
The world is changing fast and your private data is at risk whenever you go online. Numerous entities, both public and private, are working hard to track, monitor, and record your digital activities. There are many reasons for this:
- Advertisers (including Google and Facebook) want to know everything about you, including your web browsing history, location data, contacts, and more. This makes it easier (and more profitable) to serve you targeted ads and influence your purchases.
- In an age of pandemics and lockdowns, many governments around the world are working hard to track movement and biometric data of their citizens.
- ISPs (internet service providers) are spying on their customers and feeding this data to various third parties, including advertisers and government agencies. In many countries, this is not only legal, but required. See for example in the United Kingdom (with the Investigatory Powers Act), United States (Senate Joint Resolution 34), and now also in Australia (mandatory data retention).
- The internet is also becoming less free due to censorship efforts and content blocking. Whether it is China, Germany, the UK, or the United States, various groups are working hard to censor content online.
But don’t get discouraged. Alternative technologies are experiencing a renaissance as awareness about these issues grows and people seek out solutions. Indeed, for all of the problems listed above, we find excellent solutions to give you more privacy, security, and freedom in your digital life. And that is the purpose of this guide: to give you solutions. Here’s what we’ll cover in this guide:
- Secure and privacy-focused browser
- Virtual Private Network
- Ad blocker
- Password manager
- Secure and encrypted messaging
- Private search engine
- Private email
- Operating system
- Antivirus software
- Data removal tools
But before we begin, one key consideration is your threat model. How much privacy and security do you need given your unique situation and the adversaries you may face?
Most people today are seeking protection against online tracking by advertising networks as well as a higher level of privacy and security. Others, such as investigative journalists working with sensitive information, would likely need an even higher level of protection. So keep this in mind as you proceed. Everyone is unique in their approach to privacy and security; there is no one-size-fits-all solution.
So here’s what you need:
1. Secure and privacy-friendly browser
Everyone needs to be using a secure and privacy-friendly browser for three important reasons:
- Browsers have a large attack surface and can be compromised in many ways.
- By default, most browsers contain lots of private information, including your browsing history, usernames, passwords, and autofill information, such as your name, address, etc.
- Browsers can reveal lots of identifying information about your location, system settings, hardware, and much more to third parties.
Secure Browsers: Based on my own tests and experience, here are the most secure browsers that also respect your privacy:
- Brave – Brave is a chromium-based browser that is very privacy-focused right out of the box. By default, it will block ads and trackers, and it’s also customizable, fast, and has built-in protection against browser fingerprinting.
- Firefox (modified) – Firefox is a great browser for both privacy and security after doing some modifications. It is highly customizable to give you the level of security and privacy you desire, while also being compatible with many browser extensions. See our guide on how to modify Firefox for more privacy.
- Tor browser – The Tor browser is hardened version of Firefox that also utilizes the Tor network by default (but this can be disabled).
- Ungoogled Chromium – As the name suggests, Ungoogled Chromium is a stripped-down Chromium browser that has been “Ungoogled” for more privacy. Source code is here.
- LibreWolf – This is a fork of Firefox that has been tweaked for more privacy and security.
Of course, there are many browsers on the market and choosing the best one all comes down to your own needs and tastes. Chrome, Opera, Safari, and Vivaldi also get some attention, but they’re not the best choices from a privacy standpoint.
2. Virtual Private Network (VPN)
Using a good VPN (virtual private network) is one of the simplest and most effective ways to protect your privacy, secure your devices, and also access blocked content online. A VPN is a critical tool to be using, especially with internet service providers spying on their users and logging all activity.

Here are some of the problems that VPNs can solve:
- ISP Spying – A VPN will encrypt and anonymize your internet connection. This makes your traffic completely unreadable to your ISP and other third parties.
- Blocked content – A VPN will let you easily get around blocked content and censorship. Simply connect to a VPN server in the region you need and access the website or stream as normal.
- IP and location tracking – Many websites and advertisers track users through their IP address. With a VPN, your IP address and location will be replaced by the VPN server’s IP address and location.
- Copyright issues – Torrenting and streaming media from third-party sources can come with some risk in the form of copyright issues. A VPN will anonymize your IP address and help keep you safe.
We’ve tested all of the popular VPN services and the results can really vary. Below are our current recommendations that are private, secure, fast, and reliable on many platforms.
- NordVPN – Best all-around VPN with secure apps for all major devices and very fast speeds (over 750 Mbps). Great for streaming plus extra security features (with a 74% off coupon).
- Surfshark – Best VPN for many devices (unlimited)
- ExpressVPN – Secure and reliable VPN service
- Proton VPN – User-friendly and private VPN in Switzerland
We have other recommendations and providers in our guide on the best VPN services.
And if you are new to VPNs, we also have a guide on how to use a VPN.
3. Advertisement, tracker, and malware blocker
A good ad blocker is essential for privacy and security reasons. From a privacy perspective, it’s important to block ads because they also function as tracking by recording your online activity to create an intimate user profile. This data is then used for targeted ads and/or sold to other parties.
Ads are also risky from a security perspective because they can contain malicious code that can infect your device when a web page loads – no clicks required.
Effectively blocking all ads is the only way to go. Here are a few different options from our guide on the best ad blockers:
- Browser ad blocker extensions – Browser-based ad blocker extensions, such as uBlock Origin are quite popular, but they also come with some tradeoffs. Online ads may still be using up resources and tracking you, even if the ads are not being displayed. Choose your ad blocker carefully – some ad blockers will collect user data for profit and/or show you “approved” ads.
- VPN ad blocker – There are now many VPNs with ad blocking built in. With this method, the VPN can effectively block ads, trackers, and malware at the VPN server, thereby protecting your devices.
- Ad blocker apps – A dedicated app will most likely do a very good job blocking ads on your device. One popular and well-regarded option is AdGuard.
- Ad blocking on a router – Ad blocking on a router can be accomplished various ways – from using ad blocking DNS to loading custom filter lists onto your router.
- Pi-hole – Pi-hole is a network-wide ad blocker that functions as a DNS server and can be deployed in various ways. It is most often used on a Raspberry Pi, connected to your home router (but there are many other different setup options).
The best ad blocking setup will depend on your situation and needs. If you have numerous devices you use at home, setting up a network-wide ad blocker would be a good solution for blanket protection. uBlock Origin remains a popular option for browser-based ad blockers. However, I like NordVPN with the Threat Protection feature as a simple, all-in-one solution for VPN and ad-blocking.
