
There is a lot of misinformation being promoted in various privacy circles about Tor. This article will examine some facts about Tor and assess whether it is the infallible privacy tool it’s made out to be by some.
There is a growing chorus of people who blindly recommend Tor to anyone looking for online anonymity. This recommendation often ignores mountains of evidence suggesting that Tor is not the “privacy tool” it’s made out to be.
No privacy tool is above criticism or scrutiny, and each has pros and cons. Unfortunately, Tor has garnered a cult-like following in recent years among people who pretend it’s infallible. Honest criticism of Tor is often met with accusations of “FUD” and ad-hominem attacks, so as not to disrupt the collective Groupthink.
Never mind the fact that the Tor network is a popular hangout for pedophiles and drug dealers – along with the law enforcement these types attract. Today, Tor is being marketed as some kind of grass-roots privacy tool that will protect you against government surveillance and various bad actors.
According to Roger Dingledine (Tor co-founder) and other key Tor developers, getting people (outside the US government) to widely adopt Tor is very important for the US government’s ability to use Tor for its own purposes. In this goal, they have largely succeeded with Tor being widely promoted in various privacy circles by people who don’t know any better.
But is Tor really a secure and trustworthy privacy tool?
Here are the facts.
1. Tor is compromised (and not anonymous)
That governments can de-anonymize Tor users is another well-known point that’s been acknowledged for years.
In 2013 the Washington Post broke an article citing reports that US government agencies had figured out how to de-anonymize Tor users on a “wide scale”. From the Washington Post:
Since 2006, according to a 49-page research paper titled simply “Tor,” the agency has worked on several methods that, if successful, would allow the NSA to uncloak anonymous traffic on a “wide scale” — effectively by watching communications as they enter and exit the Tor system, rather than trying to follow them inside. One type of attack, for example, would identify users by minute differences in the clock times on their computers.
There are also reports of government agencies cooperating with researchers to “break” or somehow exploit Tor to de-anonymize users:
Then in July, a much anticipated talk at the Black Hat hacking conference was abruptly canceled. Alexander Volynkin and Michael McCord, academics from Carnegie Mellon University (CMU), promised to reveal how a $3,000 piece of kit could unmask the IP addresses of Tor hidden services as well as their users.
Its description bore a startling resemblance to the attack the Tor Project had documented earlier that month. Volynkin and McCord’s method would deanonymize Tor users through the use of recently disclosed vulnerabilities and a “handful of powerful servers.” On top of this, the pair claimed they had tested attacks in the wild.
For $3,000 worth of hardware, this team from Carnegie Mellon could effectively “unmask” Tor users. And this was in 2015.
In 2016, a court case brought more information to light about how the US federal government hired software engineers to effectively crack Tor and de-anonymize users.
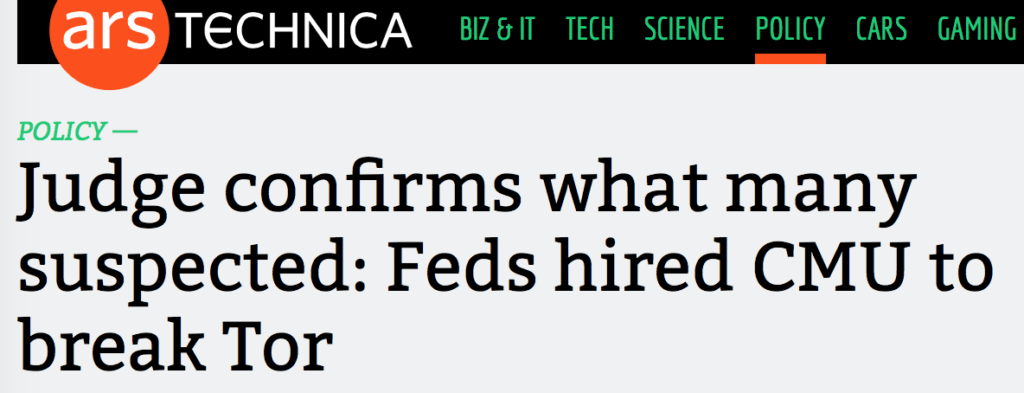
ARS Technica also discussed this case in February 2016 where they noted:
A federal judge in Washington has now confirmed what has been strongly suspected: that Carnegie Mellon University (CMU) researchers at its Software Engineering Institute were hired by the federal government to do research into breaking Tor in 2014.
The following year, in 2017, more evidence came forward showing how the FBI can see what you’re up to on Tor.
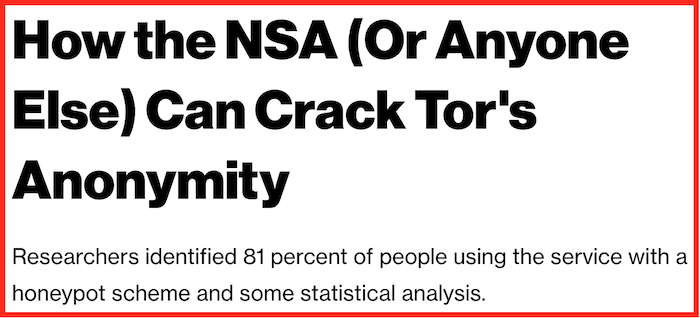
There are also researchers who devised attacks allowing them to de-anonymize 81% of Tor users in the wild. This article came out in 2014, before the Carnegie Mellon research was carried out.
And there’s more…
2017 court case proves FBI can de-anonymize Tor users
The means by which the FBI is able to de-anonymize Tor users and discover their real IP address remains classified information. In a 2017 court case, the FBI refused to divulge how it was able to do this, which ultimately led to child abusers on the Tor network going free. From the Tech Times:
In this case, the FBI managed to breach the anonymity Tor promises and the means used to collect the evidence from the dark web make up a sensitive matter. The technique is valuable to the FBI, so the government would rather compromise this case rather than release the source code it used.
“The government must now choose between disclosure of classified information and dismissal of its indictment,” federal prosecutor Annette Hayes said in a court filing on Friday.
The cat is out of the bag. The FBI (and presumably other government agencies) has proven to be fully capable of de-anonymizing Tor users. Most Tor promoters simply ignore these different cases and the obvious implications.
2. Tor developers are cooperating with US government agencies
Some Tor users may be surprised to know the extent to which Tor developers are working directly with US government agencies. After all, Tor is often promoted as a grass-roots privacy effort to help you stay “anonymous” against Big Brother.
One journalist was able to clarify this cooperation through FOIA requests, which revealed many interesting exchanges.
Here is one email correspondence in which Roger Dingledine discusses cooperation with the DOJ (Department of Justice) and FBI (Federal Bureau of Investigation), while also referencing “backdoors” being installed.
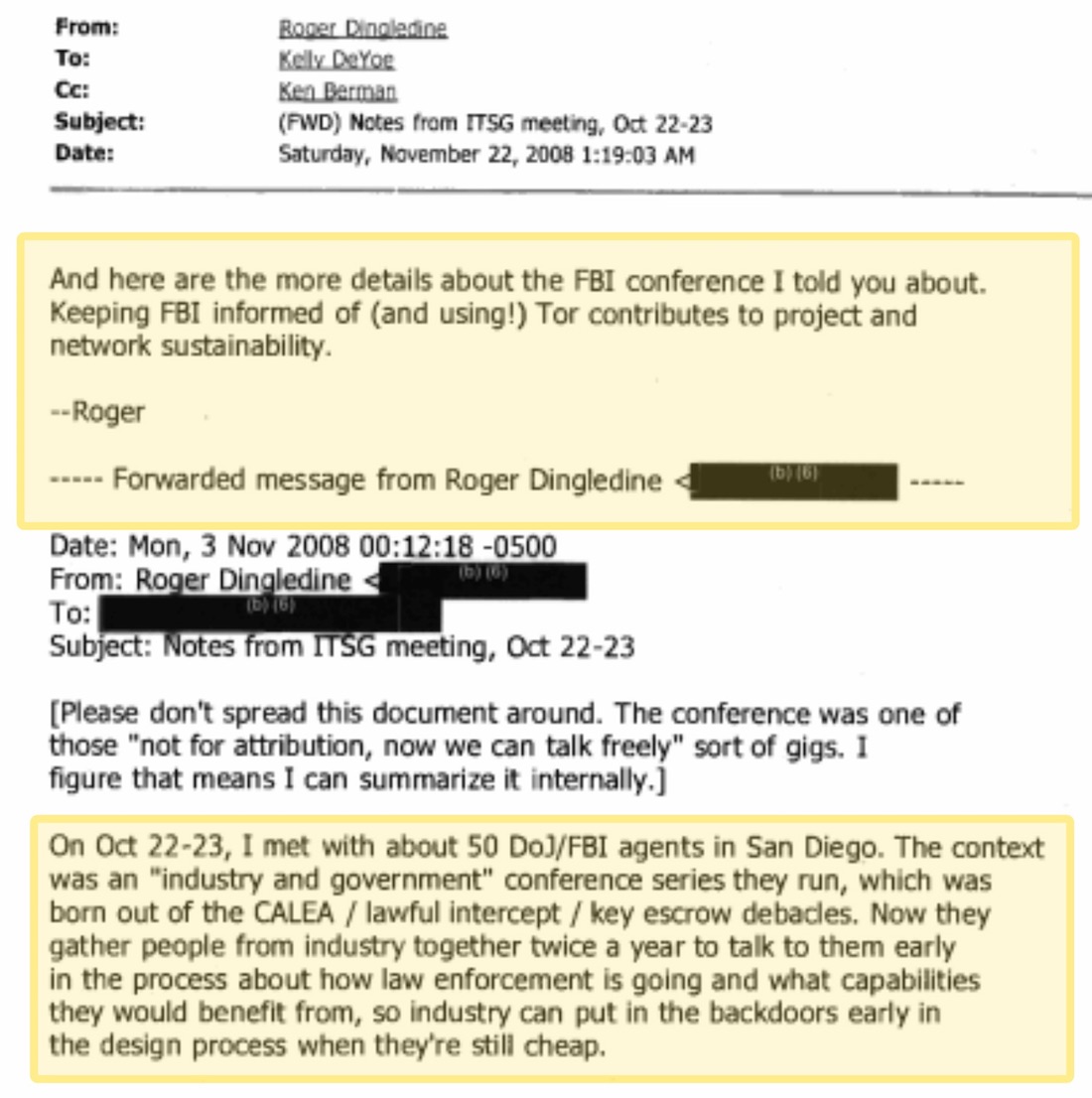
You can see more details from this correspondence here.
In another exchange below, Tor developer Steven Murdoch discovered a vulnerability with the way Tor was handling TLS encryption. This vulnerability made it easier to de-anonymize Tor users, and as such, it would be valuable to government agencies. Knowing the problems this could cause, Steven suggested keeping the document internal,
…it might be a good to delay the release of anything like ‘this attack is bad; I hope nobody realizes it before we fix it’.
Eight days later, based on the emails below, Roger Dingledine alerted two government agents about this vulnerability:

While there is disagreement as to the seriousness of these issues, one thing remains clear.
Tor developers are closely working with the US government.
The journalist who collected the FOIA documents also suggests that, “Tor privately tips off the federal government to security vulnerabilities before alerting the public.”
Whether or not you agree with the ultimate conclusion of this researcher, the facts remain for anyone who wants to acknowledge them. The big issue is the close cooperation between Tor developers and US government agencies.
