
HUMAN’s Satori threat intelligence team has mapped and taken down a massive malvertizing operation they named ‘VASTFLUX.’
The operation injected malicious JavaScript code into digital banner ads within applications, allowing the fraudsters to stack numerous invisible video ad players behind one another and register ad views that generated revenue.
At its peak, VASTFLUX generated 12 billion bid requests, and over the course of its operation, it spoofed over 1,700 applications and 120 publishers, and ran inside 11 million compromised devices.
While fraudulent ads might not directly threaten the privacy and security of mobile users, they still degrade their experience, cause significant stretch on their battery consumption, and incur unnecessary data charges.
Keeping the Scheme Invisible
The goal of the VASTFLUX scheme was to inject scripts into banner ads within applications that decrypted ad configurations and contacted a command and control (C2) server to acquire further instructions like what ad to display on the hijacked banner.
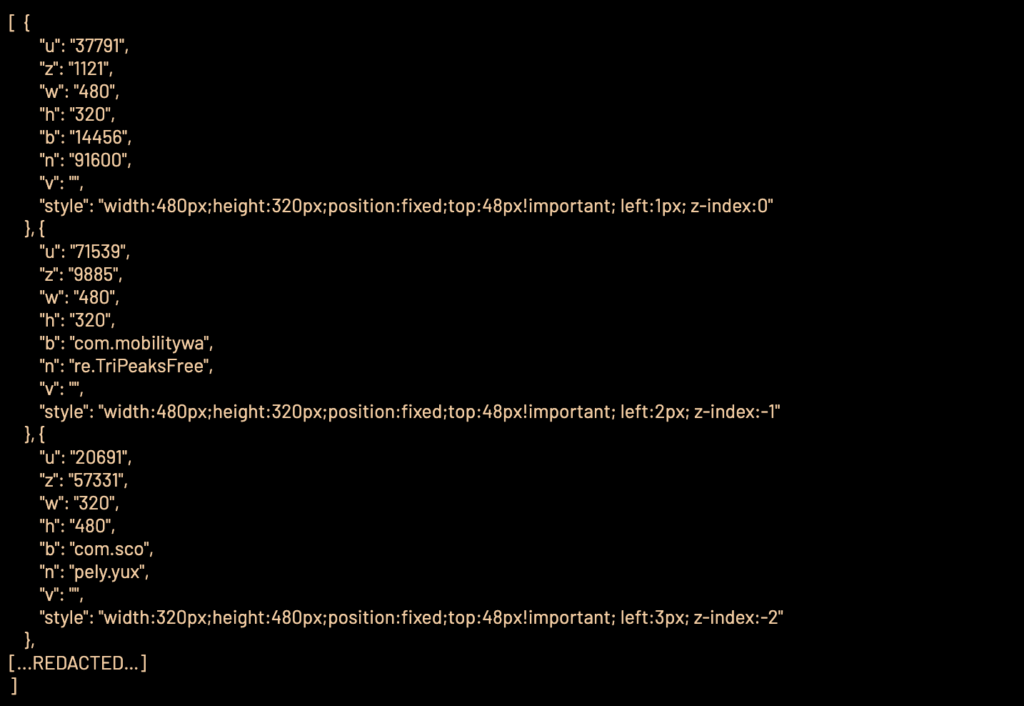
HUMAN
HUMAN’s post explains that VASTFLUX evaded detection for an extensive period of time by deploying code that prevented the discovery of the scheme, and by not using ad verification tags, indicating that the fraudsters behind this operation possess an in-depth understanding of the digital advertising ecosystem.
