
In this guide we cover all aspects of browser fingerprinting and device fingerprinting in 2022. In addition to explaining what exactly this is, we’ll also show you how to protect yourself against these threats.
Many people use VPN services to hide their IP address and location – but there is another way you can be identified and tracked online. That is through browser fingerprinting.
Whenever you go online, your computer or device provides the sites you visit with highly specific information about your operating system, settings, and even hardware. The use of this information to identify and track you online is known as device or browser fingerprinting.
As browsers become increasingly entwined with the operating system, many unique details and preferences can be exposed through your browser. The sum total of these outputs can be used to render a unique “fingerprint” for tracking and identification purposes.
Your browser fingerprint can reflect:
- the User agent header
- the Accept header
- the Connection header
- the Encoding header
- the Language header
- the list of plugins
- the platform
- the cookies preferences (allowed or not)
- the Do Not Track preferences (yes, no or not communicated)
- the timezone
- the screen resolution and its color depth
- the use of local storage
- the use of session storage
- a picture rendered with the HTML Canvas element
- a picture rendered with WebGL
- the presence of AdBlock
- the list of fonts
Is browser fingerprinting accurate?
Some researchers have found this method of identification to be extremely effective.
Why is this being done?
Browser fingerprinting is just another tool to identify and track people as they browse the web. There are many different entities – both corporate and government – that are monitoring internet activity, and they all have different reasons for doing so. Advertisers and marketers find this technique useful to acquire more data on users, which in turn leads to more advertising revenue.
Some websites use browser fingerprinting to detect potential fraud, such as banks or dating websites, so it’s not always nefarious.
Surveillance agencies could also use this to identify people who are employing other privacy measures to cloak their IP address and location, such as with VPN services or the Tor (onion) network.
Browser fingerprinting test websites
One good test website to see all of the information that is being revealed by your browser is
ipleak.net.
With ipleak.net, you will want to scroll down to the “Geek Details” section where you will be able to see:
- Detected information
- System information
- Screen information
- Plugins information
- Mime-Types information
- HTTP Request Headers
There are also a few websites that reveal browser data and also assess a “uniqueness” score based on your variables in comparison to their database of browsers.
- amiunique.org is another good resource. It is open source and provides more information and updated fingerprinting techniques, including webGL and canvas.
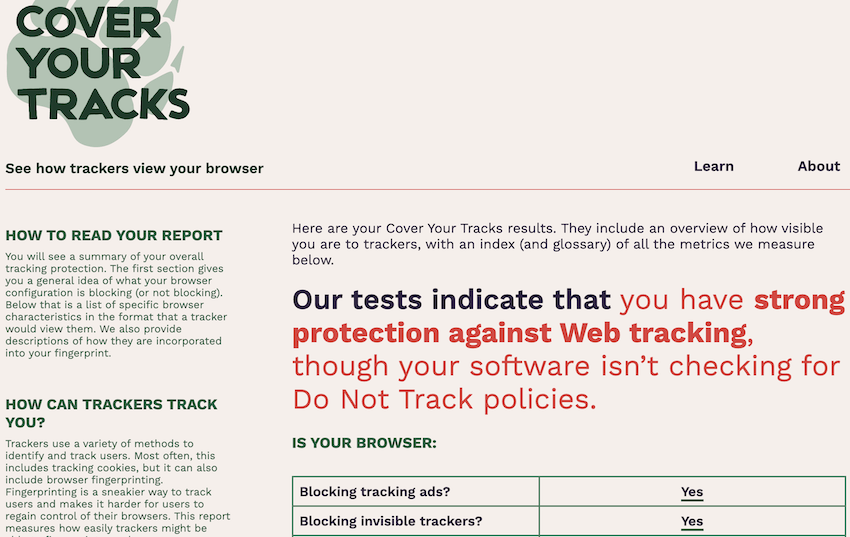
- Cover Your Tracks is run by the Electronic Frontier Foundation. You can learn more here.
Cover Your Tracks is the updated version of a project the EFF has been working on for many years. It gives you a pretty good picture of how susceptible your browser is to finger printing.
How to mitigate your browser fingerprint
Before we jump into potential solutions, it’s important to note that implementing browser fingerprinting protection methods may break some websites. Be sure to research these different options carefully before adjusting your browser settings.
