
Internet connections using the OpenVPN protocol can be easily identified by using DPI (Deep Packet Inspection) technologies and blocked with minor collateral damage.
This result was presented in a technical paper published earlier this month by a team of researchers in the United States. The team performed a large-scale study involving a million users, demonstrating that it was possible to identify 85% of the existing OpenVPN traffic while having negligible false positives.
OpenVPN is a versatile and widely used VPN (Virtual Private Network) protocol released in 2001 as an open-source project. It offers strong encryption, a variety of authentication methods, and superior cross-platform compatibility. While its speeds are not up to par with more modern protocols like WireGuard, it remains a solid option available in most modern VPN software. See our guide on VPN protocols for an in-depth comparison.
Finding OpenVPN users
The study unveils that despite OpenVPN’s popularity for its robust security features, it’s not immune to detection and blocking by governments and ISPs (Internet Service Providers).
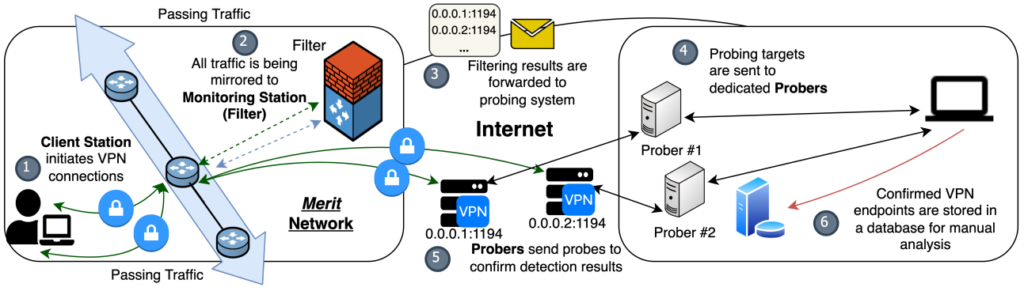
The research team first identified OpenVPN connections using three fingerprints based on protocol features like byte patterns, packet sizes, and server responses. They then employed a strategic two-phase attack, starting with passive fingerprinting to spot potential OpenVPN flows. This was followed by active probing, confirming the VPN’s presence by eliciting protocol-specific server responses.
arxiv.org
Collaborating with Merit, a regional ISP that provided secured access to the traffic data of one million users, the researchers set their framework into motion, finding that they could pinpoint OpenVPN connections with an accuracy of 85%.
arxiv.org
The study’s findings should be a wake-up call for both commercial VPN providers and VPN users, especially those in regions with stringent censorship, such as when using a VPN in China with the “Great Firewall” blocking many users. It is clear that the current obfuscation mechanisms and fingerprinting countermeasures used in the industry could be upgraded, particularly if they are being consistently blocked in Regions such as China and Russia. That said, we still see some VPNs working in these regions and bypassing censorship efforts.
The published technical paper proposes various short-term defenses, such as varying packet sizes and introducing noise in the data traffic to complicate fingerprinting efforts. However, the ultimate solution lies in the evolution of VPN protocols themselves, as the ever-advancing DPI technologies make the situation very challenging for older aging like OpenVPN.
Last summer, Russia started experimenting with protocol-based blocks in the country, targeting OpenVPN in Moscow and IKEv2 and WireGuard in other regions. This shows that ISPs can potentially identify VPN traffic if they fine-tune their methods against specific protocols, and unfortunately for OpenVPN, independent research has confirmed it.

 Employer Review Site Glassdoor Deanonymized Users Without Consent
Employer Review Site Glassdoor Deanonymized Users Without Consent
My local Costco (perhaps many have heard of this big box warehouse store) has Wi-Fi but it blocks VPN access regardless of the protocols used. I have NordVPN and ofuscated protocols and servers do nothing here. As usual, NordVPN tech support blames my iPhone and Android, not them.
Are ofuscated protocols concerned too?
It all depends on your needs. If you’re using an obfuscated protocol, and it’s working to bypass blocks/censorship efforts then you’re good to go. There are lots of ways to do obfuscation, and the results vary. If you can successfully use your VPN, then you should be good. The detection and blocking issues arise in countries like China and Russia.