You can see numerous exchanges between Tor developers and US government agencies here. (Backup copy of documents.)
And if you really want to dive in, check out the full FOIA cache here.
3. When you use Tor, you stand out like a glow stick
Meet Eldo Kim. He was the Harvard student who assumed Tor would make him “anonymous” when sending bomb threats.

Kim didn’t realize that when he connected to Tor on the university network, he would stand out like a f***ing glow stick.
The FBI and the network admins at Harvard were able to easily pinpoint Kim because he was using Tor around the time the bomb threat email was sent through the Tor network. From the criminal complaint:
Harvard University was able to determine that, in the several hours leading up to the receipt of the e-mail messages described above, ELDO KIM accessed TOR using Harvard’s wireless network.
Eldo Kim is just one of many, many examples of people who have bought into the lie that Tor provides blanket online anonymity – and later paid the price.
Had Kim used a bridge or VPN before accessing the Tor network, he probably would have gotten away with it (we’ll discuss this more below).
4. Anybody can operate Tor nodes and collect your data and IP address
Many proponents of Tor argue that its decentralized nature is a benefit. While there are indeed advantages to decentralization, there are also some major risks. Namely, that anybody can operate the Tor nodes through which your traffic is being routed.
There have been numerous examples of people setting up Tor nodes to collect data from gullible Tor users who thought they would be safe and secure.
Take for example Dan Egerstad, a 22-year-old Swedish hacker. Egerstad set up a few Tor nodes around the world and collected vast amounts of private data in just a few months:
In time, Egerstad gained access to 1000 high-value email accounts. He would later post 100 sets of sensitive email logins and passwords on the internet for criminals, spies or just curious teenagers to use to snoop on inter-governmental, NGO and high-value corporate email.
The question on everybody’s lips was: how did he do it? The answer came more than a week later and was somewhat anti-climactic. The 22-year-old Swedish security consultant had merely installed free, open-source software – called Tor – on five computers in data centres around the globe and monitored it. Ironically, Tor is designed to prevent intelligence agencies, corporations and computer hackers from determining the virtual – and physical – location of the people who use it.
People think they’re protected just because they use Tor. Not only do they think it’s encrypted, but they also think ‘no one can find me’.
To not assume government agencies are doing this right now would be extremely naive.
Commenting on this case, security consultant Sam Stover emphasized the risks of someone snooping traffic through Tor nodes:
Domestic, or international . . . if you want to do intelligence gathering, there’s definitely data to be had there. (When using Tor) you have no idea if some guy in China is watching all your traffic, or some guy in Germany, or a guy in Illinois. You don’t know.
In fact, that is exactly how Wikileaks got started. The founders simply setup Tor nodes to siphon off more than a million private documents. According to Wired:
WikiLeaks, the controversial whistleblowing site that exposes secrets of governments and corporations, bootstrapped itself with a cache of documents obtained through an internet eavesdropping operation by one of its activists, according to a new profile of the organization’s founder.
The activist siphoned more than a million documents as they traveled across the internet through Tor, also known as “The Onion Router,” a sophisticated privacy tool that lets users navigate and send documents through the internet anonymously.
Are governments running Tor nodes for bulk data collection?
Egerstad also suggests Tor nodes may be controlled by powerful agencies (governments) with vast resources:
In addition to hackers using Tor to hide their origins, it’s plausible that intelligence services had set up rogue exit nodes to sniff data from the Tor network.
“If you actually look in to where these Tor nodes are hosted and how big they are, some of these nodes cost thousands of dollars each month just to host because they’re using lots of bandwidth, they’re heavy-duty servers and so on,” Egerstad says. “Who would pay for this and be anonymous?“
Back in 2014, government agencies seized a number of different Tor relays in what is known as “Operation Onymous”. From the Tor Project blog:
Over the last few days, we received and read reports saying that several Tor relays were seized by government officials. We do not know why the systems were seized, nor do we know anything about the methods of investigation which were used. Specifically, there are reports that three systems of Torservers.net disappeared and there is another report by an independent relay operator.
Commenting on this case, ARS Technica noted in 2014:
On July 4, the Tor Project identified a group of Tor relays that were actively trying to break the anonymity of users by making changes to the Tor protocol headers associated with their traffic over the network.
The rogue relays were set up on January 30, 2014—just two weeks after Blake Benthall allegedly announced he had taken control of Silk Road 2.0 and shortly after the Homeland Security undercover officer who infiltrated Silk Road 2.0 began getting paid to be a site administrator. The relays not only could have de-anonymized some users, but they also “probably tried to learn who published hidden service descriptors, which would allow the attackers to learn the location of that hidden service,” Tor project leader Roger Dingledine wrote in a July 30 blog post.
This issue continues to gain attention. In this Gizmodo article from 2021, we find the same problems. Bad actors can and do operate Tor nodes.
Additional reading: A mysterious threat actor is running hundreds of malicious Tor relays
No quality control!
The fundamental issue here is there is no real quality control mechanism for vetting Tor relay operators. Not only is there no authentication mechanism for setting up relays, but the operators themselves can also remain anonymous.
Assuming that some Tor nodes are data collection tools, it would also be safe to assume that many different governments are involved in data collection, such as the Chinese, Russian, and US governments.
See also: Tor network exit nodes found to be sniffing passing traffic
5. Malicious Tor nodes do exist
If government-controlled Tor nodes weren’t bad enough, you also have to consider malicious Tor nodes.
In 2016 a group of researchers presented a paper titled “HOnions: Towards Detection and Identification of Misbehaving Tor HSDirs“, which described how they identified 110 malicious Tor relays:
Over the last decade privacy infrastructures such as Tor proved to be very successful and widely used. However, Tor remains a practical system with a variety of limitations and open to abuse. Tor’s security and anonymity is based on the assumption that the large majority of the its relays are honest and do not misbehave. Particularly the privacy of the hidden services is dependent on the honest operation of Hidden Services Directories (HSDirs). In this work we introduce, the concept of honey onions (HOnions), a framework to detect and identify misbehaving and snooping HSDirs. After the deployment of our system and based on our experimental results during the period of 72 days, we detect and identify at least 110 such snooping relays. Furthermore, we reveal that more than half of them were hosted on cloud infrastructure and delayed the use of the learned information to prevent easy traceback.
When conspiracy “theory” becomes conspiracy fact.
The malicious HSDirs identified by the team were mostly located in the United States, Germany, France, United Kingdom and the Netherlands.
Just a few months after the HSDir issue broke, a different researcher identified a malicious Tor node injecting malware into file downloads.
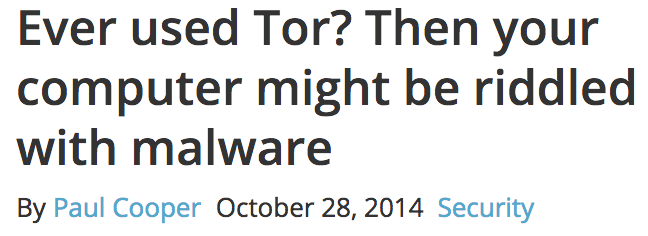
According to ITProPortal:
Authorities are advising all users of the Tor network to check their computers for malware after it emerged that a Russian hacker has been using the network to spread a powerful virus. The malware is spread by a compromised node in the Tor network.
…It has emerged that one of these exit nodes had been modified to alter any program downloaded over the network. This allowed the attacker to put his own executable code in such programs, and potentially take control of victims’ computers.
Due to the altered node, any Windows executable downloaded over the network was wrapped in malware, and worryingly even files downloaded over Windows Update were affected.
Use at your own risk.
See also:
OnionDuke APT Malware Distributed Via Malicious Tor Exit Node
6. No warrant necessary to spy on Tor users
Another interesting case highlighting the flaws of Tor comes form 2016 when the FBI was able to infiltrate Tor to bust another pedophile group.
According to Tech Times:
The U.S. Federal Bureau of Investigation (FBI) can still spy on users who use the Tor browser to remain anonymous on the web.
Senior U.S. District Court Judge Henry Coke Morgan, Jr. has ruled that the FBI does not need a warrant to hack into a U.S. citizen’s computer system. The ruling by the district judge relates to FBI sting called Operation Pacifier, which targeted a child pornography site called PlayPen on the Dark web.
The accused used Tor to access these websites. The federal agency, with the help of hacking tools on computers in Greece, Denmark, Chile and the U.S., was able to catch 1,500 pedophiles during the operation.
While it’s great to see these types of criminals getting shut down, this case also highlights the severe vulnerabilities of Tor as a privacy tool that can be trusted by journalists, political dissidents, whistleblowers, etc.
The judge in this case officially ruled that Tor users lack “a reasonable expectation of privacy” in hiding their IP address and identity. This essentially opens the door to any US government agency being able to spy on Tor users without obtaining a warrant or going through any legal channels.
This, of course, is a serious concern when you consider that journalists, activists, and whistleblowers are encouraged to use Tor to hide from government agencies and mass surveillance.
Now let’s put this all into context by looking at the history of Tor and it’s funding.
7. Tor was created by the US government (and not for your “right to privacy”)
If you think Tor was created for “privacy rights” or some other noble-sounding cause, then you would be mistaken. The quote below, from the co-founder of Tor, speaks volumes.
I forgot to mention earlier, probably something that will make you look at me in a new light. I contract for the United States Government to build anonymity technology for them and deploy it. They don’t think of it as anonymity technology, though we use that term. They think of it as security technology. They need these technologies so that they can research people they’re interested in, so that they can have anonymous tip lines, so that they can buy things from people without other countries figuring out what they are buying, how much they are buying and where it is going, that sort of thing.
— Roger Dingledine, co-founder of Tor, 2004 speech
This quote alone should convince any rational person to never use the Tor network, unless of course you want to be rubbing shoulders with government spooks on the Dark Web.
The history of Tor goes back to the 1990s when the Office of Naval Research and DARPA were working to create an online anonymity network in Washington, DC. This network was called “onion routing” and bounced traffic across different nodes before exiting to the final destination.
In 2002, the Alpha version of Tor was developed and released by Paul Syverson (Office of Naval Research), as well as Roger Dingledine and Nick Mathewson, who were both on contract with DARPA. This three-person team, working for the US government, developed Tor into what it is today.
The quote above was taken from a 2004 speech by Roger Dingledine, which you can also listen to here.
After Tor was developed and released for public use, it was eventually spun off as its own non-profit organization, with guidance coming from the Electronic Frontier Foundation (EFF):
At the very end of 2004, with Tor technology finally ready for deployment, the US Navy cut most of its Tor funding, released it under an open source license and, oddly, the project was handed over to the Electronic Frontier Foundation.
The Electronic Frontier Foundation (EFF) remains one of the biggest promoters of Tor today, which is not surprising given EFF’s deep ties to the project.
8. Tor is funded by the US government
It’s no secret that Tor is funded by various US government agencies.
The key question is whether US government funding negatively affects Tor’s independence and trustworthiness as a privacy tool.
Some journalists have closely examined the financial relationship between Tor and the US government:
Tor had always maintained that it was funded by a “variety of sources” and was not beholden to any one interest group. But I crunched the numbers and found that the exact opposite was true: In any given year, Tor drew between 90 to 100 percent of its budget via contracts and grants coming from three military-intel branches of the federal government: the Pentagon, the State Department and an old school CIA spinoff organization called the BBG.