Another consideration is your threat model. How much privacy do you need or want? The answer to that question will be different for every user.
Lastly, I use the word “mitigate” rather than “solve” because browser fingerprinting is a very complex and evolving issue. For example, a new study revealed that there’s nothing you can do to mitigate some fingerprinting attacks on smartphones (discussed more below).
Here are some good ways to mitigate your browser fingerprint:
1. Browser modifications and tweaks
Depending on the browser you are using, you might have some different options for tweaks and modifications to mitigate browser fingerprinting. Below we’ll discuss various Firefox and Brave browsers, which are both secure and private browsers.
Brave browser fingerprinting
Although it is based on Chromium, the Brave Browser may be a good option for those wanting a simple, privacy-focused browser that blocks tracking by default and still supports Chrome extensions. Brave allows you to enable fingerprinting protection, which is under the Brave Shields settings:
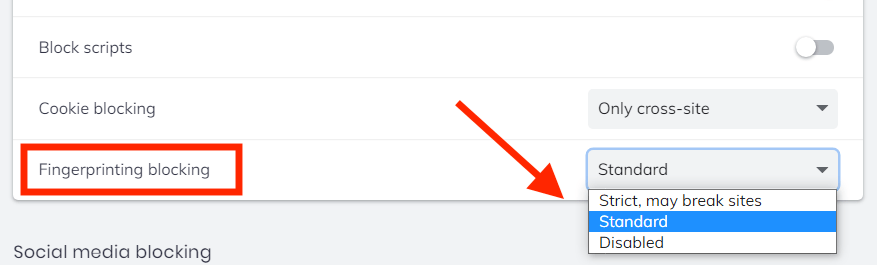
See also this article on Github discussing different aspects of fingerprinting protection in Brave.
Firefox browser fingerprinting
Firefox is a good browser for privacy and security, and it can also be modified and hardened for your unique needs. (For an overview of Firefox privacy tweaks, see the Firefox privacy guide.) The first thing you need to do is type about:config into the URL bar of Firefox, hit enter, then agree to “accept the risk” and make the following changes:
- privacy.resistFingerprinting (change to true) – Changing this value to true will offer some basic protection, but it’s far from a complete solution. The privacy.resistFingerprinting preference was added to Firefox as part of the Tor Uplift project and it continues to be improved.
- webgl.disabled (change to true) – WebGL is another tricky issue for privacy and security. Disabling this preference is generally a good idea.
- media.peerconnection.enabled (change to false) – Disabling WebRTC is a good idea since this can reveal your true IP address, even when you are using a good VPN service. See the WebRTC leak guide for more details and how to disable WebRTC in other browsers.
- geo.enabled (change to false) – This disables geolocation tracking.
- privacy.firstparty.isolate (change to true) – This is another great update from the Tor Uplift project that isolates cookies to the first party domain.
Note: This is just a brief overview of changes that improve your privacy and help to mitigate your browser fingerprint. Nonetheless, there are many different factors that go into fingerprinting and you may still have a unique fingerprint even with these changes.
Firefox with the ghacks user.js file
Another great option is to run Firefox with a unique user.js file, such as the ghacks user.js. This is a custom Firefox configuration file that has been modified for more privacy and security. I like this option because it can save lots of time with setup and is regularly updated and improved. See the Wiki page for an overview and setup instructions.
When I tested a fresh install of Firefox with the ghacks user.js file, amiunique.org showed my browser fingerprint as as not unique.
2. Browser extensions and add-ons to minimize or spoof your fingerprint
There are a number of different browser extensions and add-ons that you may find useful. With that being said here are a few things to remember:
- Be careful with third-party extensions, which could potentially undermine your privacy and security.
- Be mindful that using extensions may make your browser fingerprint more unique (many factors).
Now that we’ve gotten those disclaimers out of the way, let’s examine some browser add-ons that may be useful:
Firefox browser:
- Canvasblocker by kkapsner – Protects against canvas fingerprinting methods (source on GitHub)
- Trace by AbsoluteDouble – Protects against various fingerprinting methods (source on GitHub)
- Chameleon by sereneblue – Allows you to spoof user agent values (source on GitHub)
There are many other Firefox add-ons you may want to consider as well, which are discussed in the Firefox privacy guide. Some of these add-ons are also available for Chromium-based browsers, such as Brave.
