
The world is changing fast and your private data is at risk whenever you go online. Numerous entities, both public and private, are working hard to track, monitor, and record your digital activities. There are many reasons for this:
- Advertisers (including Google and Facebook) want to know everything about you, including your web browsing history, location data, contacts, and more. This makes it easier (and more profitable) to serve you targeted ads and influence your purchases.
- In an age of pandemics and lockdowns, many governments around the world are working hard to track movement and biometric data of their citizens.
- ISPs (internet service providers) are spying on their customers and feeding this data to various third parties, including advertisers and government agencies. In many countries, this is not only legal, but required. See for example in the United Kingdom (with the Investigatory Powers Act), United States (Senate Joint Resolution 34), and now also in Australia (mandatory data retention).
- The internet is also becoming less free due to censorship efforts and content blocking. Whether it is China, Germany, the UK, or the United States, various groups are working hard to censor content online.
But don’t get discouraged. Alternative technologies are experiencing a renaissance as awareness about these issues grows and people seek out solutions. Indeed, for all of the problems listed above, we find excellent solutions to give you more privacy, security, and freedom in your digital life. And that is the purpose of this guide: to give you solutions. Here’s what we’ll cover in this guide:
- Secure and privacy-focused browser
- Virtual Private Network
- Ad blocker
- Password manager
- Secure and encrypted messaging
- Private search engine
- Private email
- Operating system
- Antivirus software
- Data removal tools
But before we begin, one key consideration is your threat model. How much privacy and security do you need given your unique situation and the adversaries you may face?
Most people today are seeking protection against online tracking by advertising networks as well as a higher level of privacy and security. Others, such as investigative journalists working with sensitive information, would likely need an even higher level of protection. So keep this in mind as you proceed. Everyone is unique in their approach to privacy and security; there is no one-size-fits-all solution.
So here’s what you need:
1. Secure and privacy-friendly browser
Everyone needs to be using a secure and privacy-friendly browser for three important reasons:
- Browsers have a large attack surface and can be compromised in many ways.
- By default, most browsers contain lots of private information, including your browsing history, usernames, passwords, and autofill information, such as your name, address, etc.
- Browsers can reveal lots of identifying information about your location, system settings, hardware, and much more to third parties.
Secure Browsers: Based on my own tests and experience, here are the most secure browsers that also respect your privacy:
- Brave – Brave is a chromium-based browser that is very privacy-focused right out of the box. By default, it will block ads and trackers, and it’s also customizable, fast, and has built-in protection against browser fingerprinting.
- Firefox (modified) – Firefox is a great browser for both privacy and security after doing some modifications. It is highly customizable to give you the level of security and privacy you desire, while also being compatible with many browser extensions. See our guide on how to modify Firefox for more privacy.
- Tor browser – The Tor browser is hardened version of Firefox that also utilizes the Tor network by default (but this can be disabled).
- Ungoogled Chromium – As the name suggests, Ungoogled Chromium is a stripped-down Chromium browser that has been “Ungoogled” for more privacy. Source code is here.
- LibreWolf – This is a fork of Firefox that has been tweaked for more privacy and security.
Of course, there are many browsers on the market and choosing the best one all comes down to your own needs and tastes. Chrome, Opera, Safari, and Vivaldi also get some attention, but they’re not the best choices from a privacy standpoint.
2. Virtual Private Network (VPN)
Using a good VPN (virtual private network) is one of the simplest and most effective ways to protect your privacy, secure your devices, and also access blocked content online. A VPN is a critical tool to be using, especially with internet service providers spying on their users and logging all activity.

Here are some of the problems that VPNs can solve:
- ISP Spying – A VPN will encrypt and anonymize your internet connection. This makes your traffic completely unreadable to your ISP and other third parties.
- Blocked content – A VPN will let you easily get around blocked content and censorship. Simply connect to a VPN server in the region you need and access the website or stream as normal.
- IP and location tracking – Many websites and advertisers track users through their IP address. With a VPN, your IP address and location will be replaced by the VPN server’s IP address and location.
- Copyright issues – Torrenting and streaming media from third-party sources can come with some risk in the form of copyright issues. A VPN will anonymize your IP address and help keep you safe.
We’ve tested all of the popular VPN services and the results can really vary. Below are our current recommendations that are private, secure, fast, and reliable on many platforms.
- NordVPN – Best all-around VPN with secure apps for all major devices and very fast speeds (over 750 Mbps). Great for streaming plus extra security features (with a 74% off coupon).
- Surfshark – Best VPN for many devices (unlimited)
- ExpressVPN – Secure and reliable VPN service
- Proton VPN – User-friendly and private VPN in Switzerland
We have other recommendations and providers in our guide on the best VPN services.
And if you are new to VPNs, we also have a guide on how to use a VPN.
3. Advertisement, tracker, and malware blocker
A good ad blocker is essential for privacy and security reasons. From a privacy perspective, it’s important to block ads because they also function as tracking by recording your online activity to create an intimate user profile. This data is then used for targeted ads and/or sold to other parties.
Ads are also risky from a security perspective because they can contain malicious code that can infect your device when a web page loads – no clicks required.
Effectively blocking all ads is the only way to go. Here are a few different options from our guide on the best ad blockers:
- Browser ad blocker extensions – Browser-based ad blocker extensions, such as uBlock Origin are quite popular, but they also come with some tradeoffs. Online ads may still be using up resources and tracking you, even if the ads are not being displayed. Choose your ad blocker carefully – some ad blockers will collect user data for profit and/or show you “approved” ads.
- VPN ad blocker – There are now many VPNs with ad blocking built in. With this method, the VPN can effectively block ads, trackers, and malware at the VPN server, thereby protecting your devices.
- Ad blocker apps – A dedicated app will most likely do a very good job blocking ads on your device. One popular and well-regarded option is AdGuard.
- Ad blocking on a router – Ad blocking on a router can be accomplished various ways – from using ad blocking DNS to loading custom filter lists onto your router.
- Pi-hole – Pi-hole is a network-wide ad blocker that functions as a DNS server and can be deployed in various ways. It is most often used on a Raspberry Pi, connected to your home router (but there are many other different setup options).
The best ad blocking setup will depend on your situation and needs. If you have numerous devices you use at home, setting up a network-wide ad blocker would be a good solution for blanket protection. uBlock Origin remains a popular option for browser-based ad blockers. However, I like NordVPN with the Threat Protection feature as a simple, all-in-one solution for VPN and ad-blocking.
4. Password manager
The topic of passwords is actually quite large, encompassing password strength, password management, and password storage. In this section we’ll focus on password management and storage. Many people store passwords directly in the web browser — but this can be risky.
A more secure method is to use a dedicated password manager app. And note that a dedicated password manager can also offer browser extensions that are convenient and secure. Here’s a screenshot of Bitwarden, which is one of our favorites:
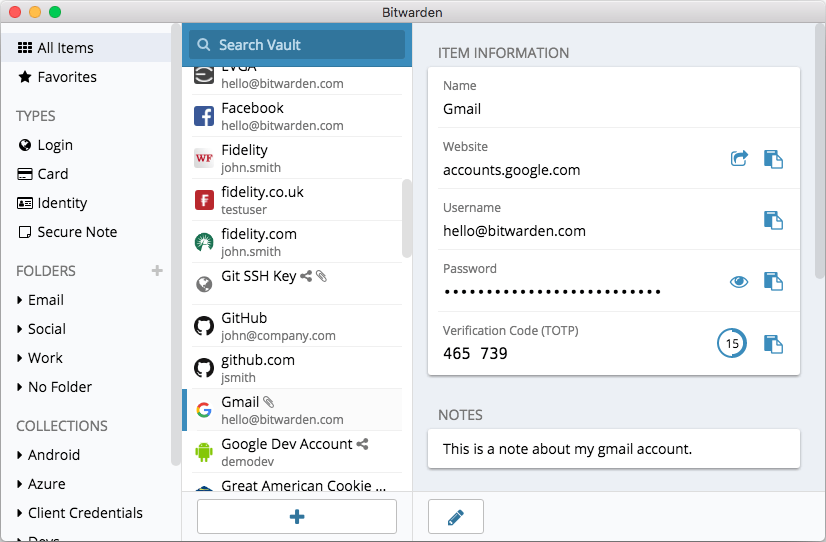
Here are the best password managers we have tested:
- NordPass – From the makers of NordVPN and NordLocker, NordPass is a secure, user-friendly password manager that has also passed a third-party audit. (See the NordPass review here.)