4. Password manager
The topic of passwords is actually quite large, encompassing password strength, password management, and password storage. In this section we’ll focus on password management and storage. Many people store passwords directly in the web browser — but this can be risky.
A more secure method is to use a dedicated password manager app. And note that a dedicated password manager can also offer browser extensions that are convenient and secure. Here’s a screenshot of Bitwarden, which is one of our favorites:
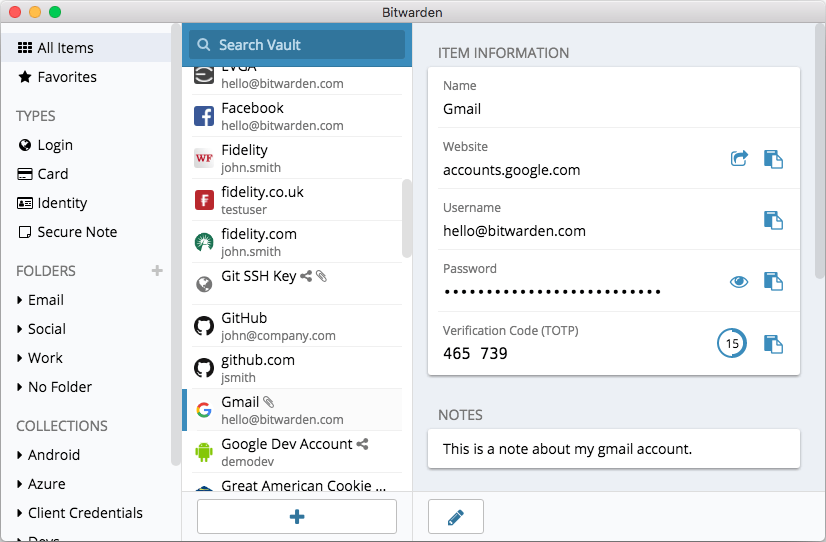
Here are the best password managers we have tested:
- NordPass – From the makers of NordVPN and NordLocker, NordPass is a secure, user-friendly password manager that has also passed a third-party audit. (See the NordPass review here.)
- Bitwarden – A free and open source password manager that is user-friendly and secure. (See our Bitwarden review.)
- 1Password – Another great option is 1Password, with many features and strong security standards for all types of devices (our 1Password review has more info).
- KeePassXC – As a locally-hosted password solution, KeePassXC differs from the others on our list. See the pros and cons of this password manager in our KeePass review.
Start using a good password manager today. See also our guide on how to create strong passwords.
5. Secure and encrypted messaging apps

Many people are turning to secure and encrypted messaging apps over concerns with privacy and security of other popular messengers. For example, WhatsApp collects and shares data from your phone with Facebook, the parent company of WhatsApp. If you find this concerning (and you should), then consider some of the secure alternatives below.
Additionally, with the inherent limitations of email, we recommend a secure messaging app for those wanting the most secure messaging platform possible. The secure messaging apps below utilize strong encryption standards and work well for teams or individual use on various operating systems and devices.
- Signal – This is probably the most popular secure messenger with a rapidly-growing user base. It is free, open source, and very secure. We really liked how it performed in our Signal review — but also noted some drawbacks, such as the need to use your phone number for verification.
- Wire – Based in Switzerland, Wire is another great option that is secure, user-friendly, and fully featured. While there is a free version for personal use, it is hard to find, as described in our Wire messenger review.
- Threema – This is one of the few paid encrypted messengers, but it’s only $2.99 for a lifetime license. Threema is also based in Switzerland and is open source. See our Threema review here.
- Telegram – Telegram is a very popular encrypted messaging app out of Russia, but it also is not encrypted by default. See the pros and cons in our Telegram review.
With all of the people abandoning WhatsApp and going over to Signal, there’s a better chance to connect with people you know on a secure platform. This trend kicked off early last year and we hope to see it continue!
Note: Also keep in mind that standard SMS text messages are not secure or private. They can be read by your phone service provider and are susceptible to man-in-the-middle attacks and also eavesdropping by Stingray devices. When privacy matters, use a good secure messaging app.
6. Private search engine
The big search engines (Google, Yahoo, Bing) record and track your searches, which helps them to build a user profile for their advertising partners.
Consider these privacy-friendly search engines instead:
- MetaGer – An open source metasearch engine with good features, based in Germany.
- Searx – A privacy-friendly and versatile metasearch engine that’s also open source.
- SwissCows – A zero-tracking private search engine based in Switzerland, hosted on secure Swiss infrastructure.
- Qwant – A private search engine based in France.
- DuckDuckGo – A private search engine based in the US.
- Mojeek – The only true search engine (rather than metasearch engine) that has its own crawler and index (based in the UK).
- YaCy – A decentralized, open source, peer-to-peer search engine.
There are also a few “private search engines” that are now owned by advertising companies. For example, Startpage was bought out by System1, a pay-per-click ad company. For more information, see our guide on private search engines.
7. Private email
Many of the popular email providers, such as Gmail, Yahoo, and iCloud are not good choices when it comes to privacy. Would you want random people having full access to your emails, collecting data for targeted ads, or passing the information on to third parties? This actually happens.
- Gmail gives third parties full access to emails and also tracks all of your purchases by reading the receipts in your inbox.
- Advertisers are allowed to scan Yahoo and AOL accounts to “identify and segment potential customers by picking up on contextual buying signals, and past purchases.”
- Yahoo was found to be scanning emails in real-time for US surveillance agencies.
And while Gmail remains the most popular service in the world, you pay with your privacy. Consequently, as awareness about these issues grows, many people are seeking alternatives to Gmail.
If you care about privacy and the security of your data, consider these secure email services. Here are some excellent options:
- Proton Mail – Best for strong encryption (33% off coupon)
- StartMail – Private email hosted in The Netherlands (50% off coupon)
- Mailfence – A secure and customizable email service
- Tuta Mail – Secure Email for Any Device
- Mailbox.org – Affordable private German email service
- Posteo – Reliable anonymous email service
- Runbox – Private email in Norway
- CounterMail – Swedish email with strong security features
- Kolab Now: Swiss email, compliant with GDPR, HIPAA, and PCI
- Soverin – Basic private email service
And if you want to learn more, check out these reviews:
- ProtonMail Review
- StartMail Review
- Tutanota Review
- Mailfence Review
- Mailbox.org Review
- Hushmail Review
- Posteo Review
- Fastmail Review
- Runbox Review
Note: We also have a guide on encrypting email.