Some people recommend spoofing different user agents through a browser extension, while others suggest this is a bad idea because it might make you more “unique”. Of course, there are many factors to consider, but adding noise to your fingerprint may not be a bad strategy.
For example, with Chameleon, you can cycle through different user agents at various time intervals.
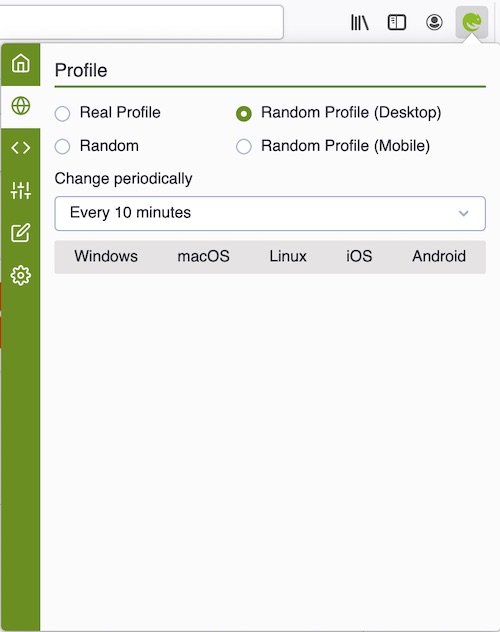
Now let’s look at another option for modifying your browser fingerprint: the use of virtual machines.
3. Virtual machines
You can also consider running different virtual machines, which can utilize different operating systems on your host computer. VirtualBox is FOSS and offers an easy way to run different Linux VMs for more privacy and security. There are many different video tutorials online, depending on your operating system and the VM OS you are looking to use.
Virtual machines offer numerous advantages in terms of privacy and security, while also protecting your host machine. For privacy, VMs allow you to easily spoof different operating systems and also chain VPN services, as explained in the multi-hop VPN guide. This also helps keep your host machine secure by isolating a virtual environment. If the VM were to be compromised, simply delete it and create a new one. You can also use different VMs for different purposes.
4. Tor Browser
Another option is to use the Tor browser, which is simply a hardened and protected version of Firefox. It includes numerous privacy and security modifications that are built into the default version:
- HTTPS Everywhere
- NoScript
- Anti-tracking features
- Canvas image extraction blocked
- WebGL blocked
- Operating system cloaking (shows as Windows 7 for all users)
- Timezone and language preferences blocked
The key here is to use the default version (the developers do not recommend adding any plugins or extensions because this could compromise the browser’s effectiveness).
You can get the latest version of the Tor browser here.
The default version of the Tor browser is configured to run with the Tor (anonymous/onion) network. While the Tor network does have added benefits in terms of privacy, it also has a number of disadvantages:
- Your internet speed will be reduced to around 2 Mbps, making streaming videos or music nearly impossible
- Tor only encrypts traffic through the browser, rather than encrypting all traffic on your operating system like a VPN
- Tor is vulnerable to IP leaks, especially with Windows
- Tor is not safe to use when torrenting (see the Best VPNs for Torrenting guide)
- Tor was created by the US government and is still funded largely by US government grants
- Some consider Tor to be compromised
Ultimately, like all privacy tools, Tor has both pros and cons.
Note: You can also first connect to a VPN and then load the Tor browser as normal with the VPN running in the background. This will hide your real IP address from malicious Tor nodes and give you an extra layer of protection.
5. Don’t expect much privacy on a smart phones
As we’ve covered before, most “smart” devices are data collection tools for various entities.
Smart phones are especially vulnerable to browser fingerprinting. A team of researchers at Cambridge published a paper highlighting how smartphones can be fingerprinted using internal sensors – and there’s nothing the user can do about it.
The paper delves into the technical details, but here’s a brief overview of their findings:
- The attack can be launched by any website you visit or any app you use on a vulnerable device without requiring any explicit confirmation or consent from you.
- The attack takes less than one second to generate a fingerprint.
- The attack can generate a globally unique fingerprint for iOS devices.
- The calibration fingerprint never changes, even after a factory reset.
- The attack provides an effective means to track you as you browse across the web and move between apps on your phone.
Aside from the sensor issue, there are many other reasons for avoiding smart phones if you expect privacy. See our article on controlling communication channels for more info on this topic.
