
Looking for a better alternative to email for secure communication? This guide highlights the best secure messaging apps and services, frequently asked questions, as well as some messaging apps and practices you should avoid.
Have you ever whispered something in someone’s ear that you didn’t want others to hear?
We all have. These days, many of us spend more time talking to people online than we do face to face. Do you ever say (or type or show) anything that you don’t want others to hear (or read or see)? If so, you had better be using some kind of encrypted messaging app to do it.
In this new and updated guide, we’ll talk about why you need to use a secure messaging service. Then we’ll take a quick look at the latest versions of several secure messaging apps and the services they run on, along with some important characteristics to look for. As you’ll see, each has its own pros and cons, and each takes a different approach to the problem of providing secure messaging capabilities.
Why you need to use secure messaging
When you chat with someone online, you might assume that only yourself and the other person are privy to the conversation. But as we’ve learned over the years, there are lots of groups that are expending considerable effort to spy on your communications. Whether it is corporate surveillance or government agencies snooping up data, your private information is under attack.
- Corporations want to read your messages so they can better target ads to you or sell your personal information to the highest bidder.
- Hackers want to use the information to steal your identity, break into your bank account, sell your company’s new business plans to the competition, or blackmail you with those pictures from that wild night in Vegas.
- Governments want to know everything you think and say and do, and maybe even catch a terrorist or two.
Unless you are using a secure messaging service, any or all of these groups will have an easy time intercepting your messages should they choose to do so.
The situation has gotten even worse with governments forcing people to work from home to protect against that virus. Businesses generally have better internal security than someone sitting on their sofa at home, exposing even your company communications to greater threats than before.
That’s why there has been a boom in new messaging services that claim to be private, secure, anonymous, or any combination of those. But some only protect your messages in transit, while leaving them accessible to the employees of the service. Others are owned by companies with bad reputations for protecting your privacy. Some may even have been hacked by the NSA or other national intelligence agencies, but all hope is not lost.
Here are some secure messaging apps that make the grade…
Best encrypted messaging apps
We’ve tested quite a few messaging services over the years. The ones listed here are the ones we consider to be the best options for secure messaging.
Signal – The most secure messaging app
Signal is one of the two messaging apps that really benefited from WhatsApp’s privacy problems in January 2021. A tweeted recommendation from Elon Musk during the crisis certainly didn’t hurt. And since then, Signal continues to get lots of attention.
Signal is generally considered to be the most secure messaging service available. Originally published by Open Whisper Systems, their encryption protocol (the Signal Protocol) is so good that many other services (including giants like WhatsApp) base their own encryption protocol on it. Signal is end-to-end encrypted, open source, and completely free of charge. It allows you to create disappearing messages (a.k.a. self-destructing messages), has successfully completed third-party audits, and also publishes Transparency Reports.
And if that wasn’t enough, it has recommendations from top privacy advocates including Bruce Schneier and Edward Snowden.
However, Signal does come with a few drawbacks. Perhaps most problematic, it requires a telephone number for registration. This, of course, links what you do on Signal to your identity through your phone number, which could be a dealbreaker for some people. Fortunately, there are some workarounds for the Signal phone number registration issue. And of course, you can also use another one of the secure messaging apps listed below.
+ Pros
- End-to-end (E2E) encryption
- Encryption algorithms: Signal protocol, with Perfect Forward Secrecy (PFS) for text messages, voice messages, and video calls
- Open source
- Disappearing messages (aka self-destructing messages)
- Published transparency reports and security audits
- Logs minimum amount of data
- Does not log IP Addresses
- Can replace your phone’s SMS messaging app
- Focus is totally on individual users
- All Signal products are free of charge
– Cons
- Requires a telephone number to sign up
- Does not support 2FA (Two-Factor Authentication)
https://signal.org
Read our Signal Messenger review for more info.
Wire – Secure messaging and collaboration app
Wire is a well-regarded corporate collaboration suite with secure messaging, group chat capabilities, file-sharing, and the ability to collaborate securely with external clients. For this roundup, we reviewed Wire (free version), a secure messaging app for individuals. According to third-party testing, the Proteus protocol that Wire relies on is secure. Like Signal, Wire is open source and gives you self-destructing messages. Also like Signal, Wire requires some personal information to create an account, either an email address or a phone number. However, you can always use a burner temporary disposable email for this.
Judging on its technology, Wire messenger is a great secure messaging app for individuals. On the downside, there are only approximately 500,000 Wire Free users. Another drawback is that the company has announced they will be focusing more on corporate users, rather than individuals. Take this into account if you are looking for a long-term solution to your encrypted chat app needs.