8. Operating system
Consider using the free and open source Linux operating system. There are many different versions of the Linux operating system designed for different types of users:
- If you want the look and feel of Mac OS or Windows, check out Elementary OS.
- Ubuntu, Mint, and Debian are other popular options.
Tails is another privacy-focused operating system that can be run live on a USB drive, CD, or SD card.
Problems with Windows and Mac OS
Windows – The latest version of Windows (Windows 10) is a platform built for total surveillance – giving corporations and governments complete access to everything you do on your machine. Aside from data collection concerns, most malware targets Windows users – another serious drawback and security risk.
Mac OS – While Apple may be slightly better in terms of privacy, it too has problems. Just like Microsoft, Apple has configured its operating systems to collect vast amounts of your private data, whether it is browsing history through Safari, connection data, location services, and more.
9. Antivirus software
While not necessarily a “privacy” tool, using good antivirus software may be wise depending on your situation. The problem, however, is that many antivirus solutions abuse your privacy and may come with some invasive and “unwanted” additions.
Just like with sketchy free VPN services, free antivirus software can also be problematic. In testing eight popular free antivirus suites, Emsisoft discovered that seven of them were bundled with PUPs (potentially unwanted programs), which can be harmful and very annoying. Tip: avoid free antivirus software!
Another major issue is privacy. Many popular antivirus suites utilize invasive data collection, to include browsing history, “suspicious” files, metadata, and more. Carefully read through the privacy policy of your antivirus before installing.
Although RestorePrivacy does not devote much attention to antivirus software, one solution that offers the highest levels of security while also respecting user privacy is Emsisoft. Another potentially good option, which is entirely FOSS, is Clam AV.
See also the antivirus privacy guide.
10. Data removal tools
As regular readers of this site know, personal data is valuable. In fact, there massive companies working behind the scenes to collect, compile, and sell your private data to third parties.
While there are good solutions for how to delete your digital footprint, there are also tools that take an active approach in targeting these data brokers. These types of tools and services are becoming increasingly popular, especially as the data collection problem becomes increasingly worse.
Here at RestorePrivacy, we have tested many different market leaders, such as DeleteMe and Incogni. Based on our tests and analysis, these are some of the top options:
- Incogni – Developed by the team behind the popular VPN service Surfshark, Incogni is a simple-to-use solution that focuses on efficient data removal across a wide network of platforms.
- DeleteMe – A popular choice that offers a wide variety of features and services designed to protect your privacy and keep your personal data away from data brokers and people search sites.
- Optery – A comprehensive tool that prioritizes the secure erasure of data from various databases, helping users regain control of their online information.
See the best data removal services here.
Conclusion: Restore your privacy and take control of your data
That’s all for now, although this guide will continue to be updated with more privacy tools and information. We’re also keeping an eye on discussions surrounding privacy tools on various forums, such as Reddit.
If you have any feedback, tips, or suggestions based on privacy and security tools you are using, feel free to drop a comment below!
This article was last updated on May 31, 2024.

I coded an encrypted calculator extension for firefox and chrome. Lightweight, no ads, no registration, free of charge.
1) https://addons.mozilla.org/en-US/firefox/addon/encrypted-calculator/
2) https://chromewebstore.google.com/detail/encrypted-calculator/cmjikefegmcdkiicdcknjbbllnbdjpig
Maybe it can be included in the list. I do not make money out of it.
How do we learn?
Is it not in part, to question what we think we know?
How to be fair and just starting from a netural blank state, when our learning independents require coordinates to specify uniquely self-centered points in a space unknown?
When they say what don’t kill you only makes you stronger, in an amniotic sac evolutionary perspective of growth expression.
In that by something, it still continues with the encoded values we have of fundamentally human flaws—blinders. Resulting from our thousands of years of culture and evolution inso we exist.
Whether or not we’d admit it, we all have prejudices.
Only in properly vetted multidirectional research methods may it suggest(s), that when a computer learns human language through a technique called machine learning, it will inevitably learns those implicit human biases, too.
The “God Factor” highlights the immense gap between human intelligence and even the most advanced computer systems. This disparity is reflected in the current AI’s ability to simulate and manipulate the world, effectively becoming its own creator and sustainer – who would succeed without the throne of god.
I do not want to live in a world as a demigod-drone of non-divine rule. Without god’s superiority at the center in all dimensions of spatial extent. Totality overall of a logic in a divine human magnitude of covet with the holy deity. A sum where his holy spirit only imbues our human existence throughout endless time and space of God’s infinite Mind. The Omni-Trinity in the spirits supreme ultimate reality.
Because in our self-deception reasons of rationalizing away the relevance, significance, and importance of all opposing evidence and logical argument.
The future path, in that a number of computer-generated minds buzzing away inside computer simulations. Soon could vastly outnumber a total sum of real human minds that have ever lived as walking throughout history as we know it.
IS AI set to runover and overran our very logic of self by every possible abhorrency in adoption. Where the overflow becomes inundating and overwhelming to our very solitude, harming our living within the truth of ourself goal.
Making corporate’s AI the matrices in threat-modes to the intricate workings of the natural world, with that of our embryonic human process. Our own natural way of approaching an equilibrium within nature for our assimilation in responding to new situations in a union’s conformity with what is already available to the consciousness.
Where human justice of administrations are marshalled within our psyche totality of the unconscious elements while forming the concord (acculturation-socialization) of evil to the human mind.
AI’s tainted equilibrium would be more likely to come from the barristers, boardrooms or bargaining tables, as example of tech’s hierarchy power to lockin their matrix dominance of an ambitionious helm.
Our forever lesson now, to the great corrupting effect on a society by a stepping up in their steroidal control of massive tech rollouts harming life in the 21 century.
Overloading the little time we all have of one’s self in solitude (fasting), by isolating ourself within thought.
Personal time needed for our careful appraisal and study for substantiating ourself against the hive’s social growth. One’s own working thoughts in the dissecting of organized patterns of relationships, through our interactions with self, as well to one another. Purging evil’s reach by removal of the soiled contents within that defile another’s ethics in their principles of consequence.
While searching for real people’s flare of self expression with a united enhanced interest, to bringing up new questions towards old problems.
One that be-
About what are computers capable of and about the mass volumed nature to reality itself. As theorists begin to think of our universe as nothing more than a vast collection of information. Can we ever truly know whether our witnessed reality is as “real” as we think it is?
https://www.pbs.org/wgbh/nova/article/do-computers-dream-of-electric-people/
Because, if this life is a dream, it has a heart without grace and no clemency for deliverance.