- Bitwarden – A free and open source password manager that is user-friendly and secure. (See our Bitwarden review.)
- 1Password – Another great option is 1Password, with many features and strong security standards for all types of devices (our 1Password review has more info).
- KeePassXC – As a locally-hosted password solution, KeePassXC differs from the others on our list. See the pros and cons of this password manager in our KeePass review.
Start using a good password manager today. See also our guide on how to create strong passwords.
5. Secure and encrypted messaging apps

Many people are turning to secure and encrypted messaging apps over concerns with privacy and security of other popular messengers. For example, WhatsApp collects and shares data from your phone with Facebook, the parent company of WhatsApp. If you find this concerning (and you should), then consider some of the secure alternatives below.
Additionally, with the inherent limitations of email, we recommend a secure messaging app for those wanting the most secure messaging platform possible. The secure messaging apps below utilize strong encryption standards and work well for teams or individual use on various operating systems and devices.
- Signal – This is probably the most popular secure messenger with a rapidly-growing user base. It is free, open source, and very secure. We really liked how it performed in our Signal review — but also noted some drawbacks, such as the need to use your phone number for verification.
- Wire – Based in Switzerland, Wire is another great option that is secure, user-friendly, and fully featured. While there is a free version for personal use, it is hard to find, as described in our Wire messenger review.
- Threema – This is one of the few paid encrypted messengers, but it’s only $2.99 for a lifetime license. Threema is also based in Switzerland and is open source. See our Threema review here.
- Telegram – Telegram is a very popular encrypted messaging app out of Russia, but it also is not encrypted by default. See the pros and cons in our Telegram review.
With all of the people abandoning WhatsApp and going over to Signal, there’s a better chance to connect with people you know on a secure platform. This trend kicked off early last year and we hope to see it continue!
Note: Also keep in mind that standard SMS text messages are not secure or private. They can be read by your phone service provider and are susceptible to man-in-the-middle attacks and also eavesdropping by Stingray devices. When privacy matters, use a good secure messaging app.
6. Private search engine
The big search engines (Google, Yahoo, Bing) record and track your searches, which helps them to build a user profile for their advertising partners.
Consider these privacy-friendly search engines instead:
- MetaGer – An open source metasearch engine with good features, based in Germany.
- Searx – A privacy-friendly and versatile metasearch engine that’s also open source.
- SwissCows – A zero-tracking private search engine based in Switzerland, hosted on secure Swiss infrastructure.
- Qwant – A private search engine based in France.
- DuckDuckGo – A private search engine based in the US.
- Mojeek – The only true search engine (rather than metasearch engine) that has its own crawler and index (based in the UK).
- YaCy – A decentralized, open source, peer-to-peer search engine.
There are also a few “private search engines” that are now owned by advertising companies. For example, Startpage was bought out by System1, a pay-per-click ad company. For more information, see our guide on private search engines.
7. Private email
Many of the popular email providers, such as Gmail, Yahoo, and iCloud are not good choices when it comes to privacy. Would you want random people having full access to your emails, collecting data for targeted ads, or passing the information on to third parties? This actually happens.
- Gmail gives third parties full access to emails and also tracks all of your purchases by reading the receipts in your inbox.
- Advertisers are allowed to scan Yahoo and AOL accounts to “identify and segment potential customers by picking up on contextual buying signals, and past purchases.”
- Yahoo was found to be scanning emails in real-time for US surveillance agencies.
And while Gmail remains the most popular service in the world, you pay with your privacy. Consequently, as awareness about these issues grows, many people are seeking alternatives to Gmail.
If you care about privacy and the security of your data, consider these secure email services. Here are some excellent options:
- Proton Mail – Best for strong encryption (33% off coupon)
- StartMail – Private email hosted in The Netherlands (50% off coupon)
- Mailfence – A secure and customizable email service
- Tuta Mail – Secure Email for Any Device
- Mailbox.org – Affordable private German email service
- Posteo – Reliable anonymous email service
- Runbox – Private email in Norway
- CounterMail – Swedish email with strong security features
- Kolab Now: Swiss email, compliant with GDPR, HIPAA, and PCI
- Soverin – Basic private email service
And if you want to learn more, check out these reviews:
- ProtonMail Review
- StartMail Review
- Tutanota Review
- Mailfence Review
- Mailbox.org Review
- Hushmail Review
- Posteo Review
- Fastmail Review
- Runbox Review
Note: We also have a guide on encrypting email.
8. Operating system
Consider using the free and open source Linux operating system. There are many different versions of the Linux operating system designed for different types of users:
- If you want the look and feel of Mac OS or Windows, check out Elementary OS.
- Ubuntu, Mint, and Debian are other popular options.
Tails is another privacy-focused operating system that can be run live on a USB drive, CD, or SD card.
Problems with Windows and Mac OS
Windows – The latest version of Windows (Windows 10) is a platform built for total surveillance – giving corporations and governments complete access to everything you do on your machine. Aside from data collection concerns, most malware targets Windows users – another serious drawback and security risk.
Mac OS – While Apple may be slightly better in terms of privacy, it too has problems. Just like Microsoft, Apple has configured its operating systems to collect vast amounts of your private data, whether it is browsing history through Safari, connection data, location services, and more.
9. Antivirus software
While not necessarily a “privacy” tool, using good antivirus software may be wise depending on your situation. The problem, however, is that many antivirus solutions abuse your privacy and may come with some invasive and “unwanted” additions.
Just like with sketchy free VPN services, free antivirus software can also be problematic. In testing eight popular free antivirus suites, Emsisoft discovered that seven of them were bundled with PUPs (potentially unwanted programs), which can be harmful and very annoying. Tip: avoid free antivirus software!
Another major issue is privacy. Many popular antivirus suites utilize invasive data collection, to include browsing history, “suspicious” files, metadata, and more. Carefully read through the privacy policy of your antivirus before installing.
Although RestorePrivacy does not devote much attention to antivirus software, one solution that offers the highest levels of security while also respecting user privacy is Emsisoft. Another potentially good option, which is entirely FOSS, is Clam AV.
See also the antivirus privacy guide.
10. Data removal tools
As regular readers of this site know, personal data is valuable. In fact, there massive companies working behind the scenes to collect, compile, and sell your private data to third parties.
While there are good solutions for how to delete your digital footprint, there are also tools that take an active approach in targeting these data brokers. These types of tools and services are becoming increasingly popular, especially as the data collection problem becomes increasingly worse.
Here at RestorePrivacy, we have tested many different market leaders, such as DeleteMe and Incogni. Based on our tests and analysis, these are some of the top options:
- Incogni – Developed by the team behind the popular VPN service Surfshark, Incogni is a simple-to-use solution that focuses on efficient data removal across a wide network of platforms.
- DeleteMe – A popular choice that offers a wide variety of features and services designed to protect your privacy and keep your personal data away from data brokers and people search sites.
- Optery – A comprehensive tool that prioritizes the secure erasure of data from various databases, helping users regain control of their online information.
See the best data removal services here.
Conclusion: Restore your privacy and take control of your data
That’s all for now, although this guide will continue to be updated with more privacy tools and information. We’re also keeping an eye on discussions surrounding privacy tools on various forums, such as Reddit.
If you have any feedback, tips, or suggestions based on privacy and security tools you are using, feel free to drop a comment below!
This article was last updated on May 31, 2024.

Can you recommend an end to end encrypted to do list / task manager app for iOS?
Many thanks
GK
I recommend ESET or Emsisoft
This brutal new malware could absolutely destroy your Windows PC
Initial attack hits Ukrainian targets, and further attacks can’t be ruled out
https://www.techradar.com/news/this-brutal-new-malware-could-absolutely-destroy-your-windows-pc
Simple Mobile Tools is selling smartphones called Simple Phone with an open-source, Android-based operating system preinstalled. YMMV.
https://simplephone.tech/
Shelter is a very interesting Android app that enables Android patrons to utilize their device’s work profile to isolate or even copy apps on an Android user’s device.
https://www.makeuseof.com/shelter-sandbox-android-apps/
Listening in on conversations is what Google Assistant, Siri, etc. are all about.
https://www.bleepingcomputer.com/news/security/google-home-speakers-allowed-hackers-to-snoop-on-conversations/
Always the first thing to switch off when you buy a new phone. Like once upon a time with Internet Explorer in Windows: download other browser and forget it. 🙂
@Bronco Sir I disable most google apps, specially Google Assistant on smartphones I use. I prefer to use simple search using a private search engine on firefox than wasting power of speech on these privacy invasive assistants.
