
A lot has changed since we first looked at the WireGuard VPN protocol. In this new and updated WireGuard VPN guide, we examine the strengths and weaknesses of this protocol, as well as some of the best VPNs that support WireGuard.
WireGuard is a relatively new VPN protocol that is already bringing big changes to the VPN industry. But is it trustworthy and safe?
While many people discuss the benefits of WireGuard – namely faster speeds and upgraded encryption – the drawbacks of WireGuard often go ignored. So is WireGuard ready for widespread adoption – or do the lingering privacy concerns outweigh the potential benefits?
For those wanting to test out the best WireGuard VPNs, below are the top choices:
- NordVPN – NordVPN is a premium VPN that fully supports the WireGuard protocol in all apps. It’s one of the fastest, fully-featured VPNs on the market and has also passed third-party security audits. Grab the 72% off coupon here >>
- Surfshark – Another leading VPN service that fully supports WireGuard in a private and secure implementation. Surfshark offers premium speeds, numerous features, and a cheap price.
- IPVanish – A very fast and reliable WireGuard VPN, IPVanish is also a top performer with streaming and has been audited.
- OVPN – One of the leading VPN services based in Sweden, OVPN supports WireGuard in all apps and works well for many use cases.
- Proton VPN – Based in Switzerland, Proton VPN is another privacy-focused VPN with extra features, including a VPN ad blocker.
- Atlas VPN – A fast, affordable, and fully-featured VPN service with a great free trial offer.
We’ll answer all these questions and more in this updated WireGuard VPN guide.
Note: Right now, WireGuard has some inherent problems that can undermine user privacy if not adequately addressed. Before using the WireGuard VPN protocol, be sure to examine how your VPN provider ensures user privacy with their WireGuard implementation.
Some VPNs have effectively addressed all privacy concerns. For example, NordVPN supports WireGuard directly in their VPN apps using a Double NAT system. This ensures no identifiable user data (IP addresses) are ever stored on a VPN server. We’ll examine different VPNs that support WireGuard more below.
Here’s what we will cover in this updated WireGuard VPN guide:
- Benefits of WireGuard
- WireGuard privacy problems (and solutions)
- The future of WireGuard
OpenVPN vs WireGuard – OpenVPN is considered the gold standard of VPN protocols by many — but things are changing. To compare these two protocols, we put together a WireGuard vs OpenVPN guide, which examines speeds, security, encryption, privacy, and the background of each VPN protocol. We found WireGuard to be about 57% faster than OpenVPN on average, and even faster with nearby servers (450 Mbps).
Now let’s begin with the benefits of the WireGuard VPN protocol.
Benefits of WireGuard VPN
Here are some of the ‘pros’ that WireGuard offers:
Updated encryption
As explained in various interviews, Jason Donenfeld wanted to upgrade what he considered to be “outdated” protocols with OpenVPN and IPSec. WireGuard uses the following protocols and primitives, as described on its website:
- ChaCha20 for symmetric encryption, authenticated with Poly1305, using RFC7539’s AEAD construction
- Curve25519 for ECDH
- BLAKE2s for hashing and keyed hashing, described in RFC7693
- SipHash24 for hashtable keys
- HKDF for key derivation, as described in RFC5869
You can learn more about WireGuard’s modern cryptography on the official website or in the technical white paper [PDF].
Minimal WireGuard code base
WireGuard really stands out in terms of its code base, which is currently about 3,800 lines. This is in stark contrast to OpenVPN and OpenSSL, which combined have around 600,000 lines. IPSec is also bulky at around 400,000 total lines with XFRM and StrongSwan together.
What are the advantages of a smaller code base?
- It is much easier to audit. OpenVPN would take a large team many days to audit. One person can read through WireGuard’s codebase in a few hours.
- Easier to audit = easier to find vulnerabilities, which helps keep WireGuard secure
- Much smaller attack surface in comparison to OpenVPN and IPSec
- Better performance
While the smaller code base is indeed an advantage, it also reflects some limitations, as we’ll discuss below.
