
Do you believe what your VPN says about its logging policies?
Be careful.
A recent court case in Massachusetts has once again proven that some VPN services with “zero log” policies are indeed keeping logs and handing this information over to authorities.
In this guide we’ll examine the recent case and other examples to illustrate what’s going on and how you can protect yourself.
Here’s what you need to know.
Law enforcement vs “no logs”
PureVPN was recently caught red-handed.
The Department of Justice just published a complaint involving a cyberstalking case. The case involved a US resident who was allegedly stalking and harassing people while using PureVPN.
The relevant section of the complaint appears at the bottom of page 22:
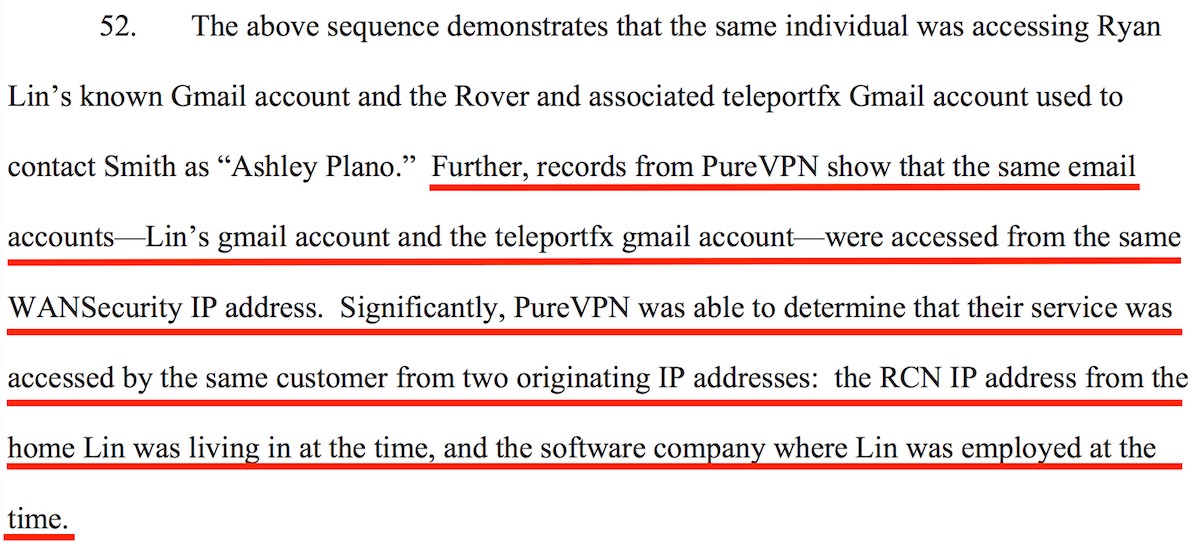
While it is difficult to determine exactly what details these “records” (logs) contained, it is clear that enough information was provided for law enforcement officials arrest the PureVPN user on cyberstalking charges.
