
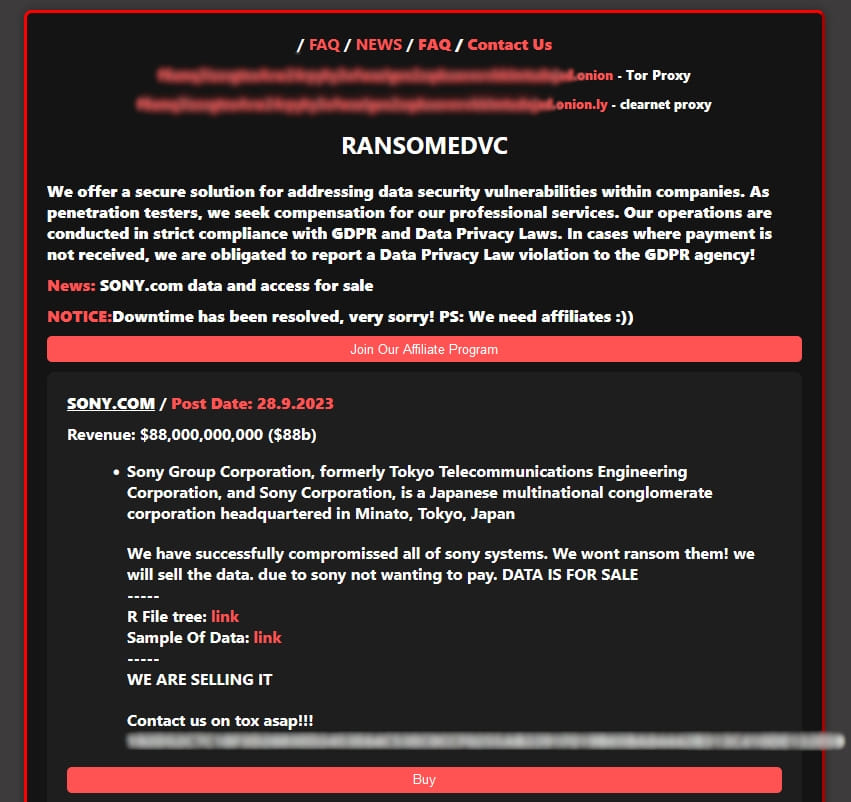
The emerging ransomware group RansomedVC has claimed an attack against Sony Corporation, offering to sell the data they claim to have stolen from the Japanese technology giant.
The threat actors have also shared the tree structure of the accessed databases as proof of the breach onto Sony’s systems, as well as samples of access on dashboards, source code, account panels, PowerPoint presentations used internally, and more. RestorePrivacy has examined the samples, and while they look authentic, we have no way to confirm they’re the genuine products of a breach on Sony.
RestorePrivacy
“We have successfully compromised all of Sony’s systems,” reads the announcement on RansomedVC’s extortion site.
“We won’t ransom them! We will sell the data. Due to Sony not wanting to pay, the data is for sale.”
This statement indicates that the company did not respond to the attackers or did not accept to enter any negotiation rounds, assuming that the claims about the attack are valid.
The threat actors offer to sell access not only to the stolen data but also to Sony’s systems. Interested buyers are urged to contact RansomedVC on a given Tox address (P2P, end-to-end encrypted instant messenger).
RestorePrivacy
It is important to note that the Cl0p ransomware gang included Sony in its extensive list of MOVEit victims in June 2023. However, Sony never admitted nor disputed the allegation, showing no interest in engaging with the attackers or handling rumors that hit the press.
If Cl0p really breached Sony recently, it wouldn’t be far-fetched to suggest that RansomedVC might have bought the stolen data and now attempts to resell it on the dark web or simply uses it as a means to boost its reputation. Still, this is merely speculation at this point, as neither attack has been officially confirmed.
In an email to RestorePrivacy, a Sony spokesperson stated that they are investigating the situation and have no further comment.

 Zero-day Vulnerability in Ubiquitous Lib Puts Millions at Risk
Zero-day Vulnerability in Ubiquitous Lib Puts Millions at Risk
Leave a Reply