
A secure browser that protects your privacy is a critical tool for staying safe online and keeping your data secure from third parties. We have been reviewing, testing, and ranking browsers for the past six years and this guide contains the latest recommendations for 2024.
Do you want a secure browser that truly keeps your data private? Well, you may be surprised by how much of your data is actually getting exposed.
WARNING: Many browsers today are actually data collection tools for advertising companies. This is the case for Google Chrome, the largest and most popular browser. By collecting data through your browser, these companies can make money through their advertising partners with targeted ads. We see this same privacy-abusing business model with search engines, email services, and even free mobile apps.
Unless properly configured, most browsers contain lots of private information that can be exploited – or simply collected – by various third parties:
- Browsing history: all the websites you visit
- Login credentials: usernames and passwords
- Cookies and trackers: these are placed on your browser by the sites you visit
- Autofill information: names, addresses, phone numbers, etc.
And as we will explain further below, using “private” or “incognito” browsing will not protect you. Your IP address will remain exposed and various third parties can still track all of your activities. And even legal action may not protect you. Here is a recent headline related to a lawsuit against Google for capturing data from users who are in Incognito mode. This case has been going on for years now and isn’t close to resolution yet.
And even with a locked-down and hardened browser, exploits may still be found that expose your data and possibly your identity. For example, in 2021 there was a spate of zero-day exploits in Google Chrome with various effects up to allowing hackers to remotely execute code on affected systems. We discuss some other privacy issues (and solutions) in our guides on browser fingerprinting and also WebRTC leaks.
But don’t panic. Effective solutions and tools exist to deal with these problems and we cover them in detail in this article. In this browser security and privacy guide, we’re going to explain the following topics:
- Best secure browsers that respect your privacy
- Problems with other browsers
- Browser privacy compartmentalization
- Secure browser add-ons
- “Private browsing” mode is NOT very private (and why you need a VPN in addition to a secure browser)
Incognito / Private browsing mode still leaves you EXPOSED
When using “private” or “incognito” browsing mode in your browser, your real IP address and location are still being revealed to every website, ad, and tracker that loads in your browser. Additionally, all your activities remain visible to your internet service provider (ISP). And at least here in the United States, ISPs log everything you do online and share the data with many other parties. This is why it’s critical to use a good VPN for basic digital privacy.
The best way to achieve true privacy while hiding your real IP address and online activities is to use a secure browser together with a good VPN. This protects you at both ends of the line, and in the middle too.
The secure browser will protect you as described in this article, while the VPN will protect your identity by hiding your real IP address and location. The VPN will also encrypt your traffic so your ISP (and any other snoops out there) cannot see your activities online. Here are our top three recommendations from the best VPN list that we have tested and reviewed:
- NordVPN: A fast, secure, audited VPN with advanced privacy features, built-in ad blocker, and a strict no-logs policy, based in Panama (see the 74% off coupon).
- Surfshark VPN: A no-logs VPN service with a large lineup of privacy and security features, based in The Netherlands.
- ExpressVPN – This is a secure and reliable VPN that boasts some great privacy features and also works well for streaming. It is based in the British Virgin Islands.
Now let’s examine the most secure browsers you can combine with a VPN for maximum privacy.
Secure browsers that protect your privacy
In this section we will examine the best browsers based on two main factors:
- Security: How well does the browser protect you from hackers, vulnerabilities, and online exploits?
- Privacy: How much data is the browser itself collecting about you and who is this data being shared with? How does the browser protect your privacy?
Conflicting opinions! Just like with Tor, opinions about browser privacy and security can be wildly divergent and contentious.
This guide is not meant to sell everyone on one browser that beats all others. Rather, it is a summary of information about different web browsers that do well with both privacy and security. Choose the best browser for you based on your own unique needs and threat model.
Here are the most secure and private browsers for 2024:
1. Brave: The most secure and private browser (for both desktop and mobile)

Brave is arguably the most secure browser with simple, out-of-the-box privacy. It is a Chromium-based browser that is fast, secure, and privacy-focused by default. It has a built-in ad blocker and browser fingerprinting protection, while also giving you access to numerous add-ons and extensions. The main developer behind Brave is Brandon Eich, who formerly worked for Mozilla.
To summarize this browser, Brave is based on open-source Chromium, but configured for more privacy. It does well with its default privacy settings and extra features. Here is a brief overview:
- Blocks ads and trackers by default
- Protects against browser fingerprinting and even offers fingerprint randomization
- Built-in script blocker
- Blocks all third-party storage
- Easy access to the Tor network
One of the reasons we like Brave is because it offers simple, out-of-the-box privacy by default. This makes it ideal for those who do not have the time, patience, or know-how for browser customizations and tinkering. Brave can also be used with Chrome extensions, making it an ideal alternative for Chrome. Just download it and you’re good to go.
Tor network – Brave also has a feature that allows you to access the Dark web by simply opening a new window with Tor. We discuss this feature in our guide on how to access the Dark web safely.
Ads – Brave has received some criticism for its ads program, which allows users to “view non-invasive ads without compromising your privacy.” While some people find it hypocritical that a privacy-focused browser has its own ad program, we also see it as a secure funding source. And with many browsers financially struggling, it appears that Brave’s business model is securing this browser’s future and ability to continue to innovate its products.
Here are some more results of Brave’s continuing innovation:
- Brave has developed a private search engine called Brave Search, which is now the default search engine when you do a new installation of the Brave browser. In March of 2023, they added the AI-powered Summarizer to Brave Search.
- A cookie consent blocker, which at least partly frees you from the endless hassle of accepting or rejecting cookies at new sites you visit.
- Brave News, an RSS news reader.
- Brave Wallet, a built-in cryptocurrency wallet.
You can read more about Brave’s privacy features here.
https://brave.com
2. Firefox (when modified and tweaked for privacy)

Firefox is a great all-around browser for privacy and security. It offers strong privacy protection features, many customization options, excellent security, and regular updates with an active development team. The newest versions of Firefox are fast and lightweight with many privacy customization options.

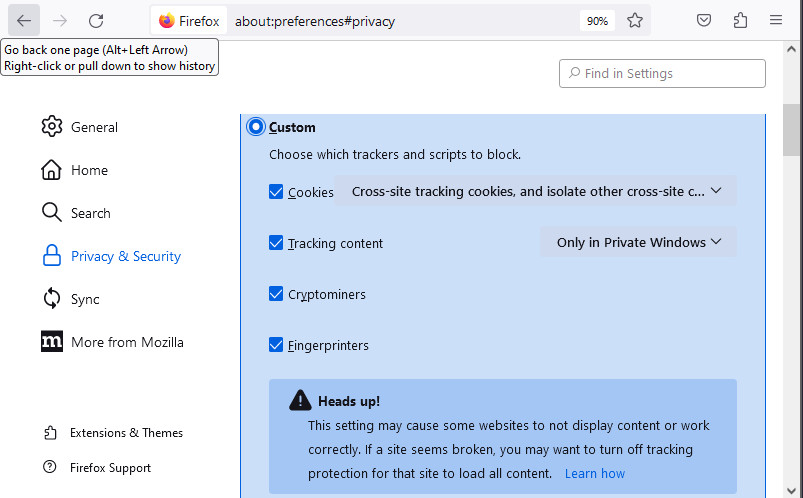
Out of the box, Firefox is not the best for privacy, but it can be customized and hardened, and we show you exactly how in our Firefox privacy modifications guide. Be sure to disable telemetry in Firefox, which is a feature that will collect “technical and interaction data” and also “install and run studies” within your browser.
Within the Privacy & Security settings area, there are many useful customization options for different levels of privacy: Standard, Strict, or Custom.
Another great benefit of Firefox is the ability to use numerous browser extensions that can enhance your privacy and security. We’ll go over some of these extensions later in this article.
Firefox highlights:
- Open source code that has been independently audited
- Active development with frequent updates
- Excellent privacy features and customization options
- Total Cookie Protection (TCP) to prevent cookies from tracking you as you move around the web
- Firefox View to easily return to recently used sites
- Built-in ad blocker
- Many browser extensions supported
- Telemetry and tracking need to be manually disabled
- Other modifications necessary for extra privacy and security
If you want to keep using older add-ons that are no longer supported by the latest Firefox release, you can go with the Firefox Extended Support Release (ESR). For those times when you want the maximum privacy viewing content on your Android phone, you could try Firefox Focus.
For additional customization and privacy settings, check out our Firefox privacy guide.
https://www.mozilla.org/firefox
3. Tor browser

Next up we have the Tor browser. The Tor browser is a hardened version of Firefox that is configured to run on the Tor network. By default, the Tor Browser is a secure browser that protects you against browser fingerprinting, but it also has some disadvantages.
Because it uses the Tor network, which routes traffic over three different hops, download speeds with the Tor browser can be quite slow. The default version may also break some sites due to script blocking. Finally, there are drawbacks to the Tor network itself. These include:
- Malicious/dangerous exit nodes
- High latency
- Many websites block IP addresses originating from the Tor network
- Dependence on US government financing, leading some to claim the Tor network to be fundamentally compromised
See the pros and cons of Tor here.
Another option is to use the Tor browser with the Tor network disabled. In this sense, the Tor browser will work like the other secure and private browsers we’ve covered above. Additionally, you can simply run a VPN in the background. Like the Tor network, a VPN will also encrypt your traffic and hide your IP, but it will be much faster.
There’s a new browser out there that takes exactly this approach. It is a collaboration between Mullvad and the Tor project, and you can learn more about it in spot #6 on this list.
Be careful when adjusting the settings for the Tor browser, however, as this may compromise the browser’s built-in privacy and security features.
https://www.torproject.org/
4. Ungoogled Chromium browser

Ungoogled Chromium is an open source project to provide a Chromium browser, without the Google privacy issues:
ungoogled-chromium is Google Chromium, sans dependency on Google web services. It also features some tweaks to enhance privacy, control, and transparency (almost all of which require manual activation or enabling).
ungoogled-chromium retains the default Chromium experience as closely as possible. Unlike other Chromium forks that have their own visions of a web browser, ungoogled-chromium is essentially a drop-in replacement for Chromium.
UPDATE: Support for Ungoogled-Chromium has continued, but it has moved from its original github archive to the new archive linked below. It does require some technical skills to download this browser from the archives.
https://github.com/ungoogled-software/ungoogled-chromium
5. LibreWolf – A private and secure fork of Firefox

LibreWolf is a fork of Firefox that continues to grow in popularity. The project’s stated goals are to deliver a browser that is focused on privacy, security, and freedom. From the LibreWolf website:
LibreWolf is designed to increase protection against tracking and fingerprinting techniques, while also including a few security improvements. This is achieved through our privacy and security oriented settings and patches. LibreWolf also aims to remove all the telemetry, data collection and annoyances, as well as disabling anti-freedom features like DRM.
The website lists the main features of LibreWolf as:
- No Telemetry
- Private Search
- uBlock Origin pre-installed
- Enhanced Privacy
- Fast Updates
- Open Source code
LibreWolf is available for desktop operating systems, including Windows, Mac OS, Linux, and Open BSD. You can find installation instructions here.
One issue to keep in mind, however, is that there are no automatic updates. This means that you will need to manually update the browser, which is certainly a drawback to consider. Fortunately, LibreWolf frequently pushes these browser updates to the relevant archive managers, making it easier to update than it would otherwise be.
LibreWolf is always based on the latest version of Firefox. Updates usually come within three days from each upstream stable release, at times even the same day. Unless problems arise, we always try to release often and in a timely manner.
– LibreWolf FAQ section
This is definitely a browser to consider for those wanting more privacy and security on desktop operating systems.
https://librewolf.net/
6. Mullvad Browser – A privacy collaboration between Mullvad and Tor

When we talked about the Tor browser earlier in this article, we suggested using the Tor browser with the Tor network disabled and a quality VPN might be a better way to go than using the Tor network. We’re not the only people who feel this way. The Mullvad Browser is designed to do exactly this.
This privacy-focused web browser is a joint project between Mullvad VPN and the Tor Project. It incorporates the privacy benefits of the Tor browser such as tracker blocking and fingerprinting. But the Mullvad Browser isn’t designed to connect to the Tor network.
Instead of going through the Tor network, the Mullvad Browser is meant to be connected to the internet through a quality VPN. Obviously, the folks at Mullvad would love for you to use their browser with their VPN, but you don’t have to. In the image below I am using the Mullvad Browser to view this website through NordVPN.
This browser collaboration definitely has potential. To learn more about it, check out our recent article on this Mullvad – Tor project.
https://mullvad.net/en/browser
7. DuckDuckGo private browser (macOS, iOS, and Android)

The DuckDuckGo private browser is available for macOS as well as mobile devices running iOS or Android. It comes with lots of privacy-focused features by default. According to DuckDuckGo, their browser offers:
- Built-in tracking protection
- Encryption upgrades via Smarter Encryption technology
- Easy data management and clearing options
- Fast speeds
Issues with Microsoft trackers
One important thing to be aware of is that security researchers previously discovered that DuckDuckGo’s browser allowed Microsoft trackers. According to DuckDuckGo founder Gabriel Weinberg, this decision was based on a “confidential” agreement between DuckDuckGo and Microsoft.
Many people in the privacy community were outraged when the situation first came to light on Twitter here. There was clearly an element of hypocrisy going on here as we see DuckDuckGo castigate Google over the same practices. But last year, DuckDuckGo announced that they had reached an agreement to block Microsoft trackers.
Should you use DuckDuckGo’s privacy browser? I’d recommend that you consider some of the alternatives we recommend in this guide. That said, the changes DuckDuckGo has made to block the Microsoft trackers makes us much more comfortable with this browser. Ultimately, the choice is yours.
The DuckDuckGo private browser is available on both the Google Play and Apple stores.
8. Waterfox
Waterfox is a fork of Firefox that was maintained by just one person for many years. In February 2020, news broke that the developer of Waterfox sold out to a pay-per-click ad company called System1. However, in July 2023, news broke that Waterfox is once again independent:
I am happy to say that Waterfox is independent again. This change allows the community and myself to shape the browser’s future direction.
