
Last month we were the first to report on a breaking data security incident involving Twitter and a database compiled from 5.4 million accounts that was for sale on a cybercrime forum. Today, Twitter has formally acknowledged the security bug that caused this data breach.
Twitter has now officially acknowledged our “news report” that first broke the story about a threat actor leveraging a security vulnerability to acquire data from 5.4+ million accounts.
Last month, we spoke directly with the threat actor selling the data and we also analyzed the data sample that was being sold, confirming its legitimacy. (See the full report here.)
Today, Twitter is now acknowledging the security bug and the subsequent data breach that impacts “some accounts” — but the full number remains unknown.
Twitter goes on to explain in the report how anyone could acquire Twitter account associated with a given email or phone number.
As a result of the vulnerability, if someone submitted an email address or phone number to Twitter’s systems, Twitter’s systems would tell the person what Twitter account the submitted email addresses or phone number was associated with, if any. This bug resulted from an update to our code in June 2021.
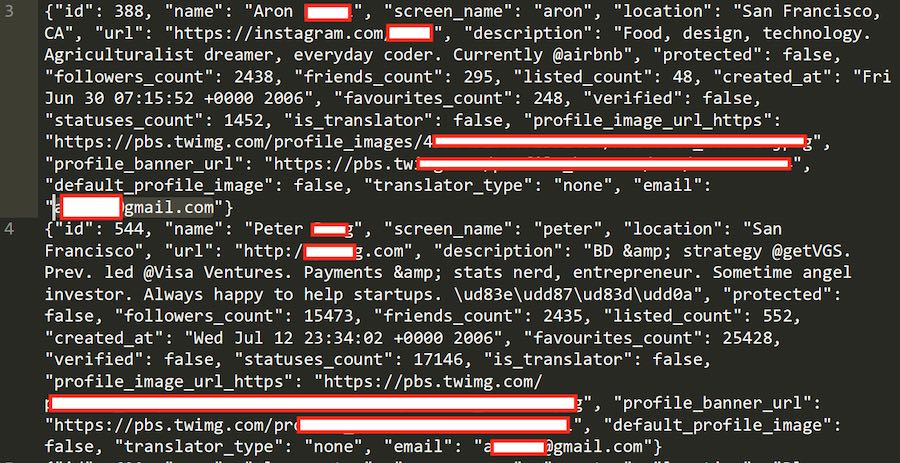
This vulnerability is what allowed a threat actor to compile a database of Twitter account data from over 5.4 million Twitter users. The data included the Twitter user’s account handle, phone and/or email, plus other scraped data.
Below is a redacted sample that we analyzed from the cybercrime forum where the full database was being sold for $30,000.
Unfortunately, the impact of this data breach is difficult to quantify.
Full impact of Twitter data breach remains unknown
Unfortunately, there is really no way to know how many Twitter users this vulnerability impacted.
The threat actor has since removed the listing on the cybercrime forum — and this suggests the database has been sold. Additionally, the sample from the database only contained 10 lines, out of 5.4 million.
There may have also been other databased compiled from this security vulnerability.
Twitter has also acknowledged that they are unable to quantify the scope of this breach:
We are publishing this update because we aren’t able to confirm every account that was potentially impacted, and are particularly mindful of people with pseudonymous accounts who can be targeted by state or other actors.
How this data breach affects Twitter users
This is a serious data security threat that exposes Twitter users to threat actors and cybercriminals.
As we reported last month, the exact number of accounts listed for sale in the database was 5,485,636 based on the seller’s information. However, there could be even more Twitter user’s affected by this breach — there is no way to know for sure at this time.
Particularly concerning is the fact that many people use pseudonymous accounts that could be exposed in this latest breach, as Twitter now admits.
This data could potentially de-anonymize Twitter users in the database and/or expose users to targeted phishing attempts.
Twitter is recommending people enable two-factor authentication to mitigate risks.
While no passwords were exposed, we encourage everyone who uses Twitter to enable 2-factor authentication using authentication apps or hardware security keys to protect your account from unauthorized logins.
Additionally, Twitter is also recommending that people not use a “publicly known phone number or email address” with their Twitter account.
To keep your identity as veiled as possible, we recommend not adding a publicly known phone number or email address to your Twitter account.
Let that one sink in.
Twitter is now saying you should be using a burner email or burner phone number with Twitter, not your real “publicly known” email or phone.
Don’t worry, we’ve got you covered. See our guide on burner email here.

 Verified Twitter Vulnerability Exposes Data from 5.4 Million Accounts
Verified Twitter Vulnerability Exposes Data from 5.4 Million Accounts
I had my twitter account for more than 16 years now.
Last week it was late and I was on twitter with my phone. There was a supposed “sensitive” tweet and then Twitter insisted I enter my birthdate and year of birth. My phone display is kind of small and I wasn’t wearing my glasses. I used the pull-down method (the only method) and I selected the wrong year of birth. Twitter then banned me saying I was under 13 years old.
Now, twitter says if I want access and regain my account I have to provide them government ID that matches my name et al when I signed up. I used a pseudo-name. Besides, there’s no way in hell I’m going to send them my personal government issued ID even though I had a legit phone number on file with them (not a good idea in retrospect).
I tried to plead my case to the twitter bots but they still locked me out. In fact, there’s no way to reach them either.
This goes to show you the extreme nature twitter can go: either far left or far right with security and more.
This is to be expected as Twitter’s former head of cybersecurity says: https://www.nbcnews.com/tech/tech-news/twitter-whistleblower-alleges-major-security-issues-rcna44361
Hi RPV,
A good read. Thanks for posting
Twitter is a terrible company based solely on trying to flag false and misleading content, or even having abusive and other supposed violations removed. It’s like the options that currently exist are just for show.
And what happened to all the comments before August 5? They have disappeared.
Hi Sven,
What you are doing is of great service to the community.
I have noticed other news outlets referencing your research, and so they should.
Only the experience of @April needs to be noted to see what a rough time these sorts of events can cause people.
I recommend your privacy and security guides.
Resources are available for affected people, for example in Australia you look to https://www.cyber.gov.au/
And if anyone wants an insider guide to what the nasty little buggers might do with your accounts:
https://darknetdiaries.com/episode/112/
Great reporting!
People need to know.
Regards,
BoBeX
Thank you for reporting on this. I hope you follow up. I was one of the people hacked…Twitter is doing NOTHING. NOTHING at all.
Meanwhile, we’re being contacted on WhatsApp with extortion offers in order to get our accounts back. A coworker of mine was hacked as well, they restored his account but the hackers now have his email account.
I’ve sent Twitter message after message and just get a form letter back.
It’s very frustrating and shitty.