
Multiple reports from cybersecurity analysts warn about the re-emergence of DarkGate, a potent malware that targets people’s data.
DarkGate has been under development since 2017 and was first spotted in the wild in 2018. However, its operators have maintained a low profile all these years, using the tool privately and targeting only a few users.
As first reported by ZeroFox at the start of the summer, someone claiming to be its original author began renting it to a limited number of cybercriminals in May 2023 for a cost of $100,000/year, $15,000/month, or $1,000/day.
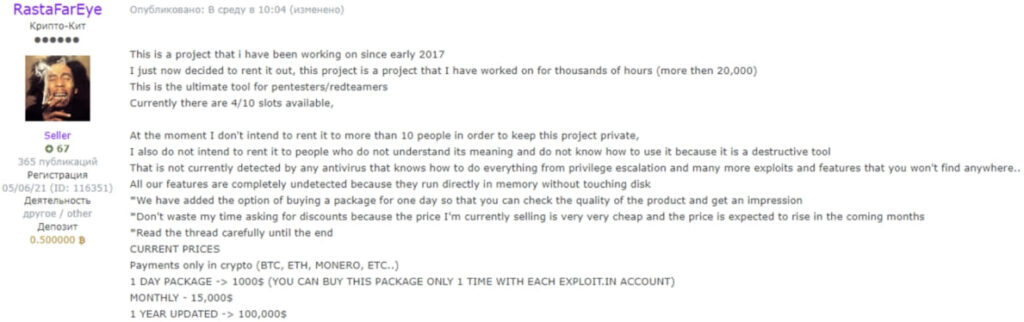
Zerofox
Malwarebytes today reports that it observed a new DarkGake campaign that started in July 2023. The campaign promotes the malware via malvertising and SEO poisoning that pushes payloads in the form of MSI installer files pretending to be network scanning tools. To evade detection by Google’s crawlers, the URL shown in the Google Search results redirects to a decoy page from where victims download the malicious payload.
The malvertising and SEO-poisoned domains used for malware dissemination in the recent campaign include the following URLs:
- top[.]advscan[.]com
- advanced-ips-scanne[.]com
- a4scan[.]com
- advanced-ip-scanne[.]com
- advancedscanner[.]link
- ipadvancedscanner[.]com
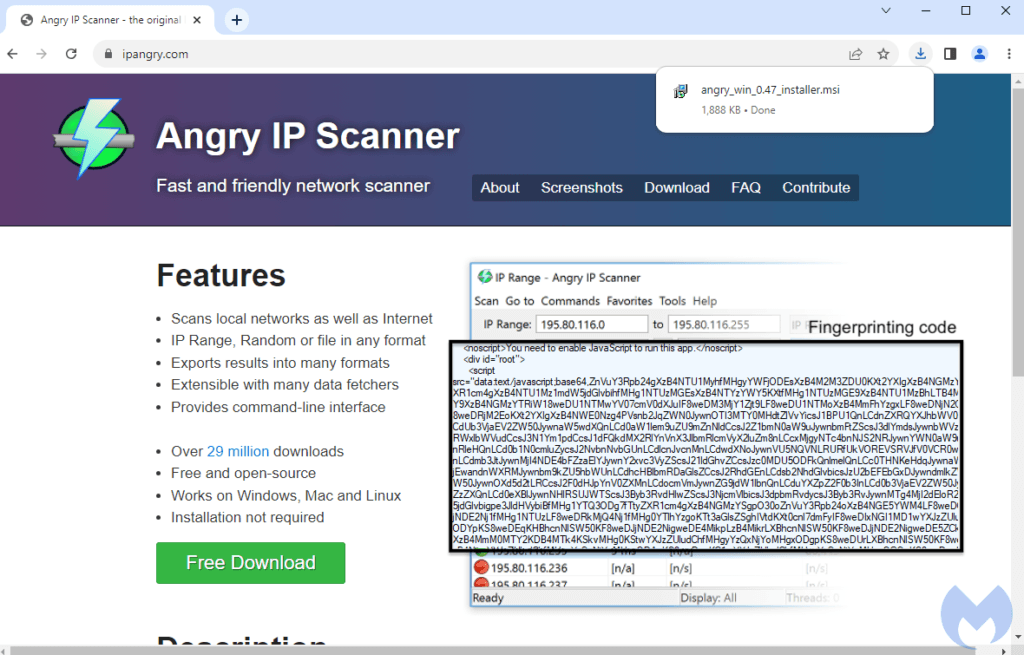
Malwarebytes
Of course, the threat actors can register and use new domains for DarkGate distribution at any time, while Malwarebytes also reports that they already diversify their delivery methods by using malspam. An independent malware analyst spotted this phishing-based campaign at the start of August 2023 and noted that it’s widespread despite being heavily geofenced.
