
RansomHouse, a cyber extortion gang that gained international notoriety in June with the breach of AMD, has now announced another well-known victim with Ipca Laboratories. RestorePrivacy received advanced notice of this security breach as well as additional information from RansomHouse for this report.
RansomHouse, an emerging cyber extortion gang, is now claiming to have breached Ipca Laboratories, the Indian multinational pharmaceutical company based in Mumbai.
RansomHouse published Ipca as the latest victim on the group’s darknet site, as we verified earlier today.
RansomHouse told RestorePrivacy that it breached Ipca Laboratories on September 3rd, 2022. The group claims to have exfiltrated .5 Tb of data from Ipca.
Below is the current post on RansomHouse’s darknet site announcing the breach.
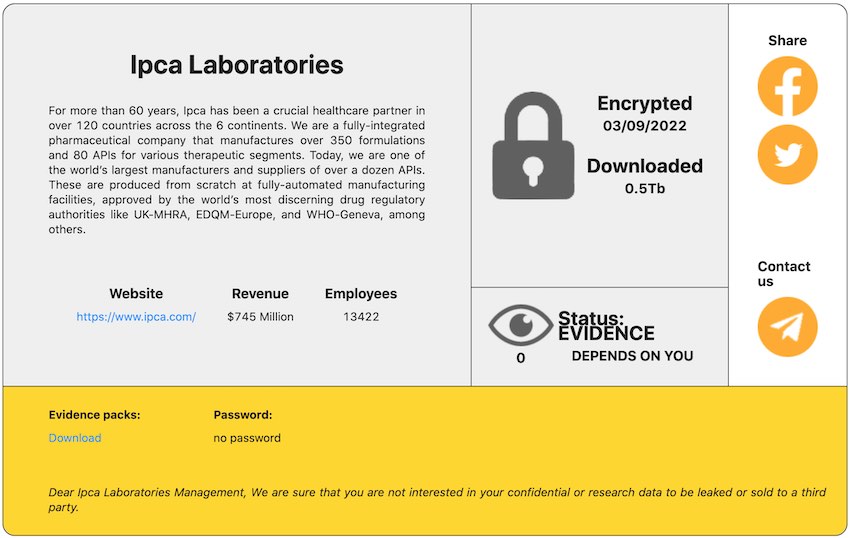
Source: RestorePrivacy.com
At the time this article went live, RansomHouse has not provided any additional details on how the data breach took place. A few months earlier, with the AMD breach, RansomHouse explained that access was gained through weak employee passwords. It’s not clear if that was also the case with Ipca.
Analysis and verification of the data sample
RestorePrivacy analyzed the data sample provided by RansomHouse on September 9, 2022.
It includes screenshots of internal company files, as well as an employee spreadsheet. In total, there are currently 13 screenshots that show files allegedly exfiltrated by RansomHouse in the attack on Ipca. Below is one of the screenshots.
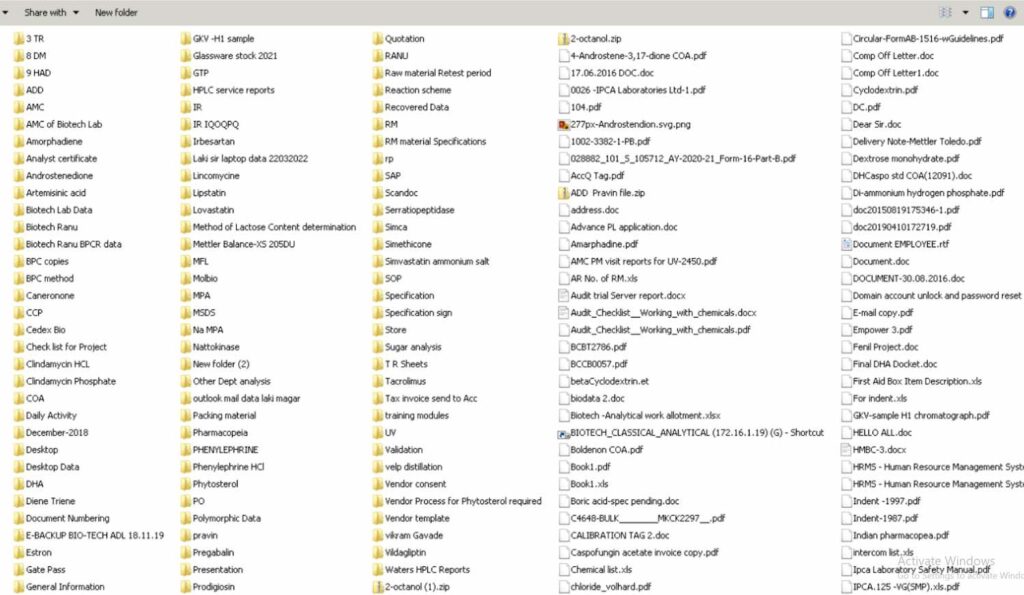
Source: RestorePrivacy.com
RansomHouse has also written a note to Ipca on its darknet site that reads as follows:
Dear Ipca Laboratories Management, We are sure that you are not interested in your confidential or research data to be leaked or sold to a third party.
