
In this guide we cover all aspects of browser fingerprinting and device fingerprinting in 2022. In addition to explaining what exactly this is, we’ll also show you how to protect yourself against these threats.
Many people use VPN services to hide their IP address and location – but there is another way you can be identified and tracked online. That is through browser fingerprinting.
Whenever you go online, your computer or device provides the sites you visit with highly specific information about your operating system, settings, and even hardware. The use of this information to identify and track you online is known as device or browser fingerprinting.
As browsers become increasingly entwined with the operating system, many unique details and preferences can be exposed through your browser. The sum total of these outputs can be used to render a unique “fingerprint” for tracking and identification purposes.
Your browser fingerprint can reflect:
- the User agent header
- the Accept header
- the Connection header
- the Encoding header
- the Language header
- the list of plugins
- the platform
- the cookies preferences (allowed or not)
- the Do Not Track preferences (yes, no or not communicated)
- the timezone
- the screen resolution and its color depth
- the use of local storage
- the use of session storage
- a picture rendered with the HTML Canvas element
- a picture rendered with WebGL
- the presence of AdBlock
- the list of fonts
Is browser fingerprinting accurate?
Some researchers have found this method of identification to be extremely effective.
Why is this being done?
Browser fingerprinting is just another tool to identify and track people as they browse the web. There are many different entities – both corporate and government – that are monitoring internet activity, and they all have different reasons for doing so. Advertisers and marketers find this technique useful to acquire more data on users, which in turn leads to more advertising revenue.
Some websites use browser fingerprinting to detect potential fraud, such as banks or dating websites, so it’s not always nefarious.
Surveillance agencies could also use this to identify people who are employing other privacy measures to cloak their IP address and location, such as with VPN services or the Tor (onion) network.
Browser fingerprinting test websites
One good test website to see all of the information that is being revealed by your browser is
ipleak.net.
With ipleak.net, you will want to scroll down to the “Geek Details” section where you will be able to see:
- Detected information
- System information
- Screen information
- Plugins information
- Mime-Types information
- HTTP Request Headers
There are also a few websites that reveal browser data and also assess a “uniqueness” score based on your variables in comparison to their database of browsers.
- amiunique.org is another good resource. It is open source and provides more information and updated fingerprinting techniques, including webGL and canvas.
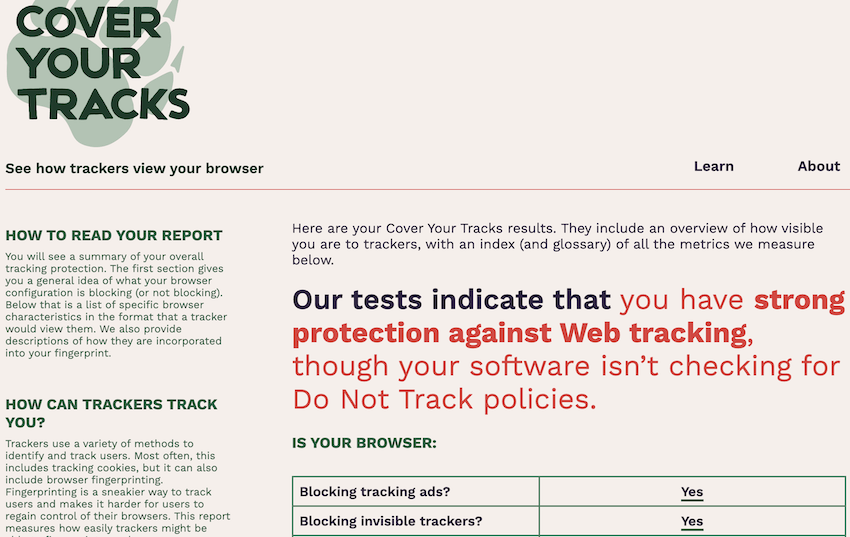
- Cover Your Tracks is run by the Electronic Frontier Foundation. You can learn more here.
Cover Your Tracks is the updated version of a project the EFF has been working on for many years. It gives you a pretty good picture of how susceptible your browser is to finger printing.
