
A shocking new report compiled by the FTC (US Federal Trade Commission) details how internet service providers are collecting vast amounts of private information that includes browsing history, device information, and location data. This data is often shared within a broad network of advertisers and partners — but we’ll give you concrete steps you can take to restore your digital privacy against these abuses.
Would you be surprised if I told you that your internet service provider (ISP) was spying on and recording everything you do online?
Perhaps not — but you will probably be surprised by the quantity and type of information they gather, as well as what they do with it. In short article, we’re going to hit the high points of a recent FTC (Federal Trade Commission) study that shows us what the big US ISPs really know about us. It also gives us some idea of what they do with the data, and the lengths the big ISPs will go to to keep you from protecting your privacy.
Which ISPs were involved?
The full-length FTC report is based on information gathered from the six largest ISPs in the United States. Together, they comprise almost 82% of the fixed, and almost 99% of the mobile internet market in the United States at the end of Q1, 2021. Their names are:
- AT&T Mobility LLC
- Cellco Partnership (doing business as Verizon Wireless)
- Charter Communications Operating LLC
- Comcast Cable Communications (doing business as Xfinity)
- T-Mobile US Inc.
- Google Fiber Inc.
The FTC also demanded data from three advertising companies that are affiliated with some of these big ISPs. Their names are:
- AT&T’s Xandr
- Verizon’s Verizon Online LLC
- Verizon’s Verizon Media
The goal of the FTC was to do a comprehensive examination of the privacy practices of the 9 organizations above. We’ll dive into the results of this examination in a minute. But before we do, you may need a change of perspective. I know I did.
Note: This is going on all over the world (not just in the United States)
And for our international readers, we should also point out that these same alarming trends have been going on for years in other countries. Over the past ten years, we have seen the UK, Australia, and Canada all pass laws requiring internet providers to record browsing history and make this data available to government agencies.
Needless to say, you should assume your ISP is collecting everything you do online, regardless of where you live — unless you take appropriate counter-measures (discussed below).
Understanding the big US ISPs
The important thing to understand is that these 6 ISPs are no longer simply internet service providers. They are now integrated tech giants in their own rights. The FTC generated the following image to show all the different (and interrelated) businesses that major ISPs may control:
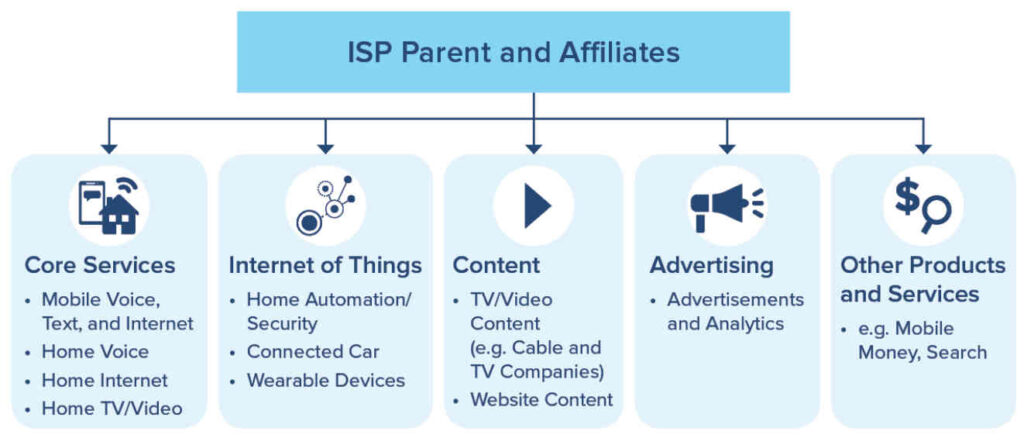
The big ISPs provide a huge range of services. Most or all of those services can gather, and potentially share, information about you and what you do, to the ISP parent company and any or all of the affiliates. This means that just one entity could collect data that is shared with a large network of other organizations.
