
Current web fingerprinting solutions can still bypass most privacy protections offered in modern web browsers, persistently tracking users and identifying them.
This applies even in cases where the user has wiped their browser’s cache and restarts them or when they use a VPN connection.
A software developer using the moniker “Bitestring” tested an open-source tool released by a company that offers “fingerprinting as a service” to websites against Chrome, Firefox, and Tor, and the results are worrying.
What Is Web Fingerprinting?
Web fingerprinting is a sophisticated tracking method that can identify users across multiple sessions and websites without using cookies or other persistent storage.
Fingerprinting works by analyzing a user’s web browser and hardware configuration to generate a unique ID. For example, websites employ fingerprinting libraries to collect data from JavaScript APIs offered by browsers, including browser version, number of CPUs, screen size, codecs, and more.
Because this data does not need cookies to collect, existing protection systems are weak against fingerprinting. Moreover, there are enough data points that can be freely collected to help websites create unique visitor IDs with high confidence.
The main problem with web fingerprinting is privacy invasion, as it allows websites, online services, and third parties to profile, track, and identify users across multiple browsing sessions and websites without their consent.
If a user visits multiple websites that use common fingerprinting technologies, third parties could create detailed profiles about their interests, preferences, and habits, deliver personalized ads across the sites, and deanonymize them even when the user actively tries to avoid that by using a VPN, for example.
Browser Test Results
In this case, the software developer tested the solution of FingerprintJS Inc., which offers a live fingerprinting demo on its website, claiming accuracy of 99.5%.
The service claims that it can persistently track website visitors for years, even after multiple browser upgrades using a combination of fingerprinting, fuzzy matching, and server-side techniques.
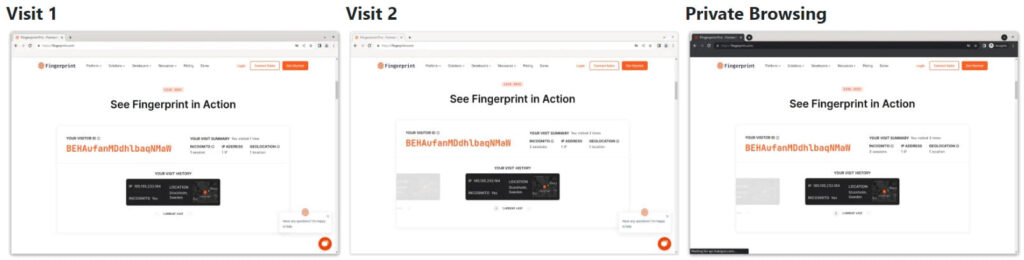
The researcher visited the test page and got a tracking ID. Then he cleared the cache and browsing data and revisited the test page, which counted this as a second visit, although that shouldn’t be theoretically possible.
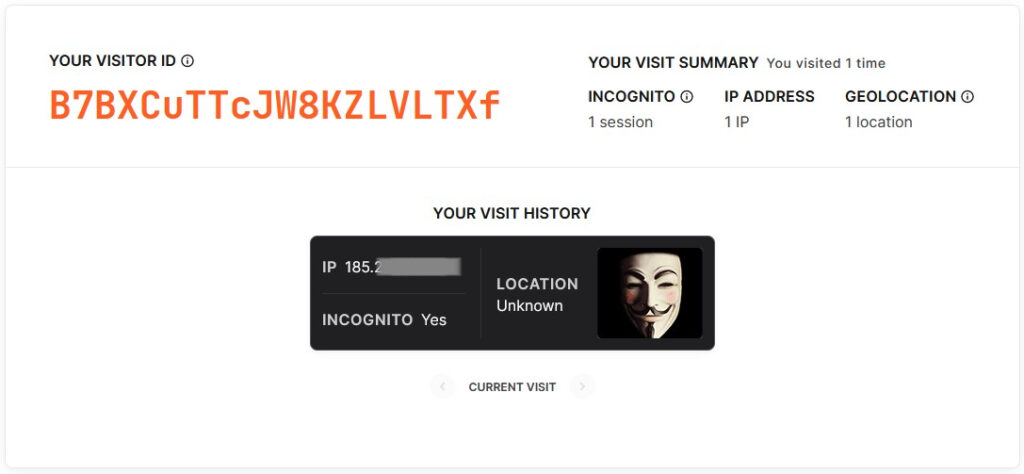
Next, he cleared the browser cache and all data and launched the browser on private mode (incognito), and yet FingerprintJS’s tool still assigned the same visitor ID, counting this as the third visit.
bitestring.com
This applies to both Firefox and Chrome but not to Tor, for which the fingerprinting tool generates a new ID on each new visit.
Restore Privacy
This is because Tor relays user traffic via network nodes, so each time, the exit node is different, and the real user’s IP address and hardware data remain adequately masked.
How to Protect from Fingerprinting
The apparent solution to fingerprinting is to use the Tor browser, however, this may not be for everyone, as regular browsing with Tor is rather slow and cumbersome.
