
A new attack involving a previously unknown malware named ‘Album Stealer’ has been spotted by Zscaler, targeting Facebook users.
The attack employs adult images to trick Facebook users into downloading a malicious ZIP archive and essentially infect themselves with information-stealing malware.
The adversaries’ goal is to steal Facebook credentials and take over accounts, particularly Business accounts that have access to ad and marketing campaigns. The threat actors use that access to run malicious campaigns for their own benefit, directing the ad-generated revenue to their bank accounts.
Facebook Attack Chain
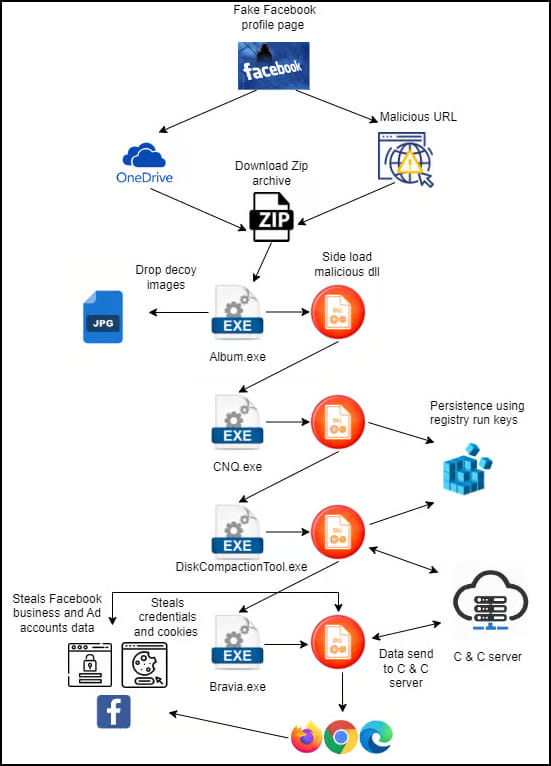
The attack begins with the threat actors using fake Facebook profile pages containing adult images of women to lure users into clicking on them. Those profiles contain a link to an archive that supposedly contains an album of more pictures.
Clicking on that link delivers a ZIP archive from Microsoft OneDrive, to evade anti-virus warnings. The archive contains an executable file named Album.exe, a malicious DLL, and a dat file.
Zscaler
Album.exe is in reality a PDF viewer that side-loads the malicious DLL to initiate the malware loading process. The executable also executes a self-extracting archive that contains images of women to serve as a decoy.
Meanwhile, in the background, the malware adds new registry keys to establish persistence on the system and continues the infection chain by loading several additional executables downloaded in each step.
Finally, Album Stealer is loaded onto the system, collecting data from the compromised computer and sending it to the command and control server.
Zscaler
Album Stealer Targets
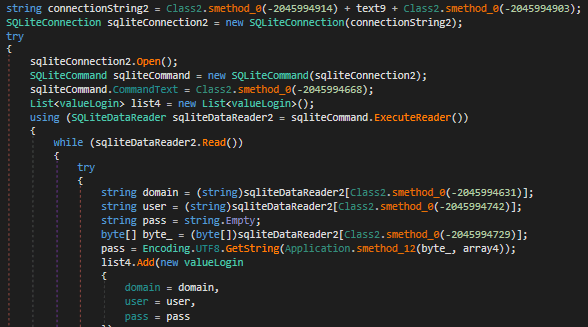
As an info-stealing malware, Album Stealer targets valuable user data that like account credentials, cookies and login data stored on web browsers like Chrome, Opera, Brave, Edge, and Firefox.
Zscaler
Its differentiating factor compared to other commonly used info-stealers is that instead of searching for static paths in the breached computer, it searches for file names.
This makes its scanning slower, but has the advantage of giving it more specific targeting, limiting the amount of false positives and unnecessary data uploads to the C2.
Moreover, Album Stealer focuses more on Facebook accounts, and if it extracts credentials for the social media platform, it uses the graph API to obtain additional information relating to business and ad management FB accounts.
The Album Stealer attack is a passive attack that waits for victims to make the first move themselves. However, it’s still a significant threat due to its potential to draw large amounts of victims on its hooks.
Facebook users are advised to avoid downloading archives from links listed on the platform, especially when these come from people they don’t know.

 Malvertizing Network with 12 Billion Daily Bid Requests Taken Down
Malvertizing Network with 12 Billion Daily Bid Requests Taken Down
@Sven
Can we get some deets on ChatGPT? They seem to be selling users data including mobile numbers. You can’t use their service unless you register a legitimate mobile number. VoIP and even Google Voice numbers don’t work. One can argue the same about Telegram and other secure chat protocols.
