
In today’s world, the typical household is full of technological wonders, all connected in a home network that runs through a router to the internet. You know, that internet that is full of hackers, spies, malware, and who knows what else, all of them just itching to get access to your tech. This has all the makings of a disaster.
That’s why you need to secure your home network. Now.
In this guide we’ll give you a plan to secure your home network as quickly and easily as possible. It’ll take some work, but in just a few hours you can probably make your home network the most secure home network in your neighborhood. And that is probably enough. As in other crime scenarios, the bad guys are more likely to look for an unsecured network to hack than to spend a going after harder targets.
We’re going to attack this by dividing up the tasks. Securing your home network involves different types of changes, some on your router, some on the devices attached to your home network, and some in your head. Here is how we’ll break things up:
- What to do to your router
- What to do to your devices
- What to change in your head
- Optional hardcore security steps
There is potentially a lot of work here. What we recommend you do is go through the list in order, completing all the security steps you can or will do in that section before moving on to the next. This way you won’t constantly be jumping back and forth from the router to a device to changing the way you do things back to the router and so on.
Getting all this sorted out will probably take more than one session, so keeping organized in this manner will reduce the chances of missing something important as you go along.
1. What to do to your router
Your router is the heart of your home network. It is the central point where all your devices connect to the internet, and to each other. Since the most common home network depends on a single router that connects to devices wirelessly, we’ll assume that as a starting point.
As the central point of connection, it makes sense that the router is the first place to look if you want to secure your network. You’ll want to check your router’s documentation to find out how to log in to the router’s control panel.
Once you log into the router, there are a lot of adjustments you can make that will quickly make your home network much more secure against attack.
Here they are, in the order we recommend you do them.
1.1. Change your WiFi password and SSID
If you bought your router from a store, it likely came with a preset WiFi password and SSID (Service Set Identifier). Believe it or not, anyone who knows which model of router you have can look up these preset values online in seconds.
If the techs from your ISP (Internet Service Provider) installed your router, they probably set the password and SSID for you, and recorded that information for the company’s records.
Note: We should also point out here that internet service providers are also a risk from a privacy standpoint. See our article on how internet service providers are logging browsing history.
In either case, outsiders know, or can easily look up, the information they need to log into your WiFi network. The solution to this problem is obvious: change the WiFi password and SSID.
We have a guide on creating strong passwords, but you can also check the documentation that came with your router. If not, you can find the documentation for your router online, and follow those instructions to make the change.
While you can come up with any password and SSID that you wish, we do have two suggestions: make the SSID boring, and the password long.
A boring SSID is one that doesn’t draw attention to itself, and doesn’t give away any personal information. You don’t want to create an SSID that might stick out in the mind of some hacker scanning all the WiFi networks in your area. Including personal information in your SSID can not only draw unwanted attention, but can help the hacker break into things.
Making the password long makes it much harder for a hacker (or a nosy neighbor) to guess your password and log onto your network. Ideally, you should make your WiFi password at least 12 characters long, and not comprised of a famous quote, or any kind of sentence fragment.
While long passwords are definitely more secure, you run into the problem of remembering them. To address that issue, we strongly urge you to…
1.1.1. Invest in a password manager
Investing in a password manager is a much better option than trying to remember a multitude of long, complex passwords. There are a variety of password managers available, with price points ranging from too high for our taste, to free.
Click the following link for a review of the best password managers.
1.2. Set WPA2 encryption
You need some way to keep unauthorized persons from connecting to your wireless network. All WiFi routers can encrypt their signals, but the encryption is not always turned on, or may not be set to the most secure option. You want to make sure that you set your router to use WPA2 (Wireless Protected Access 2) encryption.
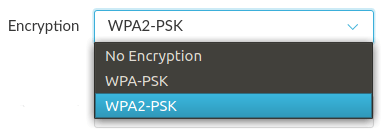
There are variants of WPA2 that sometimes appear, so if you have more than one to choose from, avoid any that include the acronym TKIP, and go with one that includes the acronym AES.
1.3. Disable WiFi Protected Setup (WPS)
WPS (WiFi Protected Setup) is a system that makes it slightly easier to connect a new device to your WiFi network. Unfortunately, WPS is incredibly vulnerable to hacking. A program called Reaver-WPS can use a vulnerability in WPS to crack the strong WPA2 encryption you just set up on your router.