Waterfox Blog
Putting all that aside, Waterfox is a great option for those wanting Firefox with out-of-the-box privacy.
Waterfox website >>
Private browsers worth mentioning (but not necessarily recommended)
Here are a few private and secure browsers that didn’t make our recommended list but we think are still worth mentioning.
9. Bromite (Android)
Bromite is a Chromium-based browser for Android only (no desktop support). It comes with some great features by default, including ad blocking and various privacy enhancements.
Unfortunately, being a small project, Bromite suffers from infrequent updates. The last update was apparently in 2020!
Here are some highlights of this browser from the official Bromite website:
- The main goal is to provide a no-clutter browsing experience without privacy-invasive features and with the addition of a fast ad-blocking engine.
- Minimal UI changes are applied to help curbing the idea of “browser as an advertisement platform”.
- All patches are published under GNU/GPL v3 to enable other open source projects’ usage.
- Bromite is only available for Android Lollipop (v5.0, API level 21) and above.
Another cool feature I like with Bromite is that you can use custom ad block filters — learn more here. Bromite is under active development and remains a great browser for Android users.
https://www.bromite.org/
10. Pale Moon
Pale Moon is another open-source fork of Firefox, which aims for efficiency and customization. In testing out Pale Moon, it does offer different customization options, as well as support for older Firefox add-ons and its own lineup of add-ons. The design feels a bit dated, but it’s also not overly-cluttered and is lightweight and fast. Even more importantly, this secure browser is still being updated
Pale Moon is currently available on Windows and Linux, with other operating systems in development. Unlike other Firefox forks, Pale Moon runs on its own browser engine, Goanna, which is a fork of Gecko (used by Firefox). This is an older engine that was previously used by Firefox, but has long since been replaced. Many argue that this older codebase is a security vulnerability. And it’s also worth noting that the development team is very small compared to more popular browsers.
Pale Moon website >>
11. GNU IceCat
GNU IceCat is a fork of Firefox from the GNU free software project. IceCat is entirely “free software” as defined here and also includes various privacy add-ons and tweaks by default. Here are the privacy-protection features listed on the IceCat page:
- LibreJS
- HTTPS-Everywhere
- SpyBlock
- AboutIceCat
- Fingerprinting countermeasures
No updates – The big issue with GNU IceCat is that there do not appear to have been any updates since 2019. This can expose IceCat users to security vulnerabilities, which is why we are no longer recommending it.
GNU IceCat website >>
12. Iridium
Like Brave, Iridium is a secure browser that is based on Chromium and configured for more privacy by default. The following excerpt from Iridium’s website provides a good overview of this secure browser:
Iridium Browser is based on the Chromium code base. All modifications enhance the privacy of the user and make sure that the latest and best secure technologies are used. Automatic transmission of partial queries, keywords and metrics to central services is prevented and only occurs with the approval of the user. In addition, all our builds are reproducible and modifications are auditable, setting the project ahead of other secure browser providers.
Iridium is still being updated pretty frequently. However, it is not a widely-used browser, and there is no support for Android, iOS, or any other mobile devices.
Iridium browser website >>
Issues with other popular browsers
While some browsers claim to be secure against vulnerabilities, they might not be the best choice from a privacy perspective.
1. Google Chrome
Google Chrome is by far the most popular browser. Unfortunately, it’s a data collection tool as well and not a good choice for anyone looking for privacy.
You can safely assume that everything you do through Google Chrome is collected, saved to your data profile, and used for targeted advertising.
2. Microsoft Internet Explorer/Edge
Edge is a Microsoft product.
Just like with Windows, it’s a good idea to avoid Microsoft products, including the discontinued Internet Explorer and its replacement, called Edge. Both those browsers are closed-source, so there’s no telling what’s going on behind the scenes, and they’re also not the best for privacy reasons.
3. Opera browser
Opera started off as a decent browser, developed in Norway. However, in 2016 it was sold to a Chinese consortium for $600 million – and a lot has changed. The following information from Opera’s privacy policy explained how user data was collected and shared when you used Opera products. This was enough to turn us off to this browser:
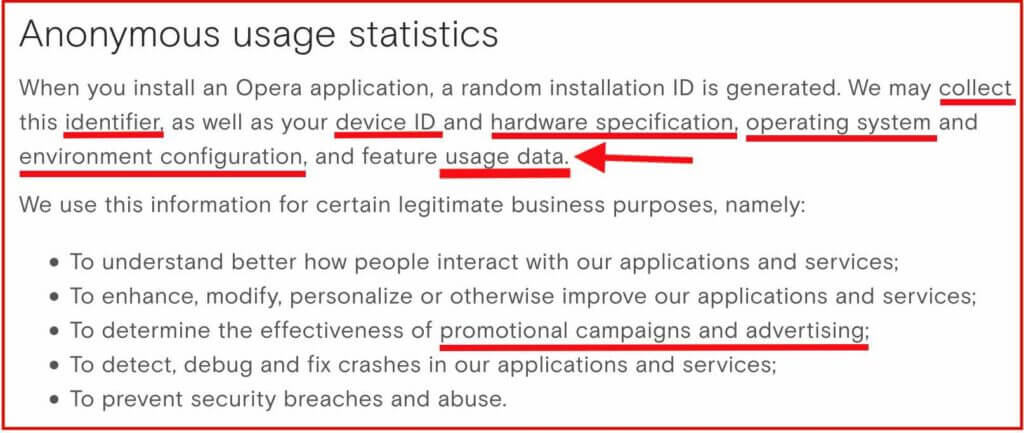
Opera also claims to offer a free VPN through the browser. However, as we covered in the Opera VPN review, it’s not really a VPN and does not offer full system-wide encryption. Additionally, your data is being collected when you use Opera browser and its “free VPN” feature.
4. Epic browser
Epic is a browser based on Chromium, created by “Hidden Reflex” which is based in India. Since 2014, Epic has been claiming they would open source the code, but it remains closed source today. What’s going on behind the scenes? How do they manage Chromium and remove invasive code? Who knows.
Just like with Opera VPN, Epic falsely claims to offer a “free VPN” through the browser, but this is not really true. The browser is merely routing traffic through a US proxy server. As we learned with Opera (and with many other “free proxy” services), proxies are often used for data collection (and they are often not secure). When reading the Epic privacy policy, we find that data from “video download and proxy services” is being collected.
One person who analyzed Epic found it to be connecting to Google on startup. This suggests that Epic is not, in fact, de-googled as it claims.
There are many better Chromium-based browsers to consider.
5. Safari browser
Safari is the default browser for macOS and iOS devices. Overall, Safari is not a horrible choice in terms of privacy and tracking protection – but it also cannot be recommended for a few reasons:
- Apple is a partner in the PRISM surveillance program
- Apple was caught “hoarding” Safari browsing history – even after it was deleted
- Apple was found to be collecting Safari history even when used in private mode
On a positive note, however, Apple does somewhat better with privacy than other large companies. The Safari browser blocks third-party cookies by default and also implements cross-site tracking protection.
6. Vivaldi browser
Vivaldi is a Chromium-based browser with source-code modifications that can be seen here. It is less popular than other browsers, with less active development than Firefox, for example.
Reading through their Privacy Policy, I did find some concerning information about data collection and the use of unique IDs:
When you install Vivaldi browser (“Vivaldi”), each installation profile is assigned a unique user ID that is stored on your computer. Vivaldi will send a message using HTTPS directly to our servers located in Iceland every 24 hours containing this ID, version, cpu architecture, screen resolution and time since last message. We anonymize the IP address of Vivaldi users by removing the last octet of the IP address from your Vivaldi client then we store the resolved approximate location after using a local geoip lookup. The purpose of this collection is to determine the total number of active users and their geographical distribution.
You can read more about Vivaldi here.
Secure and private browsers on mobile devices
Many of the recommended browsers above also offer versions for mobile users on iOS and Android.
With that being said, here are some good options for mobile users:
- Brave
- Bromite
- Firefox Focus
- DuckDuckGo
I also like using standard Firefox on mobile devices with customization and configurations for more privacy.
Browser privacy and compartmentalization
One problem that often comes with browser privacy and security is that people want to remain logged in to various accounts, while also browsing the web. But this is problematic. When you stay logged in to Gmail or Facebook, for example, their trackers can record your activity as you browse the web.
One potential solution to this problem is browser compartmentalization. This is when you use different web browsers for different online activities. For example:
- Browser #1 will only be used for accessing your online accounts that require a password. You can stay logged in with only this browser, and it won’t be used for general browsing.
- Browser #2 will only be used for web browsing, with various privacy configurations and no cookies or history being stored on the browser.
- Browser #3 could be completely locked down for maximum privacy and security.
You can also utilize different browsers, configured exactly the way you want, for various purposes, depending on your needs and threat model. The key is to keep the compartmentalization strict and not break the rules/uses for each browser.
Virtual machines – On the topic of compartmentalization, using virtual machines is also a good idea for both privacy and security. You can easily run Linux VMs through VirtualBox (FOSS) on your host computer.
Password managers – It should also be noted that storing your passwords in the browser may be risky depending on the browser you are using, especially since browsers may store passwords in cleartext. A better alternative would be to utilize a secure password manager. We have reviewed many popular options, including Bitwarden, Dashlane, LastPass, and more.
Browser add-ons for security and privacy
In addition to adjusting the settings within your browser, there are also a number of different add-ons or extensions you can install to improve your browser’s privacy and security.
Here are a few different options, but they may not all be supported by the browser you are using:
- uBlock Origin – This is one of the best browser-based ad blockers available that will also protect you against tracking.
- Cookie Autodelete – This will automatically delete cookies that are no longer needed from your browser.
- NoScript – NoScript allows you to customize exactly which scripts run on the websites you visit. Like uMatrix, this is for advanced users and requires lots of customization.
Warning: Be cautious about using third-party add-ons and browser extensions. There are many Chrome VPN extensions that are 100% free, but also very dangerous. Do your research first, since add-ons and extensions could function as spyware and data collection tools for third parties. This is especially true with free VPN services or browser proxy add-ons from questionable sources.
“Private” or “Incognito” browsing mode is NOT private (and why you need a VPN)
Many people falsely assume that using “private” or “incognito” mode in a browser actually provides some privacy. This is a false assumption.
Using “private” browsing mode only stops your browser from storing cookies, history, and passwords. But it doesn’t actually make you any more “private” to the outside world. Even when browsing in “private” or “incognito” mode, you are still exposed:
- Your internet provider can still see every site you visit. And note that internet providers are now forced to log web browsing activity of their customers and provide this data to authorities on request in many countries. In the United States, ISPs log everything and share the data with a huge network of third parties.
- Your real IP address and location remain exposed to all sites, ads, and trackers. This makes tracking and identification easy since your device has a unique IP address linked back to your identity through your internet service provider.
To easily solve these problems, we strongly recommend using a good VPN service. Using a VPN is simple. You just need to sign up for a VPN subscription, download the VPN app for your device, then connect to a VPN server and browse the web as normal. This offers many benefits:
- A VPN will securely encrypt your internet traffic, which prevents your ISP from seeing what you do online. (Your ISP will only see encrypted data, but not what you’re actually up to.)
- When you connect to a VPN server, the VPN server’s IP address and location will replace your real IP address and location. This allows you to appear to be anywhere in the world.
- A VPN will also allow you to access geo-restricted content, such as streaming Netflix with a VPN from anywhere in the world.
Below is a brief overview of our recommended VPNs. They have each come out on top in our testing for the respective VPN reviews.
- NordVPN: A fast, secure, audited VPN with advanced privacy features and a strict no-logs policy, based in Panama (with a 74% off coupon). See our NordVPN review here.
- Surfshark VPN: A no-logs VPN service with a large lineup of privacy and security features, based in The Netherlands. See the Surfshark VPN review.
- ExpressVPN – A fast, reliable, and secure VPN that also works well for streaming, but with above-average prices. See the ExpressVPN review for the pros and cons.
Short on money? There are also some good cheap VPNs that offer excellent features and performance, without breaking the bank. We also have detailed VPN comparisons. Our ExpressVPN vs NordVPN guide compares the top two providers.
Conclusion: Secure browsers and privacy in 2024
A well-configured secure browser is crucial for protecting your data if you want to browse the web with kind of privacy. But there are several good, secure browsers to choose from. So how do you do it?
Finding the best secure browser for you comes down to identifying the one that best fits your unique needs. Since this is a personal decision with subjective criteria, we can’t recommend a single option that is best for all use cases.
In truth, you need more than a secure browser that is configured to protect your privacy. To that browser you should add a quality VPN that will encrypt your traffic and hide your IP address.
You should also consider using a good ad blocker. Many ads include tracking code that companies can use to collect your browsing data and serve you targeted ads. If you aren’t blocking ads, your activities can be tracked by third-party advertising networks, which is not at all ideal.
Note: There are some VPNs that have built-in features to block ads and trackers. See our guide on VPN ad blocking for more info.
In terms of privacy, you may also want to protect yourself against browser or device fingerprinting and WebRTC browser leaks, which can expose your identity even when using a good VPN service.
This secure browser guide was last updated on May 15, 2024.

A short time ago, I bought a new Android phone and have recently tested Brave’s mobile browser on EFF’s Cover Your Tracks. The browser is ranking as having “partial protection” and while the site is not the final authority on how good a browser is, it is concerning since for many years it was rated by Cover Your tracks as having “strong protections” since I Brave mobile was the browser from the start I when I got my new phone.
Fortunately, CSagan5 has kept up on updates to Bromite recently. For those, like myself, that prefer using Chrome-based browsers for primary uses on Android, Bromite or even Vivaldi’s mobile browser might be decent alternatives to use until Brave’s bugs can be worked out. Firefox mobile is also a good choice as well.
Interestingly Vivaldi for android is still in chromium version 106, instead of latest 108. Being a small company is it struggling also ?
@shr No idea. I hope not. I like Vivaldi despite it not being one of my personal browsers of choice. It would be ashame if the effort flops.
I’ve been using Ghostery Dawn and am not that impressed with, it’s an OK browser at best. It will freeze up on certain webpages for no reason and is just a pain in the ass. I would like to give the LibreWolf browser a try and wondered if anyone has used it with the unofficial LibreWolf-WinUpdater, which automatically updates LibreWolf on Windows when its not running?