Apple has recently released an Advanced Data Protection feature for iOS which expands end-to-end encryption for the company’s mobile devices. Despite the company having the encryption keys, if I was an Apple user I would advantage of this. Here is how to set it up:
https://appleinsider.com/inside/ios-16/tips/how-to-use-advanced-data-protection-apples-other-new-security-features
Sven Sir I use Nord VPN as my main VPN on PC and Android and Surfshark as my side VPN mostly as a browser addon, Adguard Adblocker Windows PC standalone application for advertisement blocking, NextDNS to handle my DNS queries to distribute trust and massively filter out tracking links and other unwanted things which makes up twenty five percent of all queries without breaking the websites and services, ESET Internet Security as security solution with its parental control filtering web traffic system wide for blocking all harmful and unwanted traffic, Dashlane Premium as password manager which also gives access to Hotspot Shield Premium, Firefox as browser on Windows PC and Android with some privacy add-ons for cookie protection and container based site isolation for big tech websites and services, StartPage, Duckduckgo and Google Search in isolated container with link conversion blocked as search engines, Evernote and Notesnook as note taking appplications, Mobi OfficeSuite as my office application which also supports Microsoft office files and also has PDF support including editing, Sygic Premium and Osmand Plus as navigation apps, and Asus Cloud Storage Premium only as Dump as I don’t use cloud storage enough and enjoy the moment rather that fiddling with camera settings to take videos and photos, Any.do as to do list application, and finally Session messenger as the secure messenger of choice. I use all paid apps from trusted developers on Android for security and privacy along with all the above applications which are paid wherever applicable. Also YouTube Premium to avoid advertisements. Also use some open source apps on PC like Calibre Book Reader. No private paid alternative for social media exists and I am very happy not using Social media which I find very toxic. I am part of good communities like Restore Privacy.
Only Email is the thing which I use from Outlook and Gmail with different accounts for different purposes like different ones for banking, services and subscriptions, google purchases as the main google account, formal work etc. Not easy to transfer email for all services and no true good and reliable alternative. Besides, security is a part of privacy and critical Google, Microsoft services like Google Play Store are vastly more secure, not the least supremely user friendly and pleasant to use and reliable. I am a student and young and don’t want to over spend on services like Proton mail and Tesorite or Mega.
Having a privacy on internet is not that difficult, just that one needs to move away from the freemium advertisement based model of internet and should pay for apps and services and make it clear to Government and companies that we do not want to be tracked. If don’t want to pay then option is to go open source, but then one should learn coding and contribute to the open source code as a part of community than expecting someone else to do it.
Sven Sir what do you think in what areas can I improve? I try to strike a balance between privacy and security and convenience? Without governments being made accountable and companies being questioned everything cannot be done on our own.
It’s always a balance, and it all comes down to personal preferences.
Wish you a very Happy New Year Sven Sir. May you always be very happy and healthy.
iOS users need not feel left out when it comes to iOS apps. Wikipedia has a list of some and many of the open-source apps for Android have iOS versions. Two other apps not on the Wikipedia list are for 2FA: they are Tofu and Raivo OTP (links below).
https://en.wikipedia.org/wiki/List_of_free_and_open-source_iOS_applications
https://www.tofuauth.com/
https://github.com/raivo-otp
Here is an even bigger list of iOS apps.
https://github.com/dkhamsing/open-source-ios-apps
“Passkeys are here to try to kill the password.”
https://arstechnica.com/gadgets/2022/12/rip-passwords-passkey-support-rolls-out-to-chrome-stable/
The organization behind Firefox browser, Mozilla, has published an excellent guide rating the privacy policies of products and services (like smartwatches and mobile apps). This can be a very handy tool for the holidays.
https://foundation.mozilla.org/en/privacynotincluded/
The UNCTAD Global Cyberlaw Tracker is the first ever global mapping of cyberlaws. It tracks the state of e-commerce legislation in the field of e-transactions, consumer protection, data protection/privacy and cybercrime adoption in the 194 UNCTAD member states. It indicates whether or not a given country has adopted legislation, or has a draft law pending adoption. In some instances where information about a country’s legislation adoption was not readily available, ‘no data’ is indicated.
[https://unctad.org/topic/ecommerce-and-digital-economy/ecommerce-law-reform/summary-adoption-e-commerce-legislation-worldwide]
Sven Sir, when it comes to antivirus Softwares based on my experience as well as experience of others, ESET and Emsisoft are the only Antivirus softwares I recommend.
I would have also recommend Kaspersky, it is a top tier product, but due to ongoing geopolitical situation, thought I might use it personally as allegations are not proven, but hesitate to recommend it wholeheartedly. But I certainly recommend ESET or Emsisoft.
Windows Defender is okish but there are many instances when it fails to protect against malware irrespective of what results from AV Comparatives and other testing labs say.
For highly risky work I recommend running Windows user account without administrative privileges and using virtual machine.
I don’t recommend Avast and AVG (both same) and Norton, Bullguard, Avira (All five consolidated), as well as Bitdefender, and McAfee primarily because they are nagwares and always disturb user through their sales practices and always try to upsell something and also because they are resource heavy, so not recommended. Otherwise protection wise they are not bad but rather good, but as I said they are resource heavy and themselves act like adwares.
There are few other good enough options too like Malwarebytes and F Secure.
There are some other half decent antivirus like Panda Dome, Trend Micro, K7 Security, Comodo, but I don’t recommend them as there are better options which offer better protection with less false positives.
Other popular options like 360 Total Security and few others whom I don’t want to name are bad and your security actually takes a hit when you install and use them over the already average and default Windows Defender.
.
What platform(s) and device(s) are you judging these AV by? Sounds like windows but you never clearly said, just hints to windows OS. Kaspersky was blackballed by the US state department probably about the time Putin had made office over there. Seems a long time now. But all state department computors where purged of Kaspersky for it’s founders KGB ties. I like it but in those day’s security suites were the fashionable norm. I like Emisisoft for windows but dislike the setup of the central console for home users.
Response to Tombfrye and other win OS box users…maintenance, privacy, backup.
Till Sept 4th,2022 you can get the O&O Power Pack of (O&O Defrag26Pro, DiskImage17Pro, SafeErase17Pro, and AutoBackup6Pro all full versions) for $30. on 1 PC and $39. on 5 PC’s.
Separately costing $129.80 on 1 PC or PPack $59. – Windows 11, 10, 8.1, 8 – – This is the newsletter link to the deal- https://shop.oo-software.com/36/purl-oopp2022
NOTE: ONE license key valid for up to 5-PC’s if you go the $9. more on the family buy. That is one license key each x’s 4 programs and your downloads good till 03/2023. I was looking at the O&O Defrag26Pro for 30. alone. I’ve used the earlier versions of SafeErase 17 Pro and find it helpful.
Clarifying I use both in platter and solid-state drives. The O&O programs for or with interactions of your drives can distinguish a type for the drive and respond appropriately executing the task. Most of my PC is on solid-sate drives, I have one platter for storage in the PC file system, my other 3 are contained storage books as sold w/USB for PC file access. Songs, movies, documents in such access.
Also a good cyber security hygiene is essential other than using a good antivirus. Never install and use cracked apps and softwares on PC and Android, otherwise neither a Virus Total Scan not an antivirus will help prevent possible infections and consequent heavy losses.
Again, prevention is the best cure, malware generally comes from advertisement heavy bad websites, specially adult website and similar such websites, through infected USB sticks, clicking on malware links in emails and SMS or chat applications or social media and redirects on browsers, and also compromised websites and programs on your system which otherwise have good reputation. Modern malware are very sophisticated and highly advance piece of software which takes lots of resources and time to develop and often state actors are involved. It is best to avoid them as sometimes they can Infect windows and Android devices so deeply that even a system reset won’t solve the problem as drives and motherboard firmware get infected.