+ Pros
- End-to-end (E2E) encryption
- Encryption algorithms: Proteus protocol, WebRTC (DTLS, KASE, SRTP) with PFS
- Open source
- Self-destructing messages
- Published transparency reports and security audits
- GDPR compliant
- Wire Personal is free
– Cons
- Registration requires email address or phone number
- Some logging of personal data
- Does not support 2FA
- Small number of Wire Personal users (roughly 500,000)
- Company focus is now on the corporate market, not individual users
https://wire.com
Here’s our full Wire Messenger review.
Threema – Anonymous messaging app with no data collection
Threema is one of the less well-known secure and private messaging apps. With around 5 million users and over 8 years on the market, it is a mature, powerful product that somehow never gained a massive following like Telegram, or widespread fame like Signal. But none of this means that Threema isn’t a good option for certain use cases. Here’s why…
First, you can use Threema totally anonymously. Unless you choose to link the app to an email address or phone number, the only way to identify a user is through a randomly generated ID that has no connection to any user-identifiable data. Likewise, each user’s private key is stored on their device, meaning only the user of the relevant device can read messages sent to it.
Note: You have the option to securely back up your Threema ID, contacts, groups, and other data in a Threema Safe which can reside on the company’s servers or on your choice of other location.
Threema offers a business/education version of the product, along with add-ons for broadcasting messages to Threema groups, and an API to use the Threema message network with your own software.
Even Threema’s relative obscurity can be an advantage in some circumstances. Anyone trying to spy on, hack, or otherwise tamper with a messaging service is much more likely to target the services with larger user bases or greater notoriety. There can be advantages to being overlooked.
While there is currently no free version of Threema, you can still purchase this app through the Threema store for direct download, or the Google Play and Apple stores.
+ Pros
- End-to-end (E2E) encryption
- NaCl open source encryption
- Anonymous messaging; no telephone number or email address needed
- Text and voice messages, voice and video calls, file sharing, polls, groups and distribution lists
- Mobile apps plus browser-based, secure desktop chat
- Transition to Open Source is complete
- No IP Addresses or metadata logging
- They own all their own servers for better security and privacy
- Regular security audits and transparency reports
- GDPR compliant
– Cons
- Small user base
- No 2FA
- No free version
https://threema.ch/en
See our Threema review here.
Telegram – Secure messaging app with 500+ million users
Telegram was the biggest beneficiary of the WhatsApp privacy issues at the start of 2021. How big a beneficiary? Telegram gained tens of millions of new users in just the first few weeks of 2021.
It doesn’t matter how secure and private a messaging app is if you can’t talk to anyone with it. When a messaging service has over a billion users like WhatsApp or Facebook Messenger, the odds are high that the people you want to chat with already have an account. When a service has less than a million users (Wire, for example) the odds that the people you want to talk to already have an account are pretty small.
Telegram occupies the middle ground. With over 500 million active monthly users, the odds that the people you need to talk to already have an account are pretty darn good. And the service is free, too. So let’s talk about the other characteristics of a secure messenger service.
While we love the widespread acceptance of Telegram, and the ever-expanding feature set, we do have some concerns about the service. Communications in Telegram are not end-to-end encrypted by default. Only voice calls and Secret Chats are E2E encrypted. Unless you use one of these two modes, your communications within Telegram are not really secure. Even if you do use the E2E encrypted parts of the service, MTProto, the encryption protocol used by Telegram, is questionable at best, insecure at worst – all depending on who you ask. Besides, Telegram logs more user information than the other services listed here.
Whether Telegram is an option for you depends heavily on your threat model and use cases. You may well find that access to the rich feature set and huge user base of Telegram outweighs the questions about exactly how secure and private Telegram really is. If you do decide to give Telegram a try, make sure to use a good VPN service as well. Hiding your IP address and physical location using a VPN goes far toward overcoming the privacy concerns of all that user data logging.
+ Pros
- End-to-end (E2E) encryption
- Encryption algorithms: MTProto, a custom protocol
- Open source apps and Telegram Database Library
- Self-destructing messages
- Users can be logged in on multiple devices simultaneously
- Supports Two-Step Verification
- GDPR compliant
– Cons
- Registration requires a phone number
- E2E encryption only for voice calls and Secret Chats
- Servers are not open source
- Lacks published formal third-party audits
- Logs IP Address and other metadata
https://telegram.org
See our Telegram review here.
Messaging apps and practices to avoid
So now that we’ve covered the best secure messaging apps above, let’s touch on another topic: messaging apps to avoid.
1. WhatsApp (owned by Facebook)
Sure, WhatsApp may be encrypting your messages – but that doesn’t make it a safe and secure solution. It is owned by Facebook and operates under US law. Here are a few reasons to avoid WhatsApp:
- WhatsApp collects metadata about every user, which can be exploited by Facebook and/or handed over to government agencies. This data includes your name, IP address, mobile number, location history, cell network, contacts, and device type.