In finding a way home – if somethings that are not forever right with this sideshow life – something is not right period.
He’s calling your name, don’t be lukewarm.
https://m.youtube.com/watch?v=OTVkaKBtu4M
Maybe these links help get you caught up some?
Graphene is one of the hottest supermaterials on the horizon.
https://www.pbs.org/wgbh/nova/article/new-two-dimensional-material-could-be-more-powerful-than-graphene/
Einsteins Quantum Riddle
https://www.pbs.org/wgbh/nova/video/einsteins-quantum-riddle/
Quantum-Leap
https://www.pbs.org/wgbh/nova/video/the-fabric-of-the-cosmos-quantum-leap/
Universe or Multiverse
https://www.pbs.org/wgbh/nova/video/the-fabric-of-the-cosmos-universe-or-multiverse/
Decoding the Universe-Cosmos
https://www.pbs.org/wgbh/nova/video/decoding-the-universe-cosmos/
Computers That Learn Human Languages Also Inherit Their Implicit Biases
https://www.pbs.org/wgbh/nova/article/computers-that-learn-human-languages-also-inherit-our-implicit-biases/
See why experts are saying it’s the dawn of a new Information Age. (2019 News had aired that G had a working quantum back then).
https://www.pbs.org/wgbh/nova/video/six-ways-quantum-computers-could-change-the-world/
The Elegant Universe-pt2
https://www.pbs.org/wgbh/nova/video/the-elegant-universe-part-2/
To be in the world but not of it, means what?
That only can be determined within self, but see the path of the world, where from the big bang to the present. Everything has been exploited in some way.
Predator against prey in consuming and causing natural adaptations by resistance as camouflage or repel methods. Natural mechanisms having to evolved over the millions of years to thrive in their ecosystems.
The heavens that the apex of life is ascending from to a perfection that’s beyond life as we can only dream!
Thank you friends and Alex most importantly!
= ) my friend , going offline here as I said…
What if there was a national, or internation protest DAY?
Web-Out DAY
To protest against- the AI course in the internet path.
See it real in that history, the present, as well as the path they want us all on is not in benefits to us consumers personally!
☆IT’S A DANGEROUS course☆
YOUR KIND WORDS ARE AS IMPORTANT TO AN AUTHOR as their views were of value to whom relates to those perspectives, with sharing in their own idea’s. Helping get people closer together. Let Alex and others know your listening.
2024 is expected to be a significant year for quantum computing, with advancements in error-corrected quantum computers, quantum data centers, and hybrid systems, as well as continued growth in the industry and increased investment in research and development.
As a summary of the current state and expected developments in quantum computing in 2024.
1 Error-corrected quantum computers – QuEra Computing is set to launch a fault-tolerant quantum computer with 256 physical and 10 logical qubits in late 2024, marking a significant milestone in the development of practical quantum computing.
2 Quantum data center in Germany – IBM Quantum is constructing a new quantum data center in Ehningen, Germany, which is expected to introduce local quantum computing resources to Europe in 2024.
3 Quantum computing industry growth – Despite a decline in private investment in the Americas, the global quantum computing industry is expected to continue growing, with over 30 governments committing to more than $40 billion in public funding for quantum technologies by 2026.
4 Quantum emulation – Cloud-based emulators offering up to 40 qubits are available, enabling researchers to prototype algorithms without relying on hardware constraints or computational errors. However, memory consumption remains a significant challenge.
5 Quantum computing trends – In 2024, quantum computing is expected to revolutionize various sectors, including finance, with applications such as quantum-resistant cryptography and optimization algorithms.
6 Hybrid quantum systems – Combining classical and quantum computing offers a pragmatic approach to unlocking immediate value for businesses, as the journey to fully functional, fault-tolerant quantum computers is a marathon, not a sprint.
7 Quantum computing centers and initiatives – The UK National Quantum Computing Centre (NQCC) is set to open in 2024, promoting cross-sector quantum collaboration to spur growth in the UK economy. IQM Spark, a superconducting quantum computer, is also being tailored for academic institutions and research labs.
The assumption that GenAI can seamlessly integrates with network architectures without issues is unproven.
Generative AI (GenAI) as a subset of Deep Learning (DL) that generates content, such as text, imagery, audio, or video, based on patterns learned from existing data.
The unproven assumptions are as follows.
Scalability > GenAI models may not scale efficiently with large datasets or complex network architectures, leading to performance degradation or even failures.
Interpretability > The lack of transparency in GenAI decision-making processes can make it challenging to identify and troubleshoot issues in network architectures, potentially leading to nightmares for network architects.
Robustness > GenAI models may not be robust enough to handle unexpected inputs, edge cases, or adversarial attacks, which can compromise network security and reliability.
Let us start by acknowledging these unproven assumptions and any potential nightmares, that the network architects can proactively address the challenges and to develop strategies to successfully integrate GenAI with their network architectures.
Several unproven assumptions emerge as potential nightmares for network architects and internet users regarding PII (Personally Identifiable Information) data.
1 Message Auditing < The assumption that periodic human-based audits or reviews of messages will detect and correct assumptions is unproven. Auditing processes must be thorough and timely to identify potential issues.
LIKE Astroturfing by bots are a sophisticated and insidious form of disinformation. To effectively combat it, we must develop and deploy advanced detection tools, analyze network patterns, and promote transparency and accountability.
2 GenAI Model Behavior < The assumption that GenAI models will always behave as intended and not produce biased or inaccurate responses is unproven. Without robust testing and auditing, GenAI models may generate responses that compromise user data or violate assumptions.
3 Shared Indexes < The assumption that shared indexes containing end-user data do not pose a risk to data privacy is unproven. Without robust security measures, shared indexes can compromise user data.
4 Cloud Service Provider Implementation < The assumption that cloud service providers will adequately isolate tenant data through their implementation is unproven. Network architects must verify and test these implementations to ensure PII data is properly protected.
5 Dedicated Indexes < The assumption that dedicated indexes containing end-user data are sufficient to ensure data isolation is also unproven fact.
Without proper implementation and testing, dedicated indexes may not provide the necessary security boundaries.
6 Hybrid Approach < The assumption that a hybrid approach, combining shared and dedicated indexes, can effectively balance security and scalability is an unproven fact. This approach may introduce new vulnerabilities and complexities.
To ensure the secure and responsible deployment of GenAI solutions these network architects and organizations deploying GenAI solutions must be foremost transparently upfront and sheer enough to be seen throughin as in their protecting the gold of internet users PII data.