Reminds me of The Halls of Karma – the presents of the two energies – the positive and the negative. Common sense rules!
Here’s some PRIVACY news you should not miss.
Americans Deserve More Than The Current American Data Privacy Protection Act
https://www.eff.org/deeplinks/2022/07/americans-deserve-more-current-american-data-privacy-protection-act
FTC Safeguards Rule Checklist: How Many Have You Done?
The December 2021 amendment to the GBLA Safeguards Rule has prompted organizations to take a range of actions, from simply making small tweaks to their infosec programs, to frantically building one from scratch. Regardless of where your organization falls on the scale, it’s helpful to have a definitive list of action items you can review to help ensure you’re in the clear by December 9th, 2022.
In December 2021, the FTC released “The Final Rule,” an amendment to the Safeguards Rule that encompasses a variety of changes, including an expansion of the FTC’s jurisdiction and specific requirements for executing an information security program.
The Safeguards Rule was relevant to organizations that the text of the rule defines as “financial institutions.” In the latest amendment, the FTC changed the definition of “financial institution” to include a host of new businesses. The Rule lists out who is now obligated to comply, including:
auto dealerships,
mortgage brokers,
tax preparers,
payday lenders,
collection agencies,
non-federally insured credit unions,
“finders,”
and any other business that significantly participates in financial activities, or affects people’s ability to access financial products or financial services.
The purpose of making these changes to the FTC Safeguards Rule is to maintain protection of customer data in a world with increasingly sophisticated cyber attacks. The original Safeguards Rule was released in 2003—since then, advancements in tech and public comment have persuaded the FTC to mandate appropriate safeguards for the year 2022.
The Safeguards Rule (known fully as “Standards for Safeguarding Customer Information”) is one of three major guidelines that comprise the Federal Trade Commissions’s Gramm-Leach-Bliley Act (GBLA). It mandates organizations defined as “financial institutions” to implement safeguards that prepare and protect customer data from breaches and security incidents. Customer data in this case is defined as any nonpublic personal information a customer gives to an organization.
In December 2021, the FTC released “The Final Rule,” an amendment to the Safeguards Rule that encompasses a variety of changes, including an expansion of the FTC’s jurisdiction and specific requirements for executing an information security program.
The Final Rule also lists out reasonable steps that a financial institution’s information security program can take to build out digital and physical safeguards for data. We’ve simplified them, and assembled them here in a checklist for you.
https://www.virtru.com/blog/ftc-safeguards-rule-checklist-how-many-have-you-done
So we have a view to consumer privacy of the national as well states growing efforts coming abreast to the electronic data age finally as acts and rules to maybe lead in laws following with teeth of the medium where business(es) move in modern commence reaching more people nationally than yesteryears.
For those of you who have ever wondered which products and services protect their privacy, Mozilla has published a guide. I was pleasantly surprised about that some Android smart watches and ear buds even get thumbs up.
https://foundation.mozilla.org/en/privacynotincluded/
Hard core privacy facts usually will be found in an offerings Terms of Service and their Privacy Policy pages as all businesses need to include these facts…translating the legalese will need a deep understanding. Mostly found in the PP pages, if you are see 50 ways your information is shared to the east, west, up and down directions all before noon I’d say pass on it.
A strong incentive pf privacy is when primary business states and business that they need to run their own business will adhere and live up to there own privacy terms purposed as sold to you.
This guide and like are good only to weed-out the field and narrow the choices for short listing.
corrected-
if you are to see 50 ways your information…
A strong incentive of privacy is when a primary business states any business…
For Windows users concerned about their privacy, the best way to enhance privacy protections on a Windows-based computer is to replace the operating system with a Linux distro such as Fedora or Ubuntu. If doing that is not doable now, then I suggest downloading Safing. It is a free and open source portmaster that enables a Windows user to manage and restrict network activity.
https://safing.io/portmaster/
Abandon ship not so good? Invested in – so look into all the following.
Yes more in an investment but better than trying to sq. peg a round hole.
Especially if Windows is required for work needs…
https://www.getblackbird.net/documentation/
https://www.sphinx-soft.com/Vista/index.html
https://www.emsisoft.com/en/why-emsisoft/
https://adguard.com/en/adguard-windows/overview.html
https://www.r-wipe.com/
https://privazer.com/en/
https://www.revouninstaller.com/
A good password manager and a good disk cleaner offering defrag and you are set.
Seems we are all on the same Privacy River – just can’t see well of clear sight the path for all the bends it transverses.
Defragging a ssd is generally not a good idea for it’s life. Old style platter drives are in need of drefrag though.
Tombfrye maintenance is still required.
Your right in a sense of old, but this problem doesn’t just apply to hard disks but to SSDs as well. Over the course of time SSDs save file fragments over more memory cells than are necessary. This in turn, leads to a continuous slowing down of the read and write processes, just as we experience on hard disks. The SSD controller tries to counter this phenomenon on a rudimentary level but is unable to do so on account of its not having an overall view of the data structure.
Invalid data can quickly build up on an SSD. Solid-state drives can’t delete entire blocks of data when some of the data within a block is still valid, leaving behind invalid data and forcing the drive to go through the process of moving and deleting data when space is required.
To make matters worse, solid-state drives cannot write data over existing data, having to delete the existing data before performing the new write. These issues can make writing new data take more time, reducing the write performance of the SSD more and more as time goes by.
TRIM is a command that can be issued to an SSD, forcing it to go through the process of cleaning blocks to remove invalid data. This can improve the performance of your solid-state drive by taking care of this work while it would otherwise be idle rather than during a data write. Your SSD maker usually offers their own TRIM program too.
But if you run mixed drives or just want the SSD done automatically try this.
https://www.oo-software.com/en/products/oodefrag
O&O Defrag “Install & That’s All”: After installation, no further settings need to be configured. The program selects and implements the defragmentation method best suited to the system. By combining the snippets of a file and writing them one after the other to the hard drive or SSD. In addition, the files are reorganized so that the access times when loading are minimized. This saves you time and protects your data volumes. If you use O&O Defrag regularly, the access speed and the overall performance of your Windows system will increase noticeably. And so that you never have to worry about “file snippets” again, O&O Defrag can also be run completely automatically in the background.
Hi Mick,
Thanks a lot for your advice. I will have a look at portmaster.
Does a vpn block the total surveillance with windows, ios? or at least help with this?
Yes it is a tool that will help to hide your IP address and encrypt traffic, but when it comes to Windows telemetry and privacy issues, a VPN will not fix these issues. See our guide on Windows privacy here.
Sven that link only points to the VPN working for Windows OS in 2022.
Ron should have a look at – https://www.getblackbird.net/documentation/ and https://www.sphinx-soft.com/Vista/index.html
For telemetry blocking purposes.
Here Sven is the link Ron maybe should have got
https://restoreprivacy.com/windows-privacy/
Ron I see all comments left there.
Thanks JMO, you are correct. I just updated that link above.
With all of the concerns people have about Firefox’s low and shrinking user base, there is one thing Mozilla is doing that could help revive interest in the browser. About seven years ago, Mozilla tried to introduce FirefoxOS to compete with Android and iOS. Needless to say, it went nowhere and the group ended up officially sacking the project in 2017.
However, a software company forked FirefoxOS to develop their own operating system for smartphones called KaiOS and recently Mozilla agreed to help develop and support it. KaiOS is now the 3rd largest smartphone operating system in use.
https://www.kaiostech.com/kaios-technologies-and-mozilla-partner-to-enable-a-healthy-mobile-internet-for-everyone/
June 30, 2022 – https://crsreports.congress.gov/product/pdf/LSB/LSB10776
On June 21, 2022, the House Energy and Commerce Committee introduced the American Data Privacy
and Protection Act (ADPPA), H.R. 8152, which would create a comprehensive federal consumer privacy
framework.
There is a way to make payments by credit card online anonymously. Pay With Privacy creates virtual credit cards for one time or limited transactions directly from your browser. They have apps available for iOS and Android.
https://privacy.com/
Only available with a US address, I believe
Have you had the feeling since the lockdown that things are changing fast and some morphing for the worst as that you could ever remember in your history? The US financial outlook has already started resembling the tough times of the 1980’s, we (adults’ living then) can remember. Our leaders here seem about as lost now as back then. This was meant to be about privacy the world over as we adapt to the digital medium and it’s data generated. So let’s go!
