
Hackers breached the widely used Android phone monitoring app “LetMeSpy,” and leaked a file containing the sensitive data of people who were spied upon, as well as those who operated it.
LetMeSpy is essentially a commercial spyware available from outside the Google Play app store, which people use to spy on their spouses, employees, children, and others. The app is advertised as a legitimate parental control tool, and its use terms warn that it is only legal to install it on devices whose users agreed to be monitored for safety reasons. Despite that, LetMeSpy’s website even offers instructions on how to hide the app’s icon on various Android models, which indicates that the vendor knows their product is used for covert spying.
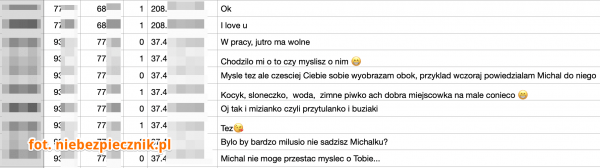
On June 21, 2023, the app’s publisher added a warning on LetMeSpy’s login page informing of a security incident that resulted in unauthorized access to some users’ data. The revelation about the scale of the data breach came on the same day from the Polish blog Niebezpiecznik, whose reporters reviewed the leaked data dump and warned that it contains the following:
- Over 26,000 email addresses of the tool’s “operators” along with their password hashes.
- Over 16,000 SMS contents, some containing passwords or codes for various services.
- Phone numbers of people in contact with the tracked people and phone numbers of people to whom the tracked people called (along with their designation from the victim’s contact book).
- SQL database dump containing more data, including 13,400 device locations.
niebezpiecznik
The above data concerns users in the United States, India, Western Africa, and other locations, and the oldest records date as far back as 2013.
Considering that LetMeSpy has previously claimed that it collects far more data than the above, it can be assumed that the data breach impacted parts of its systems, potentially an unsecured live database.
The operators of the app were irreversibly exposed for potentially illegal use against others, but unfortunately, the damage is double for people who were spied upon by LetMeSpy, as they are now exposed to the broader cybercrime community without even knowing about it. Mitigating this exposure now is hard, so the next best thing is to learn about it and take extra precautions against potential phishing and social engineering attacks.
LetMeSpy installs on Android devices under the name “LMS,” requesting permission to access call logs, the contacts list, location, and SMS. You can check your device for the app’s presence on the app drawer or through the settings menu under the “App” category. Additionally, activate Google Play Protect if switched off, which should be enough to detect and stop the spying activity. If you belong to a high-risk category that is more likely to be targeted by spyware, installing a mobile antivirus from a reputable vendor on your Android phone would be a good idea.
LetMeSpy has so far remained silent about the security incident and posted no relevant press releases or announcements on the mishap.

 Belgian Telecom Firm Accused of Collecting Data of Billions
Belgian Telecom Firm Accused of Collecting Data of Billions
Leave a Reply