Hi @Harmonious Mind,
I think you make many good and valid remarks.
What is common amongst security / privacy people is the use of a model, ‘the threat model.’
This means that everyone’s circumstances and security / privacy needs are different.
I feel this is very well outlined here:
https://www.youtube.com/watch?v=8MIIeIa25tE
GL,
Also there should be open discussion and no censorship. Censorship is wrong and an extreme measure which should not normally be taken. Like for example there is vaccine censorship, censorship when speaking against Islam etc. This is not good and a sign of decay.
But censorship is not online privacy. It is about community and interaction. And there need to be transparency too, in government, in people. Privacy is basic dignity and personal space for growth which can be preserved in a strong and enlightened society.
So what we need is more open mindedness and depth of discussion and understanding, both within and without, not isolation, being uprooted and decay. So privacy should also be taken in the right context of individual dignity and growth, not a license to personal vices and being harmful to people and life.
Technically privacy is a part of security. So there is no privacy without security. And security is bigger and includes privacy. Just by practicing security in its entirety including lack of personally identifiable information and zero trust architecture one ensures privacy by default.
@Sven Sir it is important to revisit why are we emphasizing and at times paranoid about online privacy.
One need not take such extreme steps to ensure online privacy that one gets more unsecure by using unvetted products and also loosing convenience at the same time.
In US the Government and three letter agencies do not violate human rights and are not evil. They need warrent to get data from private entities. And it is indeed very much required to protect children from exploitation and keep away extremists particularly Islamic Terrorism. A better way to ensure privacy and security would be to make the atmosphere of society open to discussion on taboos surrounding such things. So that governments, which are collective power and voice of people, need not take such investigations. Again they are not evil and not being unreasonable.
Further, advice like not using Microsoft Windows and Google’s Android is not a good advice without having good alternatives. These platforms are secure and well examined. Operating Systems are extremely complex piece of code. A cyber security person told me that Linux is 10 years behind security compared to Windows and while vulnerabilities on windows gets fixed and some what reducing, on Linux they have been increasing. This is about critical software vulnerabilities, not kiddie malwares.
The data collection on these platforms and from their first party services is indeed used for sales and marketing. This is data monitisation. But they don’t target each person individually. There are cohorts and categorisation for a few thousand people, I believe 6,000, including Apple and Facebook.
The issue can arise when there is a breach of data. That data is anonymous mostly though it may not be very difficult to deanonymise that data sometimes. Which a cyber criminal can later use to target someone. Here we have to take care to use services which have a great track record of protecting user data and no history of data breaches. As Mrwhodetheboss says when he reviewed Linux smartphone, that such monitisation indeed helps to make internet what it is and help people available free services like his free quality videos and help him earn a living and there is no proof or experience that this is very harmful for a person or Society in practical life in real world.
Then, one can pay for services and that makes service providers free from reliance on data monitisation. I also avoid advertisements by paying for services.
So Gmail and outlook are more secure and convenient and reliable and robust. Same for Onedrive and Google Drive, Windows and Android, Docs and Office etc. They are not private like Tales OS and Graphene OS but certainly more secure and not violate individual dignity or are not absolutely non-private but approximately and are reasonably safe with industry leading security practices in place for securing that data.
Then, it really depends on the type of services one use that determines data collection, so I do prefer alternative services which can be cheaper and more convenient or desirable or even secure too like a 3rd party password manager or antivirus than using edge or chrome’s build in password manager or Google play protect and Microsoft Windows defender.
So all in all what really one needs to be careful as far as digital life is concerned is safe social media usage and should practice good cyber security habits.
There is a place for websites like restore privacy which make people aware about good cyber security hygiene and security practices, ignoring their Paranoia that someone is spying on you or Google and Microsoft is evil and an out right threat and that Governments are evil. Not exactly friends though. Big companies have their commercial interests and are also passionate about what they do. The danger lies from “isms” like Islamism, Communism and other such ideologies which have a verifiable record of mass destruction.
Just as things like social media influencers, or toxic online gaming communities or strange things like audiophile or some of the animal right groups and environmental groups which may not really help that much, there is a community of online privacy advocates with varying degree of beliefs and understanding and threat level NBTV, Rob Braxxman, Techlore, Restore Privacy etc etc. Some of their advises can be useful and very much a reality and necessity in countries like China and Russia. One still needs to take care of app permissions and keep a watch on services we use and the companies which provide them. Times also change and never a constant. But some of their beliefs and advices are inaccurate and sometimes not useful.