Big performance improvements

Speeds can be a limiting factor with VPNs – for many different reasons. WireGuard is designed to offer significant improvements in the area of performance:
A combination of extremely high-speed cryptographic primitives and the fact that WireGuard lives inside the Linux kernel means that secure networking can be very high-speed. It is suitable for both small embedded devices like smartphones and fully loaded backbone routers.
Theoretically, WireGuard should offer improved performance in the following areas:
- Faster speeds
- Better battery life with phones/tablets
- Better roaming support (mobile devices)
- More reliability
- Faster at establishing connections/reconnections (faster handshake)
WireGuard should be beneficial for mobile VPN users. With WireGuard, if your mobile device changes network interfaces, such as switching from WiFi to mobile/cell data, the connection will remain as long as the VPN client continues to send authenticated data to the VPN server.
Fastest VPN protocol we’ve tested
We have now tested out WireGuard extensively with NordVPN and a few other VPN services that support it. We have found NordVPN’s implementation of the WireGuard VPN protocol, which they call NordLynx, offers the fastest speeds.
Here we are using NordVPN with the WireGuard VPN protocol (NordLynx) with a server in Seattle (USA). We hit speeds of 755 Mbps with US servers.
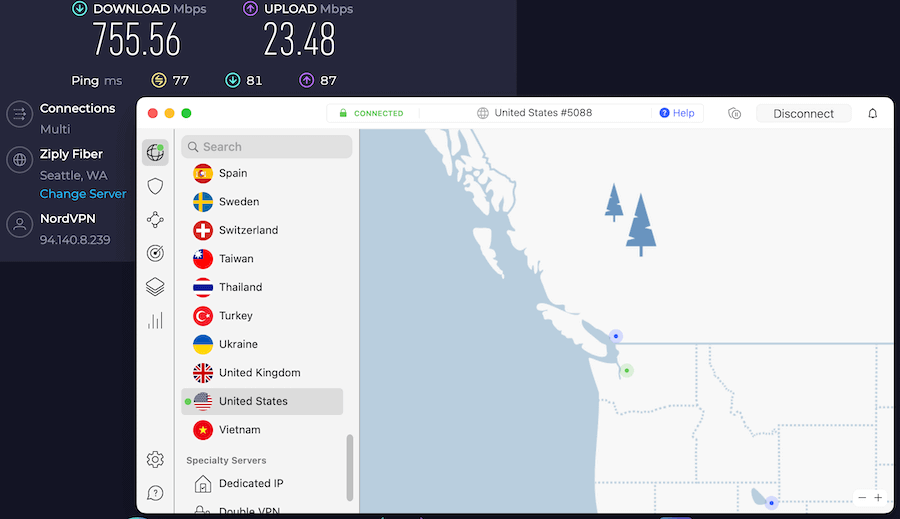
This makes WireGuard the fastest VPN protocol we have tested.
You can see all test results in our NordVPN review or check out NordVPN with WireGuard here.
Cross-platform ease of use
Although full implementation was somewhat delayed, WireGuard now works well across all major platforms. WireGuard supports Windows, Mac OS, Android, iOS, and Linux.
Another interesting feature of WireGuard is that it utilizes public keys for identification and encryption, whereas OpenVPN uses certificates. This does create some issues for utilizing WireGuard in a VPN client, however, such as key generation and management.
A few VPNs have already integrated full WireGuard support into their lineup of VPN clients. See for example NordVPN, Surfshark, and also Mullvad.
Merged into Linux and Windows kernels; fully released from beta
On March 29, 2020, it was announced that WireGuard will be officially included in the 5.6 Linux kernel. This is big news that many privacy enthusiasts have been waiting for. In August 2021, WireGuard made it into the Windows kernel.
Additionally, WireGuard is now out of beta with the release of version 1.0+ for nearly every major operating system. You can get more info on WireGuard for different operating systems here.
