
Lumen Black Lotus Labs has discovered an AVrecon RAT (Remote Access Trojan) campaign that has been underway for at least two years, infecting small office and home routers with a botnet payload.
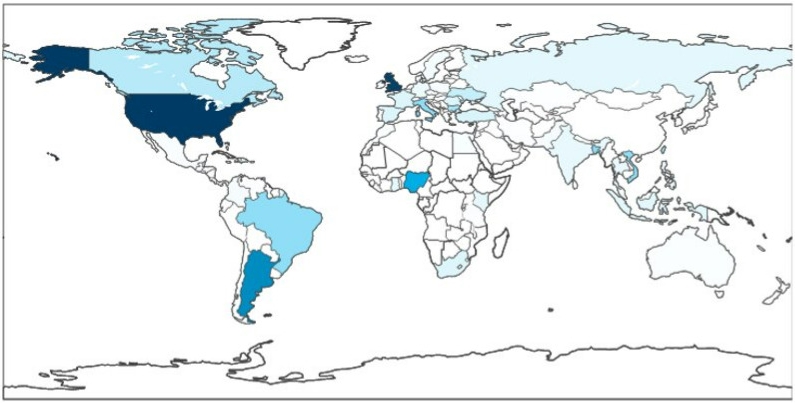
Black Lotus Labs reports that the campaign focuses mainly on the U.S. but has claimed victims globally. Currently, the botnet counts over 70,000 enslaved devices, communicating with 15 unique command and control (C2) servers.
Black Lotus Labs
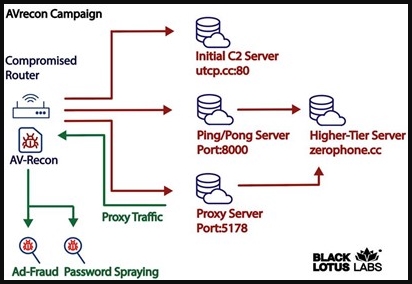
The attackers’ goal appears to be to use the compromised routers to perform advertising fraud, “password spraying” attacks, and data exfiltration. Home routers have a more trustworthy profile thanks to their regular activity and “clean” IP address history, so they can be abused for bypassing security measures and blocks that impact most bot farms and datacenter-provided IPs.
Residential proxies is a growing cybercrime industry that rent network traffic routers to malicious actors, enabling them to perform nefarious tasks at a much better acceptance rate, making malicious traffic appear as if it originates from home or small office computers.
Black Lotus Labs
AVrecon Capabilities
AVrecon spreads to poorly maintained, misconfigured, or neglected routers that are plagued by well-documented vulnerabilities for which there are publicly available exploits. However, Black Lotus Labs has not specified what flaws the campaign targets, so the malware might also compromise devices by brute-forcing weak passwords or using dictionary attacks against weak default credentials.
Once the infection has been established, AVrecon ensures that it is only running a single instance to avoid targeting the same devices and then collects information about the host device, such as the kernel version, CPU, memory usage, hostname, etc.
Next, the malware constructs the parameters for communicating with the C2 servers, configures a proxy, and waits for the reception of commands sent through the spawned reverse shell. The commands include updating its C2 configuration, fetching additional payloads and executing them, downloading an update for the malware, and more.

Black Lotus Labs
Black Lotus monitored AVrecon’s communication exchange from clients to the C2 and discovered that most activity happens in the first couple of days after the infection. The mean lifespan of an AVrecon bot is roughly a week. The analysts explain that this is likely due to the lack of a persistence mechanism on the malware, which terminates it if victims reset their routers. Possibly, the devices are abandoned after being abused for malicious purposes, resulting in them being added to block lists.
How to Defend
Signs of an infected router include connection interruptions, poor network performance, unexplained changes in device settings, DNS changes, and excessive heat. However, those signs may not be as noticeable in subtle attacks that don’t use much of the victim’s available bandwidth.
Users should follow good security practices and apply the available firmware updates for their router model, downloaded from the vendor’s website. Moreover, remote access to admin panels should be closed if not needed, and default admin account credentials should be changed with something unique and long.

 Razer Investigating Data Leak After Files Appear on Hacker Forum
Razer Investigating Data Leak After Files Appear on Hacker Forum
Leave a Reply