To help understand, the major categories of ownership in a breakdown of our own, to the US national debt. (These figures are subject to change over time due to market fluctuations, government actions, and other factors. It is not providing a comprehensive breakdown of all in holding the US debt.)
Foreign governments and investors: As of April 2024, foreign countries own approximately $7.9 trillion (22.9% of total US debt) in US Treasurys. The top five foreign holders are:
Japan ($1.1 trillion)
China ($749.0 billion)
United Kingdom ($690.2 billion)
Luxembourg ($373.5 billion)
Canada ($328.7 billion)
Federal Reserve: The Federal Reserve, as the central bank, owns approximately $21.8% ($6.87 trillion) of the public debt, which is part of the government’s monetary policy.
Intragovernmental holdings: This category includes trust funds, such as those for Medicare, Social Security, and other government programs. As of October 2018, intragovernmental holdings accounted for approximately 28% ($6.2 trillion) of the total debt held by the public.
Domestic investors: The remaining 50% or so of the national debt is held by domestic investors, including:
Individual investors (e.g., retirement accounts, individual bonds)
Institutional investors (e.g., pension funds, insurance companies)
Mutual funds and exchange-traded funds (ETFs)
Banks and other financial institutions
Interesting to see the pie cuts, yes? Defaulting only hurts our own domestic investors, who suffer the most in owning 50+% of our national debt.
How would defaulting not hurt foreign debt holders?
Hi I’m sorry you got that information from my words.
“who suffer the most in owning 50+% of our national debt.”
I only meant it as a childish thing for our US leaders to let happen, instead of working across the aisle. Yes all investors would see ill affects that lay claim to the US national debt. True…for sure!
Just that every four years this division here in our US, makes us all seem like there are no mature adults running things on our end.
Thank you for your help vanp sir.
Just something, @9o5 August 22, 2024, “The U.S. Defense Department’s task given (for{-}strikeout) (add-) by the United States government failed at my above counts 1-5 for today’s digital world.”
#4 in the 1990’s, tech companies began to recognize the potential of the Internet and started to lay the groundwork for its widespread adoption, backseating our governments military involvement.
So then as of the 90’s, without this idea of accountability, and with the distribution of control thus opened up wide to the wild-west of technology. The digital computerized way in course, that started replacing the old analog ways.
Have you ever thought about where the immense wealth of the starter Internet giants such as Google or Facebook comes from?
In pre-Internet times such wealth used to be accumulated through an access to some resource and its exploitation. It could be natural resources such as oil and gas or gold, human manpower and later with the automation in manufacturing and so on.
So what resource do web giants exploit? This is our PII data they collect. This is the digitial gold of the 21th century. Ditial gold which smart people started storing for extraction without asking anybodies permission from anyone. The gold held in our information, as one’s self as a person with their habits, associations, and interests which are basically taken from YOU in the manner of stealing.
Welcome to the present Internet where the landlords make as much money as possible and in our own making use of as much digitial data as possible. Because the titians if tech, still control of the internet’s theme and composition as being overly centralized, it’s vulnerable, manipulative nature and inso a dangerious prone state to interact with for digital users.
Good catch and the updates of your information, some I had oops passed over. I try but could use help as knowing people are reading and interested about tomorrow now…
Thanks for all help thats constructive.
I say learn from the old knowing what futuristic tech trends are here as to that were once the stuff of science fiction.
Its like a picture puzzle going from the flat-pane to a high-quality 3D model. As can accurately represent real-world objects, making them renditions for plans and product design, architecture, and visual effects. Standing in your face short of being a live hologram!!!
Alex, are you a veteran or have relation that served? Maybe there are veteran readers here?
Here is something ya all may like to know.
Google Cloud Launchpad for Veterans November 7, 2024 at 9:00 AM – November 8, 2024 at 5:00 PM CST Attend the 2 day virtual ‘Cloud Digital Leader’ training event. After the 2 day training event, you will receive a complimentary exam voucher which retails for $99 USD. Read about – register here.
https://rsvp.withgoogle.com/events/google_cloud_launchpad_for_vets
Cool, thanks for sharing BITR.
Hey, Alex let me post one more lengthy comment here and I’ll go away for a long while again – deal?
Sir…I know you are dealing with Bots, as possibility in mass commenting on the site or gearing up for that, and I don’t want to harm your efforts. As by posting where I’ve found that necessary in same kind of way, to cast the information on to people by your free resouce here.
Ego’s as I had used to engauge different reader sects of your visitors.
Like you Alex, I’m only trying to inform people for their honest good.
This is not my request herein this comment, but I want to use SA via HS ego’s to present that last comment for your readers. (You should know SA-newest and HS-oldest in long form) ego names. My last comment request, I beleve should conclude the sum whole to facts prevalent for the summarized overall digital user view in current tech within our life to understand the basic meaning of users privacy lost.
Where RestorePrivacy starts!
Not me, as in KISS principle of rule.
DEAL ??? Just post this and I know.
Digital flux, which refers to the constant change and evolution of digital technologies, platforms, and trends. This encompasses the rapid shifts in consumer behavior, market demands, and technological advancements that shape the digital landscape for any organization within the reach of a countries surveillance laws.
One flux comes up more often now.
NFV, SDN – Impact to Network Architecture.
The emerging technologies like Network Function Virtualization (NFV) and Software-Defined Networking (SDN) transform wired device connectivity.
– NFV and SDN transform wired device connectivity by decoupling network functions from hardware, enabling software-based control and forwarding planes.
– These technologies reshape network architecture by moving from hardware-centric to software-centric, introducing centralized management and orchestration, and enabling programmability and automation.
– The convergence of data center and campus networks becomes more feasible, leading to consistent policies, scalability, and automation across both environments.
By adopting NFV and SDN, network administrators can create more agile, scalable, and efficient wired networks, better suited to meet the demands of modern digital services and applications.
It is yet to be seen that this adopting by industrial automation applications can better protect individual data privacy and security. Nor, can significantly reduce the risk of security breaches and ensure the integrity of your device connections.
While NFV and SDN introduce new threats and vulnerabilities, they also offer opportunities for improved security and privacy through the implementation of defense mechanisms and a holistic approach. By designing secure networks and network slices, and leveraging automation and programmability, network architects can better protect individual data privacy and security in modern network architectures. True or Not ?
