
A few weeks ago we first reported on the Quantum ransomware gang claiming the Florida Department of Veterans Affairs as a victim. A spokesperson for the FDVA claimed the ransomware group was “unsuccessful” in attempts to install ransomware on FDVA servers. Quantum responded by releasing a sample of FDVA data on the Dark web. We analyzed the data (redacted below) and obtained exclusive commentary on the situation.
On May 27, 2022, the Quantum ransomware group claimed the Florida Department of Veterans Affairs (FDVA) as its latest victim. That same day, we published an article explaining the background of Quantum, its past victims, and the potential implications of an FDVA data breach.
Since the announcement was first published on Quantum’s Dark web blog site, the group has claimed to have a massive 1.1 TB of FDVA data. This data allegedly includes:
All possible data: veterans data, employees data, financial data, HR data, contracts with suppliers, tax and ssn [social security numbers] data and so on
– Quantum ransomware group
Here is Quantum’s post claiming the FDVA data breach:
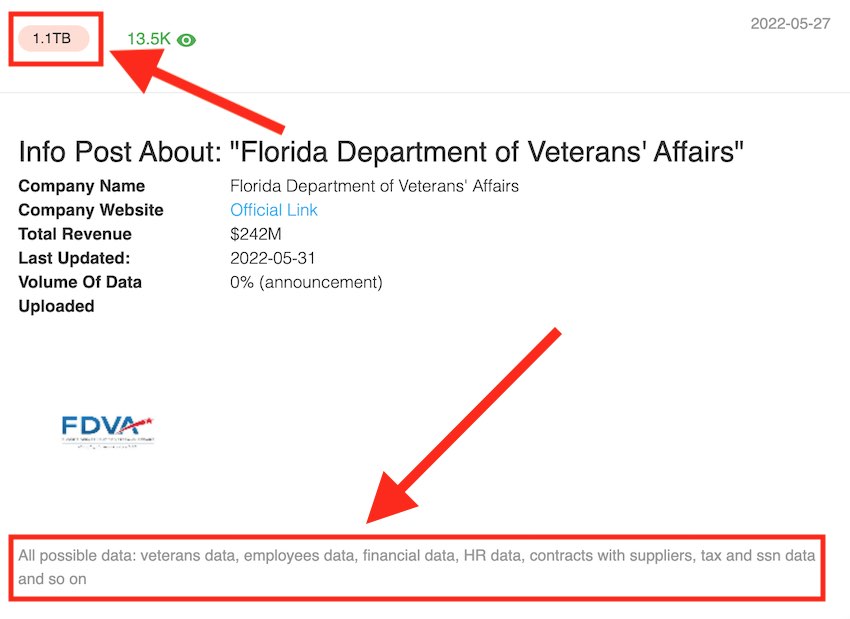
Source: RestorePrivacy.com
Following our story on the topic, a USA Today reporter contacted the FDVA for comment.
The FDVA spokesperson told the reporter that Quantum was “unsuccessful” in its attempt to install ransomware.
The FDVA’s wording here is interesting. Note that the FDVA spokesperson does not explicitly deny that Quantum gained access to FDVA servers.
Quantum responds by releasing FDVA data sample
Just a few days later, we observed that Quantum had updated its Dark web blog post to include a sample of FDVA data for anyone to download and view.
The sample size is about 47 MB, making it less than .005% of the total (claimed) data exfiltrated from FDVA servers.

Source: RestorePrivacy.com
As noted in the original article on the situation, I have no reason to doubt Quantum’s claims based on the group’s past exploits and track record. The publishing of this data further bolsters the group’s claims and raises questions about the FDVA response.