Has anyone had any issues with LibreWolf browser or the unofficial LibreWolf-WinUpdater? Thx
Go ahead as you planned. Everything is okay with LibreWolf and it’s updater.
@shr does LibreWolf update automatically or does it have to be done manually?
Updater add-on checks every time and notify if there is an update available. Then offer to download. By clicking the notification pop-up, you have to download the EXE file, then install.
ok.. what about fennec, mull, foss browser etc?
I read earlier, mull browser is librewolf for android. It is true? really best choice for android is brave?
You are right.
Mull is hardened out of the box FF fork for android, best for mobile.
Fennec also good but you have to configure it for privacy following Sven’s FF hardening guide in this website.
Both updates frequently.
FOSS browser is best among android web-view based browsers, but these categories have inherited privacy vulnerability.
Here are details – https://divestos.org/index.php?page=browsers
Brave is an all-rounder, but whitelists Amazon trackers now, as revealed when testing with NetGuard and TrackerControl app. Still, it’s better than other chromium based mobile browsers.
Bromite should be better option here, but nowadays updates late.
Mulch (from the dev of Mull)
AND
Kiwi browser (only mobile chromium based browser which support extensions) may interest you (GitHub versions only, playstore builds of Kiwi always behind).
Lastly, it’s very difficult to maintain privacy with mobile, whatever we do.
@Kayra150 I have used Fennec and Mull but not Foss. Either will do and I am sure Foss is a good browser too. My only hang-up with them is that, like LibreWolf, it is very likely they have been built and maintained by tech enthusiasts or developers with little support.
If you use any of these browsers, I suggest you keep this in mind and pay close attention to the volume of updates since lack of them can jeopardize your privacy and security. I would also regularly check the browsers against sites, like EFF’s Cover Your Tracks, to make sure the browser is still secure after updates too.
Until recently, the team behind Bromite slowed down on their browser’s updates and, according to my tests, even Brave is ranked as having “patrial protection” by Cover Your Tracks. I am more likely to use a browser backed by a major organization, like Mozilla or Brave Tech, since they have the money and people to quickly correct any problems that may arise.
Good luck!
@Mike
Here is the update history:
Firefox forks: http://divestos.org/misc/ffa-dates.txt
Chromium forks: http://divestos.org/misc/ch-dates.txt
Please don’t recommend the Cover Your Tracks: https://github.com/privacyguides/privacyguides.org/discussions/1797#discussioncomment-3721547
@voyager I used Cover Your Tracks as an example. I realize there are many other sites one can use to test a browser’s effectiveness. Thanks for the links, I have been looking for sites like them. Another good browser comparison site is:
https://privacytests.org
Hi RP Community,
I have come accross something that has quiet perplexed me.
This post is for people who like testing.
The senario is that this site bws.com. au was blocking me with “Error code 1020.” 1020 appears to be a Cloudflare specific error. With the Brave browser, I isolated this to actually be a NordVPN Threat Protection (TP) issue. Using the same browser, same IP address, in the same Brave tab; I tested TP ‘on’ and it produced the error; an I tested with TP ‘off’ by refreshing the page, and the page loaded as expected.
My custom Firefox browser produced the exactly same results.
Google Chrome browser produced the same results.
I tested with Brave for cookie related matters. I blocked all cookies and the page breaks – no error code. With FF this produced the same results. I didn’t test this with Chrome.
Interestingly, in the senario where with TP off, firstly successfully accessing the the home page, then secondly turning on TP and clearing all cookies, I was allowed be to navigate the website (which was not possible before.)
It looks like firewall rules to me.
My hypothisis was that Cloudflare was detecting Nord TP and actively bloking Nord TP customers;
And I raised a ticket with Nord yesterday.
(The Nord techs on chat will not confirm with me whether Nord has partnered with Cloudflare)
(The internet and NordVPN frontline techs viewed this as a TP white/black listing problem – which I suspect it isn’t)
Here is the twist!
I tested today with Librewolf (and retested basic tests on all other browsers – they are blocked with TP ‘on’.)
Librewolf loads the page with TP ‘on’ or ‘off’.
???
So for most cases, TP detection envolves Cloudflare and fits very tightly with the results;
…Then Librewolf produces an exception.
If you like testing, I would be interested to hear your results;
And if you are a wizz, please consider explaining.
Regards,
BoBeX
What about Avast or AVG Secure Browsers?
Being based on Chromium, are they more secure being feature specific or are they really Google Chrome clones that still transmit user data to Google?
Also Sven, what are your thoughts on SRWare Iron Browser?
@Marc
AVG is a subsidiary of Avast.
Avast and AVG collect and sell your browsing history: What you need to know…
https://www.tomsguide.com/news/avast-avg-data-collection
@Mike
“kinda sorta good news” just think hearing this at quitting time Thursaday before Friday’s payday. Trust must be earned to get the respect of loyalty. Once your cold you never get warm.
@BoBeX
Was a TYPO but I’ve seen it here couple of times and never was as an active clickable link. The B&A were large case as I recall. Isn’t our trouble maintaining the degree of privacy everyone seeks after the browser and by the way the server networks that are tainted and poisoned by big tech and ad networks, CDN’s pi_sing in the water before we get a drink?
@topcat, with politeness, I was referring to the ‘ ‘ (space keypress) between the ‘.’ and ‘com’.
Some kinda sorta good news about DuckDuckGo’s privacy browser.
https://www.bleepingcomputer.com/news/security/duckduckgo-browser-now-blocks-all-microsoft-trackers-most-of-the-time/
Contrary to my previous opinion, I think Brave browser has made a great leap in terms of quality recently! Currently, their browser is probably the best option for Android users. Bromite used to be my Android pick, but it seems they don’t update their Chromium engine in time anymore. If you test Brave against fingerprints, nothing beats that browser in Android ecosystem. It is also very solid for Windows.
Of course, for iOS users of privacy browsers, there is almost nothing that is better than Safari. Personally, I like SnowHaze. It is probably the only browser in iOS that offers some alternative to customized Safari. Also, Onion browser is a good option for private searching (with VPN on). Everything else, like Brave or Firefox, is more or less just a version of Safari, due to the same engine…
Hey Bronco, I was so excited to hear brave was available on Android. As a preference, I prefer FF forks, but this preference is not for technical reason but for market place diversity. I am very keen to be testing LibreWolf. I will post results under the ‘Browser Fingerprinting’ guide.
These are the testing tools I will be using:
ipleak.net
amiunique.org
https://nothingprivate.ml
https://fingerprintjs.com
https://noscriptfingerprint.com
https://abrahamjuliot.github.io/creepjs/
If anyone has other good testing tools please add.
https://www.deviceinfo.me/
browseraudit. com
@rhs @topcat, Great links guys I will add your suggestions to a list I will post on the fingerprinting page. (I think persons interested in them in future are more likely to look there for testing tools and given the popularity of posting to this page will quickly get buried and not found.)
In summary in my tests with browseraudit. com, for my browsers, only Librewolf on PC and Firefox Focus on Android passed without a ‘critical alert.’ The info generated by “browseraudit. com” is very detailed and complex and will take me some time to sythasise and understand.
Question to @topcat is the space in the link you provided a typo or intended to avoid scraping tools? Just courious.
Hi RP Community,
A great article hitting all the key points.
(The discussion in the comments can go above my head but I would refer this article’s advise to family and friends.)
I am pleased LibreWolf pass the RP recommendation test. I have been waiting for this go or no-go call.
Is LibreWolf private out-of-the-box or does it require modifications like FF?
(I assume it is out-of-the-box)
I was soundly pleased to hear the Brave browser is now available for mobile.
I prefer FF mods for market diversity over Chromium though I have no reason to question Brave.
I use Google Chrome for my personal business.
(Please don’t hate on me)
My bank, Visa and MC already have my data, and sell it.
I use Chrome ad Gmail for these interactions;
I want them to finger print me so no-one else can get in (to my accounts), for security.
Though I don’t like that they share / sell my data, I just haven’t found a solution for this…
A sensible answer will not just included hating on Google.
(I also have one browser set solely for Google queries.)
I welcome advise and correction from the community.
Regards,
BoBeX
You are right, LibreWolf hardened out of the box. To keep it updated, install the LibreWolf updater add-on available.
And if you feel comfortable, you can replace your business to Brave from Chrome. That will be better.
Use safe search engine like https://searx.namejeff.xyz/ (jurisdiction Switzerland and good privacy policy) to get same result as Google search.
Try to follow Browser compartmentalization technique.
Nothing to hate, according to different needs we have to compromise in some area. There is no absolute rules or solution to fit for everyone’s necessity. 🙂
Hi shr, thank you for you kind words and good advise.
I am thinking of setting up a four * browser set up: Brave for my personal accounts, Ungoogled Chromium for the use of YouTube and Google search, modified FF for general browsing and LibreWolf for other. I also use virtualisation which I think I will setup with customised FF and LibreWolf.
This looks a good setup for me.
Any polite advise will be welcomed.
“I want them to finger print me so no-one else can get in (to my accounts), for security.
Though I don’t like that they share / sell my data, I just haven’t found a solution for this…”
Could you elaborate some? Because being unknown or unacknowledged is weak privacy when either your IP, device, OS/model/log-on profiles and advertising ID’s defeates your own internet anonymity. The lack of users privacy is indeed a lack of persistent personal web security, mind you the public records open trails once your ID is known.
Security fails users when the obscurity to their own web searches makes them eminent over all other searches. Look at human life and nature that exploits, victimizes, or preys on others from the predators element where we gather or frenquent.
Googles predacious leads makes us directly or indirectly the balls in it’s court to the rules and laws it demands. See the internet if you would being developed as early trade to the water sources on the glode, trade followed those waterways. Is this not Googles plan to toll us for passage in internet trade? Directly or indirectly as the foundation of the internet G has become?
Unfortunately, it is true in all way.
so true seeing it like this.
Hi Kathy, let me be clear I was not offering advise, I was outlining my current setup and requesting advise. You requested elaboration…
My experience is that Credit Card company’s and financial institutions sell customer data, and some are more aggressive than others. In Australia it is usual that Visa and MC take 3% of of the merchant sale. A couple of years ago I opened account with a new financial institution who’s terms were to return 2% of this back to the customer. I noticed immediately that with spending on this new card my Google (specifically, Youtube) advertising content became very targeted – and the turn around from my card spending to the advertising sent to me was so fast – daily. This is why I don’t seek to obscure my financial spending from Google – it is because I believe they obtain it anyway.
This is an experience / opinion.
The reason I want to be fingerprinted (in these instances) is two fold. One, anything that I do financial is already shared and not private (perceived); And two, for security, given they already know exactly who I am, they can identify fraudulent / suspicious activity on my accounts.
So given there is zero privacy (perceived)- I will take the best security option.
I agree that the web is not free (freedom), I agree that corps are monetising the web.
I invite polite feedback from anyone in the RP community
If my post was not polite I’m sorry you interpreted it this way.
Ad blockers work wonders for what you say has happened with personal ad targeting. I suggest ad guard if nothing else but trying it out. Credit cards are a racket just like the webs ad networks. They work from all sides for personal profits often changing all for having a foot in your door.
Something like 20+ years and counting nothing has been done to eliminate our threats to the dangers these and many more have for us in our life’s. I only stated what many overlooked before now. Fingerprinting is not an acceptable means to be recognized by institutions that deal in our good. 2fa or similar is much better, something you know with something you own as guaranteed access that’s it’s you.
It’s definitely a mess up web today and no good reasons but greedy profits sought.
…Hi Kathy, There reply button was broken to I couldn’t post directly to your most recent comment. I have no reason to suggest you were impolite, maybe I was prepared to be defensive.
I use Ublock Origin and am very happy with it, I have never used AdGuard though I hear it is good. The experience I referenced was from a time about two and a half years ago. I never see ads, I never get one unless they are built in. But this now makes the data sharing invisible to me.
I looked into options e.g. privacy.com for more private financial transaction solutions and it was unavailable in my jurisdiction (though I haven’t checked that recently). If it was available in my jurisdiction I would be here asking for comments, maybe requesting a review from RP.
My view is that financial transaction data privacy is very important and on importance stands along side what RP discusses here on RP, which I would describe as focused on ‘online privacy.’
My view (and it is a view) is that technologies can be used for good or bad. This includes fingerprinting.
Have a lovely day
I say it’s the whole DNA that big tech has infused into the web that bottle-necks our search results and steals our privacy by big tech as it is their tool of control over it and us.
Sven tries to relate generally to Privacy as a threat subject regarding the usage of apps, programs and services on the Internet. Within the broad swipe are details and time-limited involved proofs, and itself is a very difficult subject to deal with totally in every aspect giving specifics on everything available. Not only can it be frustratingly difficult to actually define privacy. But it also requires the level balance between freedom of choice by the users, security and usability. Naturally you need to be able to use the browser(s) on the Internet and as such you will always leave some kind of trail(s) behind.
The analog systems of the past are welcome privacy that was forfeited to the push button digital world about us now – shame too! Thanks BoBeX we share the vision differently is all. ; )
A cool, new feature that has been added to Brave is a built-in interpretation feature for its mobile and desktop browsers. Vivaldi was the first browser to have this and now Brave followed suit. Firefox also has a non-Google interpretation extension you can install through their add-on repository.
I like to read foreign news from time to time so these features come in handy.
Hi guys,
any opinion onFloorp browser?
Hey Elemir, I like Floorp. No idea how to pronounce the name, but it looks and feels solid. Some interesting features. Worth giving it a go. (Tested on a 2013 MacBook Pro running Catalina.) Cheers!
Opera has bought back its shares from 360:
https://investor.opera.com/news-releases/news-release-details/opera-completes-repurchase-shares-360
Good news, but according to the provided link’s information in detail, Chinese connection still present. Isn’t it ?
Opera was good with Presto Engine after that is the same as the other browsers.
And BTW what is the different between Chinese connection or some others??
rhs = User profiles for 1, as do you want (that mining you have no control over) in user data farmed from either US or EU interests or those of Asia and Russia competing with the others? All have good people but global competition of free societies prosper their people fuller instead of the dominance of it’s government over it’s people for a the 2nd.
