
In a statement sent to RestorePrivacy earlier today, SevenRooms has confirmed that it suffered a data breach via a third-party vendor.
Samples of data allegedly belonging to the hospitality and restaurant guest data management (CRM) services provider ‘SevenRooms’ has appeared online, and its seller claims there has been a data breach with the company.
The data appeared on the hacking forum ‘Breached,’ and the samples include text files containing client data, payment details, information about reservations, and more.
The seller claims to have 86,847 CSV files, amounting to over 427 GB of data. The type of files indicates that the company might have suffered a database leak as a result of a breach on one of its servers.
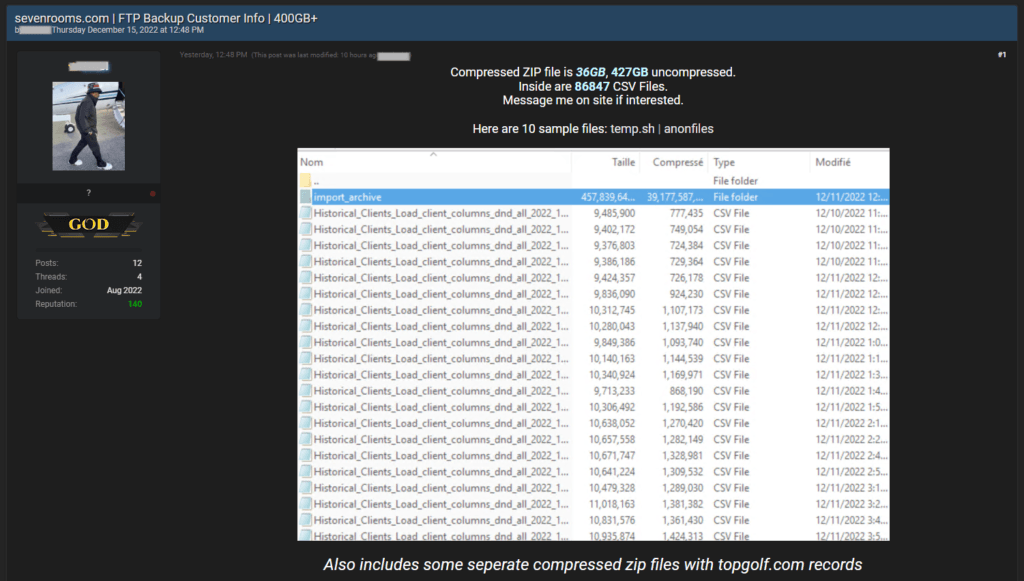
The leaked data has also been verified as authentic by the forum’s owner, ‘pompompurin,’ who vouches for the authenticity. Considering the proven record of the forum administrator on past data dumps sold on the platform, there’s a very high chance that ‘SevenRooms’ has indeed suffered a security breach, and the data is real.
RestorePrivacy contacted SevenRooms to request a comment on the validity of the samples and whether the firm has recently experienced a security incident.
Update: SevenRooms confirms data breach via third-party vendor
In a statement sent to RestorePrivacy after this article was first published, SevenRooms has confirmed a data breach via a third-party vendor:
SevenRooms recently learned that a file transfer interface of a third-party vendor was accessed without authorization. This may have affected certain documents transferred to or by SevenRooms, including the exchange of API credentials (now expired), and some guest data, which may include names, email addresses and phone numbers. Our protocol is to not store credit card information in that space. SevenRooms does not collect social security numbers, bank account information, or similarly highly sensitive information from individual guests. We immediately disabled access to the interface, launched an internal investigation, and we currently have no evidence that any of SevenRooms’ proprietary databases were affected. We have retained independent cybersecurity experts to assist with this investigation and will provide additional updates as appropriate.
– SevenRooms’ updated statement to RestorePrivacy on December 17, 2022
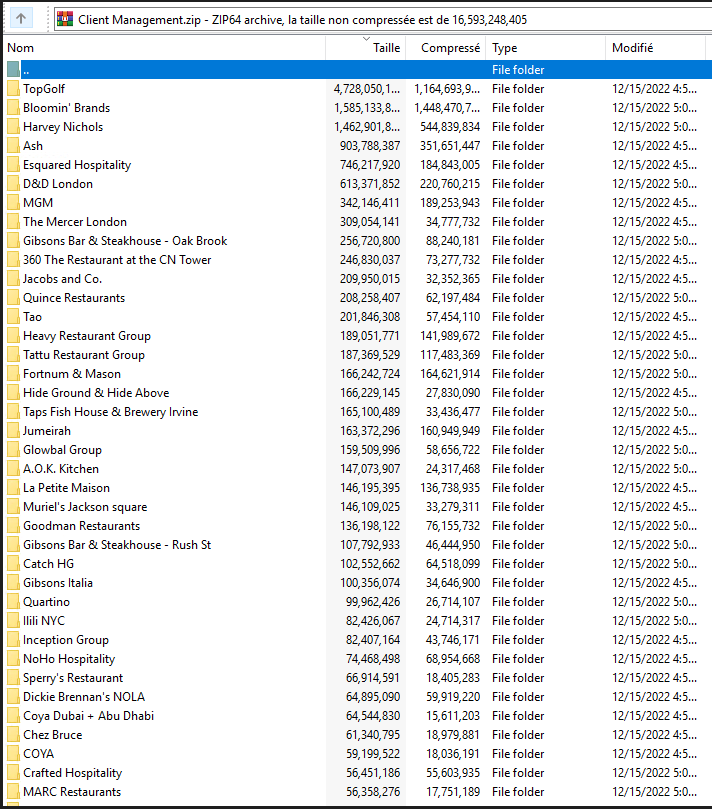
Given these details, the data dump might contain highly sensitive information exposing a large number of guests of international hospitality chains and restaurants, including MGM Resorts, Wolfgang Puck, Bloomin’ Brands, Australian Venue Co., Mandarin Oriental, and more.
The privacy implications would be devastating for many of the clients of these chains, especially in the cases of hospitality providers, which is a more sensitive field.
The samples shared by the data seller list the mentioned entities and many more. However, RestorePrivacy has not been able to confirm that any of these chains was impacted by a security incident on the CRM provider.
Notably, the seller also lists API keys in the dump, which, if they contain confidential secret keys, may be used for authorization on private apps, data exfiltration, deeper network infiltration, and more.
Last updated on December 17, 2022 to include SevenRooms’ statement sent to RestorePrivacy.

 Uber Suffers New Data Leak After Third-Party Vendor Gets Hacked
Uber Suffers New Data Leak After Third-Party Vendor Gets Hacked
Hi RP,
Great article!
In this case it sounds the vendor was storing minimal data and using some separation of data. Which is a good thing.
It is also respectable that the vendor responds to media inquiries.
I have heard it stated else where that if PPI was stored in an encrypted form that this and other breaches would be inconsequential, (assuming the key is not compromised);
That is even if data is exfiltrated that it would have know value to the attacker and victim data would be unreadable.
At a high level, if PII was encrypted, would that mitigate this and similar breaches?
From where you “heard” about encrypted form?