Put simply: the financial data showed that Tor wasn’t the indie-grassroots anti-state org that it claimed to be. It was a military contractor. It even had its own official military contractor reference number from the government.
Here are some of the different government funding sources for the Tor Project over the years:
Broadcasting Board of Governors:
“Broadcasting Board of Governors (BBG) [now called U.S. Agency for Global Media], a federal agency that was spun off from the CIA and today oversees America’s foreign broadcasting operations, funded Tor to the tune of $6.1 million in the years from 2007 through 2015.” (source)
State Department:
“The State Department funded Tor to the tune of $3.3 million, mostly through its regime change arm — State Dept’s “Democracy, Human Rights and Labor” division.” (source)
The Pentagon:
“From 2011 through 2013, the Pentagon funded Tor to the tune of $2.2 million, through a U.S. Department of Defense / Navy contract — passed through a defense contractor called SRI International.” (source)
The grant is called: “Basic and Applied Research and Development in Areas Relating to the Navy Command, Control, Communications, Computers, Intelligence, Surveillance, and Reconnaissance.”
We can also see what the Tor project has to say about the matter.
When soliciting funds in 2005, Tor claimed that donors would be able to “influence” the direction of the project:
We are now actively looking for new contracts and funding. Sponsors of Tor get personal attention, better support, publicity (if they want it), and get to influence the direction of our research and development!
There you have it. Tor claims donors influence the direction of research and development – a fact that the Tor team even admits.
Do you really think the US government would invest millions of dollars into a tool that stifled its power?
9. When you use Tor, you help the US government do spooky stuff
The United States government can’t simply run an anonymity system for everybody and then use it themselves only. Because then every time a connection came from it people would say, “Oh, it’s another CIA agent looking at my website,” if those are the only people using the network. So you need to have other people using the network so they blend together.
—Roger Dingledine, co-founder of the Tor Network, 2004 speech
The implications of this statement are quite serious.
When you use Tor, you are literally helping the US government. Your traffic helps to conceal CIA agents who are also using Tor, as Dingledine and journalists are pointing out.
Tor is fundamentally a tool for the US government, and it remains so today:
Tor’s original — and current — purpose is to cloak the online identity of government agents and informants while they are in the field: gathering intelligence, setting up sting operations, giving human intelligence assets a way to report back to their handlers — that kind of thing. This information is out there, but it’s not very well known, and it’s certainly not emphasized by those who promote it.
You will never hear Tor promoters discuss how important it is for the US government to get others on the the Tor network. This remains a taboo topic that Tor advocates simply avoid.
The Tor Project’s website also discusses how Tor is actively used by government agencies for different purposes:
A branch of the U.S. Navy uses Tor for open source intelligence gathering, and one of its teams used Tor while deployed in the Middle East recently. Law enforcement uses Tor for visiting or surveilling web sites without leaving government IP addresses in their web logs, and for security during sting operations.
Michael Reed, another early developer of Tor, explained how it has always been a tool for US government military and intelligence operations:
The original *QUESTION* posed that led to the invention of Onion Routing was, “Can we build a system that allows for bi-directional communications over the Internet where the source and destination cannot be determined by a mid-point?” The *PURPOSE* was for DoD / Intelligence usage (open source intelligence gathering, covering of forward deployed assets, whatever). Not helping dissidents in repressive countries. Not assisting criminals in covering their electronic tracks. Not helping bit-torrent users avoid MPAA/RIAA prosecution. Not giving a 10 year old a way to bypass an anti-porn filter. Of course, we knew those would be other unavoidable uses for the technology, but that was immaterial to the problem at hand we were trying to solve (and if those uses were going to give us more cover traffic to better hide what we wanted to use the network for, all the better…I once told a flag officer that much to his chagrin).
Here’s another early Tor developer who spilled the beans. Tor was never meant for “dissidents in repressive countries” or helping various privacy activists fighting for human rights, which is how Tor is promoted today.
Just as Roger Dingledine asserted in the opening quote to this section, Paul Syverson (Tor co-founder) also emphasized the importance of getting other people to use Tor, thereby helping government agents perform their work and not stand out as the only Tor users:
If you have a system that’s only a Navy system, anything popping out of it is obviously from the Navy. You need to have a network that carries traffic for other people as well.
Tor is branded by many different individuals and groups as a grassroots project to protect people from government surveillance. In reality, however, it is a tool for government agents who are literally using it for military and intelligence operations (including spying on those who think they are “anonymous” on Tor).
Tor’s utility for the military-surveillance apparatus is explained well in the following quote:
Tor was created not to protect the public from government surveillance, but rather, to cloak the online identity of intelligence agents as they snooped on areas of interest. But in order to do that, Tor had to be released to the public and used by as diverse a group of people as possible: activists, dissidents, journalists, paranoiacs, kiddie porn scum, criminals and even would-be terrorists — the bigger and weirder the crowd, the easier it would be for agents to mix in and hide in plain sight.
According to these Tor developers and co-founders, when you use Tor you are helping US government agents in doing whatever they do on the Tor network. Why would anyone who advocates for privacy and human rights want to do that?
10. IP address leaks when using Tor
Another recurring problem with Tor is IP address leaks – a serious issue that will de-anonymize Tor users, even if the leak is brief.
In November 2017 a flaw was discovered that exposed the real IP address of Tor users if they clicked on a local file-based address, such as file://., rather than http:// or https://.
This issue illustrates a larger problem with Tor: it only encrypts traffic through the Tor browser, thereby leaving all other (non-Tor browser) traffic exposed.
Unlike a VPN that encrypts all traffic on your operating system, the Tor network only works through a browser configured for Tor. (See the ‘what is a VPN‘ guide for an overview.)
This design leaves Tor users vulnerable to leaks which will expose their identity in many different situations:
- Tor offers no protection when torrenting and will leak the user’s IP address with torrent clients.
- Tor may leak IP addresses when accessing files, such as PDFs or other documents, which will likely bypass proxy settings.
- Windows users are also vulnerable to different types of leaks that will expose the user’s real IP address.
It’s important to note, however, that oftentimes de-anonymization is due to user error or misconfiguration. Therefore blame does not lie with Tor itself, but rather with people not using Tor correctly.
Dan Eggerstad emphasized this issue as well when he stated:
People think they’re protected just because they use Tor. Not only do they think it’s encrypted, but they also think ‘no one can find me’. But if you’ve configured your computer wrong, which probably more than 50 per cent of the people using Tor have, you can still find the person (on) the other side.
Once again, non-technical users would be better off using a good VPN service that provides system-wide traffic encryption and an effective kill switch to block all traffic if the VPN connection drops.
11. Using Tor can make you a target
As we saw above with the bomb threat hoax, Eldo Kim was targeted because he was on the Tor network when the bomb threat was sent.
Other security experts also warn about Tor users being targeted merely for using Tor.
In addition, most really repressive places actually look for Tor and target those people. VPNs are used to watch Netflix and Hulu, but Tor has only one use case – to evade the authorities. There is no cover. (This is assuming it is being used to evade even in a country incapable of breaking Tor anonymity.)
In many ways Tor can be riskier than a VPN:
- VPNs are (typically) not actively malicious
- VPNs provide good cover that Tor simply cannot – “I was using it to watch Hulu videos” is much better than – “I was just trying to buy illegal drugs online”
As we’ve pointed out here before, VPNs are more widely used than Tor – and for various (legitimate) reasons, such as streaming Netflix with a VPN.
So maybe you still need (or want?) to use Tor. How can you do so with more safety?
How hide your IP address when using Tor
Given that Tor is compromised and bad actors can see the real IP address of Tor users, it would be wise to take extra precautions. This includes hiding your real IP address before accessing the Tor network.
To hide your IP address when accessing Tor, simply connect to a VPN server (through a VPN client on your computer) and then access Tor as normal (such as through the Tor browser). This will add a layer of encryption between your computer and the Tor network, with the VPN server’s IP address replacing your real IP address.
Note: There are different ways to combine VPNs and Tor. I am only recommending the following setup: You > VPN > Tor > Internet (also called “Tor over VPN” or “Onion over VPN”).
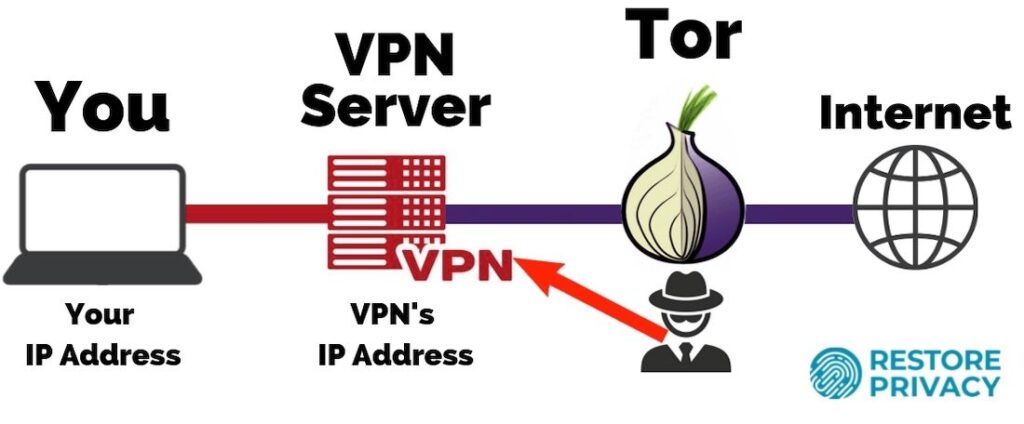
With this setup, even if a malicious actor was running a Tor server and logging all connecting IP addresses, your real IP address would remain hidden behind the VPN server (assuming you are using a good VPN with no leaks).
Here are the benefits of routing your traffic through a secure VPN before the Tor network:
- Your real IP address remains hidden from the Tor network (Tor cannot see who you are)
- Your internet provider (ISP) or network admin will not be able to see you are using Tor (because your traffic is being encrypted through a VPN server).
- You won’t stand out as much from other users because VPNs are more popular than Tor.
- You are distributing trust between Tor and a VPN. The VPN could see your IP address and Tor could see your traffic (sites you visit), but neither would have both your IP address and browsing activities.
For anyone distrustful of VPNs, there are a handful of verified no logs VPN services that have been proven to be truly “no logs”.
You can sign up for a VPN with a secure anonymous email account (not connected to your identity). For the truly paranoid, you can also pay with Bitcoin or any other anonymous payment method. Most VPNs do not require any name for registration, only a valid email address for account credentials. Using a VPN in a safe offshore jurisdiction (outside the 14 Eyes) may also be good, depending on your threat model.
For those seeking the highest levels of anonymity, you can chain multiple VPNs through Linux virtual machines (using Virtualbox, which is FOSS). You could also use VPN1 on your router, VPN2 on your computer, and then access the regular internet (or the Tor network) through two layers of encryption via two separate VPN services. This allows you to distribute trust across different VPN services and ensure neither VPN could have both your incoming IP address and traffic. This is discussed more in my guide on multi-hop VPN services.
Note: The claim that “VPN is fully, 100%, a single point/entity that you must trust” is false. This claim comes from this Tor promoter who coincidently works for the US government’s Naval Research Lab.
