
Threat actors continue to bet on the popularity of VPN apps to distribute their malware payloads onto the computers and mobile devices of unsuspecting users.
Two cases brought to light by two cybersecurity companies highlight the dangers of trusting dubious VPN publishers and what the repercussions might be for users.
LetsVPN Campaign
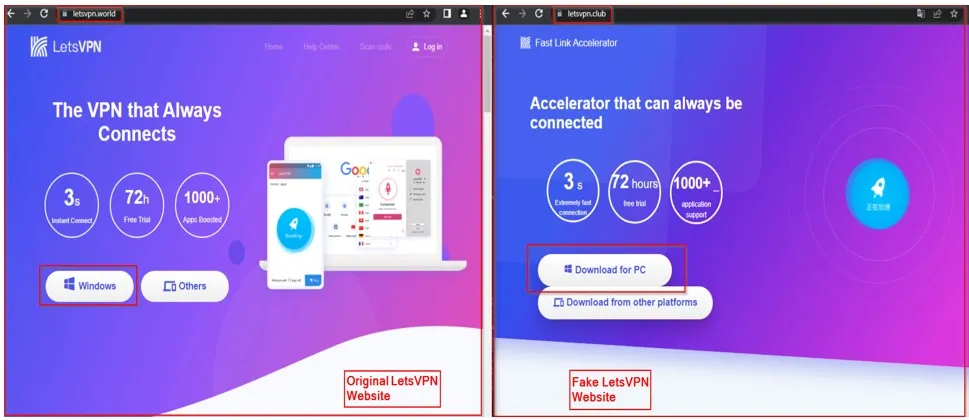
The first case, discovered by the Cyble Research and Intelligence Labs (CRIL), involves websites that mimic the LetsVPN brand, a fairly popular VPN product by LetsGo Network, with over a million downloads on the Google Play store.
The threat actors use the following typosquatting or simply misleading domains to distribute three distinct malware families:
- letsvpn[.]club – drops ‘BlackMoon’
- letsvpn[.]cyou – drops ‘BlackMoon’
- latavpn[.]world – drops ‘Farfli’
- letevpn[.]world – drops ‘Farfli’
- letsvpnaa[.]com – drops ‘Farfli’
- lestvpn[.]com – drops ‘KingSoft’
Users end up on these malicious websites thanks to Black SEO, malvertizing, phishing, and malicious instant messages.
Cyble
BlackMoon is a banking trojan that has been in circulation and active development for nearly a decade, capable of capturing the victim’s keystrokes, performing web injections (phishing webpages), providing remote access capabilities, and even automating banking account hijacking.
Farfli is also a keylogger and RAT (remote access tool), but it can additionally execute commands on the infected device, drop more payloads, and exfiltrate files from the victim’s system.
KingsSoft is an adware that generates revenue for its operators by serving victims with excessive and intrusive ads that disrupt their regular web browsing experience. Moreover, it can collect the user’s browsing history, search queries, and personal information and can also facilitate downloading additional payloads.
Liberty VPN Clone
The second case, discovered and reported by Cyfirma, concerns a clone of Liberty VPN, called ‘iKHfaa VPN,’ which is available on the Google Play store for Android phones.
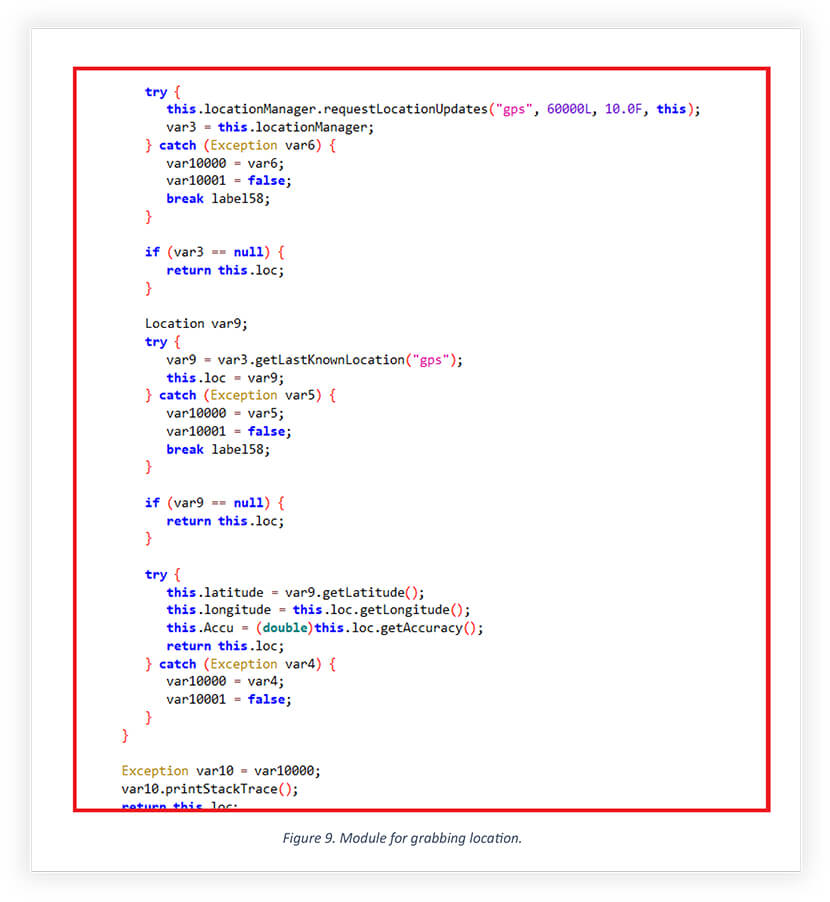
IKHfaa VPN features the same code as Liberty VPN, with the only addition being a location-grabbing module that tracks users in real time whenever they activate the GPS on their devices. Additionally, the app reads the user’s contact list and exfiltrates it to its operators.
Cyfirma
The analysts assume that victims are led to download this VPN app after attackers send them messages on WhatsApp or Telegram, convincing them of the legitimacy and superior quality of the app.
Cyfirma reports that this app was created by the DoNot APT (advanced persistent threat) hackers, and it is being used in cyberespionage operations against specific targets in the South Asian region. However, despite it not being a threat to the broader VPN user community, it is still a reminder that apps on legitimate software platforms and repositories shouldn’t be blindly trusted.
It’s also important to note that dubious free VPN services are usually a privacy and security disaster. Numerous studies have shown that free VPN apps are often riddled with malware and trackers to infect devices and collect data, thereby monetizing the “free” service. Consequently, users are better off going with a well-known, premium VPN service.

 Hackers Stole Millions of Driver’s Licenses and IDs from U.S. States
Hackers Stole Millions of Driver’s Licenses and IDs from U.S. States
This is happening a lot these. So many fake apps which are wolves in sheep clothing. This is specially the case with VPN apps. Because surveillance and censorship is on the rise and so is Geo-restriction and IP bans. To get around all of these VPN are the perfect tools and these days they are more popular than ever. So much so that earlier what used to be a niche tool used by corporate and experts is now a mainstream tool and everyone is aware of them and are increasingly using them. Since a quality VPN costs money and most people do not want to pay, they resort to using free VPNs untrustworthy and unreputed providers which harvest user data, are full of advertisements and provide low quality service and are sometimes malicious as in the above case.