The only defense? Disable WPS. Do it now since Reaver-WPS can hack its way into your network within a few hours if you don’t.
1.4. Disable Universal Plug and Play (UPnP)
UPnP (Universal Plug and Play) is a standard that allows devices to open a port to the internet to communicate outside your network. It assumes that any program running on your device that asks for such a connection does so for a good reason.
If you think that sounds like a pretty insecure assumption, you are correct. Let a hacker get some malware on your device, and it can use UPnP to open you up to all sorts of evil activities.
Unless you would be okay with letting anonymous hackers do whatever they want with your devices, disable UPnP right away.
1.5. Disable remote management
Remote management gives you access to your router’s administrative interface from devices that are not directly connected to your network. The problem is that if you can reach the administrative interface, so can all the world’s hackers.
While it would be nice to know that you can log into your router while on vacation, it is even nicer to know that you’ve given hackers one less way to get into your network. Find the remote management option and turn it off.
1.6. Change your router’s admin password
While you are making all these other changes, this would be a good time to change the administrator’s password for your router. You already changed the WiFi password. Now we are talking about the default password you used to log in to the router and make all these changes so far.
This password shouldn’t be at much risk, since someone needs to be connected to your network to mess with it (you did disable remote management, right?). Still, it only takes a moment or two to change this password, and by now you should have a password manager to store the new password in, so you might as well do this too.
1.7. Activate your router’s firewall
A firewall is a system that controls messages passing back and forth between your devices and the internet. Without getting into the details, a router’s firewall determines what messages can pass between your network and the internet.
Among other things, a firewall can stop traffic from malicious websites from entering your network. It can also stop malicious programs that have made it into your network from sending data (think your credit card info or other personal data) to the bad guys who created the malicious program.
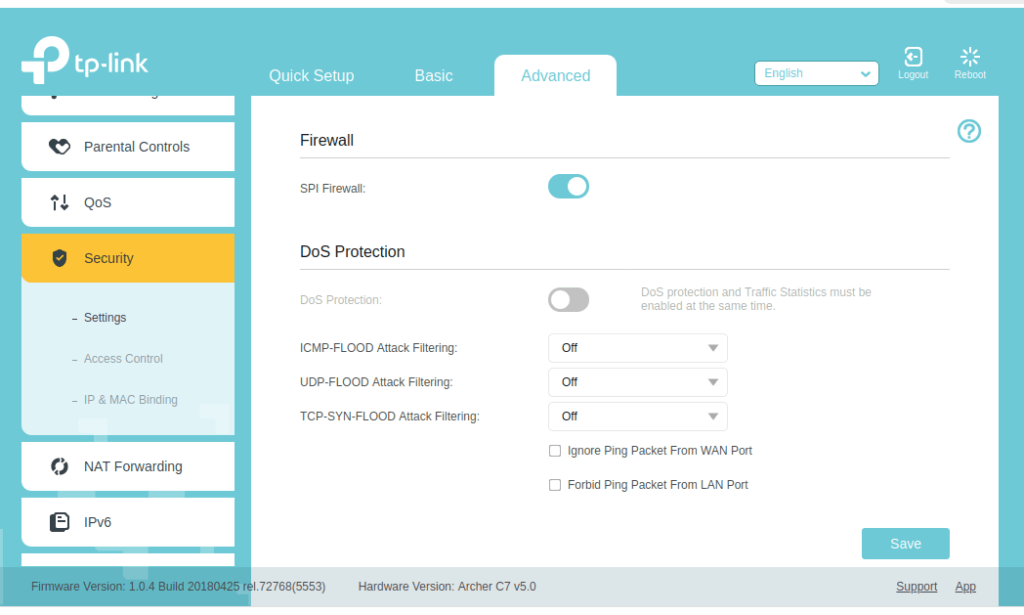
Most routers have a built-in firewall, but you may need to activate it manually. Look for an entry called Firewall, or SPI Firewall, or something similar in the router’s settings and make sure it is turned on.
1.8. Check for firmware updates
Just like your regular devices, your router gets firmware updates from time to time. Since these updates usually deal with bug fixes or patches that protect against hack attacks, it is vitally important that your router firmware is up to date.