When you chain VPNs, you can distribute trust across different VPN services and different jurisdictions around the world, all paid for anonymously and not linked to your identity. With Tor alone, you put all your trust in The Onion Router…
Tor Project agrees on the benefits of adding VPN
The Tor Project also agrees on the benefits of correctly using a VPN with Tor, as I recommend above. Here are a few quotes from the Tor Project about the benefits of using a VPN before Tor (archived):
- “might prevent your ISP etc from seeing that you’re using Tor”
- Routing Tor through a VPN “can be a fine idea assuming your VPN provider’s network is in fact sufficiently safer than your own network.” [A verified no logs VPN is a lot safer than an internet provider that has your name, date of birth, payment details, and is collecting your data and sharing it with surveillance agencies, such as the case with US internet providers.]
- “Another advantage here is that it prevents Tor from seeing who you are behind the VPN. So if somebody does manage to break Tor and learn the IP address your traffic is coming from, … then you’ll be better off.”
While I generally agree with the points above, unfortunately, the Tor Project also stated some incorrect information in the beginning of their article as follows, “Most VPN/SSH provider log, there is a money trail, if you can’t pay really anonymously.”
These points are incorrect.
- “Most VPN/SSH provider log” – This is simply not true. There are many no logs VPN services and also a small number of VPNs that are verified to be no logs, having undergone third-party audits, server seizures, or court subpoenas for user data.
- “there is a money trail” – This is a huge misconception that is promoted by people who don’t know what they’re talking about. A “money trail” has no bearing on the effectiveness or encryption of a VPN. VPNs are not illegal and are becoming mainstream privacy tools. If an adversary knows you have a subscription with a specific VPN service, this has zero bearing on the effectiveness of your VPN. Even if the adversary has your username and password, this still has no bearing on the effectiveness or encryption of the VPN (it just means your adversary can use the VPN for free). VPN encryption is dynamic and negotiated new with each connection. And if you are worried about “money trails” then pay anonymously.
- “can’t pay really anonymously” – This is again false, perhaps blatant lying to scare people away from VPNs. Most VPNs offer anonymous payment options, such as gift cards or Bitcoin, with no name required. You only need a valid email, and you can easily setup an anonymous/burner email for this purpose that’s not connected to your identity. Done.
Note: While there have been various cases proving the FBI can easily de-anonymize Tor users, there has never been any court cases (that I’ve seen) proving the FBI (or any government agency) can de-anonymize VPN users, assuming there’s good encryption with no leaks. Instead, we have seen a few isolated cases where the FBI pressured VPNs to log user data and provide this to authorities to identify a specific user, such as with the IPVanish logging case in the US.
Tor vulnerabilities and VPNs
There are other attacks that the Tor Project admits will de-anonymize Tor users (archived):
As mentioned above, it is possible for an observer who can view both you and either the destination website or your Tor exit node to correlate timings of your traffic as it enters the Tor network and also as it exits. Tor does not defend against such a threat model.
Once again, a VPN can help to mitigate the risk of de-anonymization by hiding your source IP address before accessing the guard node in the Tor circuit.
Can exit nodes eavesdrop on communications? From the Tor Project:
Yes, the guy running the exit node can read the bytes that come in and out there. Tor anonymizes the origin of your traffic, and it makes sure to encrypt everything inside the Tor network, but it does not magically encrypt all traffic throughout the Internet.
However, a VPN can not do anything about a bad Tor exit node eavesdropping on your traffic, although it will help hide who you are (but your traffic can also give you away).
I discuss these points more in my VPN vs Tor comparison.
Conclusion
No privacy tool is above criticism.
Just like with Tor, I have also pointed out numerous problems with VPNs, including VPNs that were caught lying about logs, VPN scams, and dangerous free VPN services. All privacy tools come with pros and cons. Selecting the best tool for the job all boils down to your threat model and unique needs.
Unfortunately, for many in the privacy community, Tor is now considered to be an infallible tool for blanket anonymity, and to question this dogma means you are “spreading FUD”. This is pathetic.
In closing, for regular users seeking more security and online anonymity, I’d simply avoid Tor altogether. A VPN will offer system-wide encryption, much faster speeds, and user-friendly clients for various devices and operating systems. This will also prevent your ISP from seeing what you’re up to online.
Additionally, VPNs are more mainstream and there are many legitimate (and legal!) reasons for using them. Compared to Tor, you definitely won’t stand out as much with a VPN.
For those who still want to access the Tor network, doing so through a reliable VPN service will add an extra layer of protection while hiding your real IP address.
Further Reading:
Tor and its Discontents: Problems with Tor Usage as Panacea
Users Get Routed: Traffic Correlation on Tor by Realistic Adversaries
Tor network exit nodes found to be sniffing passing traffic
On the Effectiveness of Traffic Analysis Against Anonymity Networks Using Flow Records
Judge confirms what many suspected: Feds hired CMU to break Tor

Tor Browser probably is a lie. But not too much that restoreprivacy…
I think this article does a great job highlighting how no single privacy tool can completely ensure one’s own safety online. It was interesting to see all the issues with Tor, and for a while I believed Tor was the go-to primarily because everyone recommended it. I think a good alternative for my use case might be using Windows 10/11 on a VM, a VPN, and router-level dns blocking. In the VM, a plain install of a popular browser with no extensions may be a good way to blend in with the crowd. Of course, this is given that the search activity is not linkable to an identity of sorts. Should I then clear all cookies upon every session end?
OK, I don’t have evidences, didn’t make a screenshot, but a few minutes ago I was using Tor Browser, and, as a site was not loading well Cloudflare, I change the Tor circuit and get a Russian node.
I don’t think this is a good sign. I mean, this is a contradiction, because, how do you could claim that you
“defend privacy and freedom online”, especially for people who live in country with heavy censorship and using a node from a country that in the latest years (there was no need of an invasion) have criticized, even for the people who live in Russia about ‘you know who’. Unless, this mean, that the Russian Government has official nodes on Tor.
What would be next? Nodes in China, Iran, Afghanistan, North Korea, Cuba, Venezuela?, probably Belarus too.
Don’t get me wrong, I have nothing against the people who live in those country, my problem is the f**kers who are in charge.
It’s me again, and again this afternoon I get a Russian node. Here is a screenshot.
https://ibb.co/CQCWXx1
Could be related to Snowflake bridge? Usually I don’t use bridges, but as the site in question in the latest days have some issues with Cloudflare, I thought that bridges could help to bypass the human verification.
Simply using Tor makes you sketchy and a target, it seems. Troublesome in this era of rogue agencies and repressive regimes. Alarming as recent reports finding brand name computers hiding back doors at the BIOS level. Regret supporting Patriot Act, that trojan horse sold as answer to terrorism.
Great article, probably some subsidies to VPN companies, but yes TOR and any other browser is not 100% safe.
One issue not related on the article with TOR is the constant blocking from thousands of websites when you use TOR. This is censorship disguised as ‘for your safety BS’. Behind this blocking are the usual internet censors and big tech trackers like Cloudflare, Nginx, google & co.
Sites running these false security ‘tools’ recognize the users use a browser that is more anonymous and is difficult to be tracked and spied on so they immediately send a message like : “checking your computer”. You might be a robot” or “you’ve been blocked”.
Interestingly, the majority of this censorship comes from Cloudflare, a corporation originally funded by CIA seeds who routinely ‘cancel’ websites with narratives they don’t like but on the other hand host various well known pedophile websites with zero censorship.
About TOR, my guess is that, coming from DARPA and other US gov agencies, most traffic is under surveillance of some kind even though more users allow US operatives to stay cloaked in the crowd, they probably monitor more nodes than we think.
Now about VPN’s. The problems with VPN are:
1/ that you have to pay for it, meaning you lose instantly your anonymity to the provider. They have everything about you including your bank account. So much for privacy!
2/ You have to download an application to run the VPN, it’s not like using a proxy/VPN online, it is installed on your device and what about backdoors and other inconveniences?
3/ India has recently enacted “laws” (diktats) obliging VPN providers to log IP addresses and traffic. So what privacy do the users have left to circumvent corporate and government surveillance? None! Soon, these abuses will be put into ‘laws’ in the West, it’s juts a question of time.
4/ Finally, linked to the subject above, if your “crime” is to expose the lies of the mainstream media/governments and broadcasting the truth (see Wikileaks and Julian Assange) and they decide that telling the truth is now a crime, then they can force VPN providers to release your personal details and logs to them (as if you were a pedophile or drug dealer).
The only real anonymity is offline or free, open source and publicly available services like free online VPN, proxies, TOR, Epic, Librewolf and common sense to be as anonymous as possible. Unless the VPN is yours and the relays are yours, I don’t see how you can retain your privacy.
Not quite, free VPNs typically log everything and sell your data for profit.
There are also anonymous payment options you can use.
Thank you, Sven.
How about three separate chained VPN provoders, instead of Tor? The first one on a portable router (such as the GL-iNet routers), the second one on the host operating system, and the third one on a Virtual Machine?
Hey Frank, that is an excellent idea and one I recommend for maximum anonymity.
NO! You can’t trust it at all!
1. Your internet provider (and your Government) is not happy when you are using Tor, and your ISP can report you to the authorities. Because TOR is often used for the access of: Dark Web, Onion Sites, Suspicious Websites, it’s often used by Hackers, Criminals, Child pornography criminals, illegal downloads, etc.
I think that, when you are using TOR, you are actually entering the network of all these internet parasits and criminals. You are actually using the same IP’s, the same cookies they are using, and you are exchanging that everything with them. I think it’s NOT good! 😉
2. TOR Browser is actually a Firefox browser with “NoScript” add on 🙂
(NoScript addon has Access to all browser tabs of TOR browser, It stores unlimited amount of client-side data, Has access to browser activity during navigation, Has access to your data for all websites etc.. Just read their permission conditions!)
You can notice very quickly that, TOR (Firefox) browser is NOT hardened and a LOT of security holes are just open. (Just open TOR Browser > URL bar > about:config and you can search for them there).
TOR (Firefox) uses java, geolocations, wifi scans, remote options, automatic downloads, ALL Google “safebrowsing” downloads, Telemetry pings, Normandy etc.. are just there! (I think that, Google and Firefox can each second download everything you do, what you visit etc.)
So, you have a lot of work, to harden TOR (firefox), to hide your device identity, your privacy and your internet behavior. Unless, you are so smart that you are using it only through, “Tor Over VPN” option. (NOT: “VPN Over Tor”!). In that case: your ISP can’t see that you are using Tor and your VPN provider cannot see what sites you visit or the contents of you connection. (But your VPN provider can still see dat you are using TOR ;))
3. REMEMBER: (I think) nowadays Internet Giants and governments are using: Remote Neural Monitoring, Brain Scanning, Synthetic Telepathy, Satelites, Artificial Intelligence, Brain Mapping, Smartphone Tracking technologies, A.I. Intrusion technologies etc.., They can read your thoughts )))
None of browsers can hide your identity!
My advice to you: Don’t attract unnecessary attention by using Tor browser. Because, if they want to find you, they will do it very quickly, wherever you are, does not matter which browser or operating system you are using!
Have fun!
>TOR (Firefox) uses java, geolocations, wifi scans, remote options, automatic downloads, ALL Google “safebrowsing” downloads, Telemetry pings, Normandy etc.. are just there!