2024 Predictions: 3 Broadband Trends to Watch
https://www.corning.com/optical-communications/worldwide/en/home/the-signal-network-blog/2024-predictions-3-broadband-trends-to-watch.html
What Does 2024 Have for Networking?
https://drivenets.com/blog/what-does-2024-have-for-networking/
Top 9 Emerging Technology Trends in Networking & Telecom 2024
https://www.calsoftinc.com/blogs/top-9-emerging-technology-trends-in-networking-telecom-2024.html
Yes I’m trying to understand things as they happen, if anyone can see the route better please help out. Main point, who owns the data we generate? When it leaves from our local device storage and gets stored to the cloud networks!
Review- NFV, SDN – Impact to Network Architecture.
The emerging technologies like Network Function Virtualization (NFV) and Software-Defined Networking (SDN) transform wired device connectivity.
– NFV and SDN transform wired device connectivity by decoupling network functions from hardware, enabling software-based control and forwarding planes.
Update- Open RAN (O – RAN)
One of the fascinating trends in the telco industry is network disaggregation. The network is disaggregated into multiple components that can be mixed and assembled depending on the use case model. This is achieved by utilizing the principles of Software Defined Networking (SDN) and Network Function Virtualization (NFV).
With Open RAN, the distinct functions of the base station are split into a centralized Unit (CU), Distributed Unit (DU), and Radio Unit (RU) based on open standards and interfaces, which will boost multi-vendor and cost-effective implementations.
The critical disruption in Open RAN is the RAN Intelligence Controller (RIC) which brings interoperability, flexibility, and programmability to the networks. Open RAN RIC is the practical enabler for AI-native RAN. The integration of AI into Open RAN and being consistent with the existing 3GPP evolution path can provide the benefits of a fully AI-native network.
Update- – Edge computing is a distributed computing model that brings computation and data storage closer to the sources of data, reducing latency and improving real-time processing. It involves deploying small, resource-constrained devices (e.g., edge nodes, gateways, or servers) at the edge of the network, near the users or devices generating data. These edge devices perform tasks, such as data processing, filtering, and analytics, on behalf of the cloud or central data centers.
Update- – – Caching is a technique used to improve the performance and efficiency of data retrieval by storing frequently accessed data in a faster, more accessible location. In the context of edge computing, caching refers to the temporary storage of data or content at the edge of the network, reducing the need for repeated requests to central servers.
Edge computing is a broader concept that encompasses caching as a technique to improve data retrieval efficiency. While caching is an essential component of edge computing, the two terms are not interchangeable
Are we being sold on legally binding promises?
Cloud-based computing introduces network dependencies, which can affect offline capability and data storage.
Cloud-based applications require a stable internet connection to function optimally. Sudden network outages or reboots can disrupt service, leading to operational delays and downtime.
Cloud-based data storage requires robust encryption and security measures to protect against data theft and unauthorized access. This includes using secure protocols, access controls, and data encryption at rest and in transit.
Cloud storage relies on network connectivity to access and retrieve data. This can lead to slower data retrieval times and increased latency, especially in areas with poor internet infrastructure and disrupt business continuity.
The adoption of 5G technology is one of the key trends in the telecom industry. The introduction of 5G technologies and beyond, support a broad range of use cases and applications in the market, realizing digital transformation. The upcoming substantial advancement in digital transformation is 5G Non-Public Networks (NPN) or Private 5G Networks. Enterprises have initiated embracing Private 5G to lighten security and efficiency challenges. Enterprises are competing and driving towards enhanced digitization with emerging technologies like 5G, Wi-Fi 6, and AI.
Sustainable digital transformation is a strategic constraint to any best practices that include the execution of energy-efficient procedures and the encouragement of corporate social responsibility programs.
AI-enabled network automation optimizes and automates the network planning, design, and operations in the telecom domain. By 2027, 90% of enterprises will utilize AI/Gen AI capabilities to automate network operations.
Cyberattacks and threats are increasing and becoming complex with technological advancements. Every year, reports say that cybercriminals are more prolific and worsening the threat landscape. Technology evolution also increases the number of users, devices, and software to provide innovative and futuristic solutions.
I’m not jack-jawing you guys, to be anything but a warning!
But, open those eyes up people. See it real in that history, the present, as well as the path they want us all on is not in benefits to us consumers personally!
☆IT’S A DANGEROUS course☆
LLMjacking, a term coined by Sysdig TRT, refers to the illegal acquisition of access to LLMs via compromised cloud credentials. Attackers typically infiltrate cloud environments to locate and exploit enterprise LLMs, passing the operational costs onto the victim. The rise in LLMjacking reflects both the increasing popularity of LLMs and attackers’ growing expertise in exploiting them, especially in cloud-hosted environments like AWS Bedrock.
https://cyberinsider.com/llmjacking-attacks-escalate-driving-costs-to-over-100000-day/
Microsoft Chose Profit Over Security and Left U.S. Government Vulnerable to Russian Hack, Whistleblower Andrew Harris Says…
Harris said he pleaded with the MS company for several years to address the flaw in the product, a ProPublica investigation has found. But at every turn, Microsoft dismissed his warnings, telling him they would work on a long-term alternative — leaving cloud services around the globe vulnerable to attack in the meantime.
DiCola, Harris’ then-supervisor, told ProPublica the race to dominate the market for new and high-growth areas like the cloud drove the decisions of Microsoft’s product teams. “That is always like, ‘Do whatever it frickin’ takes to win because you have to win.’ Because if you don’t win, it’s much harder to win it back in the future.
ttps://www.propublica.org/article/microsoft-solarwinds-golden-saml-data-breach-russian-hackers
These examples illustrate how states are using surveillance technology to spy on the public, often without warrants or adequate oversight. The use of these technologies raises concerns about privacy, civil liberties, and the potential for abuse of power.
– Warrantless Wiretapping: The US government uses Section 702 of the Foreign Intelligence Surveillance Act (FISA) to conduct warrantless wiretapping of communications between foreign targets and US persons. This allows the government to collect massive amounts of data on Americans’ communications, including emails, messages, and internet activity.
– PRISM Program: The PRISM program, revealed by Edward Snowden, enables the NSA to directly access communications data from major tech companies like Google, Facebook, and Apple, without a warrant. This program collects data on international communications, including those of ordinary Americans.
– National Security Letters (NSLs): The FBI uses NSLs to demand that financial institutions and other organizations provide customer data without a warrant. This has led to the surveillance of millions of Americans, including those with conservative viewpoints or Second Amendment interests.