Some routers will do automatic firmware updates without any intervention on your part. Others require you to update them manually.
While doing manual firmware updates can be a pain, it is important to do an update now if one is available. Most people never update the firmware in their routers, and hackers happily exploit those out of date routers to wreak havoc on home networks. Just do it.
1.9. Make visitors use the Guest network
In today’s hyper-connected world, one of the first questions people usually ask when they arrive at your home is, “What’s the login for your WiFi?”
The problem is, if you want to have a secure network, you can’t let every Tom, Dick, and Harry who comes along have access to it. Once you give someone the password to your WiFi network, it is out of your control.
They can share your login info with other people. They can use your connection whenever they happen to be in range. They can accidentally share your login info with the entire Darknet when some hacker breaks into their device.
If you want to be secure, you have two options. One option is to tell people they aren’t allowed to use your internet connection (that’ll go over real big with your friends). Or you can set up a guest network for visitors to use.
A guest network gives your guests access to the internet, without giving them access to the rest of your network. It is an elegant solution to the problem of giving people internet access without risking your network security. And as the following page from our TP-Link router manual shows, it is usually super simple to set up a guest network.
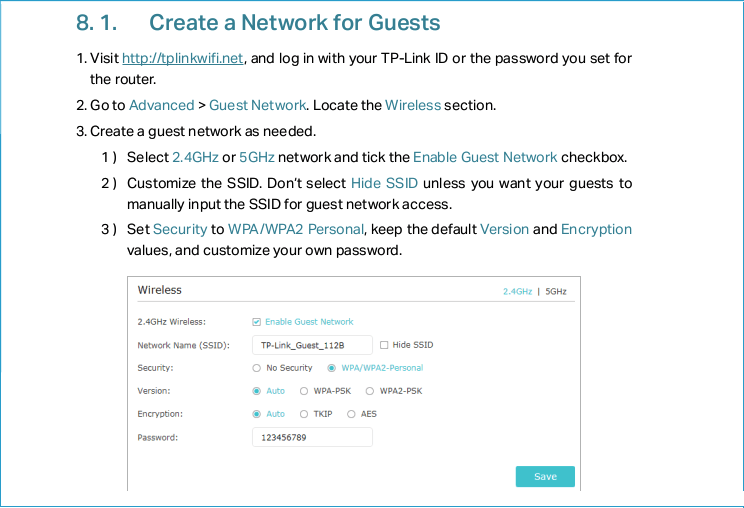
If your router supports it, you should definitely set one up.
2. What to do to your devices
Once you have your router sorted out, it is time to move on to securing your devices. Unless you only have a few devices connected to your router, this will probably be the most time-consuming part of securing your network.
Each device that uses your internet connection needs to be dealt with individually. There’s no way we can cover exactly what you need to do to secure every type of device, so this section will be pretty high level.
2.1. Check for software/firmware updates
Just as with your router, you need to keep each internet-connected device updated. For things like computers, phones, and tablets, you’ll want to check for and install the latest software updates before doing anything else.
For other devices that have some kind of administrative interface, you’ll want to check the documentation to see if there is a way to check for updates.
And the rest of the stuff? Let’s hope the manufacturer built in a way to automatically update the software/firmware.
Having the latest updates installed is the best way to secure your devices against attacks. This is particularly important for mobile devices. Your smartphones in particular spend much of their time with you out in the world, rather than in safe in your house connected to your (relatively) secure home network.
If a mobile device gets infected with something smart and nasty, your device will carry that crud right past your first line of defense (the router) into the heart of your home network. While you will ideally apply this step and all the following ones to every internet-connected device you own, if you have to prioritize, take care of the mobile devices first.
2.a. Change preset usernames and passwords on devices
Some of your devices probably came with preset usernames and passwords. You will want to change those immediately. Because they are preset at the factory, or buy whoever installed the device in your home, they are inherently insecure. Somebody else either knows them, or knows how to find them.
So change any preset usernames and passwords you can. Use long passwords and store them in that password manager so six months from now you don’t make yourself crazy trying to remember the login details for your intelligent toaster or vacuum cleaner.
2.3. Change the usernames and passwords you assigned
What about devices that have usernames and passwords you assigned? You should really change them if possible. You are going through a lot of effort to secure this network of yours and it is conceivable that someone who shouldn’t knows this information. Changing the login information eliminates this potential vulnerability.
