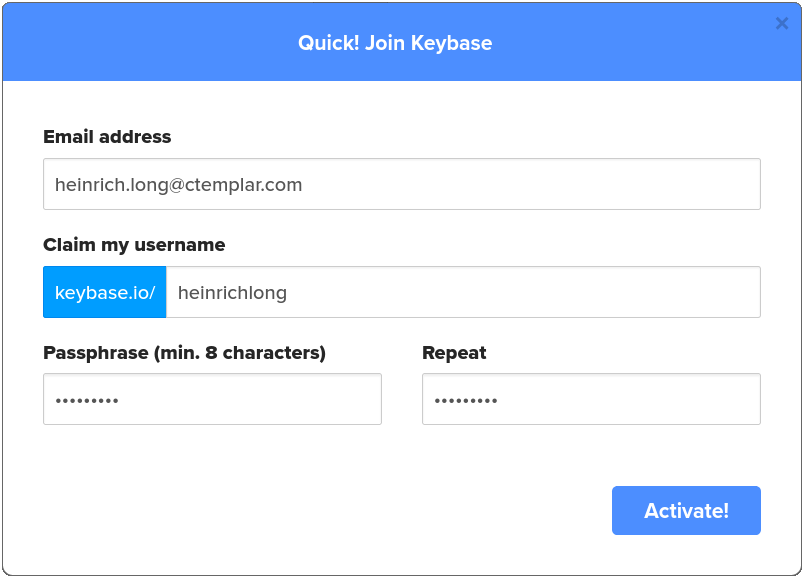
- Keybase opens to your home page. There is still action required before you can do anything useful. Click the Action required button, circled in red in the preceding image. This opens a list of things you need to do now. First up is to install Keybase on your computer.
- Click Install Keybase. This takes you to the Keybase app download page.
- Select your operating system from the Installation list on the left side of the page. From here, the process varies by operating system.
Keybase Windows and Keybase Mac OS apps
Keybase Windows or Keybase Mac OS installation is simply a case of downloading and running the version of keybase_setup the page presents you, then following instructions.
Keybase Linux app
As is often the case with Linux apps, installing the Keybase Linux app is a bit of a project. You’ll need to know which Linux distro you are using, and enter the correct commands in the Linux terminal. The instructions are here. There is also a Linux User Guide written for every level of Linux user if you want more detailed instructions.
Working with Keybase
Once you complete the installation process, launch the Keybase desktop app and log in. You’ll see a window very much like this one:
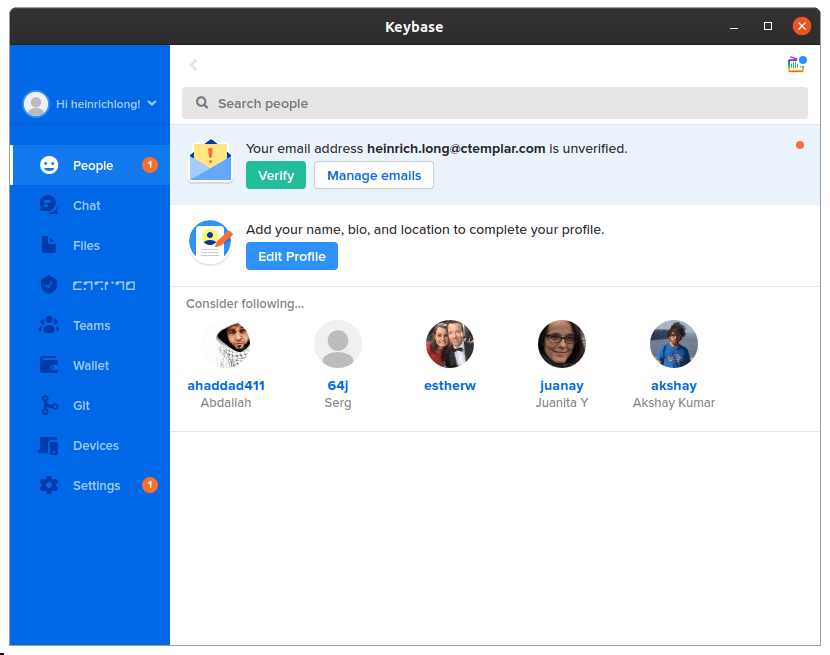
You’ll want to do whatever housekeeping Keybase requires (in my case verify my email address and update my profile). Once you get through all that, you are ready to start an encrypted chat.