- Facebook and WhatsApp will be forced to share users’ encrypted messages with British police under a new treaty.
- Reports suggest governments can easily access encrypted WhatsApp data through “WhatsApp Web”.
- In early 2021, news broke about major privacy policy changes at WhatsApp, which puts more data in the hands of Facebook.
Check out our guide on the best alternatives to WhatsApp.
2. Keybase (now owned by Zoom)
Keybase, which has grown in popularity over the years, sold out to Zoom back in 2020. We covered the story more in our Keybase review.
We know that Zoom is not a business that respects the privacy or security of its users. In fact, there have been numerous scandals with Zoom over the past few years. It’s also worth noting that Zoom has questionable ties to China. In fact, it was even busted routing user data through China.
With Zoom now owning Keybase, we can no longer recommend it.
3. Regular (unencrypted) SMS text messages
While this does not fall under the category of encrypted messaging apps, it’s still worth repeating. If you expect any privacy or security, don’t use standard (unencrypted) text messages.
These text messages can easily be seen by your mobile carriers and the entities they share data with. Additionally, regular text messages are susceptible to man-in-the-middle attacks and also eavesdropping by Stingray devices.
It is important to realize that this applies to SMS messages sent by Signal too. If you configure Signal to manage your SMS messages, it can send and receive SMS. But there is no way to encrypt SMS messages, so even if Signal is managing them, SMS messages go out unencrypted.
Characteristics to look for when selecting an encrypted messaging app
What characteristics should you look for when selecting an encrypted messaging app or service? Even if you have some very specialized requirements, these are characteristics you should definitely look out for:
- End-to-end (E2E) encryption
- Third-party testing / reviews
- Open source code
- Self-destruction
- Limited user data collection
- The specific features you need
- Anonymous signup options
End-to-end (E2E) encryption
End-to-end (E2E) encryption is the #1 characteristic to look for in a secure messaging service. When a messaging service uses end-to-end encryption, only the people who are communicating can read the messages. No one else, not even the company providing the service, can read the messages. Whether you decide to go further down the E2E rabbit hole or not, the key thing to remember is this: If a service doesn’t offer end-to-end encryption, it is not secure.
However, there are two additional conditions that an end-to-end encrypted service must fulfill to ensure it is secure. First, it must use proven encryption algorithms. Second, the end-to-end encryption must be applied to your messages. So let’s look at those two conditions a bit more.
Trusted encryption algorithms
The security of E2E encryption assumes that no one can break the encryption. Or more realistically, it would take a vast amount of time to break the encryption being used. Vast as in millions or billions of years. This normally isn’t a problem. That’s because messaging services typically use trusted encryption algorithms. Algorithms like Signal‘s Signal protocol have been analyzed by cryptographers and shown to be secure against any reasonable attacks. If a service doesn’t use trusted encryption algorithms, it doesn’t mean that the service isn’t secure, but it is something to consider.
End-to-end encryption is turned on
E2E encryption is only useful if it is turned on. Most secure messaging services have E2E encryption turned on by default. Telegram, on the other hand, does not. You need to be sure that you are using Telegram’s Secret Chat system or communicating by voice messages if you want E2E encryption to be turned on in Telegram.
Third-party testing / reviews
One of the big concerns when dealing with any kind of secure messaging service is being able to validate their claims. There are a few different questions you need to answer for yourself:
- What is the service’s definition of “secure?” One service might take a zero-knowledge approach, encrypting/decrypting all messages in the client with the servers having no access to your passwords and encryption keys. Another might use TLS to secure data in transit, and encrypt it at rest on their servers, using their own encryption keys. Both can claim their service is secure, but they would both be using different definitions of the word “secure.”
- What is your threat model? You need to understand what threats you are trying to protect against. If all you want security against third parties spying on your messages while they are zooming back and forth across the Internet, that’s one type of security. If you want your messages to be secure against someone (the NSA perhaps) getting into the messaging service’s servers and decrypting your messages using their copy of your encryption keys, that is an entirely different level of security. Which one you need to search for depends on your threat model.
Once you have the answers to the first two questions, you need to decide if the service you are considering is fit for your particular situation. But how?
Is it practical for you to validate their claims yourself? Knowing that a secure messaging service you are interested in has open source code is great. But can you analyze their code to see if it really delivers on their claims? I certainly can’t. Nor can I do penetration testing or any of the other tests that would be necessary to see whether a service really delivers what it promises.