2.4. Install antivirus software
For devices where it exists, install antivirus software. That means your computers, smartphones, tablets, and anything else that can run it.
2.5. Activate device firewalls
Just because you have activated the firewall built into your router, it doesn’t mean you can’t use the firewalls built into some of your devices too.
Activating the firewall on each device that has one simply adds more layers of defense. Again, this is particularly important for mobile devices that spend part of their time outside your safe and secure network. Out in the world, the firewall will help keep malicious websites from contaminating your device.
Back on your network, the firewall will protect your device from any contaminated devices on your network and reduce the odds that if your device is already infected it will infect the rest of the network.
2.6. Make smart devices use the guest network
Remember the guest network we set up so people can use your internet connection without threatening the security of your main network? Consider connecting all your smart devices to that same guest network.
You probably have lots of these devices and a limited ability to know how secure they really are. Why not put them on the guest network, where if something goes sideways your main network is still safe.
2.7. Delete unwanted, pre-installed software
Most new computers and similar devices come from the factory jammed with pre-installed software you don’t want. It often uses up system resources, consumes ridiculous amounts of disk space, slows down your machine, and may directly violate your privacy or weaken your device’s security.
This junk, sometimes called bloatware or crapware consists of things like antivirus trial software, shopping apps, search engine toolbars, adware, spyware, and other things that virtually no one wants or needs.
You want to uninstall anything like this immediately, even if your device seems to be working fine. However, this can be easier said than done, since much bloatware is designed to be difficult or impossible to uninstall.
2.8. Back up important data
This isn’t a way to improve the security of your network so much as to help you recover if the network does get breached.
Wherever possible, back up any devices that contain important information. Ideally, you would back up to a cloud storage service, or at least an external disk drive or storage array.
Whatever backup options you have available, the idea is to be able to retrieve as much of your data as possible if something disastrous happens to your network.
3. What to change in your head
While making the hardware and software changes we’ve discussed is important, so is changing the way you think about the security of your home network.
Most of us set up our network, then more or less ignore it until there is a problem. We have to do better than that if we want to keep our home networks secure. Here are the main things you should keep in mind when it comes to your network.
3.1. Your network needs regular maintenance
If you want to keep your network secure, you need to do some basic maintenance.
The most important maintenance step is to ensure that your router’s firmware is up to date. Since the router touches everything else on the network, this should be your #1 concern. If your router doesn’t do automatic firmware updates, establish a schedule for checking for updates manually. Once a month is probably sufficient.
The next maintenance step is to check for updates on devices attached to your network. Update anything you can that doesn’t update itself automatically. You might as well make these checks on the same schedule as you check your router for updates.
3.2. Avoid sketchy software or websites, as well as off-brand devices
While the steps you have taken to boost the security of your home network are great, no defense is perfect. You can minimize the risk of your defenses failing by avoiding unnecessary risks.
Installing software from some random website could result in you bringing spyware or worse onto your network.
Visiting sketchy adult websites or darkweb marketplaces could expose your network to vicious attacks.
Connecting off-brand devices to your network is a double threat. The security of the device itself might not be very strong, possibly opening a vulnerability. And there is the possibility that the device intentionally carries malicious software aimed at stealing your data or opening up your network to further attacks.
Stick with name brand devices, well-known websites, and software from major publishers. Doing so will reduce the stress on your network’s security.
4. Optional hardcore security steps
The steps you’ve taken so far will make your home network far more secure than most. But if you want to take this even further, here are a number of additional steps you can take.
4.1. Disable WiFi when not in use
If you are going to be away from home for a while, consider turning off WiFi. There is no reason to keep WiFi active if you are not using it, and no one can try to hack your WiFi if it is turned off.
The exception here is if you have some wireless devices that must remain active while you are gone, such as wireless security cameras.
4.2. Reduce your WiFi footprint
You may not want to disable your WiFi, but you can still take steps to make it less accessible to attackers. WiFi signals can penetrate the walls of your house, but they don’t have a very long range. Reducing your WiFi footprint means reducing the amount of the signal that gets outside your house where an attacker can detect it.