Sven, what about Seamonkey, a very old fork of Firefox? https://www.seamonkey-project.org/
(I.e. can you review it here)
Hi, I have monthly data on hosts doing a virtual gang stalking and it is most using my browser. I am not technical but I can see this with a sharkwire type program. So since I found this article via this same browser can I trust? At any rate is this browser you speak of one that is readily available on any computer? Everything I have including my email is unsafe due to the privacy breaches that now chrome is greatly helping with.
Gee do you use the page scroll function? If so you might of been answered before posting this.
“Users in the SeaMonkey community share ideas and code for features they want to add, and you can join the discussion, even if you don’t write code. There isn’t a central management team that oversees these add-ons or version updates, so you have to be vigilant about exactly what’s being added. It is possible that a version release will be buggy, include tools that you don’t want, or be insecure. In these cases the SeaMonkey community works together to provide patches or new versions to fix these issues.
The current version of SeaMonkey includes a password manager, customizable tools and session restore. It isn’t compatible with smartphones or tablets, and it feels clunky and outdated. Plus, it is much slower than other web browsers being tested. It also does a poor job of identifying phishing schemes and other harmful websites, and it doesn’t stop malware from being downloaded to your computer. You can like the open source community of SeaMonkey, but it’s not a browser people recommend you use.
I asked for the same thing two weeks ago. I too think that SeaMonkey should be reviewed. It’s a solid browser with a focus on privacy. It’s certainly better than current FireFox, that’s for sure
So noted JS and it defeats itself as I had noted. As it has (I see) more cons than pros going for it. Especially being on the web scene for so long and having a community behind it. To each’s own that’s for sure, but I couldn’t see Sven giving the time to it for review and then keep it in an update schedule that Sven gives to maintaining the site reviews and articles.
jross – DuckDuckGo has never been a browser to my knowledge – DuckDuckGo (DDG) is an internet search engine that emphasizes protecting searchers’ privacy and avoiding the filter bubble of personalized search results. https://en.wikipedia.org/wiki/DuckDuckGo
Either an all-in-one privacy app for mobile or desktop browser extension – browser itself no.
I found an old resource where Vivisimo was listed and each & every link it was mentioned at had opened the DuckDuckGo search page. Then Vivisimo was a privately held technology company in Pittsburgh, Pennsylvania, specializing in the development of computer search engines. The company was acquired by IBM in May 2012 and is now branded as IBM Watson Explorer, a product of the IBM Watson Group. Vivisimo’s public web search engine Clusty was a metasearch engine with document clustering; it was sold to Yippy, Inc. in 2010. Vivisimo specialized in federated search and document clustering. Clustering divides the results of a search for “cell” into groups including “biology”, “battery”, and “prison”.
https://en.wikipedia.org/wiki/Vivisimo
It is a coincidence that DDG and Vivisimo both are based in Pennsylvania? Both DDG family ???
Others may have more of a dilemma and ponder on things like: is DuckDuckGo a browser or a search engine? We’re hoping that our explanations below will help to answer all of these questions. https://windowsreport.com/browser-duckduckgo-search-engine/
UpDate: In April 2022, DuckDuckGo released DuckDuckGo for Mac to beta, a privacy-oriented desktop browser which automatically blocks both web trackers and cookie consent pop-ups. DuckDuckGo chose to use the WebKit rendering engine that underpins Apple’s Safari browser rather than the fork of it called Blink used by Chromium, Opera and Brave.
Vivisimo software supported both structured and unstructured information
A few clarifications that I think you should make:
What browser engine does DDG browser have?
Vivaldi makes a big deal about their lack of data collection. Although you are right that they collect one significant data point, which cannot be disabled, you don’t give them any credit for what they do right in the privacy department. By contrast, your second most recommended browser, Firefox, collects more data than that by default, and even Brave, your #1, supposedly phones home ( https://avoidthehack.com/review-brave-browser#thebad )
…So don’t you think Vivaldi should be in the middle tier?
Brave: To clarify: Yes, many people disagree with their funding model based on showing the user ads. However, the browser does not send your data to either the advertisers or Brave and the ads are optional.
First you say you dont recommend Bromite or DDG browsers, then in your “mobile browsers” section they are “good options”? What?? Also what do you think about Mull, IceRaven, Privacy Browser, and ORFOX (TOR on Android)?
jross & Great man,
jross regarding jumping around wanting everything answered-(ranting)-well good luck with that approach. Maybe I can answer you and Great man some as I really want to help you focus on the bigger picture.
BrowserAudit.com – run it and know what is what in your setup.
The modern web relies on lots of security standards and features to keep you and your data safe as you surf the web. How effective they are at protecting you depends on how well your web browser implements them. If the browser behind your search engine choice contains bugs, it might not be doing everything it can to keep you safe.
Mobile authentication is different from the traditional API authentication in the first place!
The most basic form of API authentication is traditionally known as HTTP Basic Authentication, which is great because it’s simple. A developer can request an API key and easily authenticate to the API service using this key.
What makes HTTP Basic Authentication a bad option for mobile apps is that you need to actually store the API key securely in order for things to work. In addition to this, HTTP Basic Authentication requires that your raw API keys be sent over the wire for every request, thereby increasing the chance of exploitation in the long run (the less you use your credentials, the better).
In most cases, this is impractical as there’s no way to safely embed your API keys into a mobile app that is distributed to many users. For instance, if you build a mobile app with your API keys embedded inside of it, a savvy user could reverse engineer your app, exposing this API key, and abusing your service. So this is why HTTP Basic Authentication is not optimal in untrusted environments, like mobile web browsers and mobile applications.
NOTE: Like all authentication protocols, HTTP Basic Authentication must be used over SSL at all times.
Sven tries to relate generally to Privacy as a subject regarding the usage of apps, programs and services on the Internet. Within a broad swipe and it is a very difficult subject to deal with totally in every aspect giving specifics on everything available. Not only can it be difficult to actually define privacy, but it also requires a balance between freedom of choice by the users, security and usability. Naturally you need to be able to use the browser on the Internet and as such you will always leave some kind of trail behind, and this article is not about how you can hide your tracks. What Sven is addressing in this article are browsers that are either promoted as “privacy-respecting” by the developers, or in general are considered to be so (mostly due to misunderstanding or misinformation), while it is very clear that some browsers offered are not.
Some browsers either directly violate users by collecting telemetric data without consent, or you have to opt-out rather than opt-in, or they bounce around the Internet visiting places in the background without you knowing (using dns-prefetch or automatic updates etc.), using third party services that operates with a privacy policy you either cannot trust, or that are directly violating your privacy, or they have integrated third party software that do some-if-not all of these things.
Sven can’t give people a, “One Answer Fits All,” type of review/answer. If it was so, “there would have been no point in spilling so many words on the screen. The right answer depends on your type of device, your operating system, your user case specifics, and possibly your budget – to move away from the free offerings.” Then within your ability to research and understand on your own to find those answers you sought out.
Hi Sven
I know you don’t like Android because of privacy leakages.
That’s true.
But as you tried to help mobile users suggesting some privacy respecting browsers in the article, I’m asking your wise opinion about security level of FF and it’s forks in android.
From the link https://grapheneos.org/usage#web-browsing
and https://divestos.org/index.php?page=browsers
I’ve come to know that in android, FF don’t implement full security feature like ‘per-site processes isolation’ still now, but privacy feature like ‘pre-site data isolation’ is same as their windows version.
Whereas Chromium based browsers have both in there android version same to windows version.
Now, how serious lack of this feature in FF ?
Hardening as per your guide can cover the lack of ‘per-site processes isolation’ of FF ?
Or for android we should use only Chromium based browsers from your recommendations.
What do you think
Good points and a big reason to use your smart phone only as a dumb phone for calls and texts…as the world grows more data-hungry, people are storing more and more sensitive information on their mobile devices; security is more important than ever. If I were Sven I’d avoid the subject too, especially with having to grant so many permissions for android to work which is a no privacy environment.
Applications extend the functionality of a device by providing a useful service or tool. For the Android platform, applications are developed in Java using the Android SDK. The SDK provides API libraries and tools that are required to build, test, and debug Android applications [Android SDK]. The majority of security concerns are related to applications since they need access to users’ personal information and other permissions on the device.
There are two sources for applications on any Android device. There are pre-installed applications such as phone, email, calendar, web browser, and contacts. The other would be user-installed applications that can be downloaded from any third party vendor or distributor. Most security risks associated with applications will come from user-installed applications that are actually malware masquerading as an innocent program.
Every application is given its own unique UID when it is installed, and when the application is run it will always use the same UID. This UID is to protect the application’s data from other applications and it forces developers to be explicit about sharing data between applications. This effectively sandboxes the applications from one another and keeps malicious applications from infecting other programs on a device. There are protected APIs in place that that provide applications access to user data. In general, Android devices will store user data over time within the applications that are downloaded on them. Certain applications can choose to share this data, and can use the Android OS permission checks to protect it from other parties.
It should be very clear to users what sort of data an application is trying to access on a device. Always check to make sure that you are only granting an application the appropriate permissions that you want to, because once you grant permission the application can have access to the data at any time. Applications can share data through permissions applied to the secure IPC mechanisms used by the OS [SecurityOverview].
Android users have to be careful when installing new applications, as there are malicious applications that pretend to be useful or try to trick people into downloading them. By tricking users into granting them permissions, they can do harmful things like steal user information, destroy personal data, and even make calls. This is why it is very important to look over the permissions of a specific application and checking that the developer is a trusted source before downloading it. These malicious applications are typically discovered and removed by Google when they are found but they are still a real threat to the uninformed user.
https://www.cse.wustl.edu/~jain/cse571-14/ftp/android_security/index.html
3. Real-world Attacks
3.1 Fake ID
3.2 SOP Vulnerability
3.3 GinMaster
3.4 Master Key
Mobile authentication is different from the traditional API authentication in the first place!
The most basic form of API authentication is traditionally known as HTTP Basic Authentication. HTTP Basic Authentication is great because it’s simple. A developer can request an API key and easily authenticate to the API service using this key.
What makes HTTP Basic Authentication a bad option for mobile apps is that you need to actually store the API key securely in order for things to work. In addition to this, HTTP Basic Authentication requires that your raw API keys be sent over the wire for every request, thereby increasing the chance of exploitation in the long run (the less you use your credentials, the better).
In most cases, this is impractical as there’s no way to safely embed your API keys into a mobile app that is distributed to many users. For instance, if you build a mobile app with your API keys embedded inside of it, a savvy user could reverse engineer your app, exposing this API key, and abusing your service.
This is why HTTP Basic Authentication is not optimal in untrusted environments, like web browsers and mobile applications.
NOTE: Like all authentication protocols, HTTP Basic Authentication must be used over SSL at all times.
When is comes to security now, Android is more secured than iphone..
Have u compare Samsung Knox security to that of iphone security…
The only way they thought iphone are apple devices are secured is because they don’t side load app…
I can’t help but feel it’s not just the images on the browser canvas changing, but the canvas of the old browser has been forgetting as web standards changed especially with the stage things are at today with the 3 popular blinks, gecko, WebKit, browser core’s engines being offered.
If your making a point about the web’s history as changing — yes you can learn a lot from it’s time-line just by looking at the browsers it has generated through the webs life time. There is nothing mythical about it.
Here here I couldn’t agree more!
https://unixsheikh.com/articles/choose-your-browser-carefully.html
It is absolutely mind-boggling how poor the current state of the Internet has got regarding our privacy issues. Almost no matter what website you visit you cannot avoid getting a microscope shoved up your butt (yes, I said it!) by some web developer who insists on running Google Analytics on the website. Even, (some even though they are not even running any Google Ads). Instead of using the simple build-in web server statistics, or at least one of the better Open Source and privacy-respecting alternatives.
A fact that ad revenues drive a huge part of the economics behind the Internet and many websites and YouTube content creators depend upon the income of ads.
However, it is the way that today’s ad network business is conducted that is very in your face privacy problematic – in some cases even borderline immoral and highly controversial. The companies behind the ad networking businesses need to understand that many users would actually allow ads, but what majority of web users will not allow is to be spied upon and tracked across the internet without their personal consent.
No matter what browser you use, you need to keep a very close eye on exploitable bugs and other security issues and it is important to subscribe to mailing lists, news letters, etc., which provide browser related security information in a timely manner. Even though a security bug might be exploitable it doesn’t necessarily mean that it specifically affects your usage of the browser, it all depends on the circumstance and your usage. Every persons millage varies and if you only need to read the news you can decrease the thread level substantially just by disabling that sites support for JavaScript on your device or use a simple console based browser.
Falkon has been in development since 2010 and it is using the Qt WebEngine rendering engine, which is a wrapper for the Chromium browser core. The Qt WebEngine is based upon a stable version of the Chromium core with addition security fixes backported from newer versions. Falkon aims to be a lightweight web browser available through all major platforms and has become the default browser in OpenMandrive instead of Firefox. Falkon gives the same web standard compliance as Chromium and about the same performance, but it is more lightweight and generally starts up very fast and requires less resources. Falkon comes with a bunch of very useful build-in extensions, such as a custom ad blocker and Greasemonkey. Starting from Falkon 3.1, Falkon has gained support for custom extensions written in Python or QML which can be downloaded from the Falkon Store. As always you must be very careful with third party extensions and it is a good idea to read about the source before you run any untrusted third party code in your browser or elsewhere. Falkon has a nice set of features to secure privacy, but it must be noted that not all of these features are enabled by default. It is also a very good idea to run any browser in some form of virtualized jail or sandbox, but Chromium’s process isolation and sandboxing features are also enabled as a second line of defense in Falkon to double-down.
With all things said it is important to understand that the real problem lies with us – as the Internet users. We seriously need to stop using the bad, harmful to our privacy browsers and we need to either stop visiting all the bad websites or at least disable JavaScript on these websites! We need to educate ourselves and each other better to all minds understanding generally in the technology we’re using. This is much easier said than done, because website developers have gone crazy, but once you eliminate JavaScript from running in the browser you no longer need a complex browser like Firefox or Chromium. Then once you don’t need a complex browser you no longer have to worry as much about your privacy issues – at least not from the browser point of view. *Thanks to BSD_user for the link and Sven for a free site!