– RansomHouse darknet site
About RansomHouse
RansomHouse can best be described as a cyber extortion group that first emerged in December 2021 with a website on the darknet. The group has gained global attention with large victims, such as Shoprite Holdings and AMD earlier this year.
Since its inception in December 2021, RansomHouse has announced a total of 10 victims on the group’s homepage:
- Saskatchewan Liquor and Gaming Autority (December 2021)
- Jefferson Credit Union (December 2021)
- Dellner Couplers AB (April 2022)
- AHS Aviation Handling Services GmbH (April 2022)
- Shoprite Holdings LTD (June 2022)
- Advanced Micro Devices, Inc (AMD) (January 2022)
- Summit Care (June 2022)
- Fairfax – Crum & Foster (March 2022)
- 8 Municipal Districts in Italy (July 2022)
- Ipca Laboratories (September 2022)
Will Ipca Labs’ data be leaked or sold?
It’s difficult to say exactly how this situation will play out.
RansomHouse, as the name implies, is surely demanding a ransom from the victim for the deletion of all data and keys to decrypt any files that were locked in the attack on September 3rd.
Should the negotiations fail, we can expect that RansomHouse will either sell the data to a third party or leak it on the group’s darknet site.
With Shoprite and AMD, two other high-profile victims of RansomHouse, the data was sold to third parties after negotiations with the victim failed, according to RansomHouse.
Ipca Laboratories contacted for comment
After analyzing the data sample earlier today, we have reached out to Ipca Laboratories in Mumbai for comment.
At the time this article went live, we have not heard back. We will update the article with any statements and new developments we receive.

 Yanluowang Ransomware Group Claims Cisco Systems as Latest Victim
Yanluowang Ransomware Group Claims Cisco Systems as Latest Victim
Hi RP,
You may have heard of the Optus data breach in Australia.
Tough it is a big avent here it doesn’t appear to have even noticed much around the world.
Australian cybersecurity researchers seem to be saying that there has not been enough technical information released to give views or draw conclusions.
Most statling is reports that the claimant hacker has revers3d their position of first requesting US$ 1 million and now suggesting an apology and promising to delete all data.
This is unusual and surprising.
The below link is from a credible news agency.
What would you make of this?
https://www.abc.net.au/news/2022-09-27/online-account-claims-to-have-released-optus-customer-data/101476232
Regards,
BoBeX
Hi BoBeX,
I’ve been following this and the reports are correct. Here is an archived version of the original post with the latest change about the data not being for sale:
https://web.archive.org/web/20220927065136/https://breached.to/Thread-Optus-Data-will-not-be-sold-or-leaked
Thanks for the info.
The event is being taken very seriously here, the upper number on potential affected persons would be one third of of our population. So it has attracted national attention.
Potentially the breached company may have to pay for replacement identity documents.
It now appears Medicare documents may have been included in the breach.
Our government cyber organisations have partner with the FBI for the investigation
https://vpnpro.com/blog/hidden-vpn-owners-unveiled-97-vpns-23-companies/
If I was Ransom House, and I wanted maximum attention and exposure, I would not wait until later Friday afternoon to announce this. I’d drop the info on a Tuesday morning, New York time. 🙂