Here are a few things you can do to reduce your WiFi footprint:
- Position your router near the center of the house. WiFi signals radiate in all directions. If you place your router against an outside wall, half of the signal goes out of your home. Placing the router in the center of the house will both ensure better coverage inside the house, and reduce the amount of the signal that makes it out of the house.
- Switch to the 5 GHz band. Many routers today can use either the 2.4 GHz radio band or the 5 GHz band. 5 GHz doesn’t penetrate walls as well as 2.4 GHz does. By setting your router to use only the 5 GHz band you reduce the amount of the signal that gets out of the house. An added bonus is that 5 GHz is much faster than 2.4 GHz, which could mean faster data transfers inside your house.
- Reduce the router’s signal strength. If you have a small house, or a powerful router, you may be able to reduce its signal strength. Doing so would once again reduce the amount of the signal that gets out of the house. Just make sure you keep the signal strong enough that all your own devices can connect.
4.3. Disable WiFi altogether
Disabling WiFi altogether is the ultimate way to keep someone from hacking your WiFi. Whether this solution is practical for you or not depends heavily on what you have connected to your network, and where you need those connections. Dealing with ethernet cables and dongles can be a pain, but this is faster and more secure than WiFi by a long shot.
Even if you can’t do without WiFi completely, you might want to consider physically dividing your network in two. One portion could be wireless, while the other only uses wired connections.
The details of setting up this kind of split network are beyond the scope of this guide, but the basic idea involves using a wired-only router to split the network into two subnets. One subnet would have its own WiFi router, while the other would have its own wired router. Devices that handle tasks like online banking could be connected to the wired-only subnet, while less critical devices could use the WiFi subnet.
4.4. Control access by MAC address
Every internet-connected device is assigned a unique MAC address. Routers are normally set up to accept a connection from any device that knows the correct username and password. But most routers can be configured to only accept connections from devices with specific MAC addresses.
Setting this up takes a little work and isn’t foolproof (hackers have tools for transmitting fake MAC addresses) but this approach would block people like the plumber of the nosy kid next door from logging onto your network.
4.5. Install a VPN on our router
Using a VPN (Virtual Private Network) is a great way to protect a device. The VPN hides the device’s location, while encrypting your connection so no one can see what you are doing online. While a VPN is a great solution for a single device, using one to protect your entire network presents a couple of problems. Many wireless devices appearing in modern households are incapable of running a VPN. Additionally, most VPN services support only a handful of simultaneous connections, but there are exceptions, such as with Surfshark.
The solution is a VPN router. If you can run the VPN software on your router, the router can protect everything on the network at once. To learn more about this elegant solution to protecting your entire network with a VPN, check out our report on VPN routers.
4.6. Change DNS servers
When the techs from your ISP set up your connection, they almost certainly configured your router to use their Domain Name Service (DNS). The DNS converts the human-readable internet address you enter (www.restoreprivacy.com, for example) into a computer-readable IP address that looks something like this: 45.79.189.67
ISPs want you to use their DNS because they can record the addresses you visit. This information is useful to them for planning and marketing purposes. If your ISP is in the United States, they can even sell this data about where you go online to anyone they want.
There are two solutions to this problem. One is to configure your router to use a DNS that protects your privacy, such as OpenDNS or CloudFlare.
The best solution is to upgrade your network to use a VPN router as we discussed in the previous section. Top VPN services like ExpressVPN or NordVPN provide their own encrypted DNS that is secure against snooping by your ISP or any of the other busybodies roaming the internet looking for personal information to steal.
Conclusion
In this guide we laid out a basic plan for securing your home network. We divided up the work into logical areas, and covered the particular steps you can take in each to quickly increase the security of your home network.
While there is always more you can do to strengthen the security of your network, if you follow the plan, in a few hours you’ll likely own the most secure home network in your area. This doesn’t guarantee that your network is invulnerable (no one’s network is invulnerable). And it doesn’t guarantee that some hacker won’t decide that he just has to break into your home network.
But taking action using the plan here will greatly reduce the chance that your network will be the target of a serious hacking effort. And if by some chance that does happen, your network will have at least a fighting chance to resist the assault. Which is far better than the vast majority of homeowners can expect.

What are your thoughts on segregating Airbnb guests from my home network? My ISP (Cox Cable) does not provide guest access services on their normal residential service but recommended adding a 3rd-party router downstream from the modem.
Thanks
Good idea.