Use a good VPN service
Although a VPN alone won’t protect you against browser fingerprinting, it is a very important privacy tool to hide your IP address, hide your location, and keep your data secure.
If you’re not using a good VPN, your internet provider can easily monitor all your online activity by recording your DNS requests. In many countries, such as the UK and Australia, this is mandatory. Internet providers in the US can also monitor and record their users, and since March 2017, they can also sell this information to third parties (advertisers).
An interesting report from the Federal Trade Commission in the US highlighted how all major internet providers are collecting vast amounts of private data and sharing this data within a wide network of partners. See our article for more details:
Internet Service Providers are Logging Everything You Do Online
Going through all the hassle to protect yourself against browser fingerprinting may be a waste of time if you aren’t using a good VPN that will encrypt your internet connection and hide your IP address and location. The best VPN services report discusses the top recommendations based on the latest results.
For those concerned about privacy (like us), we strongly recommend going with an audited no logs VPN, preferably one that has passed multiple audits.
As mentioned above, combining VPNs also adds additional privacy and security while distributing trust across different VPN providers.
Browser Fingerprinting FAQs
Below are some of the other questions we see regarding browser fingerprinting.
Browser fingerprinting is a method to identify and track you online based on numerous different variables, including your operating system, timezone, browser headers, plugins, cookie preferences, tracking preferences, screen resolution and more. By aggregating these browser variables, third parties can create a unique fingerprint of your browser so that you can be identified and tracked online.
Browser fingerprinting is used primarily by advertising agencies and data brokers. By creating a unique browser fingerprint, ad agencies and data brokers can track your activities as you browse different websites. Your browsing activity can then be linked to your unique browser fingerprint, which allows you be targeted with ads based on your online activities. Additionally, your activities and identity can be sold to third parties by data brokers and other ad-tech intermediaries.
No, a VPN alone will not protect you against browser fingerprinting. While a VPN will hide your true ISP-assigned IP address and location, it will not protect you against browser fingerprinting, which is based on unique variables without your browser and operating system. To protect yourself against browser fingerprinting, you will need to modify the settings within your browser, as we describe above. However, you should still use a VPN to hide your IP address and location to better protect your online privacy.
Private browsing alone will not protect you from browser fingerprinting and it also won’t hide your IP address or location. In essence, private browsing is not actually private. We explain why incognito/private browsing is not private and the steps you can take to actually have more privacy and security online with your browser.
Use browser fingerprinting protection in 2022
While browser fingerprinting may seem like a daunting issue to some, mitigating your browser fingerprint is relatively easy. For those seeking the highest levels of privacy and security, I’d recommend utilizing virtual machines and perhaps chaining different VPN services (using more than one VPN at the same time).
As a general rule of thumb, Firefox remains a great all-around browser after some modifications and configuration. The secure browsers guide also discusses various options, while the Firefox privacy modifications guide takes a deep-dive into tweaks, extensions, and custom configuration.
Another issue to consider, which was not mentioned in this guide, is using a good ad blocker. Ads today basically function as tracking – they record your browsing habits so you can be hit with targeted advertisements. A good add-on is uBlock Origin, but there are other recommendations in the ad blocker article and privacy tools guide.
This browser fingerprinting guide was last updated on April 27, 2024.

Is it possible to prevent tracking by fingerprinting.com using typical browser such as Firefox?
Any trustworthy and working extension?
All for one or one for all?
Device Fingerprinting vs Browser Fingerprinting vs Cookies (source) [https://www.cloudwards.net/device-fingerprinting/]
Although device fingerprinting, browser fingerprinting and cookies can all be used to track a website visitor’s device, they differ in a few key ways.
The chief difference is that device fingerprinting uses mostly hardware data.
Browser fingerprinting uses only browser data.
Cookies are stored on a user’s device.
Let’s go into each of these individually to give you a clearer picture.
1. Device Fingerprint
Device fingerprints create device IDs using mostly hardware-related data. Although a browser fingerprint can be part of a device fingerprint, it’s not necessarily always included. A device’s fingerprint typically holds a lot more data than a browser fingerprint does, including all the information we listed previously.