How to mitigate your browser fingerprint
Before we jump into potential solutions, it’s important to note that implementing browser fingerprinting protection methods may break some websites. Be sure to research these different options carefully before adjusting your browser settings.
Another consideration is your threat model. How much privacy do you need or want? The answer to that question will be different for every user.
Lastly, I use the word “mitigate” rather than “solve” because browser fingerprinting is a very complex and evolving issue. For example, a new study revealed that there’s nothing you can do to mitigate some fingerprinting attacks on smartphones (discussed more below).
Here are some good ways to mitigate your browser fingerprint:
1. Browser modifications and tweaks
Depending on the browser you are using, you might have some different options for tweaks and modifications to mitigate browser fingerprinting. Below we’ll discuss various Firefox and Brave browsers, which are both secure and private browsers.
Brave browser fingerprinting
Although it is based on Chromium, the Brave Browser may be a good option for those wanting a simple, privacy-focused browser that blocks tracking by default and still supports Chrome extensions. Brave allows you to enable fingerprinting protection, which is under the Brave Shields settings:
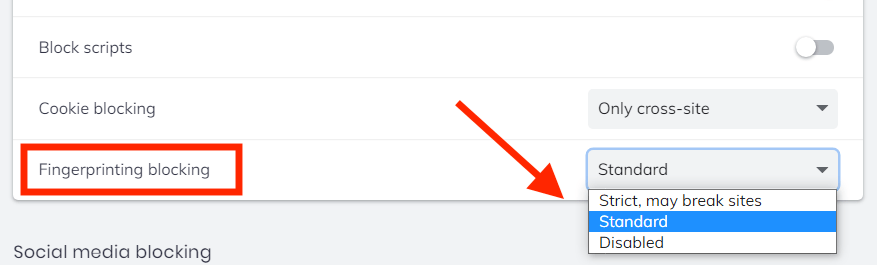
See also this article on Github discussing different aspects of fingerprinting protection in Brave.
Firefox browser fingerprinting
Firefox is a good browser for privacy and security, and it can also be modified and hardened for your unique needs. (For an overview of Firefox privacy tweaks, see the Firefox privacy guide.) The first thing you need to do is type about:config into the URL bar of Firefox, hit enter, then agree to “accept the risk” and make the following changes:
- privacy.resistFingerprinting (change to true) – Changing this value to true will offer some basic protection, but it’s far from a complete solution. The privacy.resistFingerprinting preference was added to Firefox as part of the Tor Uplift project and it continues to be improved.
- webgl.disabled (change to true) – WebGL is another tricky issue for privacy and security. Disabling this preference is generally a good idea.
- media.peerconnection.enabled (change to false) – Disabling WebRTC is a good idea since this can reveal your true IP address, even when you are using a good VPN service. See the WebRTC leak guide for more details and how to disable WebRTC in other browsers.
- geo.enabled (change to false) – This disables geolocation tracking.
- privacy.firstparty.isolate (change to true) – This is another great update from the Tor Uplift project that isolates cookies to the first party domain.
Note: This is just a brief overview of changes that improve your privacy and help to mitigate your browser fingerprint. Nonetheless, there are many different factors that go into fingerprinting and you may still have a unique fingerprint even with these changes.
Firefox with the ghacks user.js file
Another great option is to run Firefox with a unique user.js file, such as the ghacks user.js. This is a custom Firefox configuration file that has been modified for more privacy and security. I like this option because it can save lots of time with setup and is regularly updated and improved. See the Wiki page for an overview and setup instructions.
When I tested a fresh install of Firefox with the ghacks user.js file, amiunique.org showed my browser fingerprint as as not unique.
2. Browser extensions and add-ons to minimize or spoof your fingerprint
There are a number of different browser extensions and add-ons that you may find useful. With that being said here are a few things to remember:
- Be careful with third-party extensions, which could potentially undermine your privacy and security.
- Be mindful that using extensions may make your browser fingerprint more unique (many factors).