We analyzed the data sample published by Quantum and found it to contain lots of sensitive data from FDVA employees, veterans, and job applicants. Here is an overview of the information contained in the FDVA data sample analyzed by RestorePrivacy:
- Employee names (first, last, and middle), social security numbers, employment records, and contact information
- Internal revenue and financial data
- Employee litigation and court documents
- Employee fraud investigations
- Budget and procurement documents
- FDVA staff who have tested positive for COVID
- Employee evaluations
- Employee physical addresses, phone numbers, email addresses, employment history
- People who have previously applied to work at the FDVA: physical addresses, phone numbers, email addresses, employment history
FDVA employee names, social security numbers, and employment data
One document we analyzed was a spreadsheet from a “Payroll” sub-folder. This spreadsheet included FDVA employee names, social security numbers, position titles, and employment information. Here is a redacted sample of the first ten lines.
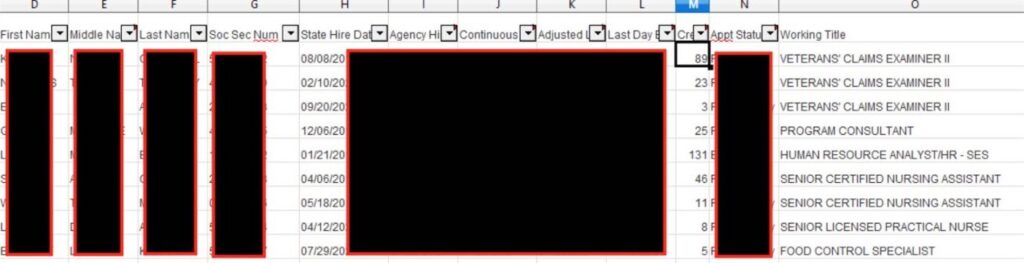
Source: RestorePrivacy.com
Aside from the spreadsheet sample above, there were other payment documents leaked that included FDVA employee names, social security numbers, and salary data.
Based on public records searches, all of the names and data appear to be authentic and match up with FDVA employees.
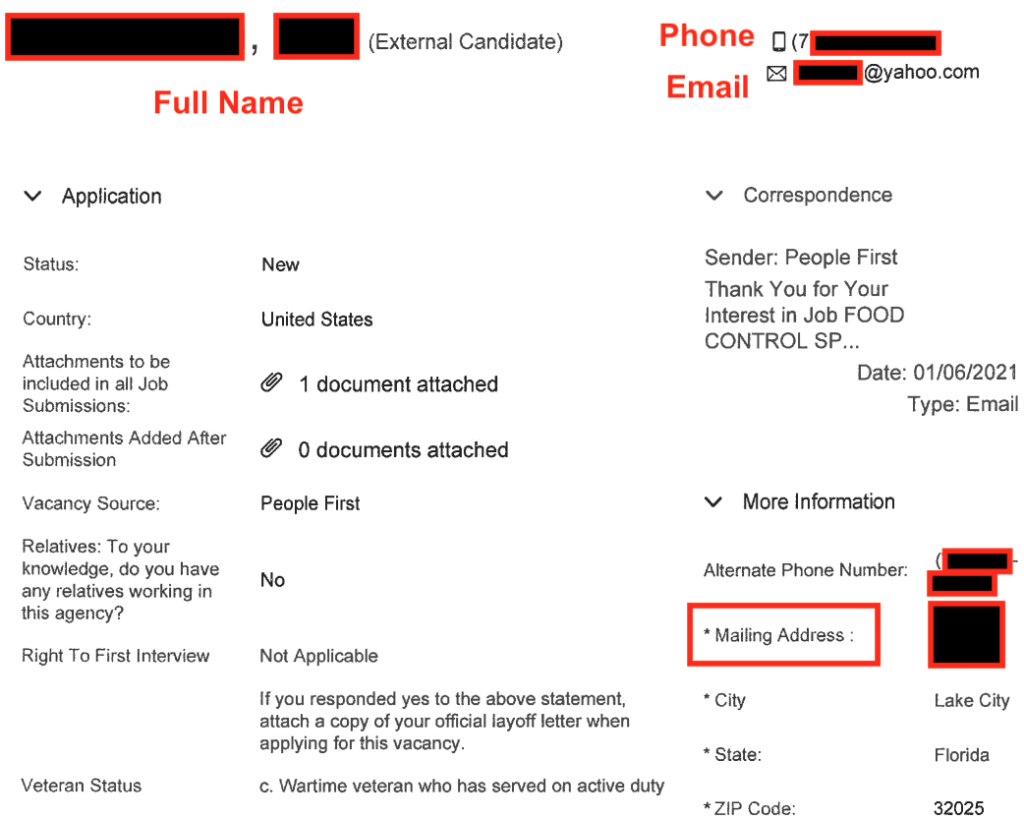
Military veteran records and job applications
The HR sub-folder also included a sample of data from people who have applied to work at the FDVA. These records included names, phone numbers, email addresses, and private military records, including DD-214 forms. The DD-214 includes the veteran’s name, date of birth, social security number, and military service data.