– Big Data Analytics: The government uses big data analytics tools to analyze and filter transactions, targeting terms like “MAGA” and “TRUMP,” as well as purchases of books, religious texts, firearms-related items, and recreational stores. This surveillance extends beyond criminal suspicion, likely encompassing millions of Americans.
– Surveillance of Financial Data: The government has accessed financial data from institutions like Citigroup, Bank of America, and JPMorgan Chase, using warrantless searches and NSLs. This has raised concerns about the government’s ability to monitor Americans’ financial activities without a warrant.
– Biometric Surveillance: The government uses biometric technologies, such as facial recognition and iris scanning, to monitor individuals. This includes the use of surveillance cameras, drones, and other technologies to track people’s movements and activities.
– Total Information Awareness (TIA) Program: The TIA program, although defunct, aimed to collect and analyze vast amounts of data on Americans’ activities, including financial transactions, travel patterns, and internet activity.
– Surveillance of Public Spaces: The government uses aerial surveillance, such as drones and spy planes, to monitor public spaces, including shopping malls and industrial parks. This blurs the line between public and private spaces, allowing for increased surveillance of individuals.
Some US AI Surveillance Used
______________________
– Mass Surveillance: Section 702 of the Foreign Intelligence Surveillance Act permits the US government to engage in warrantless surveillance of Americans’ international communications, including phone calls, texts, emails, social media messages, and web browsing. This surveillance is conducted using AI-powered systems to analyze and filter vast amounts of data.
– Algorithmic Personalized Pricing: The Federal Trade Commission (FTC) is investigating how companies use AI to tailor prices to individual consumers based on their data, including demographics, behavior, and browsing history. This practice, dubbed “surveillance pricing,” raises concerns about privacy and potential anticompetitive practices.
– Drone Surveillance: Insurance companies, like Travelers, are using AI-powered drones to monitor homeowners’ properties, potentially collecting data on residents’ activities and habits. While the company denies using this data for underwriting decisions, the practice raises privacy concerns.
– Public Surveillance Systems: AI-powered public surveillance systems, such as facial recognition technologies (FRT) and contact tracing applications, are being deployed in public spaces. These systems can track individual movements, monitor behavior, and predict social patterns, potentially infringing on privacy and human rights.
– Government Surveillance Infrastructure: Governments are investing in AI-powered surveillance infrastructure, including millions of cameras, to monitor and track citizens. AI can process every frame and provide real-time analysis, enabling authorities to identify and respond to potential threats.
When SmartTech has more liberties than the public where are our public Bill Of Rights liberties gone? You know that condition of being free from confinement, oppressive restriction or control by a government or other power, free to engage in certain actions without control or interference by a government or other power as the publics BOR liberties spelled out and is protected by the Bill of Rights.
That was our wild card in life before any surveillance technology landed, got established and being twisted now with AI…ever came along!
These liberties have been lost due to the government’s adoption of surveillance technologies without adequate safeguards and oversight. The lack of transparency and accountability has enabled the government to engage in widespread surveillance, often without a clear legal framework or judicial oversight.
To restore these lost liberties, it is essential to:
– Implement robust privacy protections and safeguards for surveillance technologies.
– Establish clear legal frameworks and judicial oversight for government surveillance.
– Increase transparency and accountability for government surveillance activities.
– Enact reforms to protect journalists’ sources and whistleblowers.
– Promote online anonymity and encryption to protect individuals’ free speech and association rights.
– Increase transparency and accountability for the use, storage, tranfer and monetary sale/profit in public PII Data, in the US territories and Mainland. Forbid the transfers of the publics PII Data outside of the US governments control.
Only by addressing these issues can we ensure that the Bill of Rights is upheld in the digital age and that individuals’ fundamental liberties are protected from the encroachment of surveillance technology.
EMFs Linked to Cancer, Autoimmunity, Immune Dysfunction
A meta-analysis of 42 studies found an association between ELF-EMFs and cancer risk, particularly in the United States and residential exposed populations.
https://drleonardcoldwell.com/2024/05/28/emfs-linked-to-cancer-autoimmunity-immune-dysfunction/
Alex, I ran across this-
Instagram AI bots are software programs designed to automate tasks on the Instagram platform, leveraging artificial intelligence (AI) and machine learning (ML) algorithms.
Types of Instagram AI Bots
1. Growthbeast: A browser extension that automates following, liking, commenting, and unfollowing, with advanced filters and customization options.
2. Axiom: A no-code bot builder that allows users to create custom bots for automating Instagram actions, including posting, liking, commenting, and more.
3. Instagram Bots: General-purpose bots that can be customized for various tasks, such as mass following, mass liking, and mass commenting.
Concerns
Bots may violate Instagram’s policies of their own Instagram’s Terms of Service leading to account suspension or termination.
Fake accounts and spam.
Misinformation and propaganda.
Aggressive or intrusive bot behavior can negatively impact user experience and engagement, which can harm the platform’s integrity.
A study estimates that up to 95 million bot accounts may be active on the platform, highlighting the need for improved detection and mitigation strategies.
In an Executive Summary, 35 news organizations in the United States, the United Kingdom, and Germany.
36 international experts from industry, academia, technology, and policy.
This report – How AI Retools, Rationalizes, and Reshapes Journalism and the Public Arena. Examines the use of AI across editorial, commercial, and technological domains with an eye to the structural implications of AI in news organizations for the public arena.
There is much debate about how artificial intelligence should be defined and what should and should not count as true AI. While it is beyond the scope of this report to explore this debate in detail, it cannot be ignored. It is fair to say there is no consensus about what constitutes AI, nor is there a generally accepted definition of AI.
There is, however, agreement around what AI is not: namely, a conscious, general intelligence that understands and works across domains.
CREDIT
https://www.cjr.org/tow_center_reports/artificial-intelligence-in-the-news.php
***- – – – – ***
THURSDAY SEPT 12TH / one-hour TV show. ABC Television has an AI special with Oprah Winfrey.
CREDIT
https://m.slashdot.org/story/432692
Soon after the announcement, some AI critics began questioning the guest list and the framing of the show in general.
https://arstechnica.com/information-technology/2024/09/oprahs-upcoming-ai-television-special-sparks-outrage-among-tech-critics/
Critics of generative AI … question the utility of the technology, its perceived environmental impact, and what they see as blatant copyright infringement.