What did the FTC discover?
The FTC uncovered a lot of disturbing information about the policies and practices of the big ISPs. The report describes the problems in some detail. But interestingly, it doesn’t name names. That is, they didn’t explicitly say Verizon did this, or T-Mobile did that. Also, much of the report is information that is of little interest to people like you and me.
The best I can do for you is to dig through the full 74-page report and pull out the information that I think regular internet users want to know. That means we’ll skip things like the history of the legal framework applicable to ISP privacy. Instead, we’ll talk about things like:
- The vast amounts of your personal information some ISPs gather
- The potentially harmful things some ISPs do with the information they gather
- The tricks some ISPs use to deny you meaningful control over your information
We’ll finish up by talking about some things you can do to fight back.
Here we go.
The vast amounts of personal information that ISPs can gather
Your ISP has access to a lot of information about you. To begin with, they probably know who you are and where you live since you probably have a signed contract with them. Since they typically configure your router to connect to a Domain Name Service (DNS) they control, they can see which websites you visit. If a website you visit doesn’t use encryption (HTTPS) your ISP can see whatever you do there. That’s a lot of information right there, but it gets worse.
ISPs are recording:
- Every website you visit
- Information from your web browser
- Data from other connected devices on your network
- Location data from mobile devices
Combined, this information could be useful for creating a very detailed profile of you that is extremely valuable for advertisers. But it gets even worse.
Remember that the big 6 US ISPs are now tech giants. They provide all sorts of services that have little or nothing to do with getting you connected to the internet. That means all sorts of additional information is available within their overall empire.
They could also have access to information like:
- Your television viewing history
- Email and search results
- Data from your home security
- Connected vehicles you drive
- Other internet-connected devices, such as fitness trackers, appliances, and other Internet of Things (IoT) devices
Feeling sick yet? No? Then you should know that the FTC says there is a trend in the ISP industry to:
“…combine the subscriber data with additional information from third-party data brokers, resulting in extremely granular insights and inferences into not just ISP subscribers but also their families and households.” -FTC
In other words, the big ISPs have the ability to create incredibly detailed profiles of our personal online activities.
And according to the FTC, at least some of the big 6 ISPs are already doing this right now. The question is, what do they do with all this information?
The potentially harmful things some ISPs do with the information they gather
One thing ISPs can do with all this information is help advertisers target you with ads, based on your unique data profile. They don’t need to sell your personal information to do this either. They can apply a process like the following to make money from advertisers without directly revealing your personal information. An ISP can do something like this:
- Combine the personal information they gather themselves with info they buy from third-party data brokers.
- Based on this information, divide their users into market segments.
- Serve targeted ads (provided by the advertisers) to each market segment on behalf of the advertisers.
- Earn advertising fees.
Note that none of your personal information leaves the ISP, yet you are still exposed to ads targeted based on the personal information they collect.
According to the FTC, a trend in the ISP industry is selling mobile device position data to third parties. This is how you end up receiving ads for some restaurant or department stores that are in your physical vicinity. That’s annoying, but this kind of real-time sharing of location data can lead to far worse outcomes. It can reveal where you live or work, as well as what school or house of worship you attend.
Numerous sources also report that the FBI uses mobile position data to arrest and detain people (including members of Congress) who happened to be near a suspected crime scene. And it gets worse.
In 2018 and 2019, news outlets reported that bounty hunters, bail bondsmen, and others were able to acquire mobile ISP users’ real-time position data through third-party location services. Although the position information wasn’t sold directly to those snoops by the ISPs, the FCC eventually proposed $200 million in fines for Wireless Location Data Violations, part of Section 222 of the Communications Act.
Another risk is that some of the big 6 US ISPs reserve the right to share your personal information with their partners and affiliates. And who exactly is within the web of “partners and affiliates”? Who knows.
Can things get worse? Yes, they can.
