
Researchers have identified a vulnerability that undermines location privacy for users of WhatsApp, Signal, and Threema. This report examines the researchers’ findings and offers potential solutions for mitigating the attack vector.
A team of researchers has found that it’s possible to infer the locations of users of popular instant messenger apps with an accuracy that surpasses 80% by launching a specially crafted timing attack.
The trick lies in measuring the time taken for the attacker to receive the message delivery status notification on a message sent to the target.
Because mobile internet networks and IM app server infrastructure have specific physical characteristics that result in standard signal pathways, these notifications have predictable delays based on the user’s position.
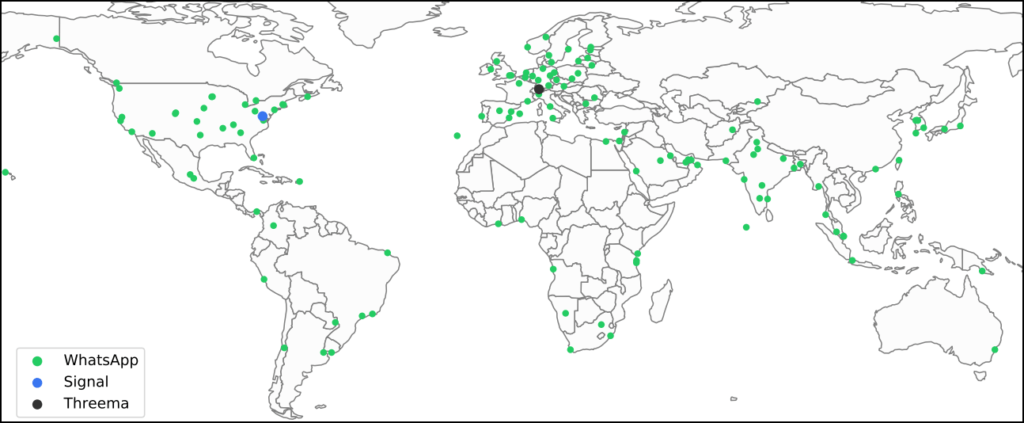
Source: Arxiv.org
By measuring these delays in a preparatory work stage, like sending messages when the target’s location is known, an attacker could figure out where the message recipient is located at any time in the future by simply sending them a new message and measuring the time taken for the delivery status notifications to arrive.
As the researchers analyzed in their technical paper, this timing attack could work well for locating the recipient’s country, city, district, and even if they are connected to WiFi or mobile internet.
If the attackers perform enough tests to formulate an extensive dataset against a target, they could infer their position among a set of given possible locations in a city, like “home”, “office”, “gym”, etc., based on nothing else but the delivery notification delay.
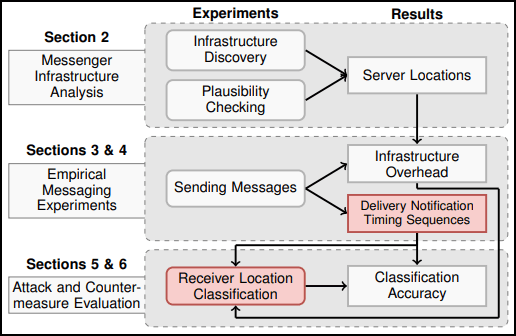
Source: Arxiv.org
These notifications are standard across many popular IM apps, and the researchers confirmed they are exploitable against even the most (generally) secure messenger services, like Signal and Threema, as well as WhatsApp.
Attack Details
For the timing attack to work, the adversary needs to use a smartphone for sending the messages and a packet capture application like Wireshark to analyze their own TCP traffic and extract the timing information.
The attacker and the victim must know each other and must have engaged in previous conversation on the IM app, which is a requirement for both the attack and the preparatory work.
The network traffic analysis can help the attacker determine which packets are the delivered status notifications. In the apps tested by the researchers, these packets either have predetermined sizes or have identifiable structure patterns.
Next, the attacker needs to classify the different locations and match them to measured “round-trip” times, and then attempt to correlate these pairs with the target’s location using the known data set.
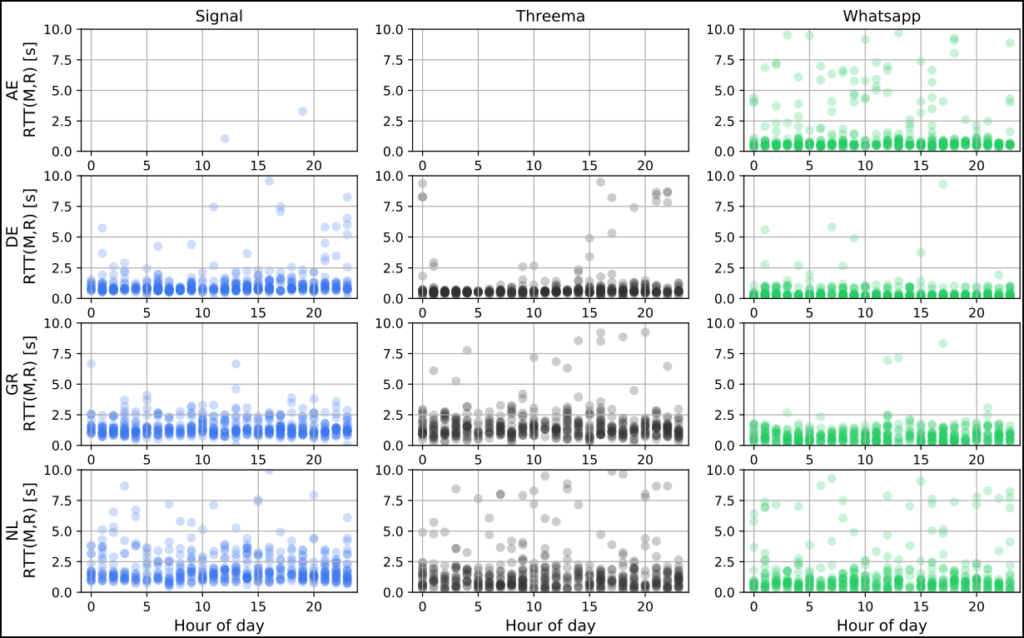
Source: Arxiv.org
The resulting classification accuracy based on the researchers’ experiments was:
- 82% for Signal targets
- 80% for Threema
- 72% for those using WhatsApp
Implications of this vulnerability
The implications of this attack are alarming from a user privacy perspective. These platforms, particularly Signal and Threema, promote themselves as secure and private messengers that go above and beyond the security of other platforms.
