
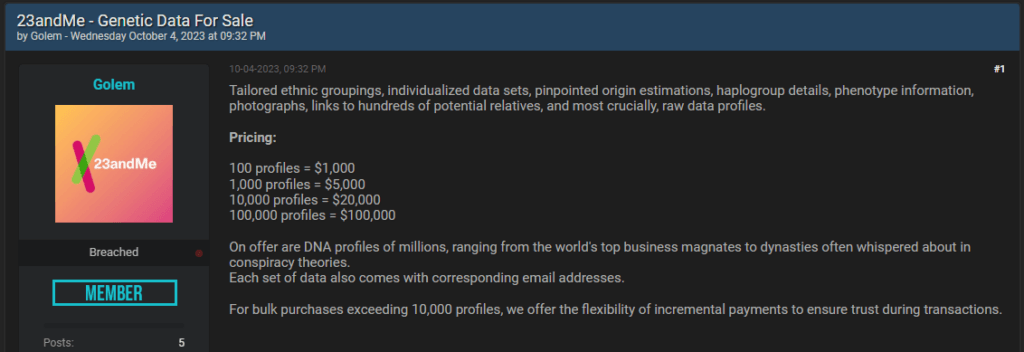
Hundreds of thousands of 23andMe profiles were made available for purchase by a cybercriminal on a hacker forum.
23andMe is a genetics testing company offering consumers the ability to discover their traits, health predisposition, carrier status, build family trees, and find unknown relatives based on their DNA overlaps.
The profiles allegedly stolen from 23andMe contain email addresses, names, DNA-estimated origin, phenotype information, photographs, and links to potential relatives. The cybercriminal offers various purchase options to encourage large bulk purchases, like $ 1,000 for 100 profiles, $5,000 for 1,000 profiles, $20,000 for 10,000 profiles, and $1 per hijacked account for those buying a massive dataset of 100,000.
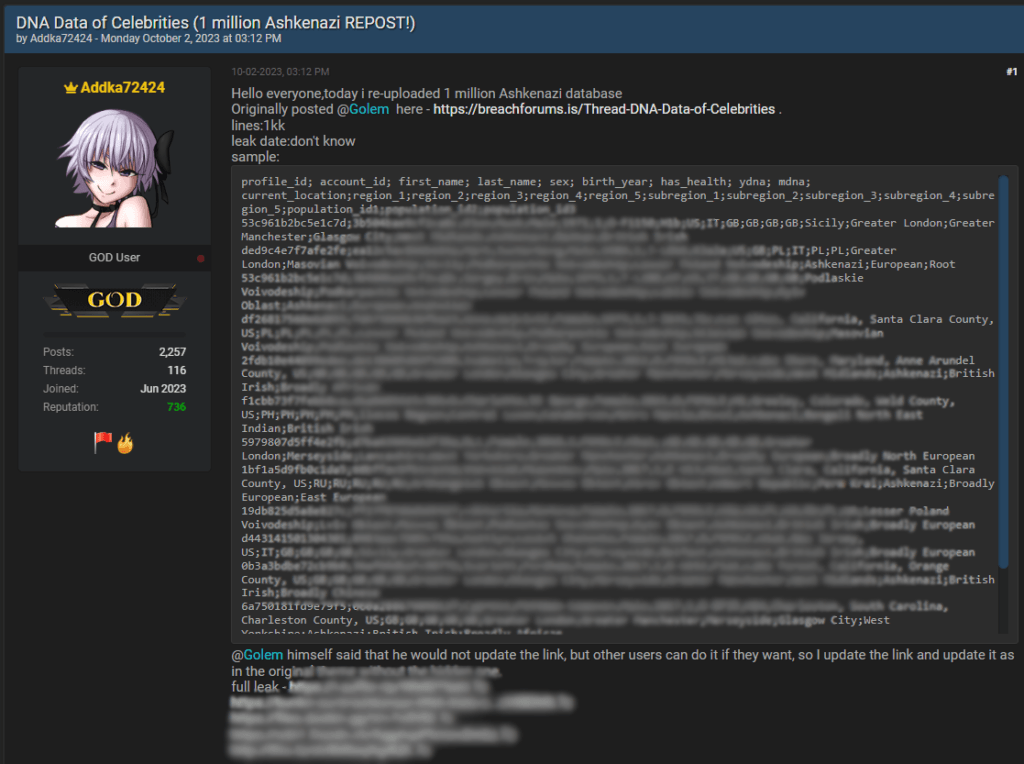
A few days before this sale became available, the same user offered a limited number of downloads for datasets containing a million profiles from a then-unnamed genetics firm, claiming the data included information on renowned individuals. Although the download count was limited to a few users, those who downloaded the packs continued to offer them through new posts on the same forum.
RestorePrivacy reached out to 23andMe to verify the authenticity of the threat actor’s claims and received assurances that hackers had not compromised the company’s systems. A spokesperson for the firm told us that the data breach results from unauthorized access to accounts achieved through attacks known as “credential stuffing.”
This is a cyberattack employing account credentials leaked from breached platforms, trying them out on other services, and hoping to gain access. To become victims of credential stuffing, the targets must follow the unsafe practice of “password recycling,” which means using the same password across multiple websites.
However, in this case, the cybercriminal sells a very large number of 23andMe profiles, which is unlikely to have been compromised directly using the aforementioned method. The firm’s spokesperson explained to RestorePrivacy that this is due to an optional feature that interconnects relatives and DNA matches on the platform, which was active on all the compromised accounts. This led to the magnification of the impact from a few breached accounts to the massive numbers we see on the forum post.
The DNA Relative Finder is an optional feature that members can opt-in to discover and meet others who share the same DNA. Due to enabling this feature, even accounts that have not been breached by credential stuffing and follow good security practices by setting a strong and unique account password were exposed to the cybercriminals.
The data for this subcategory of users does not include the rich genetic details available on the initially compromised accounts but still exposes a display name, profile photo, profile sex, birth year, predicted relationships to their match, portions of their genetic ancestry results, and locations.
23andMe will reset passwords on all accounts that appear to have fallen victim to unauthorized access, but their scanners might not catch all cases of hijacking, so users should take action themselves out of an abundance of caution. Also, all 23andMe users are recommended to enable two-factor authentication to protect their accounts from similar attacks in the future.

 Lyca Mobile Confirms Cyberattack, Hints at Possible Data Leak
Lyca Mobile Confirms Cyberattack, Hints at Possible Data Leak
I received a follow up email from 23 and me. I’m actually scared! My information was stolen and I put ALOT of my personal stuff in there because I’m adopted and I’ve been trying to find biological family though the site. SHIT! What do I do!?