Well, almost.
You still need to find someone to chat with. Select the People icon to search Keybase for someone to talk to. Enter the real name or the Keybase username of the person you want to talk to. When you find them, you can click their name to see their Keybase profile:
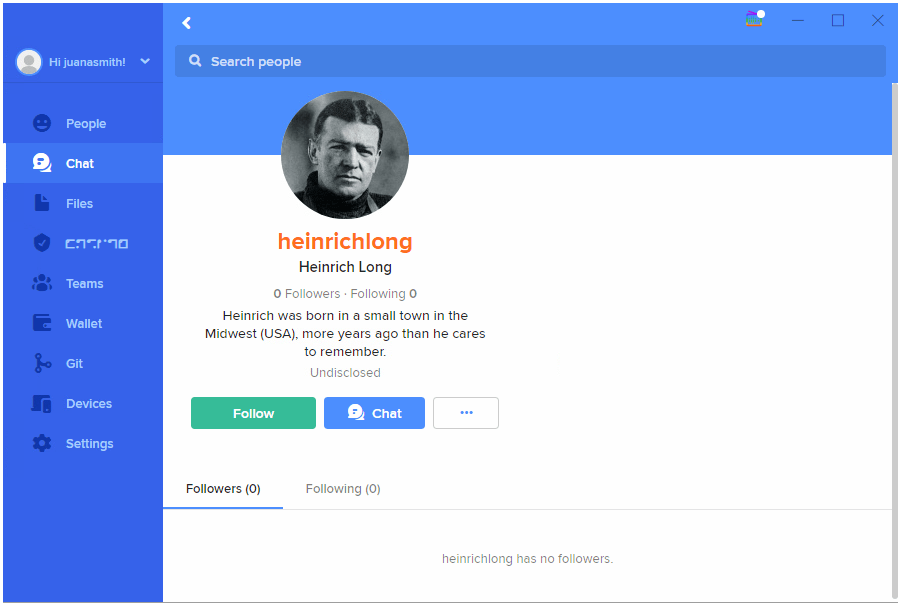
It the person’s profile looks good, and it seems to be the person you want to talk to, you can click Chat to send secure, end-to-end encrypted messages back and forth. Only you and the person in the chat will be able to read them. You can also create exploding messages, which are automatically deleted from your devices and those of the recipient after the amount of time you specify.
If you are looking for group communications, Keybase allows you to create Teams. Team give you Slack-style communication, with the added benefit of E2E encryption.
Note: Keybase urges you to “follow” anyone you find interesting on the service. At a very high level, following someone makes Keybase more secure and allows you to know that you are talking to the same person when you contact them from a different device. It sounds simple enough at this level, but if you want to really understand what’s going on, the plain English explanation of following on Keybase is around 1000 words long.
Additional features
Beyond what we’ve discussed so far, Keybase has a lot of useful features that go beyond secure messaging. Here are some of them:
- Secure file-sharing – Encrypted public and private file sharing.
- Online identity verification – Securely store identity documents in Keybase and share them as needed with just a few clicks.
- Public and private teams – Create public or private teams for personal or business use. All communications and other team data are end-to-end encrypted.
- Encrypted Git repositories – Use encrypted Git repositories to securely track changes in code or any other documents.
- Stellar wallet – A secure wallet for the Stellar Lumens cryptocurrency.
- Bots – Create your own Keybase bots or use pre-built ones to add functionality to your Keybase activities.
- 250 GB free storage per user – Free, secure storage automatically granted to every user. Note that this is not a file sync solution like MEGA.nz, or Sync.com.
Keybase mobile apps
For mobile testing, I downloaded the Keybase Android app from the Google Play store and installed it on my Galaxy S9+. To log in, all you need to do is enter your username. However, once you do that, you need to authorize your phone. As the Keybase mobile app explains,
For security reasons, you need to authorize this phone with another device or a paper key. Which do you have handy?
It then lists the devices that Keybase knows are associated with you. Select one that you have access to at this moment, and follow the instructions that appear on the phone to authorize the phone using the other device.
From there, you’ll be able to use the mobile app to chat like you would expect. Keybase allows you to be online with multiple devices at the same time, making it easy to stay connected at all times.