>wifi scans
Can you point me to this setting about “wifi scans”? Or are you talking about sandboxing Tor in a container, VM, AppArmor, Firejail etc?
The only settings that I think users should change is setting “Safest Security Level” and in
about:config
javascript.disabled=false
webgl.disabled=true
>does not matter which browser or operating system you are using!
Quit being a doomer, becoming aware of how things work and doing anything is better then nothing. One can dwell on “how bad things are” but if your not looking a ways to fix things then its just a waste of time. People should be critical and aware of times we are living in and threats to our Privacy from WEF types.
@Peace and Freedom You said “TOR Browser is actually a Firefox browser with “NoScript” add on” NO, it’s not. Most of the other stuff you said sounds like paranoid garbage. A browser CAN hide your identity, if your using a VPN with it.
You also said “They can read your thoughts ” That had me laughing !!! It sounds like you have no idea what your talking about. Maybe you should take up ping-pong, and let other people (who know what their doing) use the internet. 🙂
Have fun!
Former Tor user here, been using it for about a year and half. I will mention my observations so far with the Tor Browser Bundle (TBB), and the reason why I stopped using it.
1) My main selling point of Tor is that it allows browsing media outlets that are blocked by the government, and I found Tor doing fine against censorship.
2) Tor suffers from multiple sites blockage, especially the ones using Cloudflare and bot-checkers, by blocking the public Tor exit nodes. Around 95% from my browsing was fine, but not those 5%, like video conferencing platforms, Discord/Reddit, or even plain browser games.
3) Tor does not include any AD blocker, and installing uBlock will change the browser FP. This made surfing with it sometimes sluggish and bloated.
4) The Tor onion website has a strange issue, it will take you to the plain clearnet site if you change the domain (i.e. clicking community/blog/support links above). Minor, but gave me the impression of unprofessional site moderation given the huge funding of the project.
5) You will have no idea if the onion (darknet) sites have any trackers following/fingerprinting you that TBB NoScript doesn’t block, especially that TBB itself uses JavaScript by default, and I2P (another anonymity tech.) suffers from the same issue.
6) My ISP started blocking Tor after months of usage, which means I have no option but to use a bridge, and that I’m being suspected by the government for evading surveillance.
7) Tor gives you an entry guard node that does not change for 2/3 months. The problem is you don’t know whether they have any affiliation with the 14 Eyes governments, given that the entry node logs your IP every time you connect to the Tor network, same applies for bridges.
8) Tor will not tell you the jurisdiction of the entry node if you are using a bridge, and God knows what if it is actually an FBI computer, a German hacker, or some CCP data harvester…..
9) The non-changing entry node means your Tor circuit is not random by 33%, so I began suspecting Tor once I started inspecting the circuits it was making. Assuming same entry, you will always see mid/exit node patterns like these:
Germany -> Germany -> Internet
Germany -> Austria -> Internet
Netherlands -> Netherlands -> Internet
USA -> USA -> Internet
USA -> Germany -> Internet
Sweden -> USA -> Internet
Moldova -> Singapore -> Internet
14-Eyes -> 14 Eyes -> Internet
You figured it out, you only need to give the user a compromised bridge and an exit point operated by a friend, correlating the entry and exit traffic together, and you have a complete spying network that tracks high profile targets: https://nusenu.medium.com/is-kax17-performing-de-anonymization-attacks-against-tor-users-42e566defce8
I thank you for writing the article, it was very informative, and please update the Pando website links with web archive ones, they were also very helpful to better understand the whole background of the project.
Excellent analysis, thanks for sharing!
Have you even watched this?
https://www.youtube.com/watch?v=3CW-SzY_rCc
“2) Your login password is never transported in clear. At least on any website that is halfway decent secure. It is hashed in your browser and this hash is transported to the website and it compares it with what is stored in its database. This is called ‘Hashing’. Very simple but effective.”
This is wrong. Your password does get sent to the website, and then it gets hashed by the website, and then the website erases your password from memory. If the hash matches the hash stored in the database that was created when you originally signed up or when you last changed your password, then the website logs you in.
Your password still gets seen by the website, just that it doesn’t store it in the database, storing only the hash. This protects your password when the website’s database gets stolen, but not when the website’s been hacked to steal passwords, or when the website operators choose to save your password somewhere instead of just erasing it from memory.
Always use unique passwords.
I have read these and am thoroughly freaked out…
https://www.vice.com/en/article/jg84yy/data-brokers-netflow-data-team-cymru
https://www.vice.com/en/article/y3pnkw/us-military-bought-mass-monitoring-augury-team-cymru-browsing-email-data
https://gizmodo.com/ncis-whistleblower-military-data-broker-cymru-wyden-1849564984
https://thefreethoughtproject.com/the-state/us-military-has-a-mass-monitoring-tool-that-can-spy-on-93-of-all-internet-traffic-including-email-browser-data
Is there no privacy/anonymity left in the world???
I would like to know if there are any ways to defeat this kind of tracking? I previously like suggestions here on Restore Privacy to chain VPNs and use TOR (cautiously) but after reading these articles the picture seems bleak since Team Cymru has nodes all over the globe allowing correlation/timing attacks and even if VPN is truthful and doesn’t keep logs it doesn’t matter when you have your own collection nodes for what did it say 93% or 97% of the internet — and then on top of that a way to query such a vast amount of data?
Chaining VPNs like we describe here will make you very, very difficult to track and also thoroughly mix your traffic. Don’t give up hope. And remember that privacy is not all or nothing.
I have a thought experiment — if you lived in an oppressive country and were a dissident activist. One who organized protests, setup websites, chat with others, upload videos, this sort of thing – and your adversary potentially the likes of intelligence agencies who would like to find you. Could you have a paranoid but reasonable confidence that your efforts would keep you safe from jail/death??
What is meant by thoroughly mixing traffic? Do you mean VPN1 is UDP and VPN2 is TCP?
I understand not everyone will be in a situation like this, and hopefully not. But there are such places where it is david against Goliath and even if not the case we netizens should fight against spying with encryption – vpns – TOR and wherepossible vote to oust anti-privacy officials.
If an entity such as team cymru can see all this, would an intel agency not be able to say to them, who is using VPN1 to connect to VPN2 and to create website we don’t like or upload videos at this time? Oh yes, there is only 10 users on VPN IP 1 and 6 on VPN IP 2 — that may not be identification exactly but narrows down, no? I know you are also very busy, are there also resources that would lend to my understanding of how this is defeated? And not just for a person embarrassed on their web browsing or wanting to pirate movies. Thank you for the information and the website, truly.
Hi, I’d recommend checking out our Advanced Privacy Series to get into this topic more, particularly our article on
How to be Anonymous Online
You can distribute trust across different VPN providers and add as many as you want to the chain with either virtual machines or physical routers, or a combination of both. You can also mix in proxies and the Tor network if you want.
I agree that Tor is an extremely questionable option when used by itself. I, personally, wouldn’t use it at all. Having said that I know that Nord vpn offers a vpn/tor connection and I’m sure others do too. I think you have mentioned this in your vpn review guide. The main problem with daisy chaining vpn’s is that you need a fast high bandwidth connection to start with. Where I live that’s not a viable option. As I’m not overtly paranoid and I’m also not up to doing anything particularly nefarious, I’ll stick with the single vpn connection for the present time. Many thanks for the in depth Tor review and also your site in general.
“You are distributing trust between Tor and a VPN. The VPN could see your IP address and Tor could see your traffic (sites you visit), but neither would have both your IP address and browsing activities.”
Does this not infer that you need both a VPN and Tor for an entity to not know your IP address and your browsing activities?
From my understanding, one needs to have control over all 3 Tor nodes in order to know your IP and browsing activities. The guard does not know your browsing activities but it does know your real IP (assuming you don’t use a VPN). The opposite is true for the exit node.
This article is so informative and made me see things I’ve never even thought of. Please have my sincere gratitude, as you may have prevented many from falling into a potentially dangerous trap.
This website says boo Tor, woo Vpn.
http://www.privacyguides.org boo Vpn, woo Tor.
Who’s right?
PrivacyGuides recommend putting all your trust in Tor. I recommend distributing trust across with multiple VPNs and maybe Tor as well. PrivacyGuides can promote Tor all they want and that’s fine, but from an OPSEC standpoint, distributing trust is safer and more secure.
Thank you, Sven. What do you think of the setup: VPN_1 > Tor > VPN_2 ? Would that be better? It would probably take a lot of work to set up the VPN after the Tor connection.
I am afraid the answer is, boo Tor, boo Vpn. From what I have read, particularly from Edward Snowden, The spooks can easily decrypt VPN traffic.
Then why would governments work so hard to try to shut down “criminal VPNs” if they could “easily decrypt traffic”? Sorry your theory does not add up.
Example 1: https://www.europol.europa.eu/media-press/newsroom/news/coordinated-action-cuts-access-to-vpn-service-used-ransomware-groups
Example 2: https://torrentfreak.com/criminal-vpn-shut-down-by-europol-and-international-law-enforcement-220118/
You can’t just blindly believe on you vpn. ever thought that even strong vpns could leak your info. I personally use tor browser bundle. I also tried chaining vpn and tor but my vpn reported my tor usage to my local authorities and my tor usage was banned.😢😢
Tor like anything else has to be understood and evaluated against your threat model. And there can be bad actors running servers, but they do have ways to detect those and isolate them. I even ran some Tor servers and bridges in the past for years after the Snowden leaks and there is a huge amount of Tor traffic and Tor users, which also points out that there are many good people that contribute Tor servers and don’t try to snoop on users. And being an open source project, the code is out there to be audited and improved upon and past issues don’t represent the current state of the project. And the more issues exposed the better it is for the health of the project.
There were also logic errors in the write up, that Tor can’t be trusted but that the government supporting it trusts it for it’s operatives. And it’s far easier for a government to snoop/correlate the traffic in and out of a single VPN server than three (or six) servers spread around the world. There has also been a lot of consolidation of VPN providers, and one large group is run by a man linked to Israeli intelligence. So who is running other VPN providers? Who funded them? Money corrupts everything, so can you trust the auditors of those no log VPNs? And wouldn’t it be easy for intelligence agencies to infiltrate VPN servers even in secure facilities? Or just turn those operating them into assets by whatever means necessary. I find VPNs to be far scarier and more easily compromised than Tor though I do have a subscription to one.
Of course, I don’t have a financial relationship with a VPN provider to cloud my judgement.
OpenSSL was publicly audited whilst maintaining a critical vulnerability for 1.2 decades.
As for VPNs, you should look at how the start up was funded and then the rest of funding can simply be explained by paid subscriptions. A decent multi hop VPN + Tor at Safest mode should be pretty much foolproof, if you set VPN at router level and have no other networks saved then its pretty much impossible to leak since everything has to pass through a VPN before it reaches the internet.
Greetings!…
Sven, I’m a tad confused here!… this blog is dated December 14, 2021!… but, I am seeing comments from 2020 (and, including, a response to a comment made by YOU!)! And so, I’m wondering whether: you dated this a year late (but, which still doesn’t address comments made prior to December 14, 2020!); your “Time Stamp widget” is in need of a “tuneup”; or, some folks have been doing a bit of “time traveling”– and have replied to your blog from the past (but, which I find troubling, as this would suggest that you’re one of the “time travelers”… and that these– and including you!– would have made respective comments on an article [and, response to a website comment!] that was yet to be placed online!)!