HUMAN
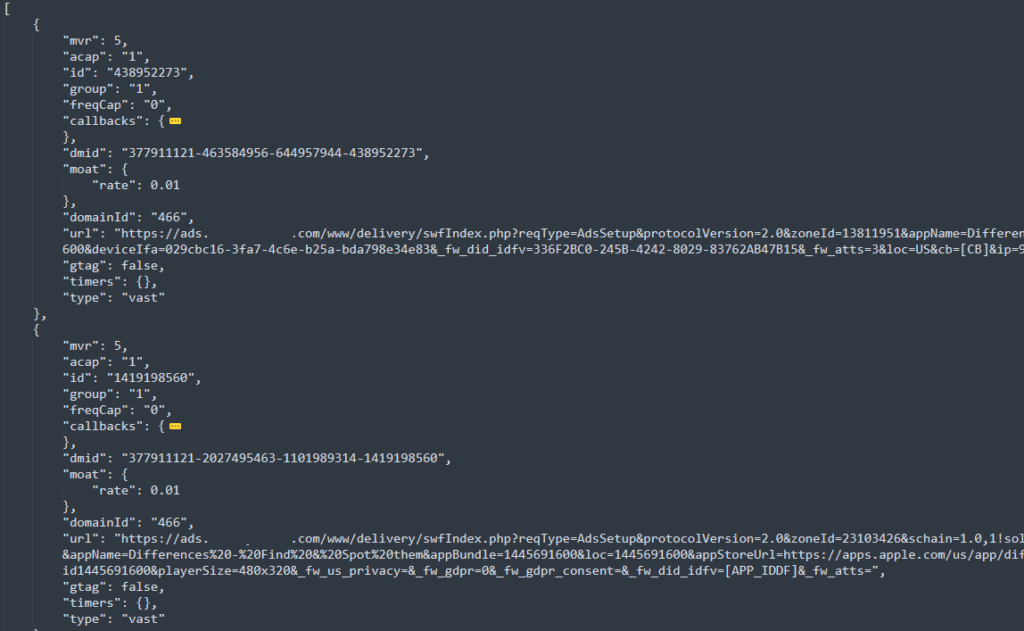
Ad verification tags are small code snippets embedded in digital ads to allow marketers to measure performance. Third-party verification companies also use them to generate metrics like viewability, click-through rates, etc.
By not using ad verification tags, VASTFLUX remained essentially invisible despite its massive size.
Moreover, the C2 sent instructions to the injected scripts on how to spoof the publisher and app ID, which helped minimize the chances of being detected.
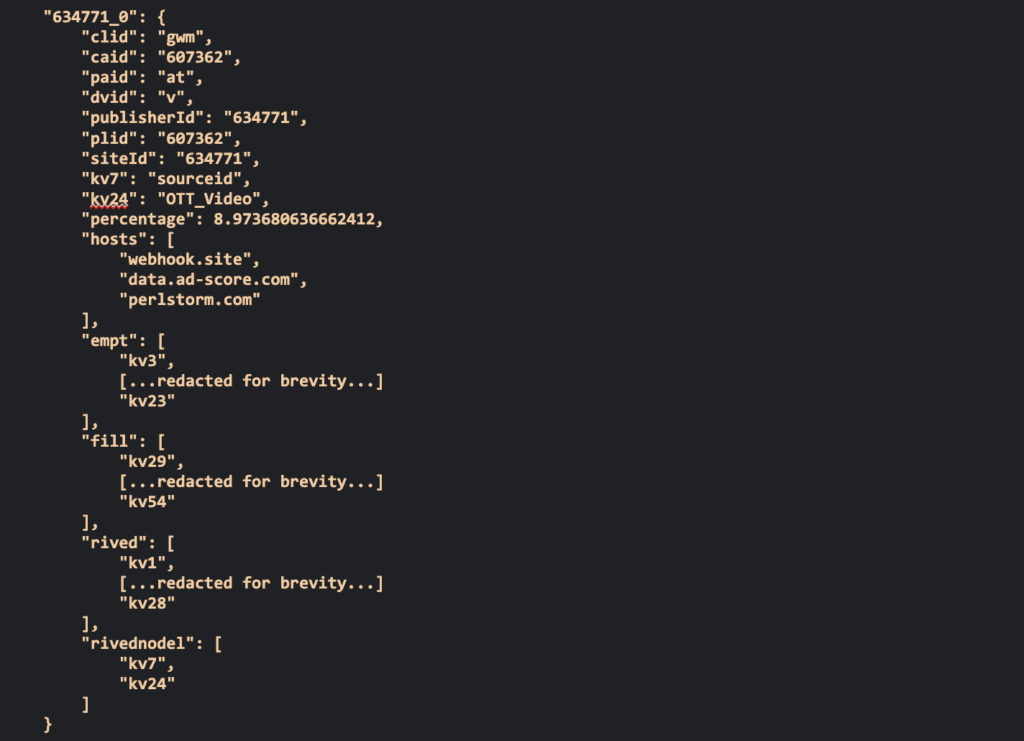
HUMAN
Taking Down VASTFLUX
The Satori team discovered VASTFLUX almost by mistake while investigating a different malvertizing fraud scheme when they noticed that an app under examination in their lab generated multiple bid requests using different app IDs.