The FBI complaint above clearly appears to contradict the PureVPN privacy policy – notably this section here:
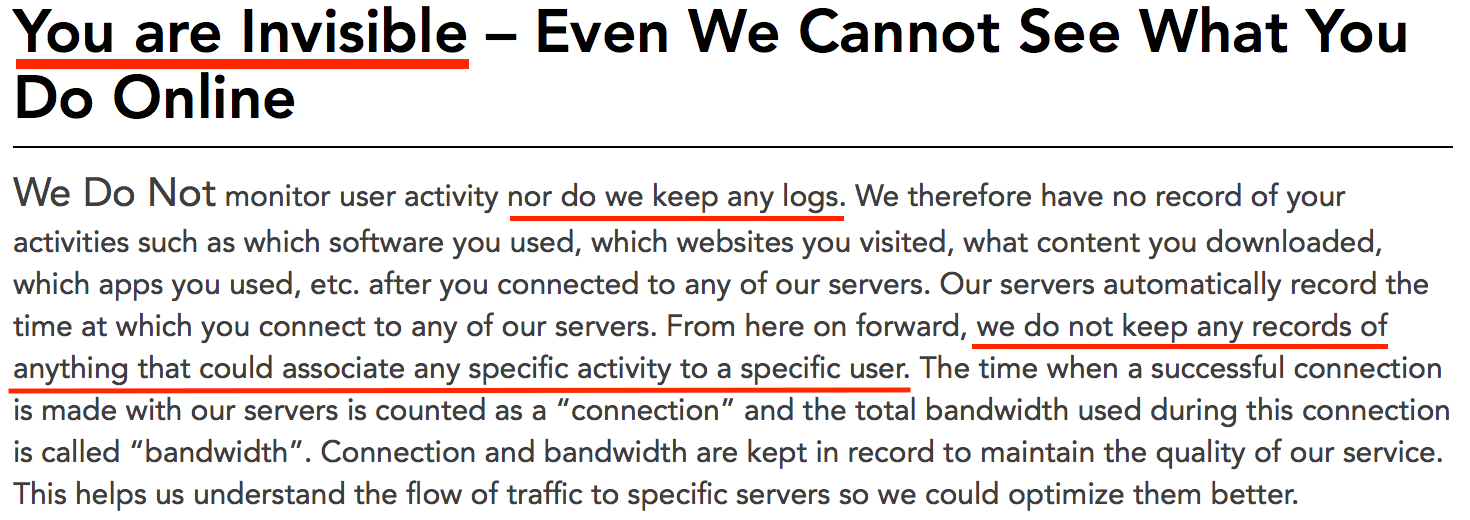
But this isn’t the first time law enforcement agencies have rained on the “no logs” VPN party.
Take, for example, the case of HideMyAss.
According to Invisibler, Hide My Ass VPN, the UK-based VPN service, appears to have cooperated with US authorities in handing over logs in a hacking case. This led to the arrest of a hacker in what is known as the “LulzSec fiasco”.
There are likely more examples that we will never know about where VPNs have handed over customer data (logs) to authorities.
Contradictory “no logs” claims
Further adding to the confusion is that there is no standard definition of “logs” or “no logs” used across the VPN industry. As you will see below, many VPNs come up with their own convoluted definitions.
Here are two examples where the marketing claims seem to contradict the privacy policies.
Example 1: Betternet

Betternet privacy policy:
Betternet may collect the connection times to our Service and the total amount of data transferred per day… Betternet uses third-parties (the “Third Party”) for advertisement. Third Party may use technologies to access some data including but not limited to cookies to estimate the effectiveness of their advertisements.
Example 2: PureVPN
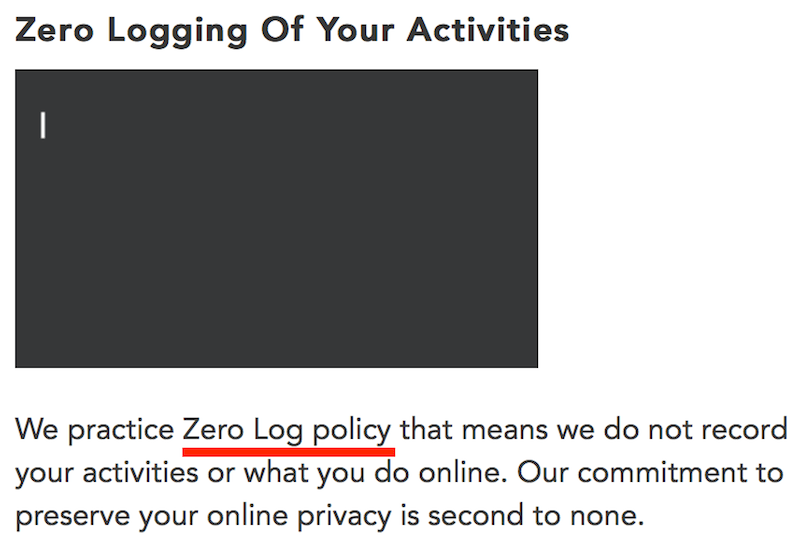
Now returning again to the PureVPN privacy policy, notice the first and second-to-last sentences:
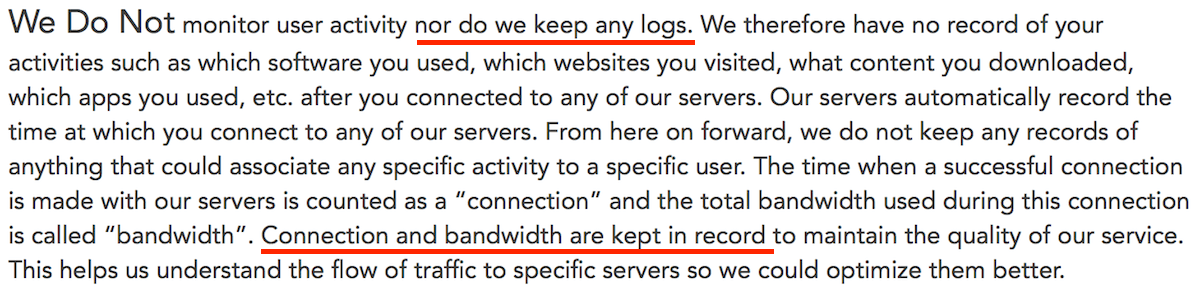
Apparently keeping “connection and bandwidth” is part of PureVPN’s “zero log policy”.
It seems many people will just look for the “no logs” claims on the homepage and never read the fine print in the privacy policy.
These contradictory claims are fairly common with VPNs.
Aside from the logging issues, we’ve also noticed performance issues with PureVPN in our NordVPN vs PureVPN review.
How to protect yourself
Here are five ways to protect yourself from a VPN service or server that may be compromised:
- Verified “no logs” claims – There have been a few examples where “no logs” claims have prevailed over law enforcement. We discuss these examples in our no logs VPN guide.