With these two developments, WireGuard is now considered stable and ready for widespread use. The old warning on the official website about WireGuard being “not yet complete” has been removed.
WireGuard privacy problems (and solutions)
While WireGuard may offer advantages in terms of performance and security, by design it is not ideal for privacy. Many VPN providers have expressed concerns about WireGuard and its impact on privacy.
IVPN noted that WireGuard “was not designed with commercial VPN providers who offer privacy services in mind.” Similarly, NordVPN also voiced concerns with the inherent privacy issues of WireGuard:
By implementing the out-of-the-box WireGuard protocol in our service, we would have put your privacy at risk. And we would never do this.
Fortunately, the dust has settled and today there are some good solutions to these problems. WireGuard is now a stable VPN protocol and a few VPNs have found effective solutions for deploying it while still ensuring user privacy.
To understand the tradeoff between privacy and security with WireGuard, IVPN did a good job distinguishing the two as follows:
The security of the protocol is concerned with protecting the data in a tunnel from being accessed by adversaries: either by breaking the encryption, MITM attacks, or by any other means, no matter how complicated.
Privacy is concerned with whether an adversary can learn anything about you, your communication or any party you’ve communicated with. It has more to do with the metadata rather than the actual data.
Privacy can be violated, even when security is rock solid. For example, when the fact that two parties communication can be determined. Or when a certain piece of information about a party becomes known after the communication took place. However, it should be noted that, if security is weak, privacy cannot be guaranteed at all.
Now that we’ve covered the basics, let’s examine some privacy problems with WireGuard.
By default, WireGuard stores user IP addresses on the VPN server indefinitely
As others have pointed out, WireGuard was not built for anonymity and privacy, but rather security and speed.
By default, WireGuard saves connected IP addresses on the server. These user IP addresses are saved indefinitely on the server, or until the server is rebooted. This makes the out-of-the-box version of WireGuard incompatible with no-logs VPN services.
So how are VPN services deploying WireGuard while still ensuring user privacy?
Solutions
Based on our research, the solution to this privacy problem varies by the VPN provider. We’ll examine a few below.
NordVPN double NAT system with WireGuard
NordVPN takes a unique approach to the WireGuard privacy issue with what they call a “double NAT system” deployed with NordLynx:
The first interface assigns a local IP address to all users connected to a server. Unlike in the original WireGuard protocol, each user gets the same IP address.
Once a VPN tunnel is established, the second network interface with a dynamic NAT system kicks in. The system assigns a unique IP address for each tunnel. This way, internet packets can travel between the user and their desired destination without getting mixed up.
The double NAT system allows us to establish a secure VPN connection without storing any identifiable data on a server. Dynamic local IP addresses remain assigned only while the session is active.
This is NordVPN’s unique solution to WireGuard’s privacy flaws, and they are referring to it as NordLynx.
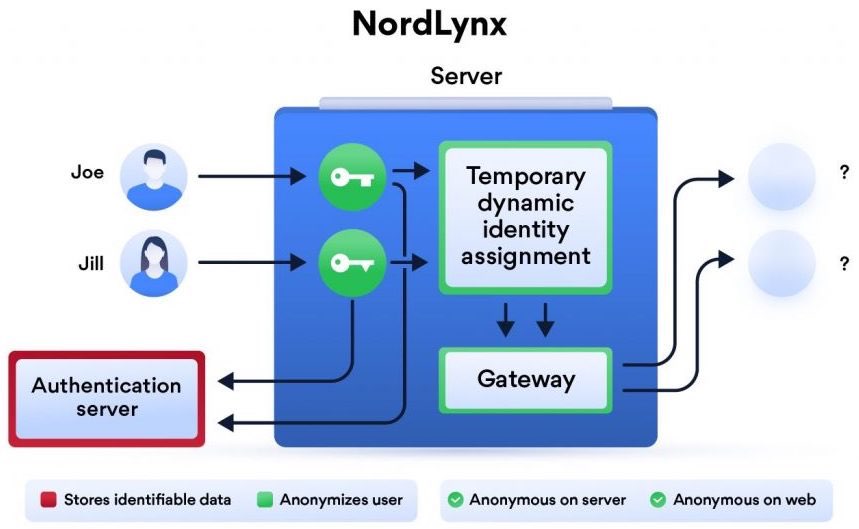
You can get more info on NordLynx and NordVPN on their website here.