First I’ve seen SEYCHELLES mentioned around here and Ctemplar referenced it as the business HQ for the privacy to their business and personal data knowledge required of customers.
SEYCHELLES
The Data Protection Act (the ‘Act’) was enacted in 2003 (Act No. 9 of 2003) with the aim of protecting the fundamental privacy rights of individuals against the use of data concerning them without their informed consent. The Act will come into operation on such date as the Minister notifies in the official Gazette.
As of January 2020, the Act has not yet come into operation.
Say compared to FINLAND
The General Data Protection Regulation (Regulation (EU) 2016/679) (GDPR) is a European Union law which entered into force in 2016 and, following a two-year transition period, became directly applicable law in all Member States of the European Union on May 25, 2018, without requiring implementation by the EU Member States through national law.
A ‘Regulation’ (unlike the Directive which it replaced) is directly applicable and has consistent effect in all Member States. However, there remain more than 50 areas covered by GDPR where Member States are permitted to legislate differently in their own domestic data protection laws, and there continues to be room for different interpretation and enforcement practices among the Member States.
Territorial Scope
Primarily, the application of the GDPR turns on whether an organization is established in the EU. An ‘establishment’ may take a wide variety of forms, and is not necessarily a legal entity registered in an EU Member State.
However, the GDPR also has extra-territorial effect. An organization that it is not established within the EU will still be subject to the GDPR if it processes personal data of data subjects who are in the Union where the processing activities are related “to the offering of goods or services” (Article 3(2)(a)) (no payment is required) to such data subjects in the EU or “the monitoring of their behavior” (Article 3(2)(b)) as far as their behavior takes place within the EU.
Look up Privacy Facts here:
[https://www.dlapiperdataprotection.com/index.html?c2=FI&c=SC&t=law]
[https://www.privacypolicies.com/blog/privacy-law-by-country/]
[https://www.privacypolicies.com/blog/privacy-law-by-country/]
The UNCTAD Global Cyberlaw Tracker is the first ever global mapping of cyberlaws. It tracks the state of e-commerce legislation in the field of e-transactions, consumer protection, data protection/privacy and cybercrime adoption in the 194 UNCTAD member states. It indicates whether or not a given country has adopted legislation, or has a draft law pending adoption. In some instances where information about a country’s legislation adoption was not readily available, ‘no data’ is indicated.
[https://unctad.org/topic/ecommerce-and-digital-economy/ecommerce-law-reform/summary-adoption-e-commerce-legislation-worldwide]
Dup – was to be
https://unctad.org/topic/ecommerce-and-digital-economy/ecommerce-law-reform/summary-adoption-e-commerce-legislation-worldwide
If someone is at risk for targeted attacks, Google’s Advanced Protection Program might be a good option to consider. There are services one can buy to achieve the same result as Google’s GAPP, but they are offering theirs for free. YMMV (Your Mileage May Vary).
https://www.howtogeek.com/404450/what-is-google-advanced-protection-and-who-should-use-it/
But which phone OS should one choose for best privacy? iOS or Android? Using custom ROMs is out of the question since it breaks a lot of basic functionality on the phone, like the ability to use banking apps, 2FA apps etc.
Also I see you recommend Ubuntu. It also has built-in telemetry, but it’s easy to remove.
You won’t like it, but there is no phone platform best for privacy.
With Android makers there are some who allow the bootloader unlock and then root with a recovery. This was working with banking and pay apps not so long ago with a newer root method.
Apple has always discouraged purchasers from messing under the hood so to say.
From cells there are no privacy achievements really. Your tracked, listened too, watched and your data processed. Much easier than on a pc I’d say.
@Svenny as to alternate OS’s, for Android the two best ones are Calyx and Graphene. iOS is a tougher nut to crack but it can still be done. There are some Linux distros that can replace iOS and some even look like it too such as Elementary, Trenta, and Zorin.
If you have iOS, be aware replacing the OS on your device may invalidate any Apple warranties. Same may also apply if you do the same on an Android device.
That root method I couldn’t remember what it was named.
Magisk: If you want to root without tripping SafetyNet, your best option is Magisk. Not only does the popular mod give you systemless root, but it also provides a framework that lets you install modules and perform system-level mods.
List of Phones with Unlockable Bootloaders -updated 3/5/2020
[https://android.gadgethacks.com/how-to/list-phones-with-unlockable-bootloaders-0179751/]
Updated 2/5/2020 Best phones for Rooting & Modding
[https://android.gadgethacks.com/how-to/best-phones-for-rooting-modding-2020-0175988/]
Once there was offered the Black Phone, it has adapted to this now.
The Silent Phone app provides enterprise-grade end-to-end secure voice, video, conference calling, and messaging. No additional hardware is required.
[https://www.silentcircle.com/looking-for-blackphone/]
&
[https://www.silentcircle.com/looking-for-blackphone/]
I have come to understand that Google has been enhancing security measures for Android and, as a result, the majority of hack attacks are conducted against iOS devices. This as opposed to before where it used to be the other way around. So for all of Google’s ridiculous spying on their users, the most secure device to have right now is Android.
Best of all, you can keep an Android phone longer than an Apple iPhone as there are ways to get OS and security updates even after the period guaranteed by Google has expired. You can also change your Android phone’s operating system down the line and it is easier to do on an Android than an Apple device.
This is from Dec/2018 which seemed long ago already. What progress has this made to mainstream web surfing of today? Most of it sounded promising back then, but adoption lacks possibly in the mainstream server’s network. Source [https://sasha35625.medium.com/what-is-web3-7fabbaa3eabf]
Have you ever thought about where the immense wealth of Internet giants such as Google or Facebook comes from? In pre-Internet times such wealth used to be accumulated through an access to some resource and its exploitation. It could be natural resources such as oil and gas or gold, manpower and automation in manufacturing and so on.
So what resource do web giants exploit? This is the data they collect. This is the gold of the 21th century. The gold which smart people started extracting without asking any permission from anybody. The gold which is basically taken from YOU.
Web 2.0 came after the original Web 1, a collection of static documents, hardly monetizable. Web 2.0 is the Internet of corporations and monopoly, which comes straight from the early stages of industrial revolution where huge corporations could control everything. This is the Internet of making as much money as possible and making use of as much data as possible. Due to being overly centralized it is vulnerable, manipulative, and prone to manipulation.
Do we need a world where the data you own and produce can be turned against you because of greed or pure malice? It’s not even about your privacy, it’s about control. We hand control over the vast amounts of precious data over to companies and individuals who just happened to be at the right place at the right time. That sounds scary and irresponsible.
So what is the alternative? We need some technical solution here, besides our desire to make things right. And we can see the shape that this solution could take now.
Web3 concept was proposed at the end of the last century, with the major focus on so-called Semantic Web (the web where computers and humans basically have some common language somewhere between natural human language and computer code). But already then the idea of accountability, and distribution of control was proposed. Basically Web3 is the architecture which can’t exist without decentralization of control.
Only with emergence of blockchain the whole puzzle of Web3 came together. Blockchain is a paradigm shift that allows us to create systems which run “on their own”, by the protocol agreed before their launch. We can construct decentralized systems which can become that layer on which you don’t have to give up on control over your data, where all your data belongs to you.
Web3 products are just emerging. But it’s clear what the will and won’t do. You will be able to explicitly allow access to your data. You won’t need to trust third parties with storing your passwords. You won’t let anybody erase your data either. Governments will finally understand that you can’t solve all the problems by just banning things, you need to dig deeper and fight the root of the problem.
Web3:
Will let you control your data.
Will be essentially decentralized.
Will still be monetizable; but the monetization will be more transparent.
Should (and hopefully will) be essentially unbreakable.
Will be a consortium of different technologies merged through blockchain (or other decentralized tech, should it emerge)
Web3 goes beyond Internet. This is a new paradigm of connected technologies (IoT, Big Data, Artificial Intelligence) which run on a decentralized layer, which brings them together and give them new synergistic meaning. It goes from technology to the structure of society, shaping and improving it.