2. Browser Fingerprint
Unlike a device fingerprint, a browser fingerprint stores only data about your browser, such as your browser version, installed plugins and fonts, and your browser login profile. It’s also much less persistent than a device fingerprint, as it can be changed by altering your browser settings.
3. Cookies
Cookies are text files that store information about your browsing sessions, including logins, app use, and settings and preferences.
Websites and apps both use cookies for this purpose, which means there are two types of cookies: app cookies and browser cookies. Cookies are always stored on your device, so it’s easy to delete them.
Cookies have some legitimate uses and some are necessary for a website or app to function, but they’re also frequently used for ad tracking and targeting. Thankfully, you can always change your app or browser settings to only allow necessary cookies.
Plus, because a website must gain explicit consent to use cookies, you can simply decline a website permission to use unnecessary ones.
Ok, I get it with the wide sweep of information being given, ALEX aka Sven, thanks!
But, Please seperate the “How to Stay Private” section per mode of internet contact that’s used and, though the protection methods may be common overall.
-Specifically devote a device section in calling out either for a fixed location computer device (home-business), or a mobile device (phone-tablet-watch) or even a smartdevice is being used to connect to the internet. Giving Ways of staying PRIVATE from the sites you visit with highly specific information about that device’s (maybe Opperating Systems) options clearly.
Make one table of Private options as numbered (ex 1-35), then colleate the numbered points of agreement to PRIVACY for whatever device/browser/platform the reader identifies with. (ex 1,2,23,31,35 for garmin watch).
= )
Hi Sven
I’ve got an article on uselessness about fingerprint protection.
As here – https://fingerprint.com/blog/browser-anti-fingerprinting-techniques/
Is there is any value of this opinion described by the author here, or just a gimmick to sell browsers haven’t fingerprint protection ?
What do you think sir ?
Hi
I am not sure that I fully understand the article, so not a right person to explicitly evaluate the content of the article.
This article is written from the angle of a company that makes money via providing fingerprinting tech. This angle is new to me. (On the topic of browser fingerprinting, I previously required information only from the side that focuses on protecting privacy.)
Therefore, for me, reading this article is one step to getting out of my own information bubble on fingerprinting. Thank you for the article. (Of course, I don’t want to be fingerprinted.)
Can we trust the method of closing sensors in Android?
I tried some applications to measure the sensors on Android, and when the sensors were closed, there was no data at all, unlike the iPhone, there is no way to turn them off
It is possible to turn off sensors on android in developer mode. Go to settings>about phone>software information and tap on “Build number” 7 times. now go back to main settings menu and open Developer options all the way at the bottom. in developer options, scroll down and select “quick settings developer tiles.” Now toggle on the “sensors off” option. you will now be able to turn that on/off from the drop-down menu like you would the flashlight. Just careful not to go around adjusting other settings in developer options if you’re not sure what they do. You can also turn developer options back off and go back to “normal.”
Are sensors restricted in iOS 14 and Android 12?
5. Don’t expect much privacy on a smart phones
This is true for the “average user”. But if you use a computer or a cell phone for a long time. It’s not that hard, just download Kiwi Browser(based on Chromium) and you can install all the Google Store extensions.
But there’s a slight catch. All of your security tools are available in your browser. Once you put it on software, there’s no way to really keep everything safe for you, and this issue happens whenever you’re connected to the Internet, whether it’s a computer or a phone. (For example, if Discord forces users to update without their consent, how can we be sure it isn’t uploading data behind its back or sharing telemetry? Or maybe Spotify is forcing the update, which again doesn’t have the user’s permission, and we don’t know what the software is collecting
But tools that do not use the Internet, which is very convenient, all default disable applications from using the Internet. That’s what I do with all kinds of software.
But in the browser you can filter everything. Exactly what the author discusses in this article)
Back to the Kiwi browser on mobile. Maybe it’s weird for me to say this. But I’ve started making mobile computers again. Almost in the modified version of the browser I made, you can see all the techniques I used. The first is to disable all privacy-affecting Settings by default. No password manager, no spell check, no Google login. All banned.