Mullvad and OVPN erase IP address logs after the VPN session ends
Another way VPN providers have addressed the problem with logs is to configure their servers to erase data logs when the session ends.
Two examples of this are Mullvad and OVPN, both of which are secure VPN services based in Sweden.
OVPN explains:
We have programmed our VPN servers so that user information is not stored forever in the VPN server’s memory. Users who have not had a key exchange for the past three minutes are removed, which means we have as little information as possible.
Mullvad takes a similar approach:
We added our own solution in that if no handshake has occurred within 180 seconds, the peer is removed and reapplied. Doing so removes the public IP address and any info about when it last performed a handshake.
While Mullvad and NordVPN take a different approach to the logging issue, the end result is the same: no retained logs.
Now let’s look at another issue/drawback of WireGuard.
WireGuard does not assign dynamic IP addresses
VPN providers have also voiced concerns about how IP addresses are assigned with WireGuard.
Mullvad had this to say in a blog post:
We acknowledge that keeping a static IP for each device, even internally, is not ideal.
Why? Because if a user experiences WebRTC leaks, that static internal IP address could leak externally. As another example, applications running on your device can find out your internal IP, and if you’ve installed software that is malicious, it can also leak that information.
Similarly, OVPN also acknowledges these drawbacks:
At present, WireGuard requires that each key pair (which can be viewed as a device) is assigned a static internal IP address. This works without issues for smaller installations, but can quickly become complex when tens of thousands of customers need to connect. Development is underway for a model called wg-dynamic, but it is not yet finished.
Additionally, there are certain scenarios in which these IP addresses can be exposed, namely with WebRTC leaks.
Solutions
Both OVPN and Mullvad have come up with ways to securely generate keys and manage IP addresses. Each service allows you to regenerate keys and therefore rotate IP addresses, which helps to neutralize this problem. You can get specific details on each of the respective VPN websites.
Block or disable WebRTC – WireGuard relies on statically assigned IP addresses, and as we have covered before, a WebRTC leak can expose your internal and/or external IP address. This is not an issue with your VPN service, but rather a problem with your web browser. Here are some helpful guides to solve these issues:
- Disable or block WebRTC – Our guide has step-by-step information for all major browsers.
- Use the Firefox browser with WebRTC disabled. Firefox, unlike Chromium browsers, can simply disable WebRTC. See our Firefox privacy guide for instructions.
- Use a secure and private browser that limits data exposure.
Comparing WireGuard to Traditional Protocols
Among various VPN protocols, WireGuard has a lot going for it. Compared to traditional protocols like OpenVPN and IPSec, the WireGuard VPN protocol offers a faster, more secure, and more reliable connection. This is largely due to its streamlined code and efficient use of system resources, which result in faster connection times and improved performance.
However, older protocols like OpenVPN and IPSec have their merits. Here are some key points to consider:
OpenVPN has been around for much longer and has undergone multiple public audits, making it a favorite among privacy-focused users.
- WireGuard, on the other hand, is known for its speed and performance. It can be up to significantly faster than OpenVPN.
- If speed is your main concern, WireGuard is the way to go.
Looking at the future of WireGuard VPN
WireGuard’s future is looking bright. Even though it has some drawbacks, the improved speeds and upgraded security make WireGuard an appealing VPN protocol to consider. With ransomware and cybersecurity incidents in the news every week, using a secure and updated VPN protocol has its benefits.
Many VPN services have adopted WireGuard into their infrastructure as it becomes more popular with VPN users worldwide. With improved speeds, reliability, and upgraded encryption, we can expect WireGuard’s popularity to continue growing.
