
Raspberry Robin has been using custom exploits for at least two 1-day local privileged escalation (LPE) flaws in Windows.
Raspberry Robin is a notorious globally spread worm in circulation since at least 2021, targeting primarily Windows computers. The malware serves as an initial access broker for cybercriminals or other malware payloads. It has been associated with crime groups such as EvilCorp and TA505, who have used the malware to deploy ransomware, banking trojans, and other types of payloads.
Check Point Research reports that Raspberry Robin has been exploiting 1-days recently, highlighting the advanced attack capabilities of the malware’s authors and the constant development work that goes into keeping the tool relevant in the cybercrime space.
In addition, the researchers highlight various stealth and evasion enhancements seen in recent versions of the worm, as well as new delivery methods that diversify the malicious operation and make detection even more challenging.
In the past, Raspberry Robin was observed using distribution methods including but not limited to USB drives and network shares. More recently, it has adapted to use other vectors, such as malicious links or files distributed through communication platforms like Discord.
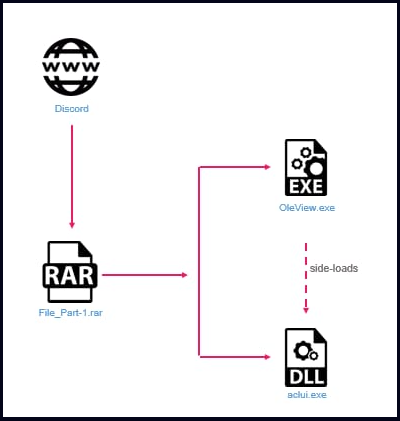
Check Point
Exploiting 1-days
1-day exploits refer to exploits developed and used after a vulnerability has been publicly disclosed but before a patch is widely deployed or applied. The window of opportunity for cybercriminals to take advantage of the gap between the flaw’s disclosure (and release of a patch) and the widespread application of the fixes is small and requires a high level of technical knowledge to take advantage of.
Check Point has observed Raspberry Robin doing precisely that, targeting two Windows flaws that were made known to the public, but before proof-of-concept exploits for them were made widely available. This demonstrates the malware’s capability to rapidly integrate new vulnerabilities into its arsenal, reducing the window of opportunity for defenders to respond and, at the same time, increasing its chances of successful infiltration and persistence within target networks.
The first flaw exploited by Raspberry Robin is CVE-2023-36802, a Type Confusion issue in Microsoft’s Streaming Service Proxy, allowing a local attacker to escalate privileges to SYSTEM. The exploit for CVE-2023-36802 was initially sold on Dark Web forums, indicating the worm’s operators either purchase exploits from third-party vendors or can develop them shortly after vulnerabilities are disclosed.
The second flaw attacked by the worm is CVE-2023-29360, an elevation of privilege problem in Microsoft Streaming Service. Raspberry Robin leveraged this flaw a month before the first exploit for it was posted on GitHub, making it widely available to researchers and cybercriminals alike.

Check Point
New evasion mechanisms
The developers of Raspberry Robin have continued to update the worm’s capabilities, including detection evasion, anti-analysis, and bypassing system protections. Check Point reports that the latest versions of the tool feature improvements and modifications in its communication methods and lateral movement modules to make it harder to detect based on known signatures and pattern analysis.
Moreover, the following systems have been added:
- API Hook Checks: Raspberry Robin checks for modifications in APIs like GetUserDefaultLangID and GetModuleHandleW early on to detect monitoring tools, comparing the first byte of these APIs to expected values to evade analysis.
- Process Termination: The malware terminates processes such as runlegacycplelevated.exe and runonce.exe to avoid detection and ensure its malicious activities can proceed with elevated privileges without raising alarms.
- NtTraceEvent Hooking: It patches the NtTraceEvent API to bypass Event Tracing for Windows (ETW), preventing the logging of its malicious activities.
- Shutdown Evasion: Implements methods to block system shutdowns through AbortSystemShutdownW or a window callback using ShutdownBlockReasonCreate, allowing uninterrupted operation.
- Remote Desktop Check: Determines if the system is under remote control by checking the GetSystemMetrics return value, querying registry values, and searching for indicators of remote desktop usage, adjusting its behavior to stay hidden.
- UWF Filter Driver Check: Searches for Unified Write Filter (UWF) filter drivers to identify systems protected against permanent changes, prompting it to clean up and reboot to escape environments where its persistence could be compromised.
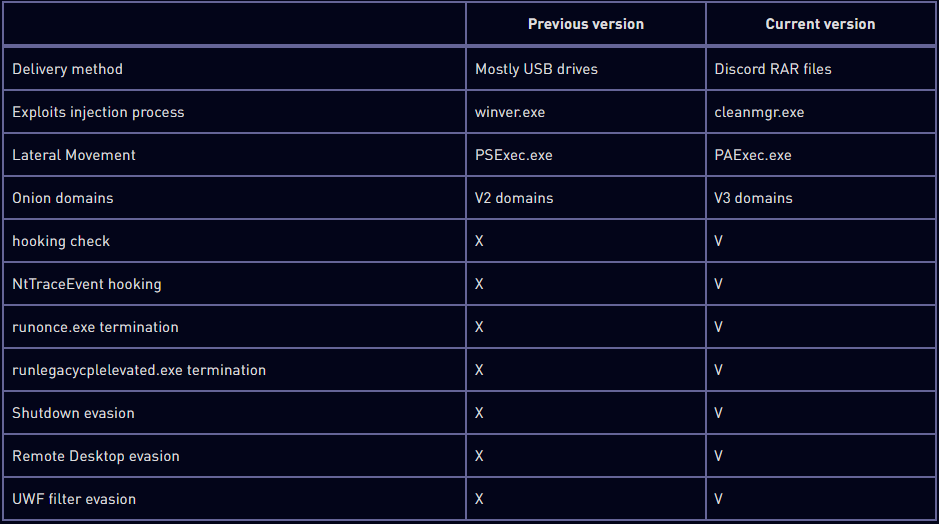
Check Point
To defend against Raspberry Robin, and any sophisticated malware for that matter, make sure to apply all available security updates for your OS and software, avoid downloads from shady sites, do not connect unknown USB drives on your critical systems, and turn off AutoRun features on Windows that can help prevent automatic execution of files from removable drives.

 Thousands of AnyDesk Accounts Offered for Sale Following Hack
Thousands of AnyDesk Accounts Offered for Sale Following Hack
Leave a Reply