Falkon scored 3/72 https://www.virustotal.com/gui/file/cafe4dd6602f13c818458b236a650e60db273348810dc8e48f685220abc228dd?nocache=1
My installed Emsisoft A/V said No Suspicious files were found, and the3 who alerts and not of old time tested and trusted A/V vendors band.
https://www.techradar.com/news/google-defends-divisive-attempts-to-replace-tracking-cookies
That stinks man, as the average web user doesn’t want to experience any advertising – period. Googles claim of building a web that works for everyone is just as close as you can get. To the old way of over the air TV advertising. You limited propels choices and charge tremendous fees in any medium to be on the air. That world of online streaming services shows that people will pay to do without advertising, as its a plague on humanity. Noteworthy products and services will sell themselves as social word and reviews travels around and with the webs reach beings it’s fast enough of spread. Just nobody gets compensated as if it were me I seek out the home website and buy from it. Not from 6 hops in different site reading reviews, comparisons, and cut-rate deal sites.
It’s the comms % of revenue that is missed by the streaming services and the web in general are struggle in tagging (inter-circle agents) track-backs inotherwords COOKIES to who should be a recipient in the tangled up monopoly of ad networks.
Web Users (joes & janes) need educating themselves in recognition of the fact that the system underpinning its lucrative advertising business (powered by third-party cookies that track people across the web) creates opportunities for invasions of privacy. Heck YES IT DOES, fingerprinting is one up on any e-tags or ever-cookies profiling measures, but it must not work as good as the tracking cookie does for advertising track-backs.
Much to be desire as a failure wanted, is to hear, those to develop a collection of new systems and technologies that fulfil the same role as cookies, allowing advertisers to target netizens most likely to engage with their products, but without compromising user privacy to the same degree.
Dont TRACK – Dont PROFILE – Dont use the web to ADVERTISE – PERIOD
The web as a utility as like of the hometown library is a resource that nobody advertises from…
DREAM ON!
“If you want a web that’s affordable, advertisers need to reach users. If you want no advertising, that’s the world of ad blockers and companies that develop technologies that allow people to block everything, but that’s a sledgehammer that destroys the funding model of original content,”
That’s total BS as advertisers add nothing to anything new being original content on the web. Advertisers only role is a parasite suck to both sides of the internet coin and being the real sled hammer on personal freedom, security and privacy from the web. As now afforded to the end user – advertisers as being in control of the original webs content do charge us by one way or another in wealthy profits gains that any original web content creators get cheated of.
Categorize the web into different zones and strip out all the networks advertising from any learning type of knowledge venues. Make a dues by use fee system for entertainment and shopping venues. Till we get all of advertising stripped out and off the web and internet, as treating this medium as an important utility for modern life and then resource to personal knowledge in the betterment of society and humankind.
Hi, JMO
“You limited propels choices and charge tremendous fees in any medium to be on the air.”
That’s the whole point. The price for /nevertheless limited / online privacy will only rise in the near future…
Yep and some of the web audience was hip to that web users privacy invasion fact in 2010 and voiced their concerns on the same internet. Still the webs infringement of users privacy articles were strong at sounding those same alarms in 2015 about the same old web user privacy issues & with new user privacy concerns to immerging tech advancements in the web’s frontier. Almost twenty-three years later in all, and nothing for users privacy has been done, and besides the original web search and software titans came an avalanche of data brokers because of the lack in security for users privacy.
Web and Internet’s definition of Privacy is Profits as a users definition is the need to know. Faceless and nameless is not a real definition of privacy, if only comparing the web and roadway system in the USA. The web you have an IP address and the roadways you have a license tag. Your not surveilled from point A to point B on the roadways but there are cameras and could be. Unlike the web where your under surveillance from point A to point B and targeted with ads the whole way. I guess the roadways could be the same someday. When car chips start broadcasting through electric billboards personal ads on a long auto trip.
Both words start with a P and are at odds against the other Privacy ~ Profit when you add the human element…
Note: propels choices is something outside of the box in wanted change or it could of been ‘peoples choices’ misspell. Whatever hits 1st base in readers here.
@JMO
It’s also about the internet infrastructure in the first place, the way it’s built – you can’t do much for user’s privacy. And power states and their agencies are grateful for that, of course.
Bronco you’ve hit the nail on it’s head. “internet infrastructure in the first place, the way it’s built – you can’t do much for user’s privacy.”
Let’s see, Web01 was before the monopoly (mostly a static internet of texts only) web server networks, Web02 was the era of the tech monopoly gaining their control (free everything and eye/candy that users traded their data for). A replaced server network as their technology advanced in allowing them to follow users everywhere in the webs sphere.
Still living today in Web02 era but in an extreme advanced state of users privacy suppression by the tech titan’s and the fan club of “power states and their agencies” because for them to be fair and level the field to users privacy being 60% respected would hit their bottom lines. Profits so huge that loosing a few commas and a bunch of zeros could stand reduced regarding users privacy – as a need to know basic right by law. That’s why todays “internet infrastructure” needs tamed in a way as the old west had been. Stamp the “internet infrastructure” as a utility and change the foundation going forth as the worlds view of the Web/Internet servers network as needed for modern life as the health, food, fuel and banking inter-structures are seen and controlled for the populations good and as the business transaction worlds move there.
Maybe the sun will shine Bronco?
In December 2021, the FTC released “The Final Rule,” an amendment to the Safeguards Rule (2003) that encompasses a variety of changes, including an expansion of the FTC’s jurisdiction and specific requirements for businesses in executing an information security program.
This Final Rule (2021) also lists out reasonable steps that a financial institution’s information security program can take to build out digital and physical safeguards for data. So the December 2021 amendment to the GBLA Safeguards Rule has prompted organizations to take a range of actions, from simply making small tweaks to their infosec programs, and for some to frantically building one from scratch.
This mostly deals with everything in the Finance business area now. As of the latest 2021 amendment, where FTC changed the definition of “financial institution” to include a host of new businesses. To which any other business that significantly participates in financial activities, or affects people’s ability to access financial products or financial services.
There’s not too broad of a jump is there for the FTC of reigning in the businesses in the online advertising & selling industry, specifically to the prices people see online. FTC as aliening those industries being uniformed to act regardless of a persons device used or their income/FICO score. That’s definitely having been affected of the past as big data was being ground through the ad networks dynasty. Where the FTC will sanction that Ad Network Dynast without ambiguity for the US consumers. Possibly a provision of laws enacting penalties for their disobedience. Stopping the mining of big data for profit means and more of an inline purpose for National Defense.
Now I know that just about everyone on the internet forgot they exist BUT…….what about Sea Monkey? Given their history, I would assume that they would at least be as secure as Firefox. Furthermore, they seem to update on a regular basis despite being relatively forgotten in the minds of internet users. At the very least, I think they deserve on honorable mention. But enough of what I think (and to be quite honest, I don’t even care about what I think). I want to know what YOU think. What do you think about Sea Monkey? And are they good enough to make “the list”? At least an honorable mention?
SeaMonkey’s open-source code gives you a lot of control over the brower’s tools and functions. However, it’s best suited to users who are a bit tech savvy and understand source code. Compatibility: Windows, macOS, Android, iOS
However, SeaMonkey has several drawbacks. First, it looks very dated. Also, some basic actions, such as opening a second browser tab, take several steps – and that’s after you find find where the function is hidden in the tool. SeaMonkey also takes significantly longer to navigate between pages, almost twice as long as other browsers.
[https://www.toptenreviews.com/internet-browser-software-seamonkey-review]
Users in the SeaMonkey community share ideas and code for features they want to add, and you can join the discussion, even if you don’t write code. There isn’t a central management team that oversees these add-ons or version updates, so you have to be vigilant about exactly what’s being added. It is possible that a version release will be buggy, include tools that you don’t want, or be insecure. In these cases the SeaMonkey community works together to provide patches or new versions to fix these issues. The current version of SeaMonkey includes a password manager, customizable tools and session restore. It isn’t compatible with smartphones or tablets, and it feels clunky and outdated. Plus, it is much slower than other web browsers we tested. It also does a poor job of identifying phishing schemes and other harmful websites, and it doesn’t stop malware from being downloaded to your computer. We like the open source community of SeaMonkey, but it’s not a browser we recommend you use. [https://www.toptenreviews.com/best-web-browsers]
SeaMonkey has several drawbacks. First, it looks very dated. Also, some basic actions, such as opening a second browser tab, take several steps – and that’s after you find find where the function is hidden in the tool. SeaMonkey also takes significantly longer to navigate between pages, almost twice as long as other browsers. Since this browser doesn’t automatically update itself, you must download new security updates directly from the SeaMonkey website. And while it does a good job of protecting against some malware, threats may still slip through, especially since so many programmers contribute to the browser. During our in-house security tests, SeaMonkey blocked a couple of phishing schemes, one of the most common internet threats, but it didn’t recognize some dangerous webpages or stop threats, including ransomware, from downloading. [https://www.toptenreviews.com/internet-browser-software-seamonkey-review]
You know, I was hoping for a reply that wasn’t a copy and paste of TopTenReviews of all things; but I guess that’s what I get for having high expectations on the internet.
Insterms of privacy, which is safer, instagram or facebook. I kkow both owned by zuck. But between the two.
You mean which affords you the what privacy? – saying company offered defaults or user set privacy within your account there? I would expect very little privacy from these social platforms as that’s not how they’re setup to make money off of you. Meaning the more you give of your info there the bigger dollar target you become. I don’t find these sites necessary at all being old school! I’d even go as far to say most people using them weekly can’t count change back from a hundred dollar bill on a $17.38 purchase. They can’t and place the whole sum in your hand. 1st if they counted the change back to themselves and then to the customer that is twice it was checked for correct amount of change given out.
Well, i know all the facebook analytics and all, but what if insta, as bad as both are for privacy, which among the two is a little bit better, thats all i asked.
In my reply you were to see money as your privacy and relate to what you had asked. You need to realize you have control of, until you don’t of your privacy. You can’t go into the fire and not get burnt, even a little. Just having an account as such is like being in an living events billboard, phone book, journal, and the time-line to data about yourself. Your exposed to all the evils against personal privacy mount in one sphere. A dead-end!!!
In my opinion, neither is safe.
None. Avoid Meta services completely. And Google too, whenever you can.
Honestly, I’m not sure your question makes any sense. You’re comparing apples and oranges. They’re 2 different types of applications; one is not a substitute for the other. They can both be bad, good, or a mix. It’s not like you can drop one because it’s unsafe and go to the other because it is safe. They serve different functions and purposes.
Let me rearrange Will Wheaton’s initial questions maybe it will be sensible then as I had related.
“I know both owned by zuck. But between the two.”
(A man owns two social networking services – apples & oranges compared). They relate in manner as one a media and second in photo and video sharing on their social networking platforms. A hub then, where with an account you make hasten your demise to personal privacy as your sovereignty in an autonomous state anywhere else on the internet. Security and privacy are inseparable in todays dealing with the internet. As core trunk your limbs and roots are a network to all others within your other networks.
“In terms of privacy, which is safer, Instagram or Facebook.”
My answers are to make you think, but everybody else that had answered Will Wheaton, was answering Will on a personal privacy concept afforded of these social platforms. Their Bad for users privacy and Bad as nothing is 100% digital secure leading to your online security risks that can filter back to you locally.
Potentially, a very good news:
https://www.ghacks.net/2022/09/27/opera-limited-buys-back-20-6-of-shares-from-360-security-technology-inc/
Wow, hopefully that goes through.
https://investor.opera.com/news-releases/news-release-details/360-shareholders-vote-yes-repurchase-agreement-opera
Seems like it might be successful! Hopefully we will be updated soon.
Opera Limited develops the Opera web browser and other Internet consumer products. Opera browser, the Opera brand name and other assets associated with the browser were sold to a Chinese consortium in 2016 for $600 million. Opera Limited representatives have come to an agreement with its pre-IPO shareholder Qifei International Development Co. Ltd., a wholly owned subsidiary of 360 Security Technology Inc.”, to acquire the entire shareholding. 360 Security Technology Inc. is a member of a Chinese consortium that purchased the Opera browser and name in 2016. Kunlun Tech Limited and Keeneyes Future Holding Inc held sizable shares of Opera Limited in 2018 as well.
That is something to hear, hope they change the name and Company headquarters first thing if successful in the buy-back. Though, it’s still – –
Opera is a multi-platform web browser developed by its namesake company Opera. The browser is based on Chromium, but distinguishes itself from other Chromium-based browsers (Chrome, Edge, etc.) through its user interface and other features.
BrainFart I guess,
the test for Browsers
BrowserAudit.com.
Checks the system web browser in that it correctly implements a wide variety of security standards and features.
Hint, after a test on your phone (android myself) bet you’ll start using the lap/desk tops more for web related and your phone use just for communication.
I don’t know how much your sponge upstairs can hold before saturation! Forgive me, this is hot thought.
By the process of selecting a web browser and changing your web browser for your operating system. You are also selecting/changing your web browser’s rendering engine. This is what helps to render web pages, while the web browser engine is responsible for handling communications between the web browser’s user interface and the rendering engine. It needs mentioned of the always-present Javascript engine which assists each of the ‘browser things’ mentioned above to process the code belonging to a given website or webpage.
So a modern day web browser needs to be understood here, which is that of encompassing the Javascript engine, the rendering engine, and the web browser engine (3-engines), as all 3 encased under the browser application label working together. In order today of actually getting the raw code belonging to a webpage and then converting it into a usable and viewable display from inside the user’s chosen web browser variant. That is all happening atop your personal devices operating system that holds everything you are digitally as kept and warehoused outside of the webs environment. There is but a thin line dividing say everything you digitally there and tossing it all out on the open web.