- Multi-hop VPN – One way to protect yourself if a VPN server is compromised is through a multi-hop VPN configuration. A multi-hop configuration will help to mask incoming and/or outgoing traffic. Bot OVPN and Perfect Privacy offer self-configurable multi-hop VPN chains with up to four servers. VPN.ac offers 18 different double-hop configurations.
- VPN + Tor – If done correctly, using a VPN in combination with the Tor network can further protect users (but performance will drop significantly). (See the VPN vs Tor guide.)
- Multiple VPN services – Using more than one VPN service at the same time will also provide more anonymity. A simple way to implement this setup would be to use one VPN on a router, and then connect to that network through another VPN on your computer/device. Implementing this technique with virtual machines is another option. (The main drawback will again be performance.)
- Privacy-friendly jurisdiction – Choosing a VPN that is outside the 5/9/14 Eyes surveillance countries may offer further protection. Nonetheless, this is no silver bullet. As we saw with PureVPN, being operated in Hong Kong does not mean they won’t cooperate with US authorities.
VPN logs are not necessarily a bad thing. It all depends on your threat model and how much privacy and online anonymity you seek to achieve.
Many VPN providers keep some logs and clearly explain this on their website. The key is to understand what’s going on with these policies, look for honest and transparent providers, and take extra precautions if you want to achieve higher levels of online anonymity.
And for more info on this topic, check out our guide on no logs VPNs that have been verified and proven true.
Update: PureVPN completes a “no logs” audit
After the logging incident described above, PureVPN subsequently underwent a “no logs” audit in 2019. The audit was conducted by Altius IT, based in California.
While we think this is certainly a step in the right direction, there are many other no-logs VPNs with a better track record to consider.
Related Articles:
This article was last updated on December 23, 2022.

 Mass Surveillance is Getting Worse (And You Are the Target)
Mass Surveillance is Getting Worse (And You Are the Target)
Leave a Reply