Sill we have Web2.0, this is the Internet that we have now, with all those features that seem so nice but are meant to collect and control as much of your data as possible. They are bells and whistles that turn out to be the hammer and the anvil that makes it so monetizable. From the past web versions to the present we still get an internet prone to manipulation in exploitations of human data. But as claimed, Will still be monetizable; but the monetization will be more transparent with web3.0. When can we put a stop to a mapping of societies data with the main purpose being used for control of your data. How big a step is it from controlling your data to the forcible control of a the person?
This is a RECONSTRUCT of the link and credit to the author, though I did add to some parts in the ideals presented then.
Lelow, I think I recognize your prose. Could it be you? If so, welcome.
https://www.youtube.com/watch?v=ec0XKhAHR5I
I like your thinking son
https://m.youtube.com/watch?v=clsBpAoWIC0
They say love hurts, so why is it’s attraction so great to us. Why then, is the Internet a great attraction to us as well.
Are we all MARTYRS?
There is no privacy until we have laws granting us such rights of the new mode as being connected electronicly today for living a pursuit of our own happiness in life…
Cheers 🍻
Wayward, wished people could understand its human privacy as well of our controlling the data we generated, in fight against the internet machine.
https://m.youtube.com/watch?v=AOqbhIulC3g
That be the connected machines we own, or use to jump on the many server conveyors belt to pull up a screen of our particular needs and/or interests.
Just remember back when cookies went to super/Zombie cookies, web bugs and beacons all were the tracking standards. Then came the slew of counter privacy fingerprinting methods that led to the profiling. First in our device’s as it advanced and then to our own person being profiled.
A shaped time stamped experience that where any fixed or mobile devices all being set to tie back to one in the same person/family.
Beyond fingerprinting then I’d suggest we’re highly exploited from the webs servers moment of use. Controled by only a few that think they know where we want to go and what we may know.
In the US as well maybe the world over the internet would be better human serving if it was controlled and governed more as an utility. Possibly some rotation of IP addresses from suppliers of Internet (ISP), where their whole served IP’s are jumbled together making all white noise to profiling and tracking of their customers IPs.
US freedom of the web means to Outlaw all types of device fingerprinting and put an end to our personal data profiling. Only like a warrent would expose only 6-months of kept data. Then it’s deleted no record carries forward.
Rant be done✔️
In short, the message being conveyed is: “Don’t use it. It’s Russian.” Instead of issuing yellow stars will red ones be issued?
[https://www.bleepingcomputer.com/news/security/german-government-advises-against-using-kaspersky-antivirus/]
US state department said more-less the same vive about this Kaspersky co. but that was some years ago. Interesting of then I had understood the KIS founder and Puttin both have KGB ties.
Tell me Mike when you see a flower do you notice the shape it has first or it’s color first?
These labels in color to people you make are rude and uncalled for, a field has many flowering kinds it can hold. Just as countries do with people kinds though, – we may draw a line isolating a country but still we are caring enough about it’s upright people sucked in to the turmoil. Quarantine till resolve as an answer. Not by labeling people with color.
I see something here that many are dumb too, your have a governing body with it’s military of a country and then it’s people, but it doesn’t stop there. Like the US other countries have their Black Opps departments running in the background shadows. Stealthily bodies unknown acting in gray zones of any laws or whole known authority. Now consider the three letter agencies the US has and then each branch of it’s military may utilize as well as fund individual contained black opps programs.
So like here in the US it’s not just the national power is shared between the national government and a state governments to govern it’s people. Covert divisions operate within a national authority supposedly to protect what/who? Definitely not what kind of powers the federal government should have and how those powers can be exercised, as have been debated ever since the adoption of the Constitution. So when did Black OPPs of the US have any merit of validity rendered in some constitutional interpretation by the courts?
One of the theoretical pillars of safeguard in the U.S. Constitution is the idea of “checks and balances” among the powers and responsibilities of the three branches of American government: the executive, the legislative, and the judiciary. Black OPP’s are not a constitutional right but wrong stealth fractions outlaws.
How can you think there is any privacy for anyone to gain if you can’t know who to defend from?
Black OPP’s are war like fractions – US hunger would cost less to cure than all Black OPP’s yearly budgets.
“[A]rtificial intelligence (AI) can help in a way that both satisfies data privacy advocates and makes ecommerce more efficient.”
https://venturebeat.com/2022/06/01/the-role-of-ai-in-data-privacy/
Hi Mike who says they (the people) over AI may have any right still to my personal data-
exactly to pull out what if any information from our shopping and browsing histories of a site.
I assure you it’s 1st and foremost for their own company profits. Though AI leads to every visitor having a personalized view of that one website’s products as is claimed. Data that who now rightfully owns? It’s still happens to be our own user’s trapped data about us, (should it venture us profits if it’s being trapped), after all it’s data that leads back to us.
Keeping a site’s user profile for any type of discounts – sounds as if it’s time has come of age….
Yet we’re not given a say in this – why? If we’d boycotted the site (and enough of us) made it clear would that make any change happen in the average Joe’s online life to data surrender?
Hitting a website as a generic unknown is preferred by most anyone new browsing a site. Patronizing it again, then one should expect to surrender more in their own sensitive personal information. How dare them to use my data for other than their history and a journal of my purchases (actions) there.
When a wave hits crashing on the beach it’s beautiful as it’s travels are over, the momentum it sustained comes to end crashing at lands edge. Data I see the same effect for it to (crashes) when the initial momentum cause should end – – data dissolved and not allowed to abstract into something powerful over us.
Mike let me take you back to the server side comment you made as that needed to be addressed for better protections in one’s privacy and system. Servers should be encrypted always I think.
Posted Apr/2021
The FBI has been making the case for years that encryption benefits criminals far more than it benefits non-criminals.
EDITED:
Last year, authorities managed to push a malicious update from _ _ _ server down to individual _ _ _ devices, according to other law enforcement documents obtained. The malware could harvest the phone’s GPS location, stored messages, passwords, and more information.
Read the whole thing here – [https://www.techdirt.com/2021/04/02/new-info-about-encrypted-messaging-service-bust-shows-signal-protocol-is-still-secure-law-enforcement-can-still-bypass/]
(Shooting fish in a barrow)
I’m not picking on you, I feel that you may correct me or enlighten me all the same.
By Mike; Your ISP and cable or broadband internet provider is probably logging all of your online activity too. No doubt a letter requesting it from the FBI or police would be quickly given to them by your internet provider or even sold to advertising companies. You know all of those computerized vehicles coming out with those neat gadgets? Well, no doubt they’re monitoring and even benefiting from your personal information too.
True mostly but, the people in the US had strong measures in place working for stronger privacy protections of the FCC. Till the Trump election win changed all that world of your ISP NOT spying on you and selling your information. WHAT arguments for less privacy was the domino affect that collapsed what privacy the US citizen did had?
The argument was it was hurting the research and investments of the phone and cable providers [PROFITS] as Google, Microsoft and titans in industries all over the US were not limited to the troves of information users give those companies.
[We had our foot at the door that had a chain slide lock – our profile was small]
Police and the FBI have always had court set procedures that must be adhered too. Inotherwords Laws in place to prove a real need or cause to gain access of your electronic data. But terrorism has most likely put a gapping hole there.
This is where the people who are running up the PRIVACY Flag rallying the people – forget about the subject nor seem to care in addressing it. WHY? because directly or indirectly PRIVACY is Big money to them. Get more people talking of the subject Privacy and push their links or apps that build a residual income fortress for themselves in years to come.
While Good people shell over their greenbacks and get in return – as is, no intended purpose, use at your own risk, nothing is 100% digital safe.
I’m not talking about a president’s service just something that happens every 4 years with the next up to serve in the roll.
That is by all means what follows:
The FCC is directed by five commissioners appointed by the president of the United States and confirmed by the United States Senate for five-year terms, except when filling an unexpired term. The U.S. president designates one of the commissioners to serve as chairman. No more than three commissioners may be members of the same political party. None of them may have a financial interest in any FCC-related business.
The Federal Communications Commission (FCC) is an independent agency of the United States federal government that regulates communications by radio, television, wire, satellite, and cable across the United States. The FCC maintains jurisdiction over the areas of broadband access, fair competition, radio frequency use, media responsibility, public safety, and homeland security. [https://en.wikipedia.org/wiki/Federal_Communications_Commission]
By Mike again; There is one vital point that needs to be made that doesn’t get addressed here and on other privacy sites. You can take as many precautions as you want (like use a privacy browser or VPN), but in order to achieve full online privacy the server-side needs to be addressed.