Now that we’ve gotten those disclaimers out of the way, let’s examine some browser add-ons that may be useful:
Firefox browser:
- Canvasblocker by kkapsner – Protects against canvas fingerprinting methods (source on GitHub)
- Trace by AbsoluteDouble – Protects against various fingerprinting methods (source on GitHub)
- Chameleon by sereneblue – Allows you to spoof user agent values (source on GitHub)
There are many other Firefox add-ons you may want to consider as well, which are discussed in the Firefox privacy guide. Some of these add-ons are also available for Chromium-based browsers, such as Brave.
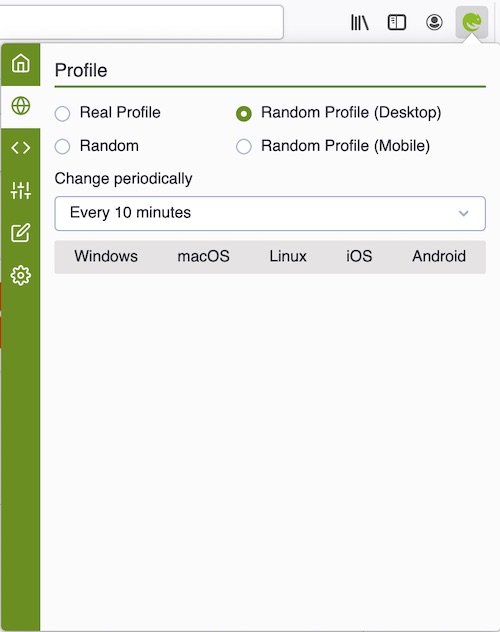
Some people recommend spoofing different user agents through a browser extension, while others suggest this is a bad idea because it might make you more “unique”. Of course, there are many factors to consider, but adding noise to your fingerprint may not be a bad strategy.
For example, with Chameleon, you can cycle through different user agents at various time intervals.
Now let’s look at another option for modifying your browser fingerprint: the use of virtual machines.
3. Virtual machines
You can also consider running different virtual machines, which can utilize different operating systems on your host computer. VirtualBox is FOSS and offers an easy way to run different Linux VMs for more privacy and security. There are many different video tutorials online, depending on your operating system and the VM OS you are looking to use.
Virtual machines offer numerous advantages in terms of privacy and security, while also protecting your host machine. For privacy, VMs allow you to easily spoof different operating systems and also chain VPN services, as explained in the multi-hop VPN guide. This also helps keep your host machine secure by isolating a virtual environment. If the VM were to be compromised, simply delete it and create a new one. You can also use different VMs for different purposes.
4. Tor Browser
Another option is to use the Tor browser, which is simply a hardened and protected version of Firefox. It includes numerous privacy and security modifications that are built into the default version:
- HTTPS Everywhere
- NoScript
- Anti-tracking features
- Canvas image extraction blocked
- WebGL blocked
- Operating system cloaking (shows as Windows 7 for all users)
- Timezone and language preferences blocked
The key here is to use the default version (the developers do not recommend adding any plugins or extensions because this could compromise the browser’s effectiveness).
You can get the latest version of the Tor browser here.
The default version of the Tor browser is configured to run with the Tor (anonymous/onion) network. While the Tor network does have added benefits in terms of privacy, it also has a number of disadvantages:
- Your internet speed will be reduced to around 2 Mbps, making streaming videos or music nearly impossible
- Tor only encrypts traffic through the browser, rather than encrypting all traffic on your operating system like a VPN
- Tor is vulnerable to IP leaks, especially with Windows
- Tor is not safe to use when torrenting (see the Best VPNs for Torrenting guide)
- Tor was created by the US government and is still funded largely by US government grants
- Some consider Tor to be compromised
Ultimately, like all privacy tools, Tor has both pros and cons.
Note: You can also first connect to a VPN and then load the Tor browser as normal with the VPN running in the background. This will hide your real IP address from malicious Tor nodes and give you an extra layer of protection.
5. Don’t expect much privacy on a smart phones
As we’ve covered before, most “smart” devices are data collection tools for various entities.