“Sure is nice of Oprah to host this extended sales pitch for the generative AI industry at a moment when its fortunes are flagging and the AI bubble is threatening to burst,” tweeted author Brian Merchant, who frequently criticizes generative AI technology in op-eds, social media, and through his “Blood in the Machine” AI newsletter. “The way the experts who are not experts are presented as such what a train wreck,” replied artist Karla Ortiz, who is a plaintiff in a lawsuit against several AI companies. “There’s still PLENTY of time to get actual experts and have a better discussion on this because yikes.” On Friday, Ortiz created a lengthy viral thread on X that detailed her potential issues with the program, writing, “This event will be the first time many people will get info on Generative AI. However it is shaping up to be a misinformed marketing event starring vested interests (some who are under a litany of lawsuits) who ignore the harms GenAi inflicts on communities NOW.”
According to various studies and tests, EVs’ braking distances are often longer than those of ICE vehicles. A recent study found that the added weight of EVs can increase their stopping distance by up to 10% compared to similar ICE vehicles.
Looking at stopping distances shows that some EVs have braking distances up to 137 feet (42 meters) from 60 mph, while a similar ICE vehicle might have a stopping distance of around 120 feet (37 meters).
Besides, the fact of responsible driver behavior’s remains essential for road safety. Drivers of EV’s should consider,
Weight: EVs are generally heavier.
Regenerative braking: EVs’ regenerative braking systems convert kinetic energy into electrical energy.
Tire selection: EVs often come equipped with tyres designed for low rolling resistance which can compromise braking performance.
Is this new for Websites or is it I just noticed it.
Vulnerability Disclosure Policy
Where I’ve seen it, is a product site, so a first for me.
[https://sharkninja.com/vulnerability-disclosure-policy/]
Alex, have you seen anything along direction this yet?
1) Around 1969, the U.S. Defense Department’s Advanced Research Projects Agency (ARPA) funded the development of ARPANET, the precursor to the modern internet.
2) By the 1970s, it brought on developments of the Transmission Control Protocol (TCP) and Internet Protocol (IP).
3) 1989 introduced the World Wide Web (WWW), a system of interlinked hypertext documents accessible via the internet.
4) Early in the 1990s the internet became available to the general public, and saw the first secure online transaction taking place in 1994.
5) The Internet has transformed life, and with the rise given to social media platforms, online communities, and e-commerce. Makes the world go round 24/7/365/360.
So by the initial plan as history has recorded it, dating back to the 1950s, when the United States government initiated a project to create a network of computers for communication and information sharing. This effort was driven by official’s concerned about the Cold War and the present potential for surprise attacks.
The U.S. Defense Department’s task given for the United States government failed at my above counts 1-5 for today’s digital world. Which is fluctuating with new technology faster than old challenges are solved.
Are we as a nation ready for Artificial intelligence, with its AI-centric tech overhead?
@Mike, I’ve always liked what you bring to the comments. I have a question, are AI smartphones our Titanic with GenAI as the iceberg?
It’s the leading design of ‘chips’ and ‘engines’ with neural processing capabilities and on-board machine learning being the pinnacle of connectivity and luxury for online users.
Since the use of an AI Phone term hit, it’s not understood what the heck the leading phone manufacturers meant by that term and how we got here. Is it to be expected than an AI Phone will give us a global resource where AI is on the same world page. That policymakers, regulators, academics, and the private sector with civil society handles the challenges posed by Artificial Intelligence?
And not like the obtuse differences contributed to the varying levels of security, speed, and functionality among VPN services of that history.
@9o5 if you’re referring to me, I do not like the usage of AI on any electronic devices and if I decide to upgrade my smartphone, I am going to see if there is one without AI on it or if the new phone I get that has AI enables me to opt-out.
AI is a useful tool to use for many things, but to be an “assistant” in this regard is not one of them.
Yez you, Mike because you supply links to support your words.
Smartphones were to help humans not hurt us. I guess you could blame it on the technology.
Happening before any set regulations, so the fuze has been lit. The bang that’s to come we have looked for – GenAI is possibly that bang.
It’s worth remembering that most Smartphones have been tapping into AI-centric tech and features for years, but, that use of AI in smartphones has mostly been as supportive. 2023 marked a move towards generative AI. So it’s now that this smart tech actually is serving up content and more actively aiding phone users. As it can generate images and itineraries for them or drafting responses to emails.
https://www.techradar.com/phones/2024-will-be-the-year-of-the-ai-phone-whether-we-like-it-or-not
Mike, me to, I do not like the usage of AI on any electronic device. Flip phones with their limited connectivity, lack of apps, no GPS, simplified design, and basic encryption make them a more private option compared to smartphones. So I will downgrade in my next phone to less convenience for more personal privacy.
Mike here’s a 02/24 discussion on the topic, note OP #1 of the point made in AI subcriptions to pay for these AI server farms by the smartphones brands. To pay to use their features of the phones with AI-centric tech thats embeded within it.
https://xdaforums.com/t/samsung-forced-phone-subscription-fee-the-future.4654151/
I’ll bet, the local area electrical grids where these server farms are located. Will cause the areas residents to see hugh electric bill price increases.
Unfortunately, two open source, privacy-oriented mobile keyboard apps, FlorisBoard and OpenBoard, have been discontinued. However, Fossify’s keyboard and a fork of OpenBoard, Heliboard, are available to take their place. AnySoft Keyboard has not been updated in two years so it might be safe to assume that is discontinued despite a lack of notice. One other option that looks promising is FUTO Keyboard.
Both apps are available on F-Droid and GitHub.
HeliBoard – https://github.com/Helium314/HeliBoard
Fossify – https://github.com/FossifyOrg/Keyboard
FUTO Keyboard – https://github.com/futo-org/android-keyboard
Fossify – https://github.com/FossifyOrg/Keyboard
I’ve just found out that Simple Mobile Tools (a suite of open source apps that can replace most of Android’s core applications) is no more. The head of the effort, Tibor Kaputa, sold his product to ZipApps that will, likely, add new features such as advertisements, subscriptions and probably convert the apps to proprietary.
Thankfully, a developer with SMT has forked the apps before the purchase was finalized and has started a new project called Fossify. Most of the original SMT apps, save a calculator, are available on Google’s Play Store, F-Droid, or Fossify’s GitHub (links below).
I must admit to being annoyed since I emailed Kaputa not too long ago, letting him know I was a customer and one would think he would at least email people he has interacted with (like me) letting them know. Plus, Simple Mobile Tools’ website is still up and there’s nothing on it to indicate the suite of applications has been sold or discontinued.
GitHub – https://github.com/FossifyOrg
F-Droid – https://search.f-droid.org/?q=fossify&lang=en
Google Play Store – https://play.google.com/store/apps/dev?id=7297838378654322558