
The Prometei botnet has returned in a new global campaign and has already infected 10,000 devices in 155 countries, with the number of breaches growing by the day.
The modular malware that has been around since 2016 has been spotted in a new campaign by researchers of the Cisco Talos team, who report that the botnet operators are using a new, upgraded variant that appears to be its third major release.
The notable additions in the new version include a domain-generating algorithm (DGA), a self-updating mechanism, and a new way to gain access to target devices using an Apache web server pre-loaded with a web shell.
Prometei Targets and Goal
Prometei’s current victimology isn’t focused but somewhat random and opportunistic, so the botnet may breach anything from the computers of big organizations to personal home PCs.
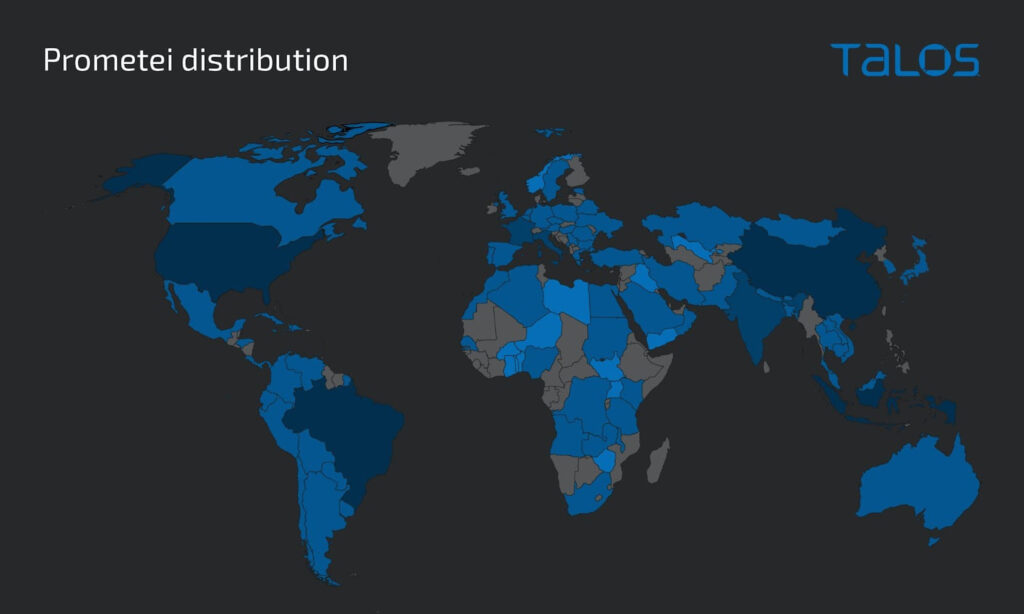
Regarding the targeted countries, only Russia is exempted from infections in the ongoing campaign, indicating that the threat actors are Russians or affiliated with Russia. The countries that have suffered the larger number of infections so far are the United States, China, Brazil, India, Singapore, France, Italy, and India.
Cisco Talos
The botnet’s primary goal is to hijack its victims’ available computational resources to mine Monero. This cryptocurrency is very popular among cybercriminals because it is very hard for law enforcement authorities to trace it. (This is discussed more in our guide on private and anonymous payments.)
However, Talos also observed Prometei engaging in credential harvesting activity, using the Mimikatz tool, which the threat actors might leverage either for account takeover attacks or reselling the data to others for an additional profit.
New Version Features
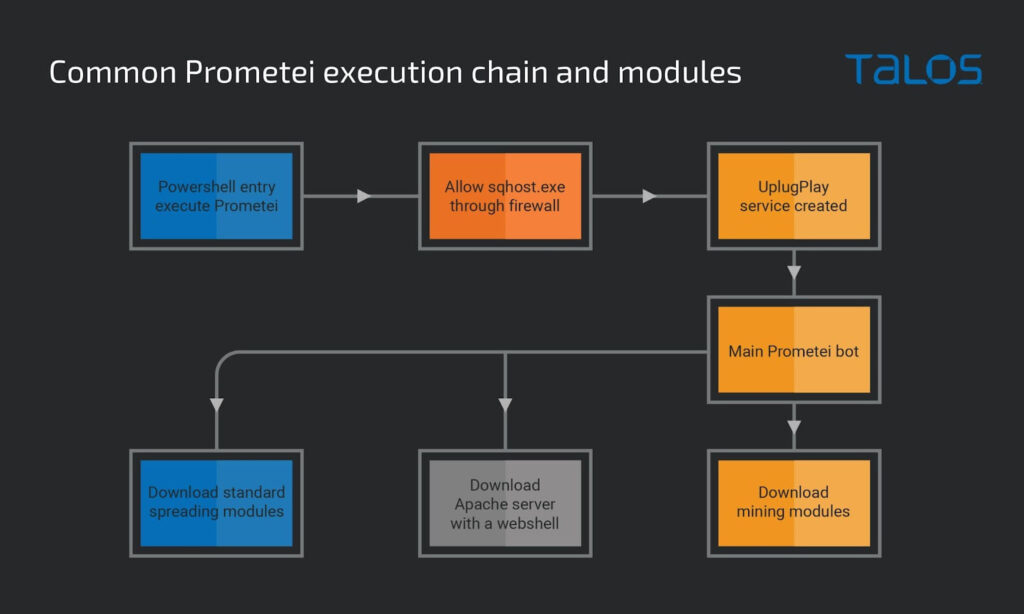
The most notable new feature of Prometei version 3 is the domain-generating algorithm (DGA), which automatically generates up to 48 new domains assigned to be used as C2 (command and control) servers for the botnet. This system gives Prometei excellent resilience against takedowns, helps in evading detection, and provides the operation with redundancy and flexibility.
The second evolution seen in the new version of the malware is its ability to update itself automatically while on the host. It does that by downloading a batch file from the C2 and running it on the host. The batch file will check what components are present in the system and then downloads an encrypted 7z archive containing the latest versions of the components. Eventually, it extracts the archive, installs the new files, and deletes the old versions.
The third important upgrade is using a pre-configured Apache Web Server that is dropped onto the victim’s system in the form of a compressed ZIP archive. The server contains a simple PHP-based web shell, giving the operators remote access to the compromised device, and the ability to execute arbitrary commands on it. In this case, the attacker uses the web shell to perform reconnaissance on the victim’s network, execute commands, download files, and exfiltrate data to the C2.
Cisco Talos
Cisco Talos also identified several new commands not previously documented, including stealing clipboard data, performing mouse clicks on specified screen positions, deleting files, and uploading files to the C2.
Protection from Botnets
Botnets rely on exploiting vulnerabilities in software and firmware to breach devices, so keeping your software and OS up-to-date is a solid defense tip. Apart from that, you should be cautious with emails from unknown senders that carry suspicious attachments and avoid downloading software from obscure websites.
When downloading something from the web, always perform a check on your anti-virus tool before executing it on your device.
“We assess the Prometei threat remains ongoing and will evolve for the foreseeable future. Its common C2 infrastructure continues to show a steady stream of activity, while the operators consistently rotate its malware and cryptomining hosts.” – Cisco Talos
Threats like Prometei that perform crypto-mining on the victim’s device may be easier to discover because they create performance hiccups, raise the temperatures of the device even when the CPU should normally be idle, and generate network traffic that cannot be attributed to legitimate services.

 Android App with 100M Downloads Found Sending Data to Remote Servers
Android App with 100M Downloads Found Sending Data to Remote Servers
Leave a Reply