Smart phones are especially vulnerable to browser fingerprinting. A team of researchers at Cambridge published a paper highlighting how smartphones can be fingerprinted using internal sensors – and there’s nothing the user can do about it.
The paper delves into the technical details, but here’s a brief overview of their findings:
- The attack can be launched by any website you visit or any app you use on a vulnerable device without requiring any explicit confirmation or consent from you.
- The attack takes less than one second to generate a fingerprint.
- The attack can generate a globally unique fingerprint for iOS devices.
- The calibration fingerprint never changes, even after a factory reset.
- The attack provides an effective means to track you as you browse across the web and move between apps on your phone.
Aside from the sensor issue, there are many other reasons for avoiding smart phones if you expect privacy. See our article on controlling communication channels for more info on this topic.
Use a good VPN service
Although a VPN alone won’t protect you against browser fingerprinting, it is a very important privacy tool to hide your IP address, hide your location, and keep your data secure.
If you’re not using a good VPN, your internet provider can easily monitor all your online activity by recording your DNS requests. In many countries, such as the UK and Australia, this is mandatory. Internet providers in the US can also monitor and record their users, and since March 2017, they can also sell this information to third parties (advertisers).
An interesting report from the Federal Trade Commission in the US highlighted how all major internet providers are collecting vast amounts of private data and sharing this data within a wide network of partners. See our article for more details:
Internet Service Providers are Logging Everything You Do Online
Going through all the hassle to protect yourself against browser fingerprinting may be a waste of time if you aren’t using a good VPN that will encrypt your internet connection and hide your IP address and location. The best VPN services report discusses the top recommendations based on the latest results.
For those concerned about privacy (like us), we strongly recommend going with an audited no logs VPN, preferably one that has passed multiple audits.
As mentioned above, combining VPNs also adds additional privacy and security while distributing trust across different VPN providers.
Browser Fingerprinting FAQs
Below are some of the other questions we see regarding browser fingerprinting.
Browser fingerprinting is a method to identify and track you online based on numerous different variables, including your operating system, timezone, browser headers, plugins, cookie preferences, tracking preferences, screen resolution and more. By aggregating these browser variables, third parties can create a unique fingerprint of your browser so that you can be identified and tracked online.
Browser fingerprinting is used primarily by advertising agencies and data brokers. By creating a unique browser fingerprint, ad agencies and data brokers can track your activities as you browse different websites. Your browsing activity can then be linked to your unique browser fingerprint, which allows you be targeted with ads based on your online activities. Additionally, your activities and identity can be sold to third parties by data brokers and other ad-tech intermediaries.
No, a VPN alone will not protect you against browser fingerprinting. While a VPN will hide your true ISP-assigned IP address and location, it will not protect you against browser fingerprinting, which is based on unique variables without your browser and operating system. To protect yourself against browser fingerprinting, you will need to modify the settings within your browser, as we describe above. However, you should still use a VPN to hide your IP address and location to better protect your online privacy.
Private browsing alone will not protect you from browser fingerprinting and it also won’t hide your IP address or location. In essence, private browsing is not actually private. We explain why incognito/private browsing is not private and the steps you can take to actually have more privacy and security online with your browser.
Use browser fingerprinting protection in 2022
While browser fingerprinting may seem like a daunting issue to some, mitigating your browser fingerprint is relatively easy. For those seeking the highest levels of privacy and security, I’d recommend utilizing virtual machines and perhaps chaining different VPN services (using more than one VPN at the same time).
As a general rule of thumb, Firefox remains a great all-around browser after some modifications and configuration. The secure browsers guide also discusses various options, while the Firefox privacy modifications guide takes a deep-dive into tweaks, extensions, and custom configuration.
Another issue to consider, which was not mentioned in this guide, is using a good ad blocker. Ads today basically function as tracking – they record your browsing habits so you can be hit with targeted advertisements. A good add-on is uBlock Origin, but there are other recommendations in the ad blocker article and privacy tools guide.
This browser fingerprinting guide was last updated on April 27, 2024.

Leave a Reply