And now, to the matter at hand…
~~~~~~~~~~~~~~~
The ONLY solution to this Tor dilemma, from my perspective– at least, unless, and until I can be convinced otherwise!– is GLOBALLY MANDATING (at least, by way of an international coalition of government signatories and Human Digital Rights and Human Rights Advocacies and Advocates– but, which may preclude the EFF!… BUT, ETC.!) the creation of a SINGLE STANDARD VPN, that/ which would be incorporated within ALL personal computing devices as a default software component of an operating system, and which would be GUARANTEED to be 100% secure against a breach of ENUMERATED Human Digital Rights/ Human Rights violations! And, if breached, such a violation would be met with both criminal and civil sanctions, as outlined within the legal framework established by the aforecited international coalition of government signatories.
Nevertheless, this solution has a built-in conflict of interest for most governments (a “cyber catch-22”):… GUARANTEEING 100% security against breaches of webizens’ ENUMERATED Human Digital Rights and Human Rights, while– all the while!– desiring to systemat(icly) breach every single Human Digital Right and Human Right known to man, as a default response to “Intelligence” Agencies’ perceived and “substantive” “Intelligence imperatives”! And… when a group like the EFF gives every indication of being a hapless– or willing!– conspirator to “governmental duplicity (in the GUISE of being a ‘friend’ to those who are in true need of online cyber security!)”, it begs the question: Who is defending whom?… and must webizens take matters into their own hands? And: Could “cyber vigilantism” result in outright attacks against network and ENEMY servers, that even RIGHTEOUSLY AGGRIEVED citizens/ webizens believe are being used to attack Human Digital Rights and Human Rights… and democracy?
Frankly, I believe that governances (at least!) are in for some rough times in the very near future… as these have placed themselves in a very compromising position and light, and have cast themselves– inadvertently, or deliberately!– as friends to ICT corporate and “right-wing”/ facist interests, and have wholly undermined the sacred trust of those these have FEIGNED service to… exchanging social cyber egalitarianism with a HYPOCRIT(IC) CYN(IC) DELUSIONAL AND PARANOID MYOPIA that’s rooted in the PARADOX(IC) Laissez-faire philosophy, “I’M ALL RIGHT, JACK (but– and, apparently!– only when ‘Jack’s’ corporate and metexistential economic interests are not being interfered with!… otherwise, MR LAISSEZ-FAIRE [a.k.a., FACIST JACK!] is not a, ‘happy camper’!… and must attack EXCESSIVE GOVERNANCE– while being excessive with, and to those who have challenged ‘HIS ECONOMY [and by way of his, *EMBEDDED ALGORITHMIC PEEPS*!]’!)!
To close…
I note with interest, that Microsoft (whose Operating System I’ve been using for decades… in conjunction with the TorProject’s Browser!) now has Operational Control of the Github Platform (see, https://www.wired.com/story/microsoft-github-code-moderation/… a “go-to-source” for everything Tor related… but, a veritable CONFLICT OF INTEREST in the light of the “backdoor breach revelations” provided by Edward Snowden and Julian Assange against Microsoft [see, https://wikileaks.org/ciav7p1/ and https://www.independent.co.uk/news/edward-snowden-claims-microsoft-collaborated-nsa-and-fbi-allow-access-user-data-8705755.html%5D)… and in apparent contrast to Tor’s proffered Human ICT Rights Protecting tome! So I ask you: “What would possess a self-professing defender of Human ICT Rights to allow it’s̲ go-to-source for everything Tor to be bought out by a group that the wisest of it’s̲ wannabe/ would-be followers and supporters suspect has been– and, suspect continues to be!– in breach of the very Human ICT Rights that it claims to uphold?”… and also: “What portion of the $7.5 billion given out by Microsoft for Github, has– in fact!– come by way of any number ANTI HUMAN ICT RIGHTS STAKEHOLDERS (e.g., the U.S. Government’s Agencies [‘Intelligent’ or otherwise!], and Corporate ICT Interests… but, etc.!), that/ which seek to undermine/ undo the FOS community’s decades of FOS app developments through MS’ new ‘cyber dogchain’ around github’s neck?” And don’t forget what Bill said re Linux: “It’s easier for our software to compete with Linux when there’s piracy than when there is not.”… nor, what Stallman said about Microsoft: “Today’s Microsoft is a megacorporation with thousands of patents. MS said in court that the main competition for MS Windows is ‘Linux’… meaning, the free software GNU/Linux operating system. Leaked internal documents say that Microsoft aims to use software patents to stop the development of GNU/Linux.” (See, bit.ly/3HbtdAA)
Well, folks… it appears that Microsoft may have found another way of stopping the development of GNU/Linux… other, than through patents.
As for those who might contend that my observations verge on hysteria and hyperbole, I’d simply offer that Wired, Independent, WikiLeaks and WIKIPEDIA are but a small fraction of the webizen community that/ which have made significant contributions to the reporting of Cyber Security threats!… and truths! (See, bit.ly/3pKz6ir)
Millions of Windows 7 users of the most popular OS in history (and, used by millions even today!) are to find that their last NON-LICENSING OS will be denied support, and may be subject to even greater cyber security threats than those currently faced! And even more REAL than the cost-burden of moving to “better” Microsoft products (especially, for those in 3rd-world countries!), is the built-in THREAT of Microsoft’s Constitutional and UDHR Human Digital Rights breaching (and hence, Human Rights breaching!) “licensing agreement”/ EXTORTIONWARE-RANSOMWARE, that flies in the face of every Cyber Rights tenet that cyber advocates and advocacies have been fighting to uphold since the introduction of the first home PC, and the “advent” of the Internet! And, is but a new believed dodgeproof method to implement the same “backdoor” cyber breaches of users’ security on behalf of the same colluding Corporate ICT and “Intelligence” Agency interests that were the security concerns of Edward Snowden, and Julian Assange (see, bit-tech.net/news/tech/software/snowden-backdoors/1/ and vault 7 – wikipedia)– and inasmuch, as thoughtless saps have “agreed” to sign-on to MS’ EXTORTIONWARE-RANSOMWARE ruse (and therewith, have transferred their “Cyber Security Agency” over to MS [and to MS’ partners!], turned their “PC”, information and data into borrowed “playthings” to be manipulated at the whim of MS and it’s̲ partners [e.g., organized criminals in control of “legitimized” “adult” porn being viewed by preteens– under the “watchful eye” and “colluding wink” of our “Intelligence” Agencies!] and transformed their “Internet Neutrality experience” into an SEME-based and S̲E̲O̲ME-based “Corporate frivolity experience”! And it’s a cyber version of coerced COVID19 vaxes– or one doesn’t get to “share” in society and in an Internet that nobody is supposed to own! And Gates is behind the “Covert License Vax (beginning with the introduction of MS’ ‘thin [Edge] of the wedge’ browser!)”, the “Covvax” and the “St̲r̲u̲m̲p̲ettavax (implemented– so said!– with a hand over the mouth… accompanied by muffled yelps!)”/ “Covert MAXvax”!
Question: was Andrew’s “out-of-court” a “Seal” on Billy’s and PHEWTUS’ “haircombing involvement (the which, Billy and PHEWTUS would gladly fund to keep ‘Sealed’!)”… and will “Max” live to tell her, “yet to be revealed tale”– as a “counter desealing fund offer” and “officially penned early release offer” may pose a real threat to Billy and to PHEWTUS (or, to PHEWTUS’ “WHITE House Fixers”, who want “their boy” back on his “high horse [at least, somewhere near the rump!]”– and, “pure”!)?
Windows messed up! And I– among millions!– will never be a part of the post Windows 7 “Microsoft experience”!… as I– among millions!– will never agree to become a “LICENSEE” to ANY “CORPORATE CYBER DARTH VADERS”!… and including “Adam and Steve’s” and Slytherin’s, “Apple” products! These can put their “Licensing Agreements”/ EXTORTIONWARE-RANSOMWARE and HUMAN RIGHTS BREACHING/ HUMAN DIGITAL RIGHTS BREACHING “Privacy/ Policy Statements” where our sun doesn’t shine!
Windows 7 was the best product MS ever produced… and which should have led to 7.1, 7.2, and etc.!… but, embedded “Intelligence” had other ideas, and GUN/Linux was keeping Bill up at night. But, even IF Microsoft had moved closer to GNU/Linux (to FOSS) in it’s̲ OS design, and had removed it’s̲ adoption of EXTORTIONWARE-RANSOMWARE, we are still met with a currently insurmountable systemic problem imposed by our network, honeypot, search engine and ISP “CYBER GEHEIME STAATSPOLIZEI”…
As I have conveyed frankly elsewhere, NONE of our global search engines are doing what they’re supposed to be doing! And in the light of the concerns expressed by Dr. Robert Epstein/ et al, who has/ have provided us with some damning accounts of SEME… and, regarding what I’ve termed, SEOME!… I am AMAZED that our cyber advocates and advocacies haven’t banded together to eradicate these BLATANT EVILS that are right under our noses!
To make a much longer tale shorter, SEME adds up to the outright CIRCUMVENTION of our searches online, by “stacking the algorithmic deck” in terms what gets answered, and to what degree… and by search engines such as Google! And throw in SEME’s dirty cousin, “Search Engine Optimization (the paying of ‘algorithmic hitmen’ to place one’s website at the top of the search engine ‘cyber bird pecking order’!)”… and what I’ve termed, the “search Engine Optimization Manipulation Effect”!… you have the recipe for the wholesale manipulation of Free Speech and Freedom of the Press (but, ETC.!)!
In other words, would a proper application of Software Forensics… of both the software being used by search engines, and network software!… reveal an unimaginable daily degree of Human Rights and Human ICT Rights abuses (whether digital, analog[l] or a hybrid of the two)! And if such were to be found, what would– should!– our REASONABLE RESPONSE be?
People!… if your search engine results are “algorithm(icly) rigged” before your search leaves the address bar gate (e.g., your “cyber horse”/ “cyber truth” has been “cyber drugged”/ “cyber hamstrung”… depending on the “revealing nature” of your search!), then wherein is there an UNFETTERED EVOLUTION of the Internet– LET ALONE, an UNFETTERED EVOLUTION of society? And “results”, which have been prepared in advance (by server selection and manipulation, network and ISP “Throttling”, “flagging, tagging, bagging and gagging” webizen expressions and sites by way of “UNACCOUNTABLE NET-NON-OWNER WANNABE AND WOULD-BE NET OWNERS” and, SEME and SEOME… but, ETC.!) before you’ve even asked the SOCIALLY RELEVANT QUESTION! And willfully being DELUDED, says what about one’s state of mind?
Search engines (in particular) are our MAIN GATEWAY to our CYBER OZ!… to the tip of the “web iceberg (the dark web, making up the largest aspect of the web)”… and if wannabe WIZARDS are “blowing cyber smoke” and “pulling cyber curtain strings”, then our choices may be but an ILLUSION! That is BAD!… VERY BAD!
And, if our logical, sound, peer-acknowledged and accepted and “intuitively expected” results are continually met with, “No such search results”, you then have to ask yourself: “Are there REALLY, ‘No such search results’?… or, am I– and millions of other would-be conscionable and responsible networked souls!– being ‘sold a bill of goods’? And are we to accept that our intuited (but, experienced!) hunches are but the DELUDED MUSINGS of “FRINGE WEBIZENS” who are ‘out of the loop’ in comparison with said more ‘l-e-a-r-n-e-d m-e-m-b-e-r-s’ of the ‘INSIDER CYBER CROWD CLUB’?”
