
A threat actor using the moniker ‘D3m0n’ has posted over 13 GB of data allegedly belonging to American trucking giant U-Haul.
U-Haul is an Arizona-based moving truck company employing 19,500 people, with an annual revenue of over $4 billion USD. The company maintains a strong presence across the United States, operating over 17,000 service points.
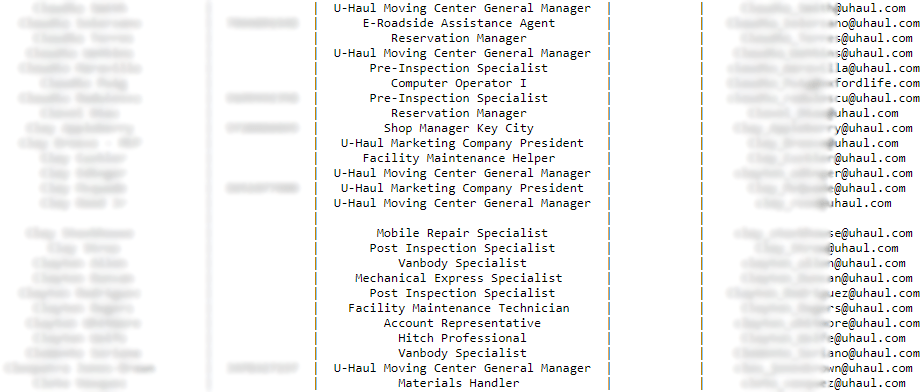
Over the weekend, Breach forums user D3m0n leaked what they claim to be the firm’s Sharepoint database containing data on every employee of the firm. Specifically, the files leaked by the cybercriminal contain full names, phone numbers, email addresses, and job titles of employees of U-Haul. D3m0n has also linked to their own website that contains a copy of the files among data packs from previous breaches.
RestorePrivacy
During a review of the leaked data, RestorePrivacy saw entries that concern high-ranking executives, including General Managers, department managers, etc. The exposure impacts workers, sales agents, maintenance specialists, assistants, customer care representatives, drivers, warehouse personnel, technicians, system administrators, inspectors, network managers, software developers, and others.
RestorePrivacy
The main risks that arise from this massive data exposure for U-Haul are phishing, social engineering attacks, and BEC (business email compromise). Also, the leaked email addresses make it easier for threat actors to perform brute-forcing to guess account passwords or use leaked credentials from other breaches to hijack the accounts. Such a compromise would open the way to lateral phishing, potentially targeting more valuable accounts within the organization.
Other data found in the 13 GB pack include retail documents, staff payments, conference presentations, IT alerts and notifications, acquisition and project documents, software development data, and many more.
The data leak seems credible, but the company has yet to publicly acknowledge any breach. We reached out to several individuals listed in the leaked documents, and some verified their positions and email addresses. This strongly suggests a potential breach at U-Haul, although definitive confirmation is still pending.
RestorePrivacy has contacted U-Haul both via email and phone to request a comment on the validity of the data breach claims, and we will update this post once we receive a response.

 Hacktivists Launch ‘GhostLocker’ Ransomware to Finance their Operations
Hacktivists Launch ‘GhostLocker’ Ransomware to Finance their Operations
There was a data breach in 2022. However, only in the past week (Feb 2024) have I starting receiving seemingly fake Uhaul survey requests referencing a rental within the last 6 months, which is very odd.
If this was related to the initial 2022 data breach, then that rental would not be part of that data dump.
So, could this be part of another breach?
The reason I ask – About 6 months prior to the Wawa data breach, I was seeing erroneous charges from Wawa on my credit card. I contacted Wawa about these couple charges, which I disputed. I ended up getting a new credit card. Then 6 months later Wawa revealed a data breach – surprise, surprise.
What I don’t understand is why d3m0n just gave all that info for free instead of ransoming it. Anyone know why?