And when that’s done, you’ve only done a small step, only about 10 percent. You’ll need additional Extension to complete the setup. The browser must use a VPN (because the browser can also act as a VPN location). When choosing a VPN, forbid using Hola, Free OpenVpn, or any Japanese university, which are all VPNS that keep Logs. And I’m not sure it’s safe. Use a free VPN provided by the company) I use Cyberghost VPN
Or use google play and a lot of unknown VPNS, these are warning signs. It does not rely solely on evaluations and user comments
I am fed up with these “fake” free VPNS that rely on bullying ordinary people and average people to gain profits. Damn it, I hate that kind of thing. If you don’t have enough technology to make a vpn, don’t send out viruses and telemetry software to everyone. In my country, there are a lot of people who want to link to other countries because they play video games, or download pirated software, download pirated movies. But someone said his computer had been hacked, or his account had been stolen. This is where free VPNS get rubbish. I only trust companies. Don’t believe in fake VPNS with free VPN flag pole)
Cyberghost Extension or ProtonVpn are conscientious undertakings. I speak from the heart.
The Extension I use on my phone is as follows: This is a good tool to disable Canvas, Webgl, Audio, Font, and Webrtc on your phone
https://chrome.google.com/webstore/detail/fingerprint-spoofing/ljdekjlhpjggcjblfgpijbkmpihjfkni
Random Useragent:
https://chrome.google.com/webstore/detail/random-user%20-agent-switche/einpaelgookohagofgnnkcfjbkkgepnp
Everything else is a basic Extension:
chrome.google.com/webstore/detail/stay-secure-with-cybergho/ffbkglfijbcbgblgflchnbphjdllaogb
chrome.google.com/webstore/detail/vytal-spoof-timezone-geol/ncbknoohfjmcfneopnfkapmkblaenokb
chrome.google.com/webstore/detail/noscript/ doojmbjmlfjjnbmnoijecmcbfeoakpjm
chrome.google.com/webstore/detail/ublock-origin/cjpalhdlnbpafiamejdnhcphjbkeiagm
chrome.google.com/webstore/detail/tampermonkey/dhdgffkkebhmkfjojejmpbldmpobfkfo
chrome.google.com/webstore/detail/stylus/clngdbkpkpeebahjckkjfobafhncgmne
U-block Database filling:
https://greasyfork.org/en/scripts/19993-en-adlist-js-fixes
https://raw.githubusercontent.com/easylist/ruadlist /master/ruadlist-fixes .user.css
Automatic page turning script:
https://greasyfork.org/zh-TW/scripts/436203-super-preloaderplus-one-new
(necessary adjustment, open in the top right corner of the small window, open the Settings. Select global automatic suture. Turn off built-in rules. It can be applied to all forums and web pages.
https://greasyfork.org/zh-CN/scripts/438684-pagetual
All the other detailed Settings, you can refer to my computer version of the browser, to do the configuration
I ran a series of tests on the browser’s security. The author’s article is good, but it omits many questions. These are all secure extensions, but sometimes you have to choose between them, because when it comes to secure extensions, some pages won’t work. Or you may have to consider the convenience of Extension to optimize it… Does it really protect privacy?
So I’d like to share with you my revised privacy browser and collected security test sites:
Centbrowser—Priavcy—V3.2(Beta)
https://github.com/LilyJone/OpenTools/releases/tag/Centbrowser%E2%80%94Priavcy%E2%80%94V3.2%EF%BC%88Beta%EF%BC%89
Browser security test site:
https://2ip.ru/privacy/
https://portscaner.ru/
https://hidemy.name/ru/port-scanner/
https://proxy-seller.com/tools/port-scanner/
https://myopenports.com/scanner
https://free.proxy-sale.com/en/skaner-portov/
https://proxy6.net/en/privacy
https://browserleaks.com/ip
http://www.find-ip.net/
https://thesafety.us/check-ip
https://whoer.net/zh#
https://browserleaks.com/webgl
https://vpntester.org/en/torrent-leak-test-en/
https://www.speedguide.net/popup_scan.php
https://html5test.com/
https://www.waveform.com/tools/bufferbloat
https://tenta.com/test/
https://www.lagado.com/tools/proxy-test
https://ipx.ac/run
https://webkay.robinlinus.com/
https://clienttest.ssllabs.com:8443/ssltest/viewMyClient.html
https://coveryourtracks.eff.org/
https://www.howsmyssl.com/
https://amiunique.org/fp
https://browseraudit.com/
https://ipleak.com/full-report/
https://webbrowsertools.com/
At the same time, I hope to absorb suggestions for improving the browser. (The browser is optimized and adjusted based on what I learned in Internet security. There are detailed tutorials and Youtube videos on my past Github)
Hi RP Commuofnity, here is a list of testing sites relevant to fingerprinting:
amiunique.org
https://nothingprivate.ml
https://fingerprintjs.com
https://noscriptfingerprint.com
https://abrahamjuliot.github.io/creepjs/
https://www.deviceinfo.me/
browseraudit.com
Please add if you know other good ones.
