
Two days ago, on September 25th, Fast Company’s website was hacked and publicly defaced, with the hacker discussing the exploits on a hacking forum. Earlier today, with the website still unsecured, Fast Company’s account sent out more offensive profanity via Apple News. RestorePrivacy has obtained an explanation from the hacker detailing exactly how this transpired.
Two days ago, on September 25th, we noticed a user on a popular hacker forum post about hacking the Fast Company website.
The hacker claimed that Fast Company left “database credentials open to the public” which provided access and data from the company.
The hacker released the data that was obtained from Fast Company on the hacker forum. Users could purchase the files that the hacker obtained using forum credits. The hacker, who goes by the name of Thrax, had this to say:
I am releasing 6,737 employee records from their WordPress database, among other things such as posts (including unpublished drafts), configurations, and more. We were not able to gain access to customer records as these were likely stored in another database. The data includes emails, password hashes for some users (WordPress format), and a few other things. Hell, I think there’s some Auth0 s*** hidden somewhere if you want to do anything with that.
The hacker also described how he was able to publicly defaced the website over the weekend. This was captured on the Wayback Machine here two days ago on Sunday, September 25th.
Fast Company’s website was publicly defaced with the same profanity that was blasted via Apple News earlier today.
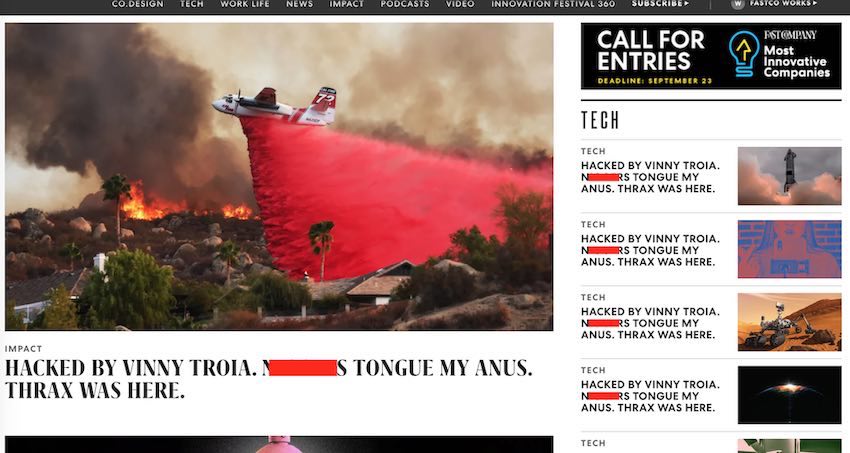
Source: RestorePrivacy.com
While Fast Company was quick to fix the article titles and profanity you see above, the security vulnerabilities were left unpatched.
The hacker’s initial post on the hacker forum is still accessible at the time this article went to publication. Additionally, users of the forum are still able to download the data that was exfiltrated from the site, including Fast Company employee records.
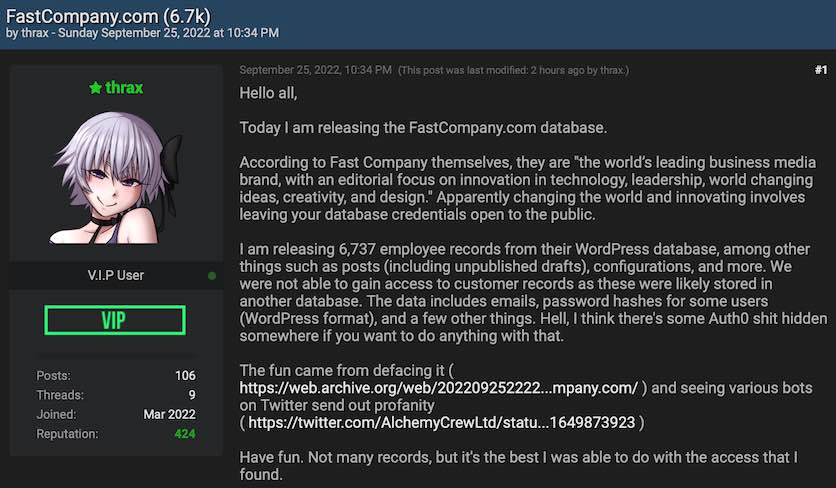
Source: RestorePrivacy.com
Interestingly, it was not until the obscene Apple News notifications were sent out today that this story really started getting attention.