This is where third-party testing, audits, and reviews come in. Many companies now hire third-parties to come in and validate the service. The exact testing that they get done varies, as does the amount of test results they publish. But this kind of testing can at least give us some sense whether or not a product delivers on their marketing promises.
Open source code
Open source code can also make us more confident that a service will deliver on its promises. Why? Not because you or I are likely to review their source code looking for back doors or flaws in their algorithms. But because it is possible for someone to do exactly that. There are people out there who can, and do, dig into open source code looking for problems.
The more popular a messaging service is, the more likely that people are looking at the code, ready to call out problems. The simple fact that there are people willing and able to go through open source code like this means that errors are likely to get fixed sooner, and anyone trying to do something sneaky in the code will get called out publicly.
Self-destruct messages
The idea of providing security through self-destructing messages has been around for a long time. Today’s secure messaging apps have revived the idea of self-destructing messages, although they aren’t quite as dramatic about it as the old Mission Impossible team was.
Some services allow you to set specific messages to self-destruct a certain amount of time after they are read. Depending on your use case for a secure messaging service, this could be a crucial feature.
Limited user data collection
Just because all your messages are securely E2E encrypted, it doesn’t mean that the service has no information about you. Most services collect a certain amount of user data. This could be your email address, your phone number, the IP address you connect to the service from, what time you connect, who you connect to, and so on. While collecting this kind of information might not compromise the security of your messages, it does reduce your privacy.
Depending on your threat model, the amount of user data a secure messenger service collects may not be important. If it is, you can easily reduce the impact of this data collection by using a VPN while using the messenger service. A VPN will hide your IP address and your location, even from the apps on your devices. Some of our top-recommended VPNs include:
- NordVPN – Based in Panama, zero logs, fast speeds, apps for all devices (see our NordVPN review)
- Surfshark – Based in the British Virgin Islands, zero logs, very low prices (see our Surfshark review)
Note: A VPN is not a silver bullet that hides all your metadata. It is just one of many privacy tools you should be using for basic digital self-defense. However, a VPN will securely encrypt traffic between your device and a VPN server, while also concealing your true location and IP address. See these best VPN services for more options and info.
The specific features you need
The security and privacy of a messaging app or service means little if it doesn’t have the features you need. Happily, most of the top secure messaging services continue to add features, reducing the risk that the one you want will be missing something you need. For example, the ability to run on multiple platforms is virtually a necessity, whereas the ability to send video messages or voice memos may or may not be, depending on your use case.
One “feature” to look for in particular is compatibility. Specifically, compatibility with the secure messaging services used by the people you need to exchange messages with. Telegram’s user base is growing rapidly and has over 400 million users. The rest of the top services have a small fraction of that user base. Depending on circumstances, you may need to compromise on the security and privacy front to be able to communicate with the people you need to reach.
Secure and Encrypted Message App FAQs
In this article, our goal was to give you several options to choose from when looking for a secure and private messaging app. But some people out there want us to pick a single winner. By far, the most frequently asked question we’ve heard when researching this topic is:
What is the most secure and private messaging app?
We get it that you want us to tell you that one particular messaging app is the most secure and private. But we’re not going to do it. While we have our own opinions on the subject, we prefer to defer to the 82nd Airborne. They recommended Signal.
Conclusion on secure messaging apps
Secure messaging apps remain a great alternative to standard email communications. We’ve said this for years, and even Edward Snowden agrees.
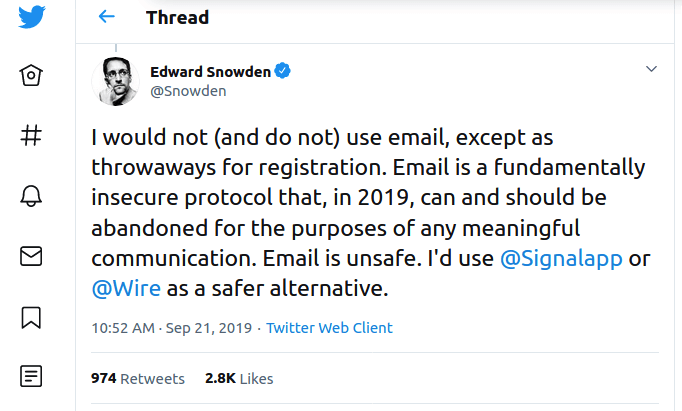
Here are the encrypted messaging apps we have reviewed on RestorePrivacy:
The secure messaging apps and services listed here each takes a slightly different approach to the problem of keeping bad guys out of your business. We’ve given you a quick overview of each of them here. We urge you to think hard about your circumstances, then decide which of these quality products looks best to you.
This guide on the best secure messaging apps was last updated on April 27, 2024.

Leave a Reply