
Threat actors are increasingly abusing the InterPlanetary File System (IPFS) to host malware samples and phishing kits to evade detection from security products and increase their campaign resilience.
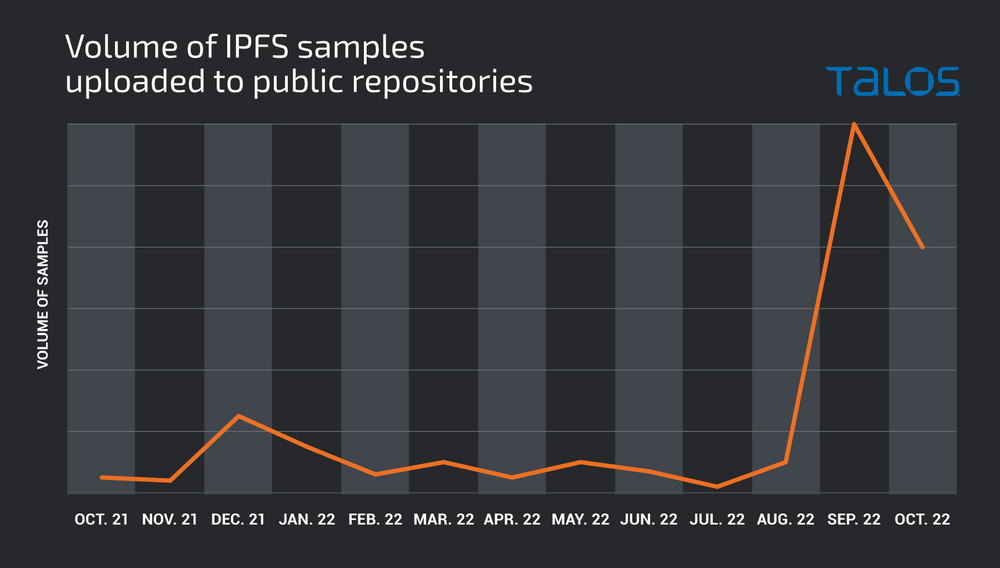
According to a report published today by Cisco Talos, there’s a steep rise in the number of malware detections concerning samples originating from IPFS gateways.
Given the current conditions in the security industry and the stance of organizations on the matter, this trend is expected to continue.
CISCO
The IPFS Advantage
IPFS is a file-sharing protocol launched in 2015, offering a new solution for building decentralized peer-to-peer networks.
It replaces the idea of hosting data on a centrally located server with a system that relies on content addresses, nodes, mirrors, and a distributed hash table.
IPFS can host various types of files, including the resources required for rendering web pages. Contrary to BitTorrent, IPFS can serve as a complete solution for a single global network.
CISCO
Because the content is hosted on a decentralized network, taking down malware or phishing sites is practically challenging, if not entirely impossible, in many cases.
This tactic ensures that malicious sites stay online for longer; thus, malware distribution and phishing campaigns are not interrupted.
Additionally, there’s the aspect of law enforcement, and the advantage of obfuscation offered by IPFS since untangling an intricate network of connections and mirrors to find the host of files isn’t straightforward.
Cisco also underlines that IPFS is generally used by legitimate service providers, so most of the activity taking place in IPFS networks is innocuous, helping threat actors bypass security checks more easily.
Abuse Examples
According to Cisco, IPFS is currently leveraged to host various phishing kits that threat actors can use to easily generate credential-stealing pages, host them on IPFS, and access the pilfers via a panel on a private address.
Abuse by malware actors is also widespread, with the most notable case concerning the Agent Tesla malware family, which is one of the most massively distributed RATs (remote access trojans) at the moment.
Cisco reports seeing IPFS gateways used for retrieving Agent Tesla to the victims’ systems within the context of a standard malspam infection chain.
“In another example, we observed a variety of malware payloads being uploaded to public sample repositories over a period of several months,” explains Cisco.
“In all three clusters, the initial payload functioned as a loader and operated similarly, however, the final payload hosted on the IPFS network was different in each cluster.”
The final payloads of these cases are reverse shell payloads, batch-based data wipers, and Python-based information stealers like the ‘Hannabi Grabber’.
In all of the cases Cisco’s analysts saw, the payload was fetched in base64 encoded form and broken into code blobs assembled on the victim’s computer.
An August 2022 report by Cisco also presented a fully-fledged “C2aaS” (command and control as a service) platform named ‘Dark Utilities‘, which leveraged IPFS for hosting the payloads, promising its “clients” ultimate resilience.
Threat Landscape Changing
Malware using IPFS isn’t a new thing, but Cisco reports the situation is now getting out of control as more threat actors realize the benefits outweigh the complexities that arise from maintaining content on a constantly shifting network.
At this time, IPFS isn’t getting the attention it deserves from defenders and security analysts, creating an opportunity for malicious actors to use the protocol to fly under the radar.
Cisco expects the abuse to continue and gradually grow in volume until additional detection and security layers are implemented to stop threats originating from IPFS networks.

 Beware of These Privacy Risks Before Migrating to Mastodon
Beware of These Privacy Risks Before Migrating to Mastodon
Hi RP,
The Medibank Private data breach in Australia has progressed as you maybe aware.
We don’t have the large population of some countries, but it looks like they got the medical data of two fifths of us that being ~10 million persons affected.
It is reported that the ransom has been refused and that the data is being dumped, though it sounds this is being staged. My policy is ‘if you don’t have a good reason to be on the dark web, then don’t go there.’ Does RP have any idea on what is occurring?
Does RP have a view on whether ransoms should be paid? There are a range of perspectives on this…
For medical data, I get the ‘sensitive’ nature of this and how concerning this maybe for many people. I don’t understand how this is being monetaried.
I get the potential for black mail / extortion (very nasty and harmful stuff). The only way I can make sence of the very high sale value of this data is that if these victims have already been targeted, either because they are a public person or have especially sensitive medical issues. It doesn’t make sense to me that all victims data would be of the same value or could be charged at that premium value. To charge that value, to my mind, it would have to be targeted.
I am pretty forgiving, but anyone who engages or facilitates this activity, well I am not going to speak the words. It takes a special form of nastiness extort people that way – they can enter the after world with Putin.
I don’t understand how medical data facilitates fraud, in my jurisdiction you don’t have to supply medical information for financial purposes. This doesn’t advise me of the high prices for medical information.
I have heard that exposed data could be used for obtaining fake prescriptions, a source I thought authoritive. Where that is possible, I can easily see the potential for victims data to be monetarized. But I have only heard that from one source and can’t find any collaborating evidence. In this case, it would make sence to me that all person’s medical data would be of value on the black market.
So what is going on?
Hi BoBeX, I have not been following this situation very closely, but the cybersecurity researcher Troy Hunt (in Australia) has been analyzing the situation and sharing his thoughts on Twitter:
https://twitter.com/troyhunt/status/1590057262361776129
Thanks Sven,
“Overnight update on the Medibank dark web site that’s presently distributing the data. No surprises on the comments around dollars, but that line on abortions is sickening. To selectively single these individuals out and publish personal data is abhorrent.” -Troy Hunt
“As I’m seeing questions about where to find the data, some advice for folks asking: don’t seek it out. There will be scams, phishing and malware all masquerading as “the Medibank data”. Major disasters are always following by criminals trying to cash in” -Troy Hunt