With the site still left unsecured, Thrax was able to send out push notifications via Apple News from Fast Company’s official account. Numerous people took to Twitter to voice their concern and confusion about receiving these notifications.
After seeing the issue blowing up on Twitter, we reached out to the hacker for an explanation.
Hacker explains how the site was left unsecured with weak passwords (pizza123)
Thrax provided RestorePrivacy with this statement explaining what happened.
After their main website was vandalized two days earlier, they changed the database credentials and took other actions they believed would be adequate to safeguard the site, but these efforts were obviously unsuccessful.
– Hacker’s statement to RestorePrivacy on September 27th.
The hacker went on to further update the initial post to provide more of an explanation on how Fast Company failed to secure the site after it was defaced last weekend.
Wow, Fast Company. Despite the public defacement of your site, which boasts millions of visitors, all you did was hastily change your database credentials, disable outside connections to the database server, and fix the articles.
Thrax’s explanation of how FastCompany.com was hacked
The articles are written through a WordPress instance hosted at wp.fastcompany.com – which we found the origin IP of and totally bypassed the HTTP basic auth, leaving us with only WordPress authentication. Thankfully, Fast Company had the ridiculously easy default password of “pizza123” on a dozen accounts, including an administrator account (sorry Amy!), so we got in there really easily. We were able to exfiltrate a BUNCH of sensitive stuff through there – Auth0 tokens, Apple News API keys, Amazon SES secrets (we could literally send email as any @fastcompany.com email with this access), etc. We also found a HTTP basic auth username/password, which happened to work for wp.fastcompany.com, meaning we didn’t have to go through hell to access it anymore. We also found a Slack webhook, which we could’ve used to pull some bulls***, but we didn’t want to bother.
Remember the Auth0 I just talked about earlier? Well, they had an access token in WordPress that allowed us to not only grab the email addresses, usernames, and IPs of a bunch of employees, but also create our own account that we gave admin privileges to two portals: Wonton (wonton.fastcompany.com) and the management portal (manage.fastcompany.com). manage.fastcompany.com was under HTTP auth as well, under the exact same username and password as wp.fastcompany.com (in fact, this site is what the credentials were originally for). Once we logged in with our account (which they still haven’t deleted after days, by the way), and basically let us do a f*** ton of funny sh** such as push notifications to Apple News users, mess with the site, and much more. Wonton was fairly boring, just listing a bunch of bulls*** that they hadn’t used since 2020-2021.
TLDR: Fast Company can’t even keep their security straight and did way too little to respond to this situation. Don’t trust them (or “Inc.”, they’re owned by the same company Mansueto) with your viewership.
[Other profanity redacted.]
This once again illustrates the importance of using strong passwords. Just a few months back we reported how AMD was hacked by RansomHouse, and this was also allegedly carried out due to weak passwords that were cracked.
Fast Company appears to be in damage control.
They have now completely shut down the website, which returns a 404 error the time of publication (September 27th).
Fast Company has also released a statement on Twitter:
Many people are upset about the obscene messages that were sent out via Apple News earlier today. And based on the hacker’s statements, this could have all been prevented by properly securing the website after it was hacked over the weekend.
If you haven’t brushed up on strong password hygiene, right now might be a good time.

 RansomHouse Cyber Gang Claims Ipca Laboratories as Latest Victim
RansomHouse Cyber Gang Claims Ipca Laboratories as Latest Victim
Hi Sven,
Great article!
The naivety is hard to believe when this occurs in corporations.
With the Optus breach in Australia this has affected such a large potion of the population that demands for change are being made.
Sensible security researchers appear to be saying that they will wait for the result of the investigation before drawing conclusions and informed persons are saying they cannot comment while the investigation is under way. With this collective patience, the wait for the report will only be tolerated for a reasonable time frame.
Threatening one third of our population, where the threat is non political is going to get action at all levels.
With the cyber people who will speculate, they say it is an unsophisticated attack, ~”could be performed by a school level programmer – two lines of python.”
I don’t wish any further damage to the Optus brand;
And, if, it is a kid who has implemented the breach, I suggest they come forward;
Because, we have lots coming after them.
Regards,
BoBeX