Remember this working case, Chrome is just the web browser software that you can install on any OS. While Chrome OS is a full cloud-based operating system, in which Chrome is the centerpiece, and does not require you to have Windows, Linux or MacOS. Though, any browser variant I see headed this direction somewhat, where Chrome OS is basically a minimal Linux kernel running Chrome browser as the only visible process. All the usually needed utilities are available as extensions on the chrome browser eliminating the need for terminal emulator. Blink is here and Gecko, Webkit how far behind? Is this the centralized web and decentralized web uses the same web but sandboxes the ad networks and big tech out as users are the client and servers making up a web03 atop web02 monopoly?
I can’t help but feel it’s not just the images on the browser canvas changing, but the canvas of the old browser has been forgot as being web standards changed especially with the stage things are at today with the 3 popular blink, gecko, webkit, browser core’s engines being offered.
So to finally end. . . If your only doing web based stuff as being able to do online stuff through the browser application. Why doesn’t the Browser itself move out and off our devices to the web sphere as it’s home to only an OS based browser client we need installed. Where we go back to an application as a client (think similar to VPN Client) where something simple as encryption does us as lot of good moving/receiving data in and out of that web sphere. Instead of accommodating the browser by making a place on our devices for it as home, and stand a greater risk – – somewhat move it isolated off our devices saving us personal risk, fending off anomie privacy standards of big tech and ad networks that exploits our privacy with every web engagement.
Sven:
Any chance you can take a look at UR browser (https://www.ur-browser.com) and see if it’s worth doing a write-up? Browsers you’ve had generally good things to say about still get some pretty negative comments from some of the people here. Although no browser is going to be perfect, maybe UR has something to recommend it. Thanks.
Hi vanp, I’m not familiar with this browser but I’ll check it out.
It seems like the latest & greatest new batch of browser really all suck. I have been using Brave for the 8 months and find it mediocre at best, the built in blocker sucks. I have also been using Ghostery Dawn and again it is mediocre at best. Is there possibly a newer browser out there that does not hog up all your memory and keeps your information private for the most part? I highly doubt it…
With ad blocking, you can also use a VPN-based ad blocker. That will cover everything and is not limited by the browser.
Steve I see it summed up this way.
As the browser is today’s browser for the modern web consisting of 3 separate internal engines in one to view the web. That’s gonna be one big hole to gain user control over if not breaking it for personal privacy sake.
Between the 3 popular browser core engines (blink, gecko, webkit) based browser users.
The JavaScript part being needed in the browser that played roll in the results of the normally viewed website. Is a weak link to your security and privacy because of the power it has for the roll(s) preformed to frame and display a window for the device your on. Because of expanding demand where all devices fit web standards in common the introduction of HTML5 and CSS 3 adding your extensive client-side scripting to the World Wide Web, encourages more widespread use of smartphones and other mobile devices for browsing the web.
As of 2022, 98% of websites use JavaScript on the client side for webpage behavior, often incorporating third-party libraries. All major web browsers have a dedicated JavaScript engine to execute the code on users’ devices. https://en.wikipedia.org/wiki/JavaScript
Browser users in general need aid as a tool used in seeing how efficient your adblocker blocking system is considering that with some DNS and browsers there may be problems. By the tool establishing connections in pure Javascript with different urls in (advertising, analytics, and social ads services). BrowserAudit.com
We really should think of a web browser engine as our translators, (ex) know how specific lines of program code affect things that are shown on your display screen. Ending with considering a given web browser’s engine as the most important component of the web browser as liken to the engine of the car. The different browser engines basically are different programmers usually having very different motivations and ideas on what would constitute the best web browser.
Problem How Thing Change – Since Google is the one that is building and developing a large portion of mass-scale cutting-edge services and web apps, the company itself has managed to gain a very advantageous position in leading when it comes to pushing for the web standards that the company itself makes use of.
The vast majority of the processing of a web page is the same (did you know that), but consider the way in which different web browser engines handle web apps security. This is the area where each web browser engine has the option of implementing something entirely different from the other. The web in general along with all the apps and websites on it, have actually managed to consistently become more and more complex.
Tell me how a browser-fork in any flavor can be of yesterdays greats in their projects time won efforts and endeavors again today? Maybe as the Internet is transitioning to Web 3.0, which will add blockchain-related enhancements, cryptocurrency payments, and more focus on user privacy allegedly, won’t be all hype and scam. I believe things have gotten to complex and connected together for our simple personal privacy respected. Every action now needs an reaction or you don’t get access which becomes the link point you surrender your privacy.
Wow someone else actually used Ghostery Dawn. Considering majority of my searches came back as “Nothing found” or “No website domain can be found”, which I find hard to believe because” Big rack japanese girls “can be found everywhere on the net. Yeah, Ghostery Dawn sucks. I’m sure they’ll be plenty of people talking 💩 about this browser, but after getting a no unique fingerprinting and strong protection from the coveryouttracks.com website I’ll stick with it Iceraven browser and been using the search engine [https://alltheinternet.com/] and honestly I been getting better and faster results than DDG. Still trying to get the “411” about how private this search engine is but search results are great and did a local search with VPN off and either engine didn’t know where I was, or it liked the food from Utah and I was in Texas. 👍✌️
It took around 6-10 hours but I got LibreWolf to install Decentraleyes…..seems there was a problem with verifying the addon and I still can’t figure out why that took so long. BlockGoogleAnalytics still won’t load or even pop up, as there is a red line saying a “unexpected error occured”, whatever that means. Something else I don’t understand about most “secure/private browsers” is that many of them has Google or Yahoo search engines set as default. even TOR browser has them! Would most people think Google or Yahoo searh as private or secure?
I am not tech savy as some of commentors on this site, but I do have one sound peice of advice…DO NOT USE CHROMIUM BROWSERS!!! And some of them uses updates or apps from the ChromeWebStore, which is like jumping out the frying pan into the fire. Still all being said Firefox and its forks seem to be the best browsers to pick from, if you have patience to configure them.
Who is !
‘I am not tech savvy as some of commenters’
Each commenter is but a grain of sand on the beach of knowledge being exposed, eye’s waiting for the next wave of change that the tide brings to disrupt and alter.
YKcir it’s the perspective people see’s things from, and yes if you can do as claimed – you up tech me.
My own perspective overall is to see privacy as a Swiss cheese image to any type of gain in your full blanket privacy sought which is shoulder touching with the security coverage anyone can achieve of the needed union.
About the [“secure/private browsers” is that many of them has Google or Yahoo search engines set as default.] Read on down in other posts why Google is a default favorite. Other than that you’ll see in their P-Policy page of each default union browser/search engines combo explaining the sharing and recording of your data, and with primary/secondary partner arrangements and everything else being understood are the open holes to your full blanket P/S effort and leaves it wafer flat. THINK about the US 14 eye’s union as worst than the union of primary/secondary partners I’d think again. As the prior you need to become a target, as in the latter you were always the target… Right?
YKcir
You make the relationship to the browser – search engine combo as the default set lacks your confidence.
What about the other engines part that you don’t see and have no choice in the matter to choose different being used. As the browser is today’s browser for the modern web consisting of 3 separate engines in one to view the web. That one big hole to gain user control over not breaking it.
THE ONLY EXAMPLE = it’s very remote as the power JS has where I can share it right now.
(Note this is outside the browser but gets linked back to JS engine in the browser) High Risk I see…
Go to a OS system User folder like documents where a PDF can be and follow count-
1) Click on the pdf and when browser window opens, 2) rt-click in it and hit INSPECT from the rt-click popup menu, 3) entering the Elements for screen to open.
Here find many JavaScript entries, and mine reflect back to my systems default browser looking as – <script src="edge://resources/js/etc/etc/etc.
WHY?
I said remote example – as I had to find something to hit closer to home in you.
Maybe this with the chrome based engines is one power that JS yields over the user to drive the point home. Chromes recent zero-day patches listed below seem patch related to the JS engine tied to the browser power roll of user input, rendering and JS functions.
#5 High severity security issue due to “insufficient validation of untrusted input in Intents,” a feature that enables launching applications and web services directly from a web page.
#4 High severity heap-based buffer overflow weakness in the WebRTC (Web Real-Time Communications) component, reported by Jan Vojtesek of the Avast Threat Intelligence team on Friday, July 1.
#3 High severity type confusion weakness in the Chrome V8 JavaScript engine reported by an anonymous security researcher.
#2 High severity type confusion weakness in the Chrome V8 JavaScript engine reported by an anonymous security researcher.
[While type confusion flaws generally lead to browser crashes following successful exploitation by reading or writing memory out of buffer bounds, attackers can also exploit them to execute arbitrary code.]
How’s those patched not but being related to JS engine power is like sayin forks of chrome have your privacy/security covered when relying in that ability given a blink fork adopter. Their forks customer base by association in main core browser engines (x3) technology to the privacy they claim? All forks are built on same key core technology that G team has a strong desire of need in push out to mass adoption of the market where G reigns a strong influence over.
@Ykcir I suggest not using many add-ons or extensions, short of U-Block Origin and maybe even Multi-Account Containers. Much of the safeguards in add-ons like Decentraleyes are already built in to Firefox and since LibreWolf is a Firefox fork I would imagine the same applies. Too many add-ons/extensions enlarges your online fingerprint and can make you a target of the very things you seek to guard against.
Agree
Have you noticed that on a site sometimes it tells you that the page you are on is sending you to another site (clicking on something) while there you did, and you have an input needed to respond Allow. Why is this needed ? Think if every website did it this way?
If say you clicked on a highlighted word or link on the site and not some box and nothing being ad based as you could tell. Then your sent away without any permission needed to move to that site.
QUESTION anyone?
When you just get sent over has the site you were on tagged you and for whatever reason but some kind of comps with and whenever you should buy something .
I don’t know, but it interesting enough to know the difference to me.
Hi RP community
I’ve a finding worth to share.
With JS fingerprinting your location can be pinpointed even while using a VPN, location spoofer.
I’ve tested with https://z0ccc.github.io/LocateJS/ in android phone (which is by nature privacy invasive) in Brave, Bromite, Kiwi, Mulch, FOSS browser, FF, Mull Fennec browser; all with recommended privacy modifications of RP, ublock origin, Location spoofers (for Kiwi) AND enabling VPN ( Proton / Privado / Hide me ).
Results ~
1) Passed – a) FF and it’s forks.
They picked up location only from my default device language setting which I’ve intentionally configured as ‘English-Canada’.
b) Bromite.
It shows completely different location like ‘Egypt’. Spoofed by browser itself 👍🏼, not related with my VPN server even.
2) Failed – Brave, Kiwi and Mulch.
3) Can not be executed – FOSS browser.
It’s easy to say ‘block JS’ or use scripts etc. but in ordinary practice it’s impractical for non-experts.
So may be in choosing browser, their inherited capacity is important (and unfortunately Bromite constantly behind updates now😢).
Thanks
I hear you well blocking the JS engine of installed default browser breaks the browsers ability to render it normally for website. Random websites where your searching and likely never been before a use of JS blocked is warranted. Normally visited sites only fair better because of your history in visiting it. The problem and issue with JS still persists in certain browser core engine(S). The JS part being needed in the browser that played roll in the results of the normal viewed website. Is a weak link to you security and privacy because of the power it has for the roll(s) preformed. If you can see the website in static view like (texts only) instead of with the visual bling candy. Find your info you seek move on. Then unblock JS, customize a block for any harmful sites.
You can test a websites URL in VirusTotal . com by their url tab selecting it to enter the url scan by multi-security engines.
LibreWolf will absolutely not allow you to add extensions like Google Analytics Blocker or Decentraleyes. Have they or are they receiving some payment from Google to allow this tracking behavior? I already dumped Firefox and may have to consider using it again. Anyone else having this problem with LibreWolf or is there a work around for this? Does Ublock and Privacy Possum block Google Analytis?
Is there a version of Google Analytics Blocker that is not made by Google that will work on Brave Browser? Brave’s built in blocker is garbage and sucks. Why are there no good browsers anymore?
FOOD FOR THOUGHT
Web3 – the vision – min. 1:33
https://www.youtube.com/watch?v=hxLQ_L10cwI
This is basic hype to me the untechy user (next link)
https://decenternet.com/philosophy.php
Here is so called working use.
(WHAT IS THE OSIRIS BROWSER?) For the first time, decentralized applications run on your personal computers browser without complicated technical procedures or having any knowledge of blockchain technology.
Concept understanding as contextual breakdown thus far.
https://en.wikipedia.org/wiki/Web3
Notice-Technology scholars have argued that Web3 would likely run in tandem with Web 2.0 sites, with Web 2.0 sites likely adopting Web3 technologies in order to keep their services relevant. {This is what I think somewhat as well…it what I see Brave wanting.}
Others have expressed beliefs that Web3 and the associated technologies are a pyramid scheme, and some other critics of Web3 see the concept as a part of a cryptocurrency bubble, or as an extension of blockchain-based trends that they see as overhyped or harmful, particularly NFTs.
Brave guessing why (bat token) I’d seen it mentioned in a Web3 browser article. Its based on Chrome as it’s blockchain attributes, which chrome having had 6 zero-day patches to roll out presently. Question – when I see “decentralized applications run on your personal computers browser” and 6 zeroday patches needed by Chrome, what is the G team up to? They presently have the biggest spiderweb and technology influence in which the majority of web users fall in to. I can’t seeing them walking away from being on top. The patches needed, are they to the progress of Web3 (as web 2&3 bond) or ensuring they G still maintains some control to tap and their dominance and understanding the technology needed the most to reign on new web standards?
I know personally when the paycheck you give yourself shrinks owing a business, it’s still nice being in the money stream if only for that to be in passing it along.
Remotely a picture I have, is the web3 internet as being the browser playing rolls in the clients part and the switch operator linking your series of local installed layered app nodes that flavors some imaginary currency you can’t even hold in your hand.
But how much cash (green-backs) do people touch today? Once bitecoin is converted ‘pun’. . .
You’ll still have an internet bill from your ISP just as you can’t run a home lightbulb without the needed electric. What your take readers and comments?
Thank you
Scott August 25, 2022 [redacted]
I have spent years researching secure (and not-so-secure) search engines. I advise my clients to use SwissCows, Qwant, Mojeek, MetaGer, and Brave searches.
Brave (browser) is just okay, since it harvests 25 warnings and one critical point when tested by BrowserAudit.com.