According to the FTC, several of these big ISPs use race and ethnicity data (or their proxies) for their advertising. Proxies for racial and ethnic data can be things like location data or other data that closely mirrors the data of a protected class.
For example, imagine that most of the population of a particular neighborhood belonged to a certain race and/or class of people. An ISP could segment its data so an advertiser could choose to target or avoid that neighborhood, in effect discriminating by proxy.
Given all the problems that could cause, it is good to know that many ISPs give you the ability to control how your data is used. But even here, the FTC found serious problems. ISPs appear to go out of their way to make it difficult for you to exercise meaningful control over your information.
According to the FTC staff, the ISPs studied make it difficult for consumers to opt out of data collection. They also make it hard to find out what information the ISPs have already collected on them. Let’s look at some of the ways ISPs do this.
The tricks some ISPs use to deny you meaningful control over your information
Some ISPs use tricks and techniques that make it hard for you to take control of your personal information. The options may be unclear, or even designed to push you toward sharing more information instead of less. User interfaces designed to influence users’ decisions like this are often referred to as dark patterns.
Examples of dark patterns that might be used by ISPs include:
- Interfaces with the desired option highlighted and the others greyed-out to make the user think they are not available.
- Interfaces that don’t allow the user to permanently opt out of data collection. There might be only two buttons, one that says you Accept data collection, and the other that says Remind me later. Neither option lets you permanently reject data collection.
- Interfaces that hide privacy options. Users are seldom given the equivalent of a, “Stop all surveillance now!” button. Instead, you must hunt down many separate options located in obscure or misleadingly named menus and sub-menus to get complete protection.
- Interfaces with unclear toggle settings. These appear to be intentionally designed to confuse you so you don’t know whether to turn the toggle on or off. The FTC provides the example of a toggle labelled, “Do Not Sell my personal information.” Should you set the toggle to On or Off to prevent the ISP from selling your information? Without additional information, there is no way to know for sure.
How you can fight back against mass data collection
It might seem that the practices we have been discussing should be illegal or at least “against the rules.” According to Covington’s Inside Privacy blog, a bill attempting to deal with dark patterns was introduced in the 116th Congress (2019-2020), but it died without being voted upon. Even earlier, in 2017 the FTC attempted to make rules to prevent some of the worst abuses we have been discussing. But Congress actively blocked the rules from going into effect.
Since the government isn’t interested in doing anything about these abuses, it falls to you and me to protect ourselves.
Some of this stuff we really can’t do anything about. We can’t make our ISPs stop using dark patterns to confuse us. And we can’t stop ISPs from gathering vast amounts of our personal information and sharing it with their partners and affiliates.
But we don’t have to make things easy for them either. Here are two specific things you can do to minimize the amount of personal information your ISP can gather:
1. Use a secure email service
Most importantly, don’t use the free email service that your ISP provides.
If you use a free email client offered by your ISP, they can probably read your email and extract tons of personal information from it. Instead, use a secure and private email service that gives you full control over your inbox. We have reviewed many private email services that can encrypt your messages, thereby preventing third parties from reading them.
And even if you don’t (or can’t) use full inbox encryption, simply switching email providers to an alternative that is more private will go a long way. (We also have a guide on alternatives to Gmail here.)
2. Use a VPN whenever you are online
A VPN (Virtual Private Network) will encrypt all internet traffic traveling to and from your computer or internet-connected device. This encryption makes it impossible for your ISP to see what you are doing and where you go online. But a VPN can do even more.
The best VPNs automatically use a private DNS system. A Domain Name Service (DNS) translates the names of websites from human languages into something your computer can understand. Typically, your ISP will configure your internet connection to use a DNS controlled by the ISP. As a result, the ISP can easily see and record every website you visit.
The best VPNs provide their own private DNS. When you use this, your ISP won’t see the websites you visit or search for.