They reverse-engineered the attack and uncovered obfuscated JavaScript, eventually leading to the ad servers (C2) that sent instructions to the injected scripts.
Next, they collaborated with the HUMAN community to get additional insight into the scheme, appreciate its size, map it, identify all traffic sources, etc.
“From late June into July, HUMAN carried out three distinct mitigation responses to fight VASTFLUX. The first cut VASTFLUX traffic dramatically, but resulted in the bad actors adapting. The second, only a few days after the first, reduced VASTFLUX traffic to fewer than a billion requests a day: a 92% reduction from the operation’s peak. The third, about two weeks after the first response, further impaired VASTFLUX activity.”
HUMAN
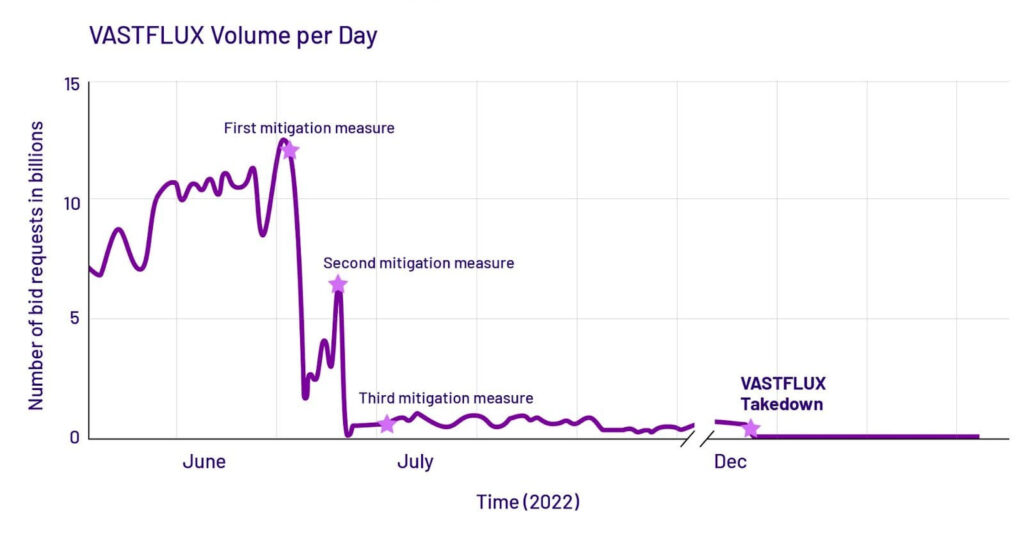
HUMAN
After that, Satori informed the abused organizations to orchestrate a broader and more coordinated action against the fraud scheme. VASTFLUX responded by taking down the C2 servers, likely fearing identification and prosecution.
Signs of Adware
From the user’s perspective, in-app ads are part of the ordinary and expected experience, and malicious hijacks that generate revenue for malvertizing campaign operators aren’t easily discernible.
However, if you notice unusually high battery consumption by certain apps, inexplicable performance slow-downs, random device screen light-ups, and increased data usage, it might indicate that adware is running on your device.

 Threema Downplays Security Issues Disclosed by ETH Zurich
Threema Downplays Security Issues Disclosed by ETH Zurich
Hi Sven Sir,
Please cover this. Google advertisements are spreading malware. Even technically proficient people are getting infected and incurring heavy losses and damages by being hacked by hackers and malware writers.
