
Oregon and Louisiana authorities have alerted their citizens that hackers have accessed and stole sensitive personal details stored in their systems.
The Oregon Driver & Motor Vehicle Services informed via an alert published on its website, that the attackers exploited a flaw in a software product called MOVEit, which Oregon DMV has been using since 2015, to breach its systems.
“Some publicly available information was included as well as some personal information (PI). Individuals should assume information related to their active license or ID card information is part of this breach.”
– Oregon DMV
The agency’s spokesperson Michelle Godfrey has shared additional information with local media outlets, explaining that the breach occurred two weeks ago, on June 1, 2023, impacting roughly 90% of the state’s driver’s license and ID card files. This corresponds to about 3.5 million documents falling into the hands of hackers.
The agency responded to the security incident two hours after the realization of the breach, locking down all systems, informing the authorities, and engaging IT experts in investigation, remediation, and system restoration works. Godfrey stated that they couldn’t inform the public earlier because the internal investigation had not progressed enough to be in a position to determine what data had been compromised.
Because Oregon DMV cannot determine which people have been impacted and what identities correspond to the unaffected 10%, they advise everyone with an active Oregon ID or driver’s license to assume their personal data has been compromised. In this context, every Oregon citizen is advised to remain on high alert for any transactions they don’t recognize and report them to their bank as soon as possible.
The situation is similar in Louisiana, where the office of motor vehicles informed that they too were using MOVEit, resulting in the exposure of names, addresses, SSNs, license numbers, and vehicle registration details for the entire population (4.6 million) of the state.
MOVEit Meltdown
The vulnerability exploited in MOVEit, a secure file transfer platform, is CVE-2023-34362, and it’s an SQL injection flaw that leads to remote code execution on exposed servers. The flaw was a zero-day, meaning that it was already under active exploitation at the time of its discovery.
The threat group that exploited the flaw was Clop, a notorious ransomware gang known for performing similar supply-chain compromises, such as the GoAnywhere MFT hacks in January 2023 and the Accellion FTA hacks in December 2020.
In the case of MOVEit, Clop has managed to hit high-profile targets, including the gas giant Shell, BBC (through Zellis), the U.S. states of Missouri and Illinois, the University of Georgia, and many more. Having set the deadline for victims to respond to the threat actor’s demands by June 14, Clop has already started the blackmail against several breached entities by publishing their data on its extortion portal.
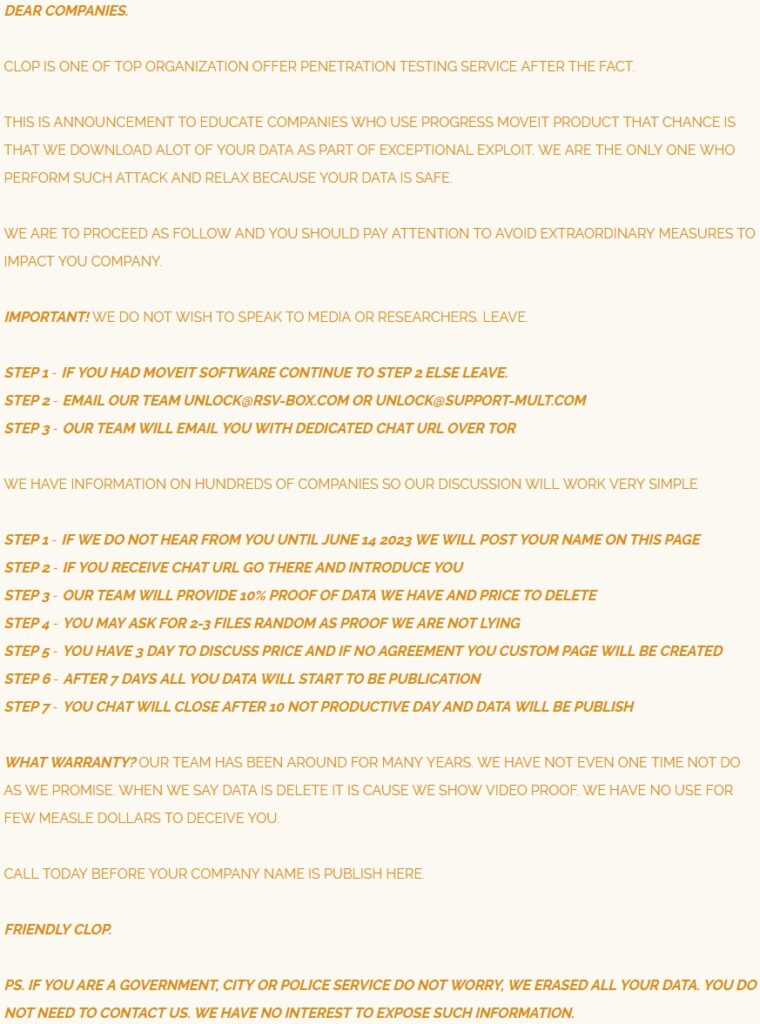
RestorePrivacy
This process appears to be gradual, as Clop has not published the data of all its victims yet. Also, while Clop promised to delete government or city data stolen from the MOVEit hacks, it seems that Oregon DMV and Louisiana OMV do not fall into the category to be spared, so the danger for millions of people remains.

 Entire Population of Turkey Had Personal Data Exposed Online
Entire Population of Turkey Had Personal Data Exposed Online
Something that confuses me is how many spelling Mistakes there were in the threat. How can people who make that many mistakes hack into secure government data then threaten to expose it if anything they would screw it up with spelling mistakes but I could be wrong.
They are probably not native English speakers.
Fair point
Thank you for your new post Heinrich! that is a big impact. We should learn as much as possible everyday to be protected. I really appreciate your effort. I love your site, I learn a lot from you and Sven.