
Network specialists warn about the rising popularity of “CNAME cloaking”, that big advertisers use to get past user-tracking restrictions and third-party cookie blockers by web browsers and extensions.
CNAME cloaking isn’t a new technique, but its effectiveness is becoming more potent despite the various approaches developers of anti-trackers have taken to tackle it, resulting in increased adoption rates by marketers.
Network security company Palo Alto Networks has created a CNAME cloaking scanner to gauge the extent of the problem and reports that a large percentage of new domains are using the anti-blocking technique.
Cookies and CNAME Cloaking
First-party cookies are generally considered essential for ensuring users’ stable and satisfactory browsing experience, so these are excluded from blocks.
Third-party cookies, on the other hand, are loaded from websites outside the domain visited by the users, and their goal is to track them for purposes of targeted advertising.
These third-party cookies are blocked either by comparing the origin resource of the cookies to the active domain or by using blocklists.
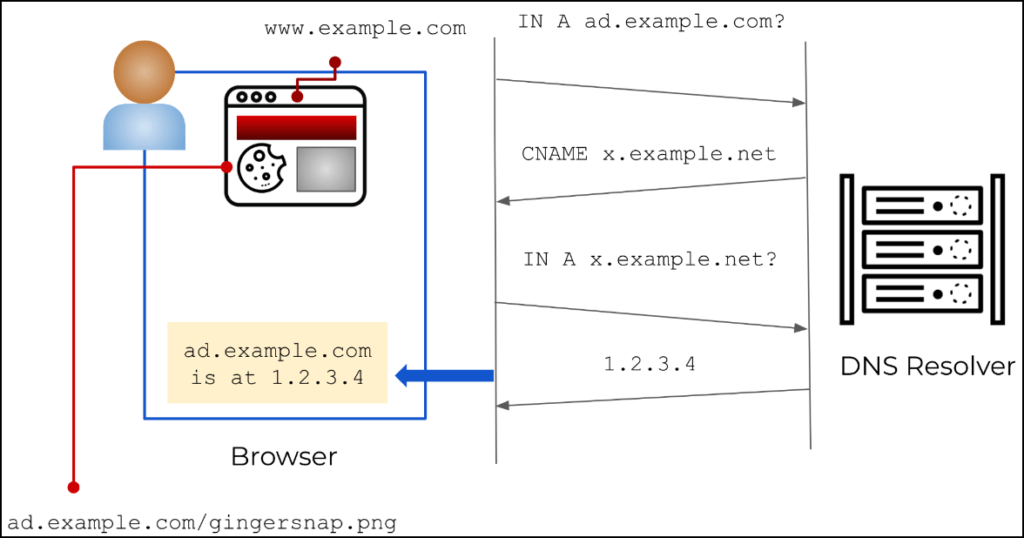
To bypass these blocks, CNAME cloaking uses DNS query-resolving pathways that aren’t scrutinized by the browser to make it appear as if the external resource is a subdomain of the website the user visits, and hence its cookies should be allowed.
Palo Alto Networks
The result is to allow advertisers to determine if a visitor is returning or new, assign unique IDs for persistent tracking across websites, retrieve browser information, measure the frequency of visits, and more.
While this is still not the same as allowing third-party cookies, it still will enable advertisers to funnel user data outside the site they visit, essentially breaching their privacy while they falsely assume they are protected from all third-party trackers.
The Scale of the Problem
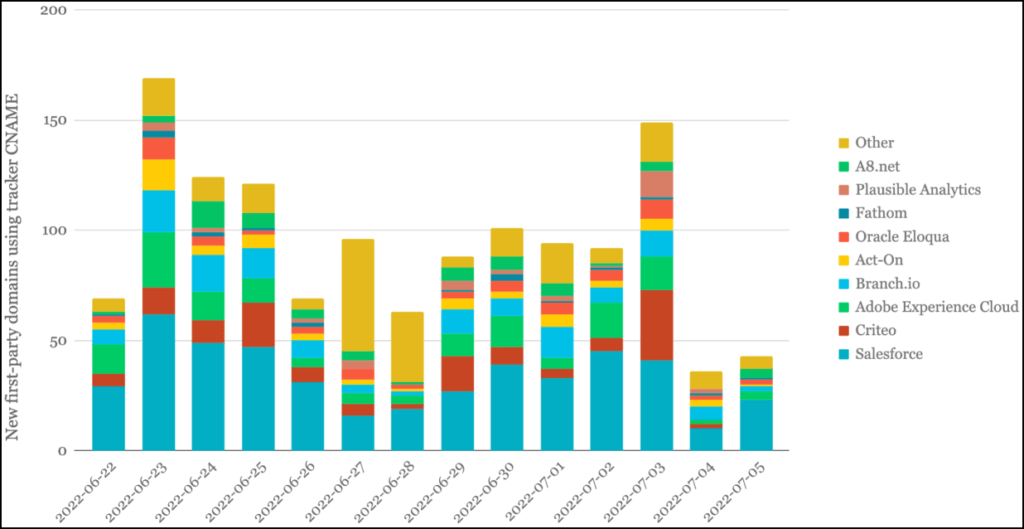
Palo Alto Networks reports that while running its CNAME cloaking scanner for a month, it detected 43,000 cloaked subdomains in 38,000 root domains, with most of them (98%) pointing to a single external resource.