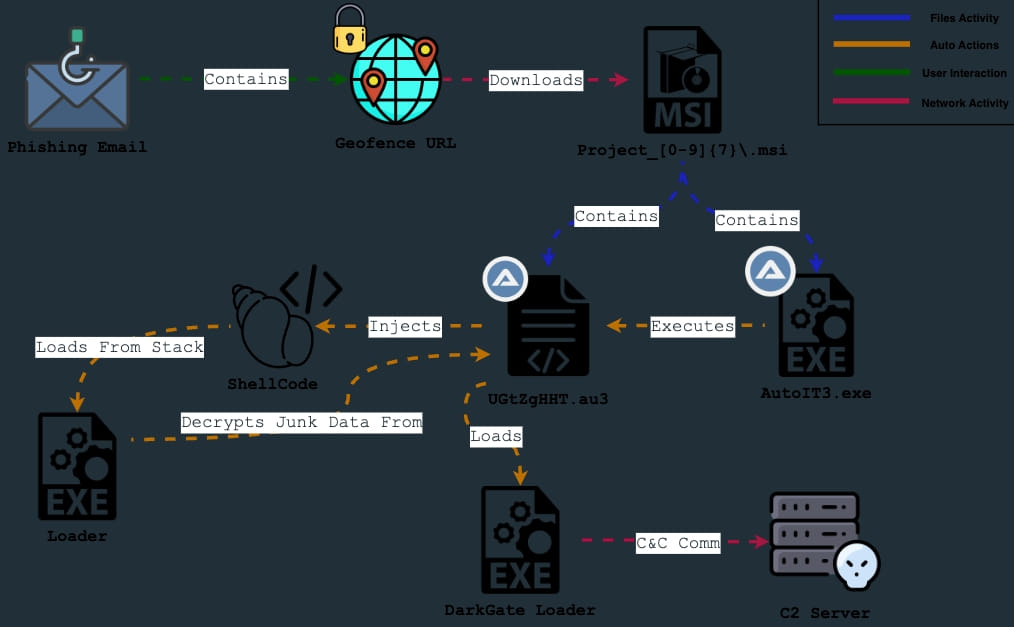
0xToxin
DarkGate capabilities
Due to its high cost and exclusive use within small, private circles, DarkGate has remained elusive to security researchers and never really posed a threat to the general public. Yet, the few who have crossed paths with this malware faced a highly formidable tool capable of evading most antivirus engines. DarkGate evades AV detection by arriving on systems in packaged (wrapped) form, using base64-encoding for string obfuscation and loading straight onto memory without ever touching the disk.
A recent analysis by AON researcher Stroz Friedberg highlights the following DarkGate capabilities:
- hVNC (Hidden Virtual Network Computer) access
- Cryptomining
- Information Stealing
- Reverse Shell functionality
- Keylogging
The researcher also explains that the recorded keystrokes, clipboard data, and process information are AES encrypted before they are sent to the attacker’s command and control (C2) server, which is a method to evade detection from network traffic monitoring tools. It’s also worth noting that the malware can elevate privileges on compromised machines to execute code without restrictions and can persist between system reboots thanks to its persistence mechanisms.
Although DarkGate isn’t opening up to the broader cybercrime community, even renting to a small circle of knowledgeable hackers has had notable results and a noticeable uptick in “in-the-wild” activity to guarantee multiple reports. It is unclear why DarkGate’s author has decided to rent the malware to others and whether they plan to expand the renting scope to include more, but it is already clear that internet users should keep an eye out for this threat.
When searching for software on Google, skip promoted results as abuse of Google Ads has been well-documented. If unsure about a software project’s official URL, use their verified social media channels or check the project’s Wikipedia page. Many open-source software projects are hosted on repositories like GitHub or SourceForge. Finally, saving frequently used trustworthy software sources as bookmarks is preferable to searching them every time.

 Discord Inc. Discloses Limited-Scope Internal Data Breach
Discord Inc. Discloses Limited-Scope Internal Data Breach
Thank you for such regular updates. I appreciate the work you and Svenn do.