Support
User support is one of Keybase’s weak areas. You won’t find the typical Support section where you can request help, or even the extensive Telegram FAQ page. Keybase offers you a Documentation page and a blog. And neither of them is geared toward a regular user with basic questions. Here’s the Documentation page.
How secure and private is Keybase
Keybase appears to be very secure. End-to-end encryption on everything by default is great, and the few issues that were cited in their third-party audit were fixed by early 2019. Add that I’ve not seen any reports of the Keybase system being hacked, ever, and this looks to be a very secure system.
On the downside, Keybase collects a lot of information about you and your activities that is not encrypted. Data that they collect and use for various purposes includes: your name, avatar picture, email address, social media handles, the names of the teams and subteams you join, their membership, when they were formed, account activity, your Keybase user ID, your IP address (which is stored only temporarily), the type of device you’re using, and the operating system you’re running.
That’s a lot of data. Add the fact that the service is based in the United States, where government mass-surveillance is common, and there is reason to be concerned about your privacy. If this concerns you, please read the Keybase Privacy Policy for more details, or check out some of our other secure messenger reviews.
Keybase business features
Keybase doesn’t have a business version of the product. The ability to create public and private teams, as well as public and private file sharing, could certainly be valuable for a business. As of now, however, all the features are available to everyone for personal or business use, for free.
Keybase pricing
As of today, everything Keybase publishes is free of charge. Further, the company states they will never run ads on Keybase. The company has stated that they may add some optional paid features in the future, but the core product is supposed to remain free of charge.
Keybase review conclusion
Keybase is a powerful suite of secure tools that make PGP encryption more practical for general use. It may be a good secure messenger for your unique situation, but there are also some other great options to consider. Unfortunately, I think Keybase may be a bit too complicated and technical for the average user.
With Zoom now owning Keybase, I would recommend considering other options. Zoom has a troubling background with privacy and security issues. Additionally, Zoom has deep ties to China.
Is Keybase right for you?
Even if you are well versed in privacy technologies like public key encryption, and are willing to learn the Keybase way of doing things, there are other secure messaging services that are easier to use, record less personal information, and have larger user bases than Keybase. I suggest you check out the other secure messaging services we’ve reviewed before investing a lot of time testing Keybase.
And here are the other Secure Messenger reviews on RestorePrivacy:
Signal Review
Threema Review
Telegram Review
Session Review
Wickr Review
Wire Messenger Review
This Keybase review was last updated on April 27, 2024.

The underlying idea is good, but the implementation is terrible.
Everything is tied to their website, which is rarely accessible or stable.
And even if everything is fine with the site, the software itself is full of bugs.
Let’s add to this the “security” policy (due to which, in the event of critical failures, it is faster to create a new account than to wait 5 days or longer if you need an answer on Github) and the result is a completely unacceptable product.
Super thorough and honest breakdown. Well-researched and well-written. You’re doing God’s honest work!
Well, I didn’t join Keybase since it started, but certainly before its acquisition by Zoom (I did use OkCupid in the distant past and had no idea they were by the same guys! What a change of business model 🙂 ). While it’s true that the server(s) used by Keybase are proprietary technology, they have been quite open saying that they use Amazon’s AWS for that; and the client software is open source and can be extensively tested by a knowledgeable community of crypto-experts to see if it does what it claims it does — notwithstanding whatever happens on the server-side.
You see, on open-source software, you cannot ‘hide’ information that may be sent to a remote server. There will only be ‘security through obfuscation’, and, at some point, someone will clearly see through such a ruse. Keybase lists in minute detail what they collect and how; this can be validated by looking at the client code to confirm that it doesn’t send anything it shouldn’t.
Granted, Keybase does store some information about their users; these are actually stated clearly on their Policy Page. They also claim that they do not resell that data to any third party; we obviously have to take their word on it, since that cannot be independently verified. But we’re talking about things like joining/leaving groups, IP addresses, how often connections are made, and so forth; important for profiling data, yes, to a degree, but they won’t associate any real data with the account ID, just, well, they will knows that user X comes from country Y and does Z and W during the day, and has joined the team of #BarbarianGirlsfromHell.
Hardly a thing to worry about.
Upload and encryption speed are too slow for me. I just tried uploading a 20GB folder and it’s taking forever on a gigabit connection. Also it takes up around 20% of your disk space for cache use and there is no easy way to turn this function off.