Source: RestorePrivacy.com
The data sample also included past FDVA job applications, which contained first and last name, email, phone, physical address, and career experience.
There are many other documents from Quantum’s data sample. And as noted above, this release is only a tiny sample of the total 1.1 TB of FDVA data that Quantum claims to have exfiltrated from FDVA servers.
Quantum plans to sell or release all FDVA data
In researching this situation, we reached out to both the FDVA and Quantum to provide more information. The FDVA’s response to our request concluded with, “We can’t confirm or deny” the cyberattack. This was posted in our original story here.
Quantum also provided RestorePrivacy with a comment on the situation.
We’ve tried to contact with the FDVA officials regarding the leak, however they have always ignored us.
FDVA is a profit organization with high revenues, we’re also not a charity organization. We could come to the agreement, but in the end the data will be sold on the black market or fully published.
And believe me, this is not the largest organization on the list, majority of our targets do pay us, so they never get to the blog.
You can see that the group claims to have not reached an agreement with the FDVA and plans to release all of the FDVA data “on the black market or fully published.”
A full release of all FDVA data on the group’s Dark web blog site would not be out of the ordinary. Other past victims have suffered the same fate after failing to reach an agreement with Quantum.
Consequences of an FDVA data breach
If the group’s claims prove to be legitimate, and the data is leaked, it could expose thousands of veterans, FDVA employees, and associated personnel to serious risk and fraud. Private data is a valuable tool for targeting individuals with:
- Identity theft and fraud – When criminals use personal data to impersonate individuals and carry out fraud and various types of attacks.
- Phishing attacks
- Social engineering attacks
- Hacked accounts
- Financial fraud
For cybercriminals, data is gold. This is especially true if the data includes social security numbers, which enable more attack vectors and financial fraud.
One trend we are seeing is for cybercriminals to create detailed profiles of their victims. This in turn opens up a variety of opportunities for fraud and criminal activities. The data included in these profiles can come from data breaches, other black market vendors, or publicly-available sources such as social media sites like LinkedIn or people search websites.
The more data that is available, the higher the risk of attack and fraudulent activity. Consequently, we have seen cases of class action lawsuits against organizations that have failed to secure data from cyberattacks, such as with Equifax a few years ago.
Related Reading on RestorePrivacy:

 Quantum Ransomware Gang Claims Florida Dept. of Veterans Affairs as Latest Victim
Quantum Ransomware Gang Claims Florida Dept. of Veterans Affairs as Latest Victim
Any updates from FDVA on this breech which they are denying?
https://www.bleepingcomputer.com/news/legal/surfshark-expressvpn-pull-out-of-india-over-data-retention-laws/
Vets deserve better than this. Come on VA, get your act together.
I think there should be some new way of our identity presence developed so that cyberattacks won’t harm our privacy, because they are becoming a real nightmare, can ruin people’s lives, and are relatively too easy way to earn huge money that next serves maintaining this activity, and hard to fight with.
This is clearly a lose-lose situation. Both options are bad.
Either the criminal hackers get a big payout to further fund their nefarious activities, or veterans and FDVA employees have all of their data released thereby exposing them to fraud and identity theft.
Both options suck.