I’d say it’s lots more than a server/side involvement – – like the people we elect into office and the people they assign to head duty rolls. True as of today anything you hold and use online is trapping your data in some form. Many have a profile(s) on you and your electronic actions to harvest the most gain overtime of your income potential yet to steel your data gold.
Not helping man but a leaching of his personality to the shaping the electronic landscape they witness.
I say enough of the dog eat dog world of the advertisement titans – I want a world where everyman counts!!!
One man one vote
“The company’s stab at the biometrics checkout market has raised debate about data storage and tracking.”
https://www.theguardian.com/technology/2022/may/17/mastercard-launches-smile-to-pay-amid-privacy-concerns
Steven, I’d like to suggest that you test and review drive wiping software such a CCleaner and PrivaZer and others on a Windows machine. To test it out, you could wipe a drive and then run the same forensic software that the NSC would use to see if these wiping apps really do get rid of all you browsing history, thumbnails and sensitive files.
What do you think?
Hi Mega1
You may find this article of interest:
https://www.techradar.com/reviews/piriform-ccleaner
I don’t believe CCleaner would get a pass mark for privacy:
“Some users may find it useful to note that CCleaner runs constantly on the background of your computer and reports anonymous user data to its developers. While this is a mostly harmless feature and no sensitive information is shared, you may just want to be extra careful about installing this piece of software.”
“… the free version includes very intrusive pop-up ads that one might find it difficult to work with.”
I personally haven’t seen or been bothered by these mentioned ads, maybe because of my add blockers.
My view is that CCleaner can be useful for a person who needs the services CCleaner provides.
Myself, I periodically (not often) download and run it to see what it finds.
I do that for a couple of days then then uninstall it.
On the whole, before I started learning CCleaner was a very important tool for me, now it is less unneccessary.
For Windows users the >’netstat’ command can be handy.
(It shows the connections your devise is making to remote servers. Boy!)
It was interesting for me to run ‘netstat’ then clean with CCleaner then run ‘netstat,’
You have the tools, maybe do some testing..?
(If you have an add blocker the change won’t be as dramatic)
So you need to decide if CCleaner is a good tool for you
Maybe you should test for yourself?
BeBeX
I wouldn’t trust CCleaner though it’s been around forever. Who owns it now – they lost me going so commercial way back with everyone pushing them.
PrivaZer the donors version is okay I’ve set it for weekly PC drive cleaning and use the interface to clean manually the browser traces when I close one.
Here’s one that is old and still going
R-Wipe & Clean. R-Wipe & Clean is a complete R-Tools solution to remove useless files, free up your disk space, and clean various privacy-compromising information on your online and offline activity. This includes internet history and cookies, lists of downloaded files and opened documents, various data caches, temporary files, and many more .
You check mark items individually, by sub-groups or whole groups of what gets cleaned and can set many different runs of combinations when there cleaned.
Windows OS has a recovery feature and I believe this makes deep cleaning from shut down to shut down extremely difficult to be a bawd swath cleaning. R-Wipe & Clean allows you to know what you’ve set per run that is cleaned. Others don’t go half as far or offer as much that is set to be cleaned.
The statement, “If something sounds too good to be true, it is” comes to mind.
Such is the case here: [https://www.unspyable.com]
Or is seems. I cannot put my finger on it but something reads…off.
Maybe I am wrong and if so, please correct me. But parts of this system looks good and others…not so much.
Any opinions would be good. Thanks.
Disroot is a very interesting operation. They’re based in Amsterdam, Netherlands and are a privacy-focused, all volunteer outfit. Their products are all free the ability of users to being send OpenPGP encrypted emails through their web-based email service (they have an app on F-Droid), choose Disroot’s client or Mozilla’s Thunderbird for desktop emails, have decentralized chat thanks to their partnership with Matrix, and they even support custom domains.
https://disroot.org/en
However, because they’re all volunteer and funded by donations, Disroot may lag in terms of updates. This European website has done a comprehensive review:
https://proprivacy.com/email/review/disroot
There is one vital point that needs to be made that doesn’t get addressed here and on other privacy sites. You can take as many precautions as you want (like use a privacy browser or VPN), but in order to achieve full online privacy the server-side needs to be addressed. For privacy advocates, this is a very bad problem.
Your ISP and cable or broadband internet provider is probably logging all of your online activity too. No doubt a letter requesting it from the FBI or police would be quickly given to them by your internet provider or even sold to advertising companies. You know all of those computerized vehicles coming out with those neat gadgets? Well, no doubt they’re monitoring and even benefiting from your personal information too.
During 2019, Maine enacted an ISP privacy statute that is presently the subject of court challenges. So far, it has been upheld. It could be a model for other laws, but, until other states enact them, you’re information is still available to them.
https://www.cnet.com/tech/tech-industry/maine-governor-signs-internet-privacy-protection-bill/
So, congratulations on following the advice on websites like this. But know that, until you can have the ability to opt-out of the surveillance mentioned above, just try to keep a low profile and pull out of as many services that benefit from your data as you can.
Someone on this page asked if a VPN can bypass a firewall. This article does a good job explaining the difference between a Firewall and a VPN and if bypassing a firewall with a VPN can be done.
https://cyberwaters.com/can-vpn-bypass-firewall/
In short, the message being conveyed is: “Don’t use it. It’s Russian.” Instead of issuing yellow stars will red ones be issued?
https://www.bleepingcomputer.com/news/security/german-government-advises-against-using-kaspersky-antivirus/
“A small team of researchers at the Darmstadt University in Germany have published a report illustrating how their AirGuard app for Android provides better protection from stealthy AirTag stalking than other apps.”
https://www.bleepingcomputer.com/news/security/free-android-app-lets-users-detect-apple-airtag-tracking/
Look up Snowden ExpressVPN for details about why I don’t believe it belongs on the list
MullVadd has a good reputation for respecting user privacy
Tor browser should hands down be #1 in regards to privacy, by a long shot
QubesOS and Whonix are both great operating systems
Here are some different opinions on using Tor browser alone.
Blokada is now on ios also. I can’t get Lockdown to work at the same time as my vpn. How do I use both at the same time? or is it not possible?
@rufnhappy I am unsure as I am not an Apple user. I would assume you can only use one and not both at the same time.
Hi Guys, above Sven says for ad blocking he likes Nord with CyberSec, so my question? Is anything gained running adguard while connected via Nord w CybSc. =regards single PC -ethernet connection
Yes, I would guess that AdGuard has a more robust filter lists than the CyberSec feature from NordVPN. Therefore AdGuard may block more stuff, but it may also slow things down a bit, whereas CyberSec won’t do that.
While Apple has taken a public stand on privacy, curtailing data and app abuses declaring it doesn’t profit from its users’ information, the company has also created comprehensive new ways to track us.
https://www.wired.co.uk/article/apple-surveillance-technology
Privacy is a fundamental human right. Prominently included in the Universal DECLARATION of said Human Rights and also the International Covenant on Civil and Political Rights. Alas, privacy is (and likely always will be) an absolute mythical f’n unicorn/white-buffalo hybrid.
My dismay has grown, year after year as the complacent masses give zero Fs. But, as you all well know, turns out that two de facto titans of the realm were at worst, machinations of the “enemy” all along. At best, they were ultimately proven to be complete failures at their stated purpose.
As privacy pundits have long echoed is response to the (seemingly fizzled) FBIs faux-war on encryption, “if there are forced zero-days included in encrypted tools, then they would cease to be encryption at all.” Period. End of story.
— BTW, I say “faux-war” because it was mostly ‘smoke and mirrors’ all along, really. They don’t NEED mandated backdoors, they just kinda would like to have them. —
Signal App:
I once really admired straight man, B. Acton and his funky, rebel-with-a-cause crypto partner. You know the one? The caricature of self-serving bravado that calls himself, “Moxie Marlinspike”….probably in the 3rd-person but to be fair, I’m just guessing on that. 😉
But I’ll try and stick to respective functionality of the tools, themselves….l est I go off on a tangent and wax malevolent in ad-hominems.