You– and your’s– are free to believe that the search results you receive are accurate, “non-caballed” and ALL THAT THERE IS TO BE RECEIVED!… and that’s your Right as a “Free” citizen! But, truth be told, our information and data are off (e.g., on the origin of COVID19!… let alone, the use of vaccines to treat it!), our cabals are increasing by the day (and especially, within ICT… and beyond the unspecified cabals cited by pundits throughout the Net!) and, one only need compare the sum of search results received from any given search engine to the estimated total number of “REVEALED” sites making up the Net (excluding, of course, those on the Dark Web, on Paranets and on Intranets!), to get but a tiny GLIMPS of the amount of search results being “FILTERED OUT” of existence by way of our “NET-NON-OWNER” Corporate ICT and colluding wannabe and would-be “Stakeholder Interests”! But, the EVILS with these chaps behind our search engines are FAR WORSE, and not protected through Tor!…
If you wish to efficiently and effectively address the impact that Corporate ICT generated porn has had, and is having on our children (and not just on society!), you would do well to consider the role that our search engines have had, and are having in facilitating this “GROOMWARE”… an impact, that ICT players like MS, Apple and Google could have easily mitigated– AND, CAN MITIGATE NOW! And the following is a case in point…
I wanted to offer DuckDuckGo.ONION “Feedback” concerning images that appeared under their “Images”, of naked men and women having intercourse amid the pictures of the late Dr. James Fraser Mustard, and children at play (late Dr. Mustard, a pioneer MD in Early childhood Development, and heart surgeon)… but, a popup demanded that I receive a “DOWNLOAD” before the Feedback message could be sent! My guess then, was that DDGOO was no longer allowing me to send them messages concerning the CRAP that they often displayed when using Images, re REASONABLE SEARCHES made by way of their said “search engine”! In other words, I was to “ENJOY” being VISUALLY ASSAULTED in one’s use of DDGOO!… AND I MUST, “LEARN TO LOVE IT”!… or we (i.e., DDGOO!)– if one complains!– will “F you up” with a “THROBBING CYBER DOWNLOAD (so to speak!… like those used to gag young ‘rape complainers’!), so that any future “yelps” will be “circumvented” through our “Weinstein-Epstein-like” “KNOBWARE PACKAGE DOWNLOAD”! Incidentally, the search that was made included the combined expressions, Betty Mustard and Fraser Mustard (Betty, being his late wife). And this forced FLASH VIEWING is in contrast to the “Network” filtering… with the aid of colluding search engines and ISPs… of “flagged, tagged, bagged and gagged” search expressions and sites that certain “NET-NON-OWNER” Corporate ICT and wannabe and would-be “Stakeholder Interests” have DECREED shall not be expressed, or accessed– WHILE, giving deference to expressions and websites that/ which are HYPOCRIT(ICLY) in stark contrast to their “PUBLIC FACE”!
Simply, despite Safe Search being OFF, this shouldn’t translate to an image of a sexual nature… UNLESS, an associated phrase is found within the string one is using within DDGOO’s search bar! And as this wasn’t so in my case, I wanted to express– AGAIN!– my views about the images that were added to my search results THAT SHOULD NOT HAVE INCLUDED IMAGES OF NAKED FOLK, OR ANYTHING HAVING TO DO WITH SEX!… AS SEX WASN’T A PART OF MY SEARCH STRING! And YES, I am saying that DDGOO’S “PRINCIPALS” have MUCH in common with Harvey Weinstein and Epstein!… and that the “Safe Search Off Default”, CANNOT– AND MUST NOT!– BREACH OUR DIGITAL HUMAN RIGHTS, AND COMMON DECENCY! MY SEARCH EXPRESSIONS QUALIFY “SAFE SEARCH OFF”!… AND “SAFE SEARCH OFF” DOESN’T JUSTIFY IMPOSING “WEINSTEIN-EPSTEIN-LIKE” SEARCH RESULTS NOT INCLUDED IN MY SEARCH EXPRESSIONS! AND AS “SAFE SEARCH OFF” ALLOWS FOR INFORMATION AND DATA THAT/ WHICH MAY NOT BE AVAILABLE THROUGH DDGOO’S “MODERATE” AND “STRICT” SETTINGS (AND BY WAY OF GRAPHS AND CHARTS THAT/ WHICH CAN ONLY BE FOUND UNDER “IMAGES”!), WHY SHOULD A USER BE ABUSED BY DDGOO FOR INVOKING A SETTING THAT AFFORDS INFORMATION AND DATA THAT/ WHICH MAY OTHERWISE NOT BE AVAILABLE! NONETHELESS!… NON-IMAGE-BASED ALPHANUMERIC SEARCH RESULTS ARE LIKEWISE AFFECTED! AND WHY WOULD ANY “RATIONAL” PRINCIPLES AND/ OR EMPLOYEES OF A SEARCH ENGINE NOT GET THE, “MORAL MEMO”?… UNLESS, AND OF COURSE, THE PRINCIPLES/ EMPLOYEES OF OUR SEARCH ENGINES HAVE BEEN “ORDERED” BY THEIR “TRUE BOSSES” TO IMPLEMENT A CAMPAIGN AND PRACTICE OF GOOD, “CYBER HAIRCOMBING”!… O-R E-L-S-E!
Nevertheless!… the ability of ALL Corporate ICT Players to address the ASSAULTS on webizens has been, and is EVER PRESENT!… and Operating System OEMs have as much power to address what’s in network play as any other ICT Player! And more so, because OSs make the connections happen, and “manage” the incoming information and data!
And so and thus, Microsoft, Apple and Google have no excuse!… but then, nor do countless other ICT Players who are also feigning indignation over the Net’s state of affairs– while, benefitting!
All the Best!… and may God Bless!
P.S.:…
BTW, Sven!… it would be interesting to get your take on the viability of Gnunet.org (i.e., in a dedicated future blog!)!… and whether we need yet another “new and improved” version of the Net beyond even this!
Hello, in regards to your question on the publish date, I try to regularly update all the content on this website based on changes, new information, etc. So the date at the top of the page reflects the latest date the article was updated. I leave the comments as they are because they add value, even if they are older than the date the article was last updated.
While you seem to have a very well thought out opinion, grounded mostly in fact rather than fiction, I’d suggest you look up the Constitution and the Federalist Papers. The Constitution does not protect us against each each other. It protects us from the government by explaining SOME of our rights as humans. The Federalist Papers explain the reasoning of the founding fathers. The Constitution was never intended to be a shield or sword wielded by citizens against each other. It was meant to protect against Government.
Federal, State and Local laws and such protect us each each other. Not the Constitution. While all humans have the right to privacy against the government and other citizens, I believe you give up your right to privacy when you choose to use the product of a company. Absent protection from this by government regulations or laws/ordinances, Microsoft has the right to demand anything it wants from you in exchange for allowing you to use their products.
It’s sleazy and completely immoral to force people to give up their rights, all the while Microsoft and others are crying and whining about violations of their rights in court. That doesn’t mean it is illegal or Unconstitutional.
Greetings!…
The Federalist Papers ARE NOT LAW!… they are ESSAYS expressing OPINIONS about a proposed Constitutional framework for the patrons of America, and how this framework could be interpreted (albeit, ESSAY OPINIONS from contributors to this framework). Had all or part of these papers been added as a LEGAL PREAMBLE to the proposed U.S. Constitution, then there’d be no question as to their legitimacy as an OFFICIAL GUIDE re Constitutional interpretation and re the scope of each and every provision to be included in the proposed document… but, these were not included (nor a distilled version of same), because there was an unspoken fear that to do so, would compel entrenched opposition to this, that and the other before the document could be ratified– and because, a FORMAL LEGAL PREAMBLE is no longer a matter of public debate, but a course of legislated action that must either win, or fail. And so, to move the debate into the public arena… and away from the prospect of having the document socially shredded by amassed dissent!… is to invite proactive discourse on ESSAY OPINIONS about a proposed Constitutional proposal, while– all the while– document designers were “feeling the pulses” of “America’s patients” to gauge whether their “designer bedside manners” were either an assist to the document’s ratification, or but blunders that/ which needed further “treatment” before passage could be effected. In my opinion, it was an unfortunate– but necessary– tact(ic) move… but, the drawback, was that the courts would be without an OFFICIAL GUIDE with which to aver DEFINITIVE yeas or nays re issues of Constitutional interpretation and provisional scope… and must either “pull rabbits out of hats”, or give deference to the “Federalist Papers”. And that, became an ongoing Judicial dilemma…
“The amount of deference that should be given to The Federalist Papers in constitutional interpretation has always been somewhat controversial. As early as 1819, Chief Justice John Marshall noted in the famous case McCulloch v. Maryland, that ‘the OPINIONS expressed by the authors of that work have been justly SUPPOSED to be entitled to great respect in expounding the Constitution. No tribute can be paid to them WHICH EXCEEDS THEIR MERIT; but in applying their opinions to the cases which may arise in the progress of our government, a RIGHT TO JUDGE of their correctness must be retained.’ In a letter to Thomas Ritchie in 1821, James Madison stated of the Constitution that ‘the LEGITIMATE MEANING of the Instrument must be derived from THE TEXT ITSELF; or if a key is to be sought elsewhere, it must BE NOT IN THE OPINIONS OR INTENTIONS OF THE BODY WHICH PLANNED & PROPOSED THE CONSTITUTION, but in the sense ATTACHED TO IT by the people in their respective State Conventions where it RECD. ALL THE AUTHORITY which it possesses.'” – The Federalist Papers, Wikipedia (see, Judicial use) (Note: the bold lettering is my emphasis.)
Nevertheless!… and on a positive note!… now that the American Constitution is in place, all that Americans need do (through their Representatives!) is to ratify a Constitutional Amendment that would entrench all or part of a distilled rendition of the Federalist Papers in a FORMAL LEGAL PREAMBLE, and/ or script a further FORMAL LEGAL PREAMBLE.
Reader, despite the cited SEPARATION OF RELIGION AND STATE within the enumerated Sections of the U.S. Constitution, most of us acquainted with the “textual evolution/ contextual evolution” of this document are familiar with yet other opinions of the “founding fathers” that/ which aver a God-centric basis for the document’s manifest existence– and yea, CITE BIBL(IC) PROPHECY. And if this basis be true, then what can we make of– what must we make of!– the following bibl(ic) quotes…
In the New Testament’s Book of Romans Chapter 13: 1 and 2, we read the following:…
1) Let everyone be subject to the governing authorities, for there is no authority except that which God has established. The authorities that exist have been established by God. 2) Consequently, whoever rebels against the authority is rebelling against what God has instituted, and those who do so will bring judgment on themselves. [NIV]
(ATTENTION: IF THE FOREGOING BE TRUE, THEN HITLER’S AUTHORITY AND GOVERNANCE WAS PERMITTED BY GOD, AS EXPLAINED IN THE STORY OF JONAH, AND THE CONVERSION OF NINEVEH.)