Google Search Ads Are Spreading Dangerous Viruses
https://youtu.be/apji28Zrbis
Malware in Google Ads: Fake OBS, VLC, Notepad++
https://youtu.be/e6o2afben0s
Hi @Virtues are independent cosmic consciousness,
If you are interested in a deep dive into MalAdvertising this link may interest you:
https://darknetdiaries.com/episode/44/
RP ad-blocking solutions are discussed here:
https://restoreprivacy.com/best-ad-blocker/
GL,
P.S. There are a lot of personal security / privacy guides on the RP homepage.
Sven Sir please add a prominent donate button on restore privacy and expand restore privacy to become the privacy hub of internet and the torch bearer of human civilization and may be the entire cosmos for freedom and justice.
Sven Sir there has been a databreach at paypal. Please write an article about it.
PayPal confirms data breach, sends warning emails to users
https://www.techradar.com/news/paypal-confirms-data-breach-sends-warning-emails-to-users
T-Mobile, too.
https://www.techradar.com/news/millions-of-t-mobile-customers-have-data-stolen-in-breach
I use Adguard Adblocker and it helps protect from all kinds of advertising. It is noteworthy that there are advertisements on private search engines too like Startpage and Duckduckgo. Probably without these advertisements these search engines won’t exist. Same for browsers like firefox and brave. But in case of Firefox and Brave they show first party advertisements which is a great way to support the developer as such advertisements load faster and are not abusive and invasive. But this isn’t the case with advertisements on privacy friendly search engines like Startpage and Duckduckgo. While these search engines themselves don’t collect and store user data like search queries, user agent and ip address. I fear when a person click on advertisements which are displayed first on these privacy friendly search engines the ip address some other information is sent to them. This is what is said by Alok, the privacy enthusiast and founder of Epic Browser. Epic developers also says that for this reason they haven’t incorporated these search engines in Epic Browser. They say they mailed these private search a lot to ask about what data they share with 3rd party and how they operate these advertisements but they didn’t disclose the information. Though Duckduckgo says these advertisements are based on user query and aren’t targeted. Duckduckgo also faced the heat from users and privacy community for not initially blocking Microsoft trackers on its privacy browsers. The truth is making a search engine requires a huge budget amounting to billions of dollars and Duckduckgo relies on Microsoft Bing for search results and is more of a meta search engine, just like Startpage is a proxy to Google search. The other option is to pay for search engine like Neeva and paid tier of Swisscow search engine. But since it is easy to block search engine advertisements on Duckduckgo and startpage and Duckduckgo also has a dedicated option in setting to disable advertisements, personally I won’t pay for a search engine, as I am already paying for a lot of privacy services and softwares. Also search engines are becoming less and less relevant each day with the rise of AI bots and internet is also getting dispersed into walled communities and services as now websites are demanding subscription and Facebook, Tik Tok, Reddit, Quora nag to create account or download app to use their service or pay for paid tier to access full content.
Currently I rely on Startpage as my main search engine and Duckduckgo too as side search engine. Startpage doesn’t like vpns but I don’t face any issues with Nord, Surf shark and Atlas VPN, because they are great overcoming ip bans due to their high quality of service. I also use Google like a privacy friendly search engine using hermit sandbox enabled browser on Android with a vpn and on firefox on windows using container and again a VPN. Incognito mode and deleting cookies, with VPN and Adblocker is a great friend of online privacy. But both browser and BPN themselves should not be tracking users.
Thank you for the information. Does using Adblocker protects from this kind of threat?
Hi @PoliceSven, The short answer is that it depends on what type of adblocking service you use and on the quality of the service you use. Sven explains it all here: https://restoreprivacy.com/best-ad-blocker/
But in short something like Ublock Origin (which is fantastic) wouldn’t help because it only blocks ads in the browser and the problem discussed in this article is about in app ads. My preference for this problem is ad blocking by my vpn (Nord) but there other options discussed in the link
GL,