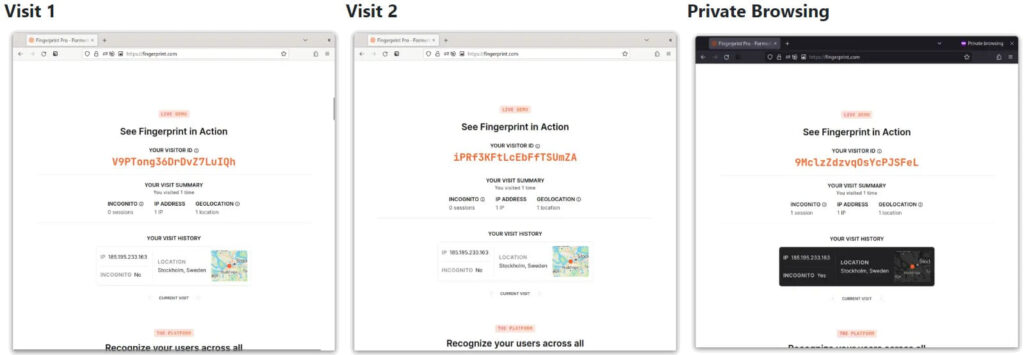
Another solution would be to enable the “resistFingerprinting” feature on Firefox, which yielded good results in the test, tricking FingerprintJS’s tool into generating a different visitor ID on each visit.
bitestring.com
This feature, which is also available for Firefox for mobile, was initially contributed to Firefox by the Tor Project. It works by masking most of the data points websites collect to achieve fingerprinting, like CPU core count, timezone, screen resolution, user agent, etc.
If you’d rather use a Chrome-based browser, Brave would be the best bet. The browser randomizes the fingerprint for each session, making persistent tracking harder, although not impossible.

 15GB of Data from the S.T.A.L.K.E.R. 2 Video Game Leaked Online
15GB of Data from the S.T.A.L.K.E.R. 2 Video Game Leaked Online
I use Fingerprint Spoofing extension which is available for Chrome and Firefox. I find it simple to use and not complicated like canvasblocker. However, both extensions seem to be no longer supported.
For those of us who have resistFingerprinting set to false because they can’t deal with the constantly changing zoom levels of web pages, I’m happy to report that the CanvasBlocker add-on for FF (https://addons.mozilla.org/en-US/firefox/addon/canvasblocker/) seems to do a good job of generating a different fingerprint for every session. As far as mobile browsers, I was surprised to discover that Mull and FF did not seem to be able to defeat fingerprinting (at least not out of the box) although Fennec F-Droid did.
I tested the Brave browser, but it did not change, knowing that it is strict, while Firefox was changing with each session with modification and adding script, ublock and canvas
Question to founder: why don’t you create a forum for yourt website? I mean old school phpbb type! no facebook groups, but real disccussion forum! I would like to be a member! Because, your site is must have in a bookmakarks! My go to information about privacy!
I use “Temporary tabContainer” extension for Firefox and I get new fingerprint every time in the live fingerprinting demo. The extension works fine with multi-account container.
I am so sorry, my experiment isnt entierly true. I forgot I had canvas defender extension (hidden in Firefox) enabled. When I disabled it, I got the same fingerprint.. If I disable temporary containers and just run Canvas defender, then it gets the same fingerprint every time also. So my conclution is that you get a new fingerprint every time. when both extensions are enabled.
I used Firefox with ArkenFox’s userJS, Chameleon, CanvasBlocker, and UBlock Origin and got a different user session every single time I switched VPN servers (5/5)
I succeeded twice using Brave (Fingerprinting set to aggressive) with UBlock Origin.
Thanks for the test and your dedication. Have you tested Brave or Firefox with other browser add ons like canvas blocker, ublock, and clearurls? I have had a hard time with firefox and various config changes. Also how do you feel about eff.org’s cover your tracks tool that doesn’t require creating an account?
I am working with friends who expressed interest in helping their online privacy and we are finally at the part where hes ready to use tools in addition to a change in his habits and his specific “threat modeling”.
Respectfully
I’ve apparently visited 13 times before from 9 different IP addresses including 5 incognito sessions. I don’t do incognito. Ever.
In the past, fingerprinting type sites have always shown me to be unique. Running Gentoo, compiling everything just as I want it, having an oddball mix of hardware and so on does make for a very unique system. I’ve been running Librewolf lately and I’ve been forced to turn on resistfingerprinting because audio from several sites won’t play correctly otherwise (it’s a Firefox/Linux thing.) It seems this has at least made me a little bit harder to uniquely identify. It does take some getting used to, but I live with it. Tor has always seemed useless to be because more and more sites block exit nodes all the time.
I do use a VPN, but it just routes me through a personal VPS, and I only do it because my ISP tracks *everything* I do and this way all they see is copious amounts of traffic going over a tunnel. They’re welcome to the traffic my archiveteam warrior client generates.
Congratulations! for your great post Heinrich. I learnt a lot from you.