
A well-known threat actor with a long list of previous breaches is selling private data that was allegedly collected from 70 million AT&T customers. We analyzed the data and found it to include social security numbers, date of birth, and other private information. The hacker is asking $1 million for the entire database (direct sell) and has provided RestorePrivacy with exclusive information for this report.
Update: AT&T has initially denied the breach in a statement to RestorePrivacy. The hacker has responded by saying, “they will keep denying until I leak everything.”
Hot on the heels of a massive data breach with T Mobile earlier this week, AT&T now appears to be in the spotlight. A well-known threat actor in the underground hacking scene is claiming to have private data from 70 million AT&T customers. The threat actor goes by the name of ShinyHunters and was also behind other previous exploits that affected Microsoft, Tokopedia, Pixlr, Mashable, Minted, and more.
The hacker posted the leak on an underground hacking forum earlier today, along with a sample of the data that we analyzed. The original post is below:
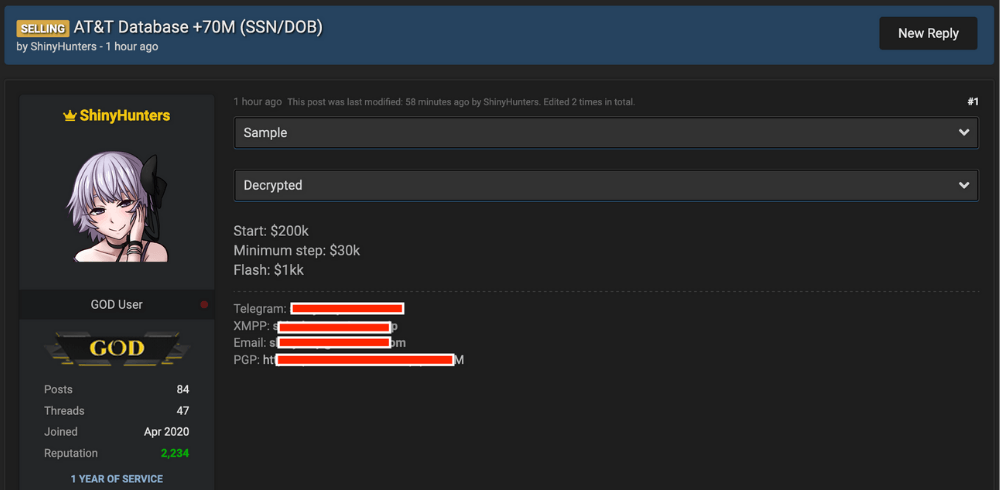
We examined the data for this report and also reached out to the hacker who posted it for sale.
70 million AT&T customers could be at risk
In the original post that we discovered on a hacker forum, the user posted a relatively small sample of the data. We examined the sample and it appears to be authentic based on available public records. Additionally, the user who posted it has a history of major data breaches and exploits, as we’ll examine more below.
While we cannot yet confirm the data is from AT&T customers, everything we examined appears to be valid. Here is the data that is available in this leak:
- Name
- Phone number
- Physical address
- Email address
- Social security number
- Date of birth
Below is a screenshot from the sample of data available:
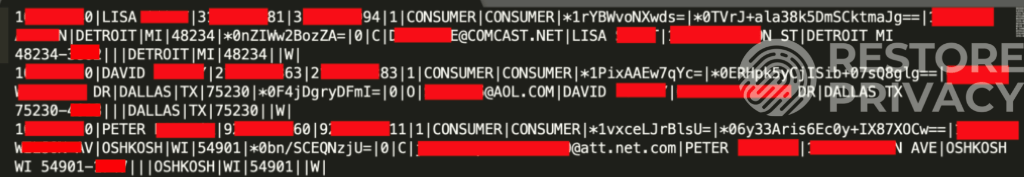
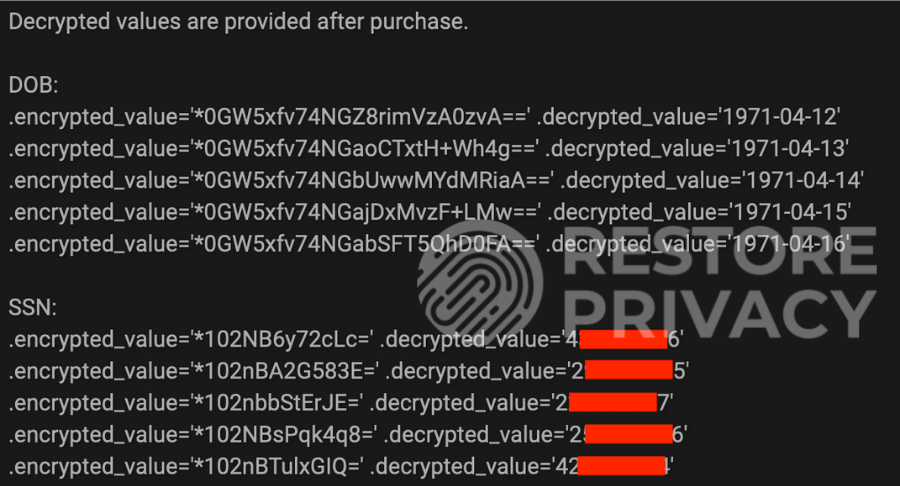
In addition to the data above, the hacker also has accessed encrypted data from customers that include social security numbers and date of birth. Here is a sample that we examined:
The data is currently being offered for $1 million USD for a direct sell (or flash sell) and $200,000 for access that is given to others. Assuming it is legit, this would be a very valuable breach as other threat actors can likely purchase and use the information for exploiting AT&T customers for financial gain.