Hi RP, LibreWolf seems to fail the fingerprint tests same as does Custom FF and Brave. (I haven’t retested FF and Brave recently)
The only solution I have found is to use virtualisation.
For everyday use I will use browser compartmentalisation, but I am changing my setup to a four browser setup:
-Brave: for personal business;
-UnGoogled Chrone: for YouTube and Google search;
Then two browsers for usual browsing, Custom FF and LibreWolf, where one has JS disabled. (I haven’t decided which)
I so love UBlock Origin! But it will be a pain-in-the-butt to customise each browser again to meet my new setup..
I can spin (clone) a light weight version of Ubuntu in a minute,
And I have a VPN
Goodluck all
Hi Sven. Regarding the sensors fingerprinting you’ve stated above, it can be mitigated by only installing open source and trusted apps can’t it? So big tech apps that will likely use the sensors data, like Facebook or Google, should be avoided.
It’s said too that the sensors fingerprinting can also be done through websites. However, to overcome this, Google and Apple have implemented motion sensors access control in their browser settings haven’t they? So that you can block sites from accessing these sensors. I’ve checked my browser settings, and it’s blocked by default (I’m using a Chromium-based browser).
Hi Klaus, yes, using trustworthy open source apps is a great idea to mitigate privacy risks. Yes, Apple and Google have said there are restrictions on sensor data, but who knows.
Klaus is right. There’s actually something you can do about it. It’s by blocking sites from accessing the sensors. As for Apps, there’s this OS (a fork of Android) that allows you to disable sensor access for Apps. For what it’s worth, I’d say this article should be updated.
No
Can you share how you beat them?
What about this?: https://fingerprintjs.com/blog/disabling-javascript-wont-stop-fingerprinting/
I was just going to provide the same website as it is where I test my fingerprint vulnerability.
The only Chromium/Firefox extension I’ve found that actually can spoof this site is called “Fingerprint Spoofing” by leelei. The extension is quite draconian though and can break sites.
Hi! The recommendation ocurred in the “Dynamic filtering” section of the Wiki.
https://github.com/gorhill/uBlock/wiki/Dynamic-filtering
Recently, chromium-based browsers added chrome:flags which is the same as about:config for gecko-based browsers
Do you will upload anytime soon a tutorial like Firefox has but with Brave and their brave:flags? Thank you for reading!
Probably not because Brave gives you lots of control in a user-friendly control panel with the Shields options. It’s pretty self-explanatory.
Thank you! I noticed that if you use v96 ghacks/arkenfox user.js you are not gonna need to enable FPI anymore because they moved to dinamic-FPI (reference: https://github.com/arkenfox/user.js/issues/1281) and according to Librewolf docs: dFPI, also known as Total Cookie Protection, is a newer implementation and it causes less breakage, plus it is included by default when using Tracking Protection in Strict mode. Never change it to Custom mode because it will disable it! Besides that, i think its not recommended to use Librewolf or other third-party Firefox binaries (except Tor if you really need it for your threat modeling) when you hardened it with your own user-overrides.js settings.
Hi RP Community,
I would like to hear peoples thoughts on Privacy Badger.
Comments recently have suggested that it hasn’t been actively maintained for over two years.
I am wondering where this information comes from?
EFF still has it listed as a tool they supply.
I just read an interesting article (to me at least) on how browser extensions can lead to fingerprinting.
I feel it is relevant to many of the question on extensions that have been asked recently.
https://www.eff.org/deeplinks/2020/10/privacy-badger-changing-protect-you-better
For me, until recently, I was adding every (nearly but not really) Mozilla recommended privacy extension;
Than I took a minimalist approach and cut back to UBlock Origin and another tool (not a privacy one)
Two extensions only.
As I have been learning, my belief is a good approach is to pick a good tool (for me Ublock Origin);
and learn to utilise it to it’s potential before adding another tool.