Palo Alto Networks
The cloaked subdomains point to central domains belonging to just 32 organizations, generally advertising and marketing giants.
The report highlights that extensions using blocklists like Adguard and EasyPrivacy, only block roughly 10% of the subdomains the scanner detected, leaving users exposed to tracking in 90% of the cases.
One critical consequence of this practice is that first-party cookies, too, might leak sensitive data to cloaked domains, most commonly Google Analytics, Hotjar, Microsoft, and Dynatrace.
What can Users do
Users can feel more confident about the effectiveness of their tracker blockers by using tools that detect CNAME cloaking based on DNS lookups.
Palo Alto Networks provides the example of UBlock Origin on Firefox, where access to DNS APIs is open to extensions.
Brave browser also checks for CNAME cloaking using an embedded DNS resolver and blocks the request if one is detected.
Note: Brave and Firefox are the top recommendations in our secure browser guide.
Apple’s Safari also features bounce tracking detection to detect CNAME cloaking and block the trackers, and its developers are constantly improving it.
One thing to remember is that this is a “cat-and-mouse” game between advertisers and web browser developers, so using up-to-date software is key in fighting the phenomenon, or at least having the best chances.
As for VPNs, using a trustworthy product will help you against all forms of data collection by encrypting all data in transit, so even if CNAME cloaking won’t be blocked, the privacy breach effect will be negated.

 Timing Attacks on WhatsApp, Signal, and Threema can Reveal User Location
Timing Attacks on WhatsApp, Signal, and Threema can Reveal User Location
I need more information regarding CNAME cloaking and including how to effectively prevent it and whether Firefox Browsers block 3rd party cookie option prevents CNAME cloaking.
Also when using 3rd party DNS provider like NextDNS and Adguard DNS Private, does access to domains required for CNAME cloaking gets blocked?
Is Adguard Adblocker Software for PC effective against CNAME cloaking?
In my case on PC I use Cookie Auto delete addon on Firefox along with block all 3rd party cookies enabled. So all cookies are deleted except those which I whitelist and I also use Firefox containers for websites like Amazon and Outlook.
I also use Firefox on Android and whenever I quit the browser all cookies without exception gets deleted.l and all tabs gets closed. Firefox on both the platforms has the option to prevent against fingerprint tracking.
Also how effective is VPN againt CNAME cloaking? I am using Nord VPN.
Good questions and good practices Moon Cocoon! I was about to ask the same about https://adguard-dns.io/en/welcome.html (link is not my answer; I am asking for an interpretation of it)
I agree with the above. Great comment Moon Cocoon! My set up is similar to yours.
Can the article be read to say, if you are using a recommended browser (Brave/Firefox – I use both with Ublock Origin, Firefox is custom from the RP guide) and keeping them updated; and using a trusted VPN (Nord) that this is the best way to mitigate these buggers?
I also have my browsers set to delete all cookies on close (best balance of privacy and convenience for me). I imagine this would be a good strategy also?
As Sun Cocoon says this is not an answer just questions.
Read the full report, I would say. Just delete all cookies regularly (or manually select those you don’t use) and don’t allow third-party cookies. And yes, you will need to sign in and out of all used services because of it. You can experiment with several browsers, use disposable VM’s if you’re really paranoid, etc. Monitor your routers outgoing logs if you can use pfSense and their extension tools.
For Windows, users, well, either use customized builds or install scripts as far if they prevent things I’m not certain. But you know your operating system is already spying and reducing your privacy, so software can reduce it a bit, but you never know for sure. Same for Apple, Androids (most builds) etc.
For AdGuard, just apply extra CNAME cloaking lists. https://github.com/AdguardTeam/cname-trackers
But remember, not all those cloaked CNAME cookies are malicious, and blocking them can make websites unusable or have consequences.
As mentioned, Google Analytics and other big company analytics tools (Microsoft, Oracle, etc.) are the main culprit. Cookies related should be blocked should be blocked.
One consequence of using CNAME cloaking is that other first party cookies might automatically be sent to the cloaked FQDN. Unexpectedly, the most common cookies seen in requests to cloaked domains were not those set by the tracker involved in the cloaking, but those associated with Google Analytics (see Table 1).
“will help you against all forms of data by encrypting all data in transi..”
Correction: against all forms of data collection/harvesting……
Thanks, fixed.