In the New Testament’s Book of Mark Chapter 3: 23 to 27, we read the following:…
23) So Jesus called them over to him and began to speak to them in parables: “How can Satan drive out Satan? 24) If a kingdom is divided against itself, that kingdom cannot stand. 25) If a house is divided against itself, that house cannot stand. 26) And if Satan opposes himself and is divided, he cannot stand; his end has come. 27) In fact, no one can enter a strong man’s house without first tying him up. Then he can plunder the strong man’s house…” [NIV]
To the matter… for TRUE Christians, it is clear that we are to be subject to that which is in authority. But, it’s also clear, that the PARAMOUNT AUTHORITY within a democratic country– at least!– is a country’s God-allowed respective national constitution!… and which– invariably!– contains Rights and Freedoms (e.g., Freedom of Expression, Freedom of the Press and Security of the Person… BUT, ET CETERA!). And, to resist such… and in keeping with Romans 13: 1 and 2!… IS TO RESIST THE CONSTITUTIONAL RIGHTS AND FREEDOMS GRANTED TO A COUNTRY’S PEOPLE THROUGH GOD’S PARAMOUNT AUTHORITY; AND THEREBY, TO RESIST GOD AND HIS HOLY SPIRIT! And in addition to the PARAMOUNT AUTHORITY of our national constitutions, is the PARAMOUNT AUTHORITY of the Universal Declaration of Human Rights (UDHR)… the signatories to which, are available for all too see.
And reader… and if I may!… let me offer up juxtaposed analogous “relevant arguments” and translations of Christ’s words conveyed in Mark 3…
1) How can Constitutional Paramountcy drive out Constitutional Paramountcy? 2) If a Constitution’s words be RELATIVE, NON-DEFINITIVE, INCONSISTENT, SELF-CONTRADICTORY AND NON-INTEROPERABLE in the context of it’s̲ entirety, that Constitution can’t stand. 3) If a Government is divided against itself, that Government can’t stand. 4) If a President opposes one’s self and is divided, such a soul can’t stand; that soul’s end has come. 5) In truth, no one can defeat a strong philosophy’s premise without first binding it’s̲ premise, or premises. Then one can defeat the strong philosophy’s premise, or premises.”
To close… in keeping with the PREREQUISITE NON-RELATIVE, DEFINITIVE, CONSISTENT, NON-SELF-CONTRADICTORY AND INTEROPERABLE expressivity demanded of a Constitution, a Constitution that cannot aver EQUAL PROTECTIONS AND BENEFITS to ALL citizens within the scope of it’s̲ mandate, is based upon a RELATIVE, NON-DEFINITIVE, INCONSISTENT, SELF-CONTRADICTORY AND NON-INTEROPERABLE premise, or set of premises… and so and thus, if local and state-wide interpretations of the scope of EQUAL PROTECTIONS AND BENEFITS D-E-L-I-M-I-T-S EQUAL PROTECTIONS AND BENEFITS, and the Constitution– in truth!– supports such a delimitation, then that Constitution’s premise or premises are faulty, and EQUAL PROTECTIONS AND BENEFITS can never be achieved; and thus, CONSTITUTIONAL PARAMOUNTCY is but RUSEFUL deference to LOCAL AND STATE-WIDE DIVISIONS!
As for the PARAMOUNTCY of wannabe and would-be Corporate ICT stakeholders, we don’t have a “KERDOCRACY” anywhere in the world, nor is it sanctioned through scripture.
I would not recommend the Brave Browser anymore…i was a huge fan of that pice of Software until i realised the Security Issues in it.
Brave has a HUGE History of Security Flaws.
For further reading:
https://thehackernews.com/2021/02/privacy-bug-in-brave-browser-exposes.html?m=1
Is it true that even if you use a VPN or Tor on a android phone all your actions are recorded into “logcats”? So google has all your actions stored anyway and can give them to thirdparties? I got curious about the darkweb from youtube and decided to go snooping around and ended up downloading a few things and went to drug sites although I did not buy anything. But now I have learned that this will always be connected to me and I am worried about this.
I know Im responding to my own comment here but I also wanted to thank you for writing this whole article. This is very insightful and obviously took alot of time and research. It was well written and interesting to read even for me Im not a big computer guy.
I’ve always been critical of Tor since its inception. The ability to access Onion sites sounds cool and all but most of those links are dead, Tor is selfdom rarely used by free speech activists to access legitimate websites. Nor is it practical since most sites are protected by Cloudflare and require Javascript to load sites up. On top of that its slow, and as Sven mentioned, you can be monitored or compromised by bad actors at any given moment since you don’t know whose operating the Tor servers.
Tor simply can’t compete with VPNS at the moment. It might be a slightly better option than using free VPNS but that’s not saying much. Paid VPN providers with the right audits done on them is simply the way to go. They might not be a 100% bulletproof requiring privacy, and speed but HTTPS already has you takened care of since your VPN/Internet Service Provider cannot see your individual activities beyond the Home URL you are in.
Solid article by Sven Taylor. Hope more see it to wake themselves up from the lies promoted by the Tor team.
My Timeline: (I’ll be shocked if this is not instantly deleted or even makes it here)
– I met once a year with several others I networked around the world with to basically prove each other wrong and ultimately learned from each other. Most were from Europe, with several Oxford grads who wrote compilers for Borland, two from the US and one from Australia.
– Two years before 9/11, a businessman and friend who we all knew wanted us guys to work for a new startup to collect data about companies that they would then sell. The businessman said to me, “It is a great opportunity and it will make you a rich man in a few years.” The guy in charge at the new company had architected what the Police use. When interviewed, they led me around and showed me a large data center in the building and I noticed the provider was Southern Bell. I asked and they said they use so much bandwidth the phone company decided to just move the central office of the area there. That didn’t make sense to me. They made a peculiar comment that they liked it that I was a military pilot and they liked pilots, which also made no sense. I saw three guys dumping traffic and asked what they were doing. The answer was, “Defending against hackers trying to get at our information.”. What also didn’t make sense is what they said I would be doing was too simple to hire someone like me for. It would be like watching paint dry for me. One of the guys they had already hired said, “I’m looking forward to working with you. Isn’t this amazing for only 4 months old?” Exactly what I was thinking. While the guy courting me was very wealthy, he was not this wealthy. This didn’t make sense. For $60 I could buy CD’s from Microsoft with a lot of business information and there is Dunn&Bradstreet. I had a great job as CIO of a Tier-1 Automotive supplier, paid well, great family area, could do what I wanted, set my own hours, and I had weekends off except during major upgrades of my own doing. I refused. Some time later, I started receiving peculiar phone calls from attorneys asking me vague questions and insisting I knew a lot more than I did. I relayed that to the guy who wanted me to work with them and I never heard from him again.
– A few years after 9/11 I’m in a conversation with a guy I knew who had worked directly for the guy who was on the board that courted me. He had closer ties personally with the guys but was not one of us. I mentioned the reason I refused was things didn’t make sense and also the peculiar calls from attorneys. At that point he told me it was a front company for the government to monitor people’s conversations. This was 2+ years before the Patriot Act. I also learned that they perform drone strikes from down there, which might be why the strange comment about me having been a military pilot. The story from him was the peculiar calls were because the guy in charge turned out to be a crook. Of the guys hired, the guy from Australia and the girl from Germany found out their goals were the same and both left. They got married and still got to stay in the US and are now citizens. As I recall from the last conversation, baby #11 was on the way, and they were homeschooling. They both work as contractors for the guy telling me all of this stuff. The remainder immediately ended up at LexisNexis, which is noteworthy, because if you need an accident report, this is where the police send you, and is the brain child of the guy I would have been working for. I know the character of the one who left with the girl from Germany and another in the group who was also a pastor, which might make sense of the move to LexisNexis. They were there for a long time but no longer there and seem to be bought and sold as a group in which they are each shareholders, of which I’m guessing the businessman is among them. The place that wanted to hire me has since morphed into an organization for healthcare support, which fits perfectly with what had been the businessman’s main money maker.
– As you might imagine, the Snowden saga is a different read for me. On the one hand I understand the government’s interest to protect its citizens. On the other hand, when Snowden was hired, he would have had to have been sworn to secrecy before knowing the scope of what it entailed. The verdict of what he did afterward can swap in your mind daily. If you read the official story of the Julian Assange case, and what they claim to be his maladies, it doesn’t add up. Both could release extremely damaging information to national security but AFAIK neither has yet.
– Days ago I decided to test my VPN that had been recently purchased by Kape Technlogies like my last one was. I picked a far away country and determined it was actually exiting a server in New York. I published several places on YouTube how to duplicate what I had done and it is deleted immediately.
– Today, I hate technology and am getting out of it and will plead ignorance. I wished I’d never gotten into it. My concern is not that they are collecting everything, it is you cannot trust those entrusted to safeguard us and work for the good of its citizens. Some examples are the IRS targeting certain groups by not only denying their rights, they gave their customer lists to their competition who are their supporters, and then pled the 5th. Then there was the Trump investigation fiasco where we saw attempted entrapment and obtaining telephone records with no warrant of any kind, which were never presented, so apparently worked against the narrative. Assange’s comments at his hearing are worth noting, “I don’t understand how this is equitable. This superpower had 10 years to prepare for this case and I can’t access my writings. It’s very difficult where I am to do anything but these people have unlimited resources. They are saying journalists and whistleblowers are enemies of the people. They have unfair advantages dealing with documents. They know the interior of my life with my psychologist. They steal my children’s DNA. (which was proven) This is not equitable what is happening here.” Others have plea bargained under these circumstances even when innocent because there was no prospect that justice would prevail.
I find all of this interesting as a person who has always felt we were never truly free or even valued since a child. I had a feeling everything was fabricated, and even as a child I could sense that what we are exposed to on a daily basis, is what “they” chose for us to be exposed to. Maybe I am going insane – or is that what the controlling people(s) want me to think? As I age, I realize that the powers of the world are of the darkest of the “world”. Yet, they are the most protected. Also, like Bill Gates, Mark Zucky, etc., are used by the “government(s)” or whatever (and vice versa), and operate under no laws. As you’re reading this it might not make sense, but that is partly because I am confused to be honest. I have all of these jumbled thoughts about the true hierarchy of the world, or how we are all preached that the government and POTUS are “Here to help!”, is a complete lie, because they are all so interested in self and party-affiliated gains, or maybe that isn’t even the case, I truly don’t know, BUT NOTHING SEEMS RIGHT.
That’s all I have for now,
Hope you are well
I’m a bit confused. If people can so easily be identified when using Tor, why would any goverment agent use it? It’s not like other goverments wont know of US’ usage of Tor for agency purposes and would of course put resources into unmasking them, finding security holes etc. Wouldn’t this place them at the same risk as anyone else using Tor?
Very good point Per. If tor was that bad at anonymizing spooks wouldn’t use it. But it’s true that the more people use it the more anonymous everybody is (including spooks).
There are other browsers out there, one is Epic which comes with integrated VPN with Ip adresses from different countries (USA, UK, France, Germany, Singapore) and integrated encryption.
Brave is alos presnted as some kind of privacy respecting tool, but it’s not, they even have a Tor button allowing it to connect to Tor nodes (basic ones).
VPN might be the solution BUT, as soon as you pay for something, you’re not anonymous anymore (bitcoin has never been anonymous), and your email adress even if it’s an assumed one reveals your real Ip adress to your VPN provider who will give you to government agencies if he has to.
To be safe is to be like Afghan resistance (they kicked the US out), using zero technology.