WhatsApp, the largest of these three messengers, has around 2 billion users based on some estimates. Signal and Threema are much smaller, with around 40 million and 10 million users, respectively.
While billions of people around the world rely on these messengers for secure and encrypted communications, these findings show us that user location privacy remains vulnerable to attack. However, we do identify some potential solutions.
What to do about it
While performing the experiments, the researchers noticed that some devices were idling while receiving the messages, which can mess up the attack results and is practically an unreliable countermeasure.
A solid way for app developers to deal with this problem is to introduce a system that would randomize the delivery confirmation times to the sender.
Anything from 1 to 20 seconds would be enough to render this timing attack impossible to carry out while not hurting the practical usefulness of the delivery status notifications.
From the user’s perspective, if the app allows disabling the notification feature that informs the sender when the message was received, using this setting would deal with the problem decisively by removing the abused element.
Finally, users can also utilize a VPN (virtual private network) on mobile devices to increase latency and help obfuscate location data. For example, connecting to a VPN server that is not near one’s physical location should interfere with the timing of status notifications. Intermittently switching VPN server locations would further add variability to message timing. However, this assumes these messenger apps are not bypassing the VPN, but recent reports also illustrate vulnerabilities with Android VPNs.
RestorePrivacy has contacted all three messenger apps mentioned in the report. We will update this article with any comments and new information.
UPDATE 1: Two of the named messengers have told RestorePrivacy via email (on October 20th) that they are investigating the situation and will provide a comment on the report shortly.
UPDATE 2: Threema provided RestorePrivacy with the following statement on October 21st:
We have already considered different workarounds and conducted various tests, including ones where the client randomly delays delivery notifications slightly to render these kinds of timing analyses useless. (App updates containing this improvement should become available soon.)
– Threema GmbH
Please note, however, that the practical exploitability of these timing analyses is debatable: Users typically don’t have their messenger app open all the time, and push notifications that wake up the app in the background already add a considerable delay of up to several seconds.

 Everest Ransomware Group Leaks MultiCare Medical Data in Latest Data Breach
Everest Ransomware Group Leaks MultiCare Medical Data in Latest Data Breach
Could the same effects be applied to VPN to unmask VPN users? Even through chaining techniques?
No. VPNs do not have message status notifications that are unique to instant messengers.
Mobile messenger from XX Network [https://xx.network/messenger/] guards against these problems.
Download it from phone app store or (Android) load from app package. Open source.
yo quiero saber como localizar a un tipo que me ha estafado 3000€ como puedo saber donde se ubicar el estafador ?
Merci pour cette information
Anyone heard of XX Messenger from elixxir? Quantum secure messaging, open source, no metadata, link [https://elixxir.io/]
Even if one use the privacy friendly messengers, the main part is who else to communicate with if all use whatsapp or the other.
I assume Sessions is not here as it is an Onion?
Yes I’m wondering how this affects Session given that it’s a peer to peer ecosystem that is not centralized. From the review linked in this article:
“In an onion routing system, messages are surrounded by multiple layers of encryption and pass through multiple nodes in the system. Each node decrypts a layer of encryption before passing the message along. Because of the way the messages are encrypted, no node can know both the origin of the message and its destination. Additionally, your IP address is never visible at the destination, meaning whoever you are conversing with has no way to identify you when you use Session. The Session service should prove to be very resilient, and continue functioning even as individual Service Nodes join or leave the network.”
Based on this, I would assume that Session is not affected by this vulnerability, but they should confirm.
That’s what I thought.
Thanks.
Session should be safe with its routing system for messages. This is another reason to use Session over the others, it scores the best in privacy — my two cents!
Bernd,
Exactly,
I understand the Australia thing, but you can’t give what you don’t have and you don’t know what you can’t know.
Wish they would be ranked higher on this site than they are.
To me, they are the best.
I would really like to know if this affects Telegram.
Telegram doesn’t have message delivery feature, so it’s not susceptible to this attack.
signal just turn of delivery receipts problem solved. article says the attack can only happen from people you have chatted with not random people your not communicating with. signal you can also route threw there servers to hide IP also if needed.