The VPN protocol itself, however, certainly has room for improvement. It remains flawed from a privacy standpoint with the issues we discussed above. However, many VPNs have already found good workarounds to ensure user privacy while still enjoying the benefits that WireGuard offers.
Now that WireGuard has been fully released and incorporated into the Linux and Windows kernels, it is safe to say this VPN protocol is ready for mainstream use and the future is looking good.
Check out our other WireGuard VPN guides:
This WireGuard VPN guide was last updated on January 11, 2024, with new information.

I want to know how the F^%$ Secure VPN Wireguard got onto my system. I use AVG and it did not come with it when I installed it. It does not show up in program files and I can’t delete it.
Ha what you say is not what is !
Please read the article to find out WireGuard is only a VPN protocol. In this new and updated WireGuard VPN guide, we examine the strengths and weaknesses of this protocol, as well as the best VPNs that support WireGuard.
Maybe AVG (having a VPN function) offers the WireGuard protocol. Find the settings and disable that protocol or pick another protocol it’s VPN uses. None the less chill T Y because people aren’t going to pay your comments much interest – meaning no one cares to answer negativity.
I’ve been using Mullvad for my VPN provider because it allows me to use a wireguard client running on an OpenBSD machine (and which is in fact built in to the OpenBSD kernel). I’d like to try out other providers, but (not surprisingly) none of them provide clients for OpenBSD, and I haven’t found any indication on their web-sites whether it’s possible to use a third-party wireguard client. Are there any other providers whose solutions for mitigating wireguard’s security issues don’t require that their own specialized clients be used?
By way of a partial answer to my question, I’ve just received responses from NordVPN and ProtonVPN: both say that they are working on manual connection methods, but that at present it’s necessary to use their client applications.
I’m using the built in Wireguard with Fedora 36 with ProtonVPN. I doubt I’ll continue using that VPN after what I paid runs out. Proton’s codebase is a writhing horror of incompetence. Don’t use it unless you can compile it and even then it’s icky sticky.
I can only compile their encrypted email bridge software which is using GO and other bits of cruft. GO is Google’s excretion, some privacy that is. My other concern is their knack of dumping my speed to clogged drain flow right when I need the damn thing. Openvpn client is about 60% slower than Wireguard. Doesn’t matter which you use they’ll flush the speed down the drain.
It’s overpriced, if their servers are coded like their clients it’s probably just waiting to be pwned. I think the Linux client has three ancient libraries they’re carrying on their backs and handing out like candy to little kids to compile and use. Have fun with that.
However you can get a config and as best I can tell the security and speed are awesome due to Wireguard.
Go to ProtonVPN, login and get a configuration file with keys and settings generated. Use the information in that to configure your system.
For Fedora find the website blogs gnome org and look up Thomas Haller on that page. There will be a post about getting wireguard up with NetworkManager using nmcli and the generated config. This is very trivial to do but rubiks cube level to figure out on your own. Also don’t expect the freaks at Fedora/Gnome not to leak IP. Fixing that is not easy. Wireguard is NOT privacy friendly and it is NOT the VPN provider at fault. It’s damn near impossible to stop Fedora from blindly and stupidly bringing the link back up without the VPN. I’ve finally broken down and run another daemon process to slam the damn network off if I see any connection change. It’s brutal, dirty and stupid but works.
The privacy stuff is all on Linux probably due to systemd, gnome, redhate etal. Proton’s code might compromise privacy depending on just how bad it is. I have some view of what they publicly release and can only just the rest of them base on their code.
Yea it’s a real email. It’s tied to me. Sue me.
I use OVPN with Wireguard, they now have wireguard app for IOS, Windows and Linux (with full GUI on Linux!) , and I guess MacOS too. Although in beta2 for Linux and Windows, but they work nicely. In Linux especially, very stable. Now we are only waiting for Wireguard in their Vilfo router too.
I get around 475Mbit out of my 500Mbit cable with their VPN. I am satisfied with the way OVPN secures Wireguard (as explained on their site)