I am thinking of adding Privacy Badger;
And I would welcome the communities thoughts?
Regards,
BoBeX
Hi BoBeX!
I did the same thing a few weeks ago… all gone except for uBlock! (An amazing tool/extension, IMO.)
Have added Privacy Badger and Privacy Possum since. (I consider myself at a low threat level. I just want enough “tinkering/adjustment” to optimize my browsing.) Neither PB nor PP slow down anything and do their respective thing automatically including automated updates. I believe they compliment each other and do not duplicate functions of uBlock. (Don’t know for sure though.)
(I also have one browser I have hardened just for accounts with passwords.
An other browser just for news…. in addition to various other browsers I have checked out for the right features.)
I’m right now looking at and reading the version date at the bottom left (very faint) – says 2021.11.23.1! So the ‘2 year no maintenance’ statement I believe is quashed!
Best of luck to yu’ on going minimalist!!! Cheers, George
(BTW… I’m no geek, but I think the whole fingerprinting thing with the “unique” attribute is seriously overdone/overrated and academic. I’ve tested for over a year now and I ALWAYS COME UP AS UNIQUE!!! So the F what??? That said, I could be completely wrong on my take! LOL
I use only Badger in Firefox for some time, even though I like Origin and I always used it throughout the years. Badger seems enough if you set all in FF as recommended and set your Network to go through DNS ad blocker (I recommend AdGuard DNS). In case you set DNS, you may also use a VPN add-on as well.
Very good tip Bronco… I’ll give it a go! Cheers, George
@Bronco, With Badger, do you use Badger Sett or local learning?
I have NordVPN with CyberSec enabled, do you still think I need more DNS protection?
With Origin, I really like the idea of customising it to suit the particular purpose I have for a browser in a browser segmentation framework.
I do believe Badger will compliment this in fit for purpose cases
@George I do believe PB compliments other ADBlocker tools due to it’s local heuristic learning – rather than reliance on predetermined lists.
Before I read the article I posted above, I thought PB’s move away form heuristic diminished it’s capability.
The “Badger Sett” I assume is ~95% as good as the local learning (now turned off by default)
And local learning can be turned back on (understanding the risks outlined in the article)
I am looking into browser compartmentalization with he mind to make UBlock Origin my primary tool. I think in some cases PB will be complimentary to it.
On PP, it was one of the many tools I had previously installed and it still appears in FF recommended. I always did find it hard to find much documentation and reviews of PP.
I recently read their Github and I still like their concept;
But I am unsure if they are big enough to be providing security really well (like EEF) and to draw the attention of Google security team if there is a vulnerability.
This said, I can’t criticise PP, I am just not sure.
All ways great to hear from a fellow Commonwealth countrymen
BoBeX
Hi BoBeX,
I think Privacy Possum was/is the one that hasn’t been updated in two years. (2019-2021)
I’ve no experience in using Privacy Badger. Privacy Badger works like Safari Intelligent Tracking Protection (ITP) which is based on local learning or heuristics. Now, Privacy Badger mainly uses Badger Sett as basis for predetermined or known trackers. Likewise, Safari now also includes known trackers database (from DuckDuckGo) but local learning is still on by default unlike Privacy Badger.
EasyList, AdGuard, Ghostery, Disconnect and DuckDuckGo—these ad/tracker filters are similar but not 100% identical. One may be stronger/stricter/more bloated than the other. Badger Sett claims to be unique from those because its tracker list is automated rather than handcrafted by community. Badger Sett learns from 1000s of popular websites listed by Tranco.
Should you use Privacy Badger with uBlock Origin or other ad blockers? I think it’s not necessary due to redundancy but there’s probably no harm either in terms of ad blocking quality or computer performance.
Different Question: how do we configure the browser so that it sends wrong “user agent info” ( I am referring things such as the OS used, display information such as width(height etc.). Tor browser and Librewolf do this but how would we accomplish that with Firefox/Ungoogled Chromium ?
@JanesaidNO(UC) th answer is that hey ready do
Firefox>about:config>privacy.resistFingerprinting, it changes the display information.
The AmIUnique website contains a job posting whose deadline for application expired more than 3 months ago. How seriously should we take these people if they can’t keep a silly mistake like this from happening?