Thomas September 9, 2022 [redacted]
Very interest website BrowserAudit .com, how reliable it is?
Seems safe: 0/88 No security vendors flagged this URL as malicious
https://www.virustotal.com/gui/url/805cc2334f65b41d712a875f74b5b5eed9bef491ec68606d8f3fb52f892df074/details
Seems thoroughly detailed: Passed 352 / Warning 31 / Critical 1 / Skipped 20
Report was on a Brave browser without a single update taken since installed probably in june22, this is the critical 1 for the topic tested and that critical flag generated on flagged subject.
Topic – Cookies
A lot of cookie security relates to the same-origin policy, and the setting of cookie scope through the Domain and Path attributes. This is covered in the Same-Origin Policy section. In this section, we are testing two other aspects of cookie security: the HttpOnly and Secure attributes. We test the behavior of these attributes as defined in RFC 6265 “HTTP state management mechanism” (Kristol, David M. and Lou Montulli, 2000).
Subject – Secure flag
When a cookie has the Secure attribute set, a compliant browser will include the cookie in an HTTP request only if the request is transmitted over a secure channel, i.e. an HTTPS request. This keeps the cookie confidential; an attacker would not be able to read it even if he were able to intercept the connection between the victim and the destination server.
The Secure flag is supported by all major browsers.
We have four tests, testing the behavior of the Secure flag both when the cookies are set by the server and set by JavaScript. In each pair of tests, the first checks that a cookie with the Secure flag is sent to the server with an HTTPS request. The second test is the interesting one: it checks that a secure cookie is not sent with a request over plain HTTP.
FLAGGED RED – cookie set by JavaScript should not be sent over HTTP
https://browseraudit.com/results/134969/e505123f78fb96045960fa68c44c8f27fbd9b5ad
My OS FreeBSD and I tested Firefox 104 with UBlock Origin, Canvas Blocker and Smart referer addons and arkenfox user.jsm – javascript enabled:
Passed 331, Warnings 13m Critical 0 Skipped 57
and test Qutebrowser 2.5.1 with some mine settings but javascript enabled:
Passed 376, Warnings 8, Critical 0, Skipped 20
I am using both browsers.
Cool thanks for the share
Hi RP community
About chromium’s clipboard access issue –
I found FOSS BROWSER in android free from this issue. That is website don’t writing on clipboard without permission as with Brave, Bromite or other chromium browsers now.
But there is a privacy issue with FOSS BROWSER. Though it doesn’t collect/send/store any user data, it is built on Android System WebView, which has lots of telemetry.
Good tip!
Problem – Since Google is the one that is building and developing a large portion of mass-scale cutting-edge services and web apps, the company has managed to place itself in a very advantageous position when it comes to pushing for the web standards that the company itself makes use of.
The many faces of EVIL (brick on brick) in their G kingdom must be dislodged before the heart is exposed leading to a crushing of the king in this large kingdom and it’s hold in reign over all web users.
(think of the worst – prepare for that, if it’s found out to not be as bad – then survive)
Had you missed this? Finally had time to run it down…
brave://settings/content/clipboard
Done, just back-page once and find under a Content (label) the JavaScript entry.
Sites usually use Javascript to display interactive features, like video games or web forms…
Customized behaviors
Sites listed below follow a custom setting instead of the default
Not allowed to use Javascript
Allowed to use Javascript
Excuse me shr should of had clipboard shown as I was addressing it. Anyway you’ll find the same structure offered to change the default browser setting of clipboard and javascript.
That being found like On / Off as your default set and then any sites you want the opposite browser response happening on as the customized action for it.
With the introduction of HTML5 and CSS 3 adding extensive client-side scripting to the World Wide Web, encourages more widespread use of smartphones and other mobile devices for browsing the web. Those two with Javascript abbreviated JS, are the underlying programming languages that constitute the core technologies of the World Wide Web. Where 98% of websites use JavaScript on the client side for webpage behavior, often incorporating third-party libraries. All major web browsers have a dedicated JavaScript engine to execute the code on users’ devices.
This is where blink, gecko, webkit based browser users need aid as a tool used in seeing how efficient your adblocker blocking system is considering that with some DNS and browsers there may be problems. By the tool establishing connections in pure Javascript with different urls in (advertising, analytics, and social ads services).
Sven
Often abbreviated JS, is a programming language that is one of the core technologies of the World Wide Web, alongside HTML and CSS. As of 2022, 98% of websites use JavaScript on the client side for webpage behavior, often incorporating third-party libraries. All major web browsers have a dedicated JavaScript engine to execute the code on users’ devices. https://en.wikipedia.org/wiki/JavaScript
Us noobs need an article/piece done on JavaScript as it’s roll and any harm associated with todays web browser – please sir!
Have you tried SRWare Iron? it is very secure and privacy oriented. It is a very lightweight option specially thinking about RAM. https://www.srware.net/iron/
Not a lot of public site info since 2015.
In December 2014, Lifehacker said that Iron offers little that is not available by simply configuring Google Chrome’s privacy settings. However, the_simple_computer wrote that Iron removes the Google Native Client, Google’s custom navigation and error pages and other similar features.
In October 2014, the_simple_computer wrote that even though SRWare Iron released under the BSD licence, the latest source code publicly available at the time was incomplete and for version 6, even though the binaries were on version 14; source code was moved to RapidShare in 2013, with external access blocked, effectively making the program “entirely closed source”. In the same year, Lifehacker wrote that SRWare had not released the browser’s source code for years. In 2015, SRWare temporarily resumed releasing the source code for the browser.
Questions – Why is updating of the browser SO IMPORTANT…reflecting back to the IE browser days, where ages actually went by without any browser update? What gets updated to the browsers core function ? Barring any additional security functions it may have such an adblocker and/or malicious sites guards, etc…it has incorporated, which would need to be updated to maintain a zero-day defense of those security functions.
So you trust and rely or wanting to in your browser for security protective functions which are better left handled by a dedicated as well installed software to your OS instead. Software which can not easily connect your dots across the web you roam. But basketing these and more up in the browsers overall functions is just one failure which can cause you many defeats. as well as knows and sees everywhere -everything you do with the web. JMO
Because there are often new security exploits and holes that are discovered that need to be patched, thereby requiring an update to ensure browser security. Here is a recent example:
https://www.bleepingcomputer.com/news/security/google-chrome-emergency-update-fixes-new-zero-day-used-in-attacks/
“With this release, Google has issued security updates to address the sixth Chrome zero-day patch since the start of the year.”
Sven I’m on board (agree logically to reason) with the browser variants engine cores needing and getting key core updates. Then these forks (lack of better word) as a core browser engine adopter(s) offer you those browser core engine updates. Which is when relevant new Web standards continue to be added to the engine or something within the core needs patched in an security issue as well as inherent bugs.
By the process of selecting a web browser and changing your web browser for your operating system. You are also selecting/changing your web browser’s rendering engine. That helps to render web pages, while the web browser engine is responsible for handling communications between the web browser’s user interface and the rendering engine. It should be mentioned the always-present Javascript engine which assists each of the ‘things’ mentioned above to process code belonging to a given website or webpage. So a web browser needs to be understood here which is that of encompassing the Javascript engine, the rendering engine, and the web browser engine as all work together. In order to actually get the raw code belonging to a webpage and then converting it into a usable and viewable display from inside the user’s chosen web browser.
Active browsers core engine choices today given of Gecko-Firefox/Thunderbird , Blink-Google Chrome/Chromium-based, WebKit-Safari, Goanna-Pale Moon/Basilisk/K-Meleon, Flow*Proprietary, Serenity-Ladybird. https://en.wikipedia.org/wiki/Comparison_of_browser_engines
Browser engine: https://en.wikipedia.org/wiki/Browser_engine
A total of three main web browser engines that dominate the market today and worth users knowing more about. Blink, Gecko, WebKit – first you should think of a web browser engine(s) as translators, (ex) know how specific lines of program code affect things that are shown on your display screen. Ending with considering a given web browser’s engine as the most important component of the web browser as liken to the engine of the car. The different browser engines basically are different programmers usually having very different motivations and ideas on what would constitute the best web browser. We know not how the web browser engine go about its job of displaying colors, refreshing pages, optimizing code and all the other stuff.
You might find it surprising, but this is exactly how the market has reached the situation that it has reached today. Major web browser engines stay the course and truth be told, no one in their right mind would argue that much of what different web browser engines do is pretty much standardized and not all that different from each other. The vast majority of the processing of a web page is the same (did you know that), but consider the way in which different web browser engines handle web apps security. This is the area where each web browser engine has the option of implementing something entirely different from the other. The web in general along with all the apps and websites on it, have actually managed to consistently become more and more complex. As a result of that, web browser engines have had no choice but to find a way to handle more and more code. Part that differentiates web browser engines is how the new dynamic code is optimized and processed having an impact on the speed with which a given page fully appears on the screen. This is the part where Javascript engine comes in and actually plays quite a big role.
Regarding the modern version of the web, questions such as should your web browser in question render text before it loads images or should it go the other way? Then there comes the question of how should a given web browser engine manage multiple processes which may be taking place in multiple tabs? Should a web browser engine not only have to cover any existing standards regarding the web, but they are also required to support various new standards that keep popping up, as the thing we know as the internet becomes ever-more mysterious and complex?
On “With this release, Google has issued security updates to address the sixth Chrome zero-day patch since the start of the year.”
Since Google is the one that is building and developing a large portion of mass-scale cutting-edge services and web apps, the company has managed to place itself in a very advantageous position when it comes to pushing for the web standards that the company itself makes use of. Developers behind this web browser engine are able to push updates fairly rapidly and the web browser engine itself is robust.
Of course, there are many other less known issues. But they are of concern only to people who like to think of themselves as developers.
We’re talking about issues such as,
The amount of time it can take a developer to add and approve code.
The standard procedures one has to follow to fix bugs.
The extent to which the given web browser engine is tied up to the web browser in question.
End users who have an interest in keeping a count of the frequency in which a given browser develops and rolls out update patches, would definitely want to keep all points mentioned above in mind. To as mentioned above, if we are looking at the surface level only then there actually isn’t such a massive difference between all the available mainstream web browser engines.
Safari with the help of WebKit, Firefox with the help of Gecko and Chrome with the help of Blink render the majority of the websites that you will ever visit almost the same. Not only that, they do so pretty much at the same speed. The reason for that is all major web browser engines now accept and implement the same kind of basic standards of the modern web. Which 5+ years ago you should definitely know by now that this wasn’t always the case.
Blink still has not gotten over its chronic problems such as its tendency to hog memory in specific situations. On the other hand, Mozilla Firefox has managed to impress everyone and continues to do so with the help of its Quantum update to Gecko. Again, whatever difference that exists in the above-mentioned web browser engines, do not really have a big impact on the performance that the end user gets to experience.
In simpler terms, if you are happy with your current web browser then you should continue to use it without any second thoughts.
Of course, Blink looks all set to continue its dominance. And that might actually have serious negative side effects on the rest of the web community. That is because at the moment almost all the web browser technologies that may fall on the side and get left behind along with the ones that will come in the future and make an impact. Truly are dependent on how Google engineers are thinking and how they call the shots. Currently, because of its market share, it has the privilege of deciding how the web should work for the vast majority of the people on the internet. Firefox still has enough user base to not let Chrome have a free roam. As result, the danger most of us end users are having to deal with is the web would go in the direction of whatever works best FOR and WITH Google Chrome rather than the general web community.
We haven’t touched on your privacy with these major web browsers engines but you really think they care if it meant loosing their dominance? They are setting the rules of how you can play? Let them know your privacy within and outward is a main user concern.
Google zeroday
#6 High severity vulnerability caused by insufficient data validation in Mojo, a collection of runtime libraries that facilitates message passing across arbitrary inter- and intra-process boundaries.
#5 High severity security issue due to “insufficient validation of untrusted input in Intents,” a feature that enables launching applications and web services directly from a web page.
#4 High severity heap-based buffer overflow weakness in the WebRTC (Web Real-Time Communications) component, reported by Jan Vojtesek of the Avast Threat Intelligence team on Friday, July 1.
#3 High severity type confusion weakness in the Chrome V8 JavaScript engine reported by an anonymous security researcher.
#2 High severity type confusion weakness in the Chrome V8 JavaScript engine reported by an anonymous security researcher.
While type confusion flaws generally lead to browser crashes following successful exploitation by reading or writing memory out of buffer bounds, attackers can also exploit them to execute arbitrary code.
#1 Described as a “Use after free in Animation” and was assigned a High severity level discovered by Clément Lecigne from Google’s Threat Analysis Group.
Attackers commonly exploit use after free bugs to execute arbitrary code on computers running unpatched Chrome versions or escape the browser’s security sandbox.
Bromite is behind on being updated … again! The last time it was updated was almost a month ago and (yet again) the browser has been flagged with an announcement that it is behind on its updates:
https://www.bromite.org/vulnerable-version
Unfortunately, this isn’t the first time either. PrivacyGuides.org dumped recommending Bromite precisely because of infrequent updates and, unless CSagan5 changes his ways, Bromite users can expect this to happen quite often.
Bromite is an all volunteer effort and small wonder that they fall behind on updates from time to time. None the less, this is not good for people who rely on or like it since delays jeopardize a user’s privacy and security.
Thanks for the update Mike. I’ll be updating this guide soon with changes.
UPDATE: Bromite has been removed from the recommendations
@Sven Thanks! I just checked and Bromite was updated 5 days ago and it was neglected for a month. It is too bad, but CSagan5 and others involved in their project need to get their act together.
Thanks Mike
From the last delay of update as you pointed out earlier, I did back up my all stuffs which I used to do with Bromite, in Fennec (with hardening).
And there are also some present confusion about chrome’s clipboard issue going on….
shr
(websites may push anything they want to the operating system’s clipboard without a users permission or any user action.) This means to write, so then worst case, JavaScript can be used to modify the clipboard content via an attack – dubbed ‘paste jacking’.
(operating systems have means provided for short-term storage and transfer within and between websites and your system application programs this is know as the systems clipboard).