Finally, a VPN hides your IP address. When you use the internet, your IP address gets shared with every website you visit. Knowing your IP address makes it easier to track your activities throughout the internet. Because the VPN hides your real IP address, it becomes much harder to track your online activities.
Choosing the best VPN can be challenging simply because there are hundreds of VPNs to consider. To make life easier for you, we’ve done all the hard work. We’ve created a list of the best VPN services available. Any one of them will help you shield your personal information from the clutches of your ISP.
And to get up to speed on other solutions, check out our main privacy tools page for more info.

 Taking a Closer Look at Kape Technologies, Crossrider, and Malware
Taking a Closer Look at Kape Technologies, Crossrider, and Malware
After reading article after article about the unethical “practices” of the dwindling choices of internet providers, I’m not too shocked to find that NOBODY appears to be claiming evidence that their IP provider is acting maliciously by ever known (and a few I didn’t know about) attack under the sun (including ntp attacks, bios-level attacks, ddos, dropping connections so that your computer automatically reconnects to the fabricated connection provided by the predator providers, etc.).
I’m old and remember when the internet was free by using netzero or one of the other huge choice in providers back about 23 years ago? That was the bait.)
Me:
13 simultaneous blacklists
Banned from EVERY american social site (only the russians didn’t suspend my zen and yandex accounts).
Shadowed and erased comments are the norm for me
There’s much, much more, such as my having the attorney general of our state finally come to my rescue. After which it appeared I won something (but actually it wasn’t entirely a win). I would love to show my evidence which has been documented and updated since I started in 2016 but it appears my website no longer come up in search results and eventually it was hacked (so I initially thought it was the hoster of my site….that was about a dozen hosts ago).
Finally, I operated my own server here and then I saw it. Attacks and hacks are traced using nmap, iptraf-ng, wireshark, etherape, and ever known forensics program you can possibly think of to try and ward off the FBI and Department of Defense and even the local Springfield Ohio Commissioner and another privileged person that I just happen to admire so I’ll leave his name out….his aid and I spoke together and agreed.
Some things aren’t worth fighting for if it hurts good people. Later that same week a military guy arrived here not for my I.T. Services (yes, I’m a tech), but to state he hopes he’s not ordered to kill american citizens.
So what’s the answer?
Plain and simple (if you can do it) , burn the computers, televisions, radios, and phones. I wish that I could regurgitate the words, “oh just use a proxy or tor or vpn or blah blah blah” (but I can’t).
The only solution is to trust NOBODY & believe NOTHING!
The only way to deal with the global spy network is to ATTACK it. Just like the greatest terrorist nation has been doing all over the world for the past 70+ years to anyone who stands in their way to complete global domination.
Hackers unite and destroy the evil empire!
So, if ExpressVPN was used with DuckDuckGo would that make searching safe?
If I were to show I was located in a different country by way of ExpressVPN would my searches be safe on ddg?
Or, is it to simple to think, whatever I type in on any “private search” companies search bar that is saved, and reported, and no VPN can protect that?
I have been reading your companies report on the best “private search” companies. What I found interesting, one area you pointed out all companies in the USA must turn over all our searches. Then in another area of that report you point out Brave is one of the most private search apps. How can that be if they are located in the USA.?
I realize I am dancing around, but I just discovered your company and read about ddg and then this report when i added Brave. I saved your page to Brave. I am also going to look at your other private search companies. I know these questions don’t match the topic, but trying to find privacy is your main topic.
Duck duck go is now censoring their search information and have been doing that for about 2 years now but they just admitted it on twitter.
Hi Festus,
Your questions really go to an analysis of your threat model.
I mean, analyse your threats first, then seek the tech / security options you need.
A common idea is that the more you increase your security and privacy the more you increase your inconvenience .
If you feel unsafe, use VMs and a VPN. Your chosen search search engine matters much less in that case.
(VMs are not a defence against seizure of your devise)
Good luck,
BoBeX