Hacker provides RestorePrivacy with additional information
We made contact with the hacker who confirmed that all data is from AT&T customers in the United States. The hacker would not tell us how the data was obtained.
The hacker also told us that he obtained three encrypted strings of data, with the first two being social security numbers and date of birth. He believes the third encrypted string is the user pin, but is not yet sure.
Potential impact for AT&T users
A data breach of this scale is a very serious issue, especially if the data includes detailed private information, particularly social security numbers.
Specifically, AT&T users could be at risk of the following attacks:
- identity theft
- phishing attempts
- social engineering attacks
- hacked accounts
- social security scams
We strongly urge AT&T customers to be vigilant against any suspicious activities and/or compromised accounts on other platforms. The website haveibeenpwned, which is maintained by cybersecurity researcher Troy Hunt, is a useful tool to check if your personal information has been compromised.
UPDATE: AT&T comments on the situation
AT&T has provided us with a comment on the situation, posted below in its entirety:
Based on our investigation today, the information that appeared in an internet chat room does not appear to have come from our systems.
-AT&T Corporate Communications Officer (sent to RestorePrivacy on August 19, 2021).
This is an interesting response. The claim that this was posted in an “internet chat room” is simply not correct. It was posted in a well-known hacking forum by a user with a history of large (and verified) exploits.
ShinyHunters replied to AT&T’s statement by telling RestorePrivacy:
It doesn’t surprise me
I think they will keep denying until I leak everything
ShinyHunters’ past exploits and breaches
We should also point out that ShinyHunters is a well-known threat actor with a laundry list of previous exploits. You can see a small sample on the hacker’s Wikipedia page here. This gives further credibility to the hacker’s claims in light of AT&T’s initial denial. The hacker’s previous exploits include:
- Microsoft – 500 GB of Microsoft source code stolen and sold online
- Mashable – 5.22 GB of company and staff data
- Tokopedia – 91 million user accounts
- Pixlr – 1.9 million user accounts
- 123RF – 8.3 million user accounts
- Wattpad – 270 million user records
- Pluto TV – 3.2 million Pluto TV user records
- Animal Jam – 46 million accounts leaked
- WedMeGood – 41.5 GB of user data
- BigBasket – 20 million user accounts
- Dave.com – 7 million user accounts
- Couchsurfing.com – Data from 17 million users
- Dunzo – 11 GB of company data
- Nitro PDF – 77 million user records
- Bhinneka – 1 million user accounts
- Minted – 5 million accounts leaked
- ProctorU – 444,267 accounts
- Bonobos – Full backup database with 7 million customers and 1.8 million registered users
- Swvl – 4 million users
- Mathway – 25 million records
- Wishbone app – 40 million user records
This list is not exhaustive. You can find more breaches and exploits from ShinyHunters that have been verified and discussed on various hacking forums, particularly RaidForums.
Hacker is willing to work with AT&T on an “agreement”
The hacker told us he is willing to work with AT&T directly if they want the data removed — for a price.

We will continue to monitor the situation and update this article as new information unfolds.

 Windscribe VPN Security Breach: Servers and Private Key Seized
Windscribe VPN Security Breach: Servers and Private Key Seized
I have been trying to secure my att prepaid Phones for several months. I sent plenty of evidence to the office of the president.. FCC.. I can’t get into my account to delete it and remove my information.. I don’t control the two accounts that are linked by email address.. prepaid login in are just your phone number to log in.. never email.. At&T knew about this breech.. the prepaid customer service is very different than post paid contract phones. I still can’t close or secure my account.. The FCC had complaints with AT&T prepaid consumers and have been charging customers for service that the government 🛜 program pays for.