Confusion about chrome and like based browsers clipboard issue yes (FOGGY), but specifically as I quoted from a comment of and about, that I found within the link you had supplied:
Sdar said on August 27, 2022
Reading the clipboard will require specific permissions on both chromium and firefox based browsers and will not be granted automatically as it’s done with the write permission.
If you remotely understand read and write permissions on window OS devices, the read permission seem to be at a lower priority that’s given, then as opposed to a write permission being given generally. Basically, a needed priority as to the function that an app or program is aligned to have access on your system.
Now what I find shocking is not knowing what a website (say 10 open in different browser tabs – some logged in) or even the browser itself has written on my OS clipboard, and since as I understand about your write permission on a site. Can easily be given simply by acting on a popup, cookies or whatever may cause your user input, as soon as you have a user input the tab is considered active and the clipboard-write permission is granted automatically. Since our defensive use of ad blockers today (baked-in / add-on) that act on popup’s and cookies automatically – is that write permission been achieved then making the site visitor venerable to more than we realize? How far to a read permission grant of the systems clipboard being achieved as it’s where everything resides in plain texts that was just written in the active site session?
JavaScript should not be enabled on random websites because you run risk to the session hijacking vulnerability. All of your login information decrypted into plain text” and “all of your unique, sensitive data” such as session cookies are stored in ram memory at all times until the browser is closed that is stored and contained within your systems clipboard.
To bad Sdar that made the demo on https://jsfiddle.net/dvxaywrj/1/show isn’t here on restore privacy as RP is a site of people contributing pieces of answers to the privacy puzzle we’re faced with. We are all at different levels in knowledge that was hard won, as the experts are out making the big money and maybe the cause for us to generate the questions we ask.
Hi Sven,
(I wrongly posted this in search engine section before, sorry for that)
May be you already came to know that, with latest update, websites may write to the clipboard in Chrome without user permission.
Hear is the link of this info I found – https://www.ghacks.net/2022/08/27/websites-may-write-to-the-clipboard-in-chrome-without-user-permission/?amp
I’ve confirmed that with my Brave and Bromite.
FF doesn’t has this problem.
So now what is your view about this. How much anti-privacy it is and what should we do ?
If you please….
Regards
I can somewhat understand why this is concerning and would be interested in seeing what @Sven has to say about it.
Wikipedia, Hacker News, gHacks Tech News
Clipboard (computing)
https://en.wikipedia.org/wiki/Clipboard_(computing)
The clipboard is a buffer that some operating systems provide for short-term storage and transfer within and between application programs. The clipboard is usually temporary and unnamed, and its contents reside in the computer’s RAM.
The clipboard provides an application programming interface by which programs can specify cut, copy and paste operations. It is left to the program to define methods for the user to command these operations, which may include keybindings and menu selections. When an element is copied or cut, the clipboard must store enough information to enable a sensible result no matter where the element is pasted.
Clipboard: Computer security
https://en.wikipedia.org/wiki/Clipboard_(computing)#Computer_security
Clipboard hijacking is an exploit in which a person’s clipboard’s content is replaced by malicious data, such but not limited to as a link to a malicious web site.
JavaScript can still be used to modify clipboard content via an attack dubbed ‘paste jacking’
There have been exploits where web pages grab clipboard data.
Clipboard: APIs JavaScript
https://en.wikipedia.org/wiki/Clipboard_(computing)#JavaScript
Using JavaScript isn’t supported by every browser since altering the clipboard of a user can represent a security issue.
Chrome allows websites to write to the clipboard without the user’s permission | Hacker News
https://news.ycombinator.com/item?id=32614037
Web Platform News
https://webplatform.news/
Issue #182 · w3c/clipboard-apis · GitHub
https://github.com/w3c/clipboard-apis/issues/182
Naleksuh commented, “This has been a problem for some time. Because of this problem, JavaScript should not be enabled on random websites.”, but This comment was marked as off-topic.
Apparently, your browser stores passwords and sensitive data in clear text in memory – gHacks Tech News
https://www.ghacks.net/2022/06/12/your-browser-stores-passwords-and-sensitive-data-in-clear-text-in-memory/
Security researchers have pointed out the session hijacking vulnerability is to Google,
Google responded, “Session hijacking risk measures are the fault of the end user, and the browser developer is not responsible for them. We will not fix it”.
Take away:
Google Chrome (and the Chromium family of web browsers and Vivaldi Mail) deploys “all of your login information decrypted into plain text” and “all of your unique, sensitive data” such as session cookies. Even if a Chrome process with only a new tab opens, stored in ram memory at all times until the browser is closed. If you run Google Chrome or another Chromium-based web browser, then websites may push anything they want to the operating system’s clipboard without a users permission or any user action. Mozilla’s vision is based on user consent, which is the exact opposite of Chromium, which operates without the users consent. Firefox, gets nowhere near red of the security issues of other browsers like Chrome, Edge, Brave and Vivaldi.
If I understand correctly Google has bypassed a basic privacy feature for the sake of its insane doodles! Doodles for which you’ll find several dedicated scripts to remove those exotic absurdities. But what about this clipboard risk?
O&O Shutup contains a section “Activity History and Clipboard”, is then the Clipboard risk gone if O&O is used or would extra attention also be needed in Settings-System-Clipboard as switched off and inaccessible).
Brave – Paste below url into addybar,
brave://settings/content?search=clipboard
Then hunt for the clipboard setting. It is hidden from easy view and intentionally made very difficult to find. But once found, disable the clipboard access setting; then sites will no longer be able to access this highly private data holding resource. While there, disable access to most all private resources such as USB, File, Camera, Mic, et al access. Chromium et all have a similar setting located via the same url scheme.
Add-make the usual global filter in uBlock and it is fixed *##+js(acis, navigator.clipboard)
it is weird because it doesn’t work like the usual scriplet injection but nothing gets copied to the clipboard which is I guess okay?
There are many ways to stop it since it is a inline script on that page, but uBlock made it easy and it works, and it should work on other cases.
Thanks for detailing.
Could you please elaborate the solution parts, specially with brave (and other chromes) and ublock origin ?
It’s little difficult to follow for a non-expert like me.
Greetings.
@TwocanSam Too much information. Is it safe to use Chrome-based browsers or not? What’s the deal?
shr & Mike looks important enough to find out for those browser users
From shr’s link reveling the news-
“Computer users may use the clipboard of the system for temporary storage: a password for entering it on a website, a file for moving it to another location on the system, or a bit of text found on a site for pasting in a Word document or a search engine.
Sites should never have access to the content of the clipboard, at least not without user permission. Chrome and other Chromium-based browsers have no such restriction currently. The makers of the Brave web browser considered adding the user gesture requirement in 2021, but this has not been implemented in the browser. The two other major browsers that do are not based on Chromium, Firefox and Safari, protect the clipboards of their users.
Source: MARTIN BRINKMANN Aug 27, 2022
Comments:
Sdar said on August 27, 2022
REPLY
A little demo, as I said you can conceal this any way you want, a dismiss for a popup, cookies or whatever may cause user input, as soon as you have user input the tab is considered active and the clipboard-write permission is granted automatically.
In this demo you can click the button so it writes to your clipboard, but I wanted to show that it doesn’t need to be a button so clicking anywhere on the site (except the edit in jsfiddle button) will write on your clipboard.
https://jsfiddle.net/dvxaywrj/1/show
Reading the clipboard will require specific permissions on both chromium and firefox based browsers and will not be granted automatically as it’s done with the write permission.
Anonymous said on August 28, 2022
People are just dramatic for real, I mean, if people really think they have control over websites they visit and developer’s god complex, well, too bad. They should quit the internet. Developers have the power and some will use and others won’t, that’s life and that’s your risk for going to any website.
How to Block Unwanted Content From Web Pages Using uBlock Origin
https://www.freecodecamp.org/news/how-to-block-content-from-web-pages-using-ublock-origin/
brave://settings/content/clipboard
Finally had time to run it down…
Regarding the RP checklist, at the bottom of the page. When setting up a brand new device, starting from scratch, what is the best installation sequence to retain the most privacy? For example, segregated or throwaway email address, 2fa, and new passwords, will be asked for and should be ready to use for some other items. (I have never succeeded at creating these on-the-fly in the middle of another process.) I muffed this one on the new phone, partly because it became my only internet before I had a vpn going on it. It’s hard to logically plan when each step is your first time. Got a lot of exposure along the way. Please don’t make me tattoo NOOB on my forehead! So next device I try again. I’m looking to avoid leaks during setting it all up.
Deep question Juneteenth as if there are many kinds of devices all connecting to the hive. Lifestyles to who you’ve known and those whom know you, gives a path in life all to ones privacy loss. Secret agent or just a conscientious soul trying to harden that open path in your privacy of self life being the goal. Off the shelf products seldom offer any privacy refinements. What you do for one device you must do for all, TV to the car and those you pack that connect up to the hive.
Though all being different all must be treated alike for mining your data.
Your right about one’s privacy in the initial set-up counts most in that particular device. If you start off giving it up point blank by accepting without questioning the decisions your presented and any rights infringements by it’s primary as well as secondary partners involvement. You’ve lost the war.
I have spent years researching secure (and not-so-secure) search engines. This article professes that DDG and StartPage are “secure”. They are not! DDG reports back to eBay and Amazon, while StartPage had been acquired by System-1 (an ad-tech agency).
I advise my clients to use SwissCows, Qwant, Mojeek, MetaGer, and Brave searches.
As far as browsers may go, I prefer Pale Moon and Basilisk. I specifically advise against the use of Chinese-owned Cent and Opera, Tor, Vivaldi, Chrome, Edge, IE, WaterFox, and several others. Brave (browser) is just okay, since it harvests 25 warnings and one critical point when tested by BrowserAudit.com.
@Scott as it turns out, the money System 1 gave Startpage was an investment and not to acquire the company.
https://www.ghacks.net/2019/11/18/startpage-replies-to-questions-about-ownership-change/
what is money – it is power and usually has to be paid back at a premium. a privacy built businesses borrowing money from the soul harm their to protect from is just nonsense.
Very interest website BrowserAudit .com, how reliable it is? I did use Pale Moon, it was decent but the updates were far & few and it was causing my webpages to freeze and crash. How does Basilisk compare to Pale Moon? I am currently trying Ghostery Dawn it is OK, do not like the blacked out background, it is annoying.
Scott please be more active in our comments here! Yes I see you rely on your skill for an income. Maybe Sven and you can find an arrangement to refine our communities understanding. Be it on the push to Web3 in the fields of decentralized web software protocols, Or to browsers and the search/browser engines in use and slated new advancements to come. Maybe even to submitting articles on restore privacy?
How dangerous is JavaScript now and how can the end user defend against? Since the always present Javascript engine which as all major web browsers have a dedicated JavaScript engine to execute the code on users’ device.
Brave “tampers” with your privacy settings. Prove it yourself. Go to settings –> shields:
Set “trackers and ad blocking” to “aggressive”
Set “block fingerprinting” to “strict”
Browse the web and note performance. Exit Brave. Restart Brave. Check your privacy settings. Both have been reset to “standard”. This was confirmed with both the windows version and the Linux version. If Brave will pull this stunt, what else would they do? Not using it. Ever. Tell your friends.
I’ve been using Brave for years and never had this issue.
Though there are some controversy about code modifications to whitelisting Amazon, I never faced automatic change of brave shield configuration.
It works fine in my android phone.
May be some other problem causing this annoyance.
I have endured many similar crimes against me on android. It was my cellular provider doing it. No stopping it. I invested in a different phone plus the best cellular provider privacy policy I could find. Please try to see if Brave is truly the culprit. This would be a dealbreaker for sure.
@max
It’s probably about your Clear Browsing Data settings. There you should uncheck Site & Shield Settings (not to be deleted), otherwise Brave will revert it to the default.
Know any editing software free which respects privacy? As well as any foss ms excel and powerpoint
@Wil you can find lots of open source alternatives for Microsoft and even Google products (including browsers) at AlternativeTo:
https://alternativeto.net/
Otherwise, I would say a good alternative to MS Excel would be LibreOffice (link below). I am unsure about a PowerPoint alternative. Hope this helps and good luck!
https://www.libreoffice.org/discover/calc/
Hi RP community,
Android version of ungoggoled chromium stopped updating for a long time. It’s github repro archived by the dev unfortunately.
At this situation to maintain the browser compartmentalization technique, I’ve found Mulch browser as an alternative 2nd or 3rd one.
It’s now updating frequently, at present have chromium version 104.
What are your opinions about Mulch.
If you please……
For your convenience here are some links –
1) https://divestos.org/index.php?page=our_apps#mulch
2) https://divestos.org/index.php?page=browsers
Too bad! Yet another well meaning enthusiast project bites the dust.
Thanks Mike for your opinion.
It helps us to make proper judgment.
Could you please share some of your findings about Mulch kindly ?
I have not used Mulch but based on some user reviews I have read, looks like Mulch is a browser designed for DivestOS and is similar to Bromite. If so, then Bromite or Brave on Android would be the way to go rather than build a version for your Android device.
I cannot seem to respond to you Mike, the button is not there.
DivestOS, Mull, and Mulch are my projects. Mull is a privacy oriented browser, and Mulch is security oriented.
Mulch is two distinct bits: The WebView, which is included in DivestOS, and the standalone browser which works on all Android 7.0+ devices.
Per these tables you can clearly see Bromite falling behind with known security issues, while Mulch updates usually within two days: http://divestos.org/misc/ch-dates.txt
Hello SZ
At last I find you somewhere to communicate at least. 👍🏼👍🏼👍🏼
Thanks to Sven for creating this great platform – Restore Privacy. 🙏🏽 We are obliged to him other expert members here.
I’m using Mull for years as my primary browser with my logged sites in Bromite (for more security in android versions of browsers, as you picted in https://divestos.org/index.php?page=browsers).
Later I’ve came to know about Mulch.
Many times I’ve found that it’s very difficult to communicate with you, though there are some way provided in divestos.org’s community section.
Could you please create a more common channel like Signal or Telegram, and a simple E-mail for ordinary users like me ?
I’ll like to see such option in https://divestos.org/index.php?page=community
Thanks a lot for your excellent projects and good wishes.
Best Regards