Long the darling of the privacy advocates , Signal have been at the forefront and seemingly excel where it matters most in spite of myriad shortcomings. I, for one, truly believed they were going to be an Institution in this winnable war.. Turns out, that was almost surely BS. I don’t think that we can hang on to “not great but, best we’ve got at the moment” logic anymore, do you? I’m not using them.
Aside from the obvious and very serious implications surfacing as of late, the entire project itself has long suffered from lack of transperancy, extremely poor comms/interaction with users and a a questionable roadmap while ignoreing glaring faults.
Yeah, it’s probably…….nay, it is *MAYBE* better than SMS and voice data just floating around unencrypted. But settling is growing thing for me. I always gave Signal Foundation the benefit of the doubt assuming they were obviously one the good guys and things just take time. They’re “working on it”, I’m sure. Maybe we just need to hit that “Donation” button more so theat they can hire more staff. (fyi: we didn’t/don’t need to do that, btw….they are FLUSH with cash).
I uninstalled Signal for good and now I feel naked. Now what? Session, XMPP, Syphon? Certainly not Telegram! ugh
Tor Browser/Onion:
Always lauded as the slow moving – but invisible – tank of internet anonymity. Many moons ago, when a buddy in college first told me that he bought his weed online and it delivered via USPS, I was in utter disbelief. But he sure did. For a fairly long time, the Onion Router seemed to be exactly what it was supposed to be: a truly anonymous gateway to web only foiled in the case of user error.
Now obviously, it goes without saying that Nation States will always work to combat any such obfuscation. But what vexes me most in this unfortunate saga is that they succeeded in such grand fashion against Tor Project and with such little clamor, to boot. It’s going on a decade now (IIRC) since the first fed court documents plainly stated that a convicted criminal had been de-anonymized using Tor.
I don’t particularly give a damn about the dark web nor do I frequent .onions nor use Tor Browser, itself beyond occasional tinkering. But upon hearing it had been broken, I found this to be incredibly noteworthy. Tor Project was synonymous with “anonymity” and I assumed this would be a very big deal.
Using good ol’ fashioned logic, I immediately considered Tor Project to be broken and likely, nearly dead. Who wouldn’t? Welp, most as it turns out. Tor dev soldiered on with what had become their mantra, “Will not fix”, for years. with almost nary a fuss from almost anyone.
Only in the the past year (and for some reason, REALLY ramping up this past December) have I begun to see scattered reports on ‘KAX17’ and the widespread, very-much known about and very long-standing issue with malicious nodes being used by “SOMEBODY”.
(Gee, I wonder who it could be?!? /s)
Tor brass ultimately removed all traces ot the word “anonymity” from their marketing and documentation. The very MISSION of the entire damn project, itself….or was it?
I’m going to stop short of a full-blown rant (too late, amitire!) assuming we all know the gist of these two unfortunate events. I just wanted to say that for me personally, my confidence in privacy is at an all-time low. Like surely many of you here, I’ve long a stalwart of among a veritable sea of complacent, clueless, ‘don’t-give-a-damn’ lemmings out there. You know, somebody who religiously updated about:config prefs (let alone, knew they existed). Somebody who knew better than to trust the likes of the laughably layman-lauded Ghostery. Someone who knew better than to think Google’s “incognito” meant a damn thing, really. Somebody who had cautious optimism and believed in the cause.
However lately, I find that I, myself am giving in/up on increasing levels of IDGAFedness. If you can’t beat em…..
Maybe I’ll just buy a couple privacy nightmare smart watches and even use some Gapps and why not?…Samsung hardware, while we’re at it. Oooh, Knox….that just SOUDS secure. Find My Mobile? Bluethooth headphones? Safe Browsing? Diagnostics uploads? Seems legit.
I’m finally sick of swimming against the stream….and for what? There are like, I dunno…15? 20 of us out here who care enough to even actually fight the growing monolith of surveillance culture/”marketing”?
What say you, friends? I don’t even do social media…never had a Facebook. I’ve always wondered what the other half (99.9%) lived like with their Instagrams, their OnStar, their Near Field Comm payment methods, their Samsung Photo Gallery automatically creating “stories” for them based on the pictures they take (gross!). Google Drive? What’s that LIKE? Google Docs? What even IS that? Windows that makes 500+ calls home per day…LOLFIREWALL, be damned?
Sorry, I’ve just about had it here, man. Am I alone? Go read the Play Store reviews for literally EVERY GApp/G suite…whatever. Hilarity will ensue. From Google Health to the newly forced, Intelligence Service, 100% of clueless apes are in full, faux-outrage mode. “Where did this app come from?” and “I’m so sick of Google!” and my personal favorite, “Suddenly battery life is suffering and I can’t get CCleaner to work properly anymore!”
Until we far surpass ~1%-3 of us caring enough to actually take action against our enemy overlords at Google, FB, Adobe, LexisNexis, Deutshe Telekom, Oath, etc and STOP F’n USING THEIR “free” products, we’re jogging in place at BEST.
I mean, Zuck could stop pretending to care at all and change their slogan to “F all you Sheeple..all your hopes and dreams are belong to US!”….he could stop bothering with blatantly lying to dog and pony congress….he could literally walk around spitting in people’s faces and I’m certain that STILL, pretty much nobody would leave their precious FB/Metaverse accounts. And complaing about it the whole way.
////rrrraaaannnntttt
Forgive me, my typos…they know no what they say….as it were, I hunt ‘n pecked that diatribe via mobile.
Can’t be using proprietary SWYPE nor AutoCorrect. Much less, a mobile keyboard with full friggin’ network access (all of em but two last I checked)! Simple Keyboard or nothin’.
TBH, “Nothin” is growing on me. But manics gon’ manic.
¯\_(ツ)_/¯
Awesome Rant.
I started in computers/ networks in 1984.
Who would have thought the whole world would be ok with Goatse level privacy and security.
But its FREE. Ya so is prison sex, but not for me thanks.
McDonalds continues to sell the most burgers….
Outer Limits was right (their intro).
Hi Brad,
Somethings that may address your inquiries:
Facebook Pixel:
https://developers.facebook.com/docs/facebook-pixel/get-started
“The Facebook pixel is a snippet of JavaScript code that loads a small library of functions you can use to track Facebook ad-driven visitor activity on your website. It relies on Facebook cookies, which enable us to match your website visitors to their respective Facebook User accounts. Once matched, we can tally their actions in the Facebook Ads Manager so you can use the data to analyze your website’s conversion flows and optimize your ad campaigns.
By default, the pixel will track URLs visited, domains visited, and the devices your visitors use. In addition, you can use the pixel’s library of functions to:
-track conversions, so you can measure ad effectiveness
-define custom audiences, so you can target visitors who are more likely to convert
-set up dynamic ad campaigns”
https://developers.facebook.com/docs/facebook-pixel
“The following data can be collected by the Facebook Pixel:
– Http Headers – Anything present in HTTP headers. HTTP Headers are a standard web protocol sent between any browser request and any server on the internet. HTTP Headers include IP addresses, information about the web browser, page location, document, referrer and person using the website.
-Pixel-specific Data – Includes Pixel ID and the Facebook Cookie.
-Button Click Data – Includes any buttons clicked by site visitors, the labels of those buttons and any pages visited as a result of the button clicks.
-Optional Values – Developers and marketers can optionally choose to send additional information about the visit through Custom Data events. Example custom data events are conversion value, page type and more.
-Form Field Names – Includes website field names like email, address, quantity, etc., for when you purchase a product or service. We don’t capture field values unless you include them as part of Advanced Matching or optional values.”
Facebook Cookie Policy:
https://www.facebook.com/policy/cookies
“Websites and apps provided by other companies that use the Meta Products, including companies that incorporate Meta technologies into their websites and apps. Meta uses cookies and receives information when you visit those sites and apps, including device information and information about your activity, without any further action from you. This occurs whether or not you have a Facebook account or are logged in.”
Facebook Shadow Profiles:
https://www.makeuseof.com/tag/facebook-shadow-profiles/
Best way I know to block them is Ublock Origin though there are other methods. Here’s a tutorial that shows how easy it is.
https://www.youtube.com/watch?v=2lisQQmWQkY
Regards,
BoBeX