
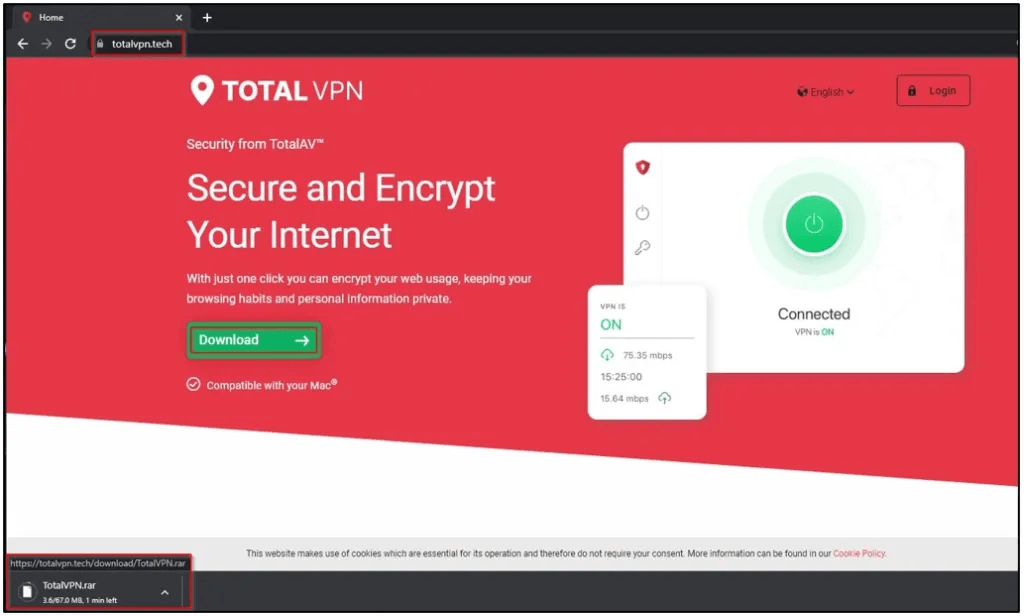
A new BbyStealer malware distribution campaign is underway, using various phishing domains to target users seeking to install Windows VPN applications.
The campaign was discovered by Cyble Research and Intelligence Labs, who have found multiple fake sites mimicking legitimate software vendor download pages that all feature a ‘free download’ button. Visitors who click on those buttons receive a RAR archive with a fake VPN installer that drops the BbyStealer info-stealer on the device.
The phishing domains used in this campaign, whose names also indicate which VPN products they spoof, are:
- totalvpn.tech
- wolfervpn.com
- vpncyberfortress.com
- vpnfortres.online
- itroppervpn.online
Cyble
These fake VPN sites may be promoted through malvertizing and Black SEO, which helps them rank high on search results for relevant search terms on Google. Additionally, traffic to these sites could be channeled through malicious social media posts, direct messages, and others.
Cyble reports that none of the current anti-virus engines flags the RAR files dropped from these sites as malicious. The same applies to the contained executables that install the BbyStealer, making it unlikely that the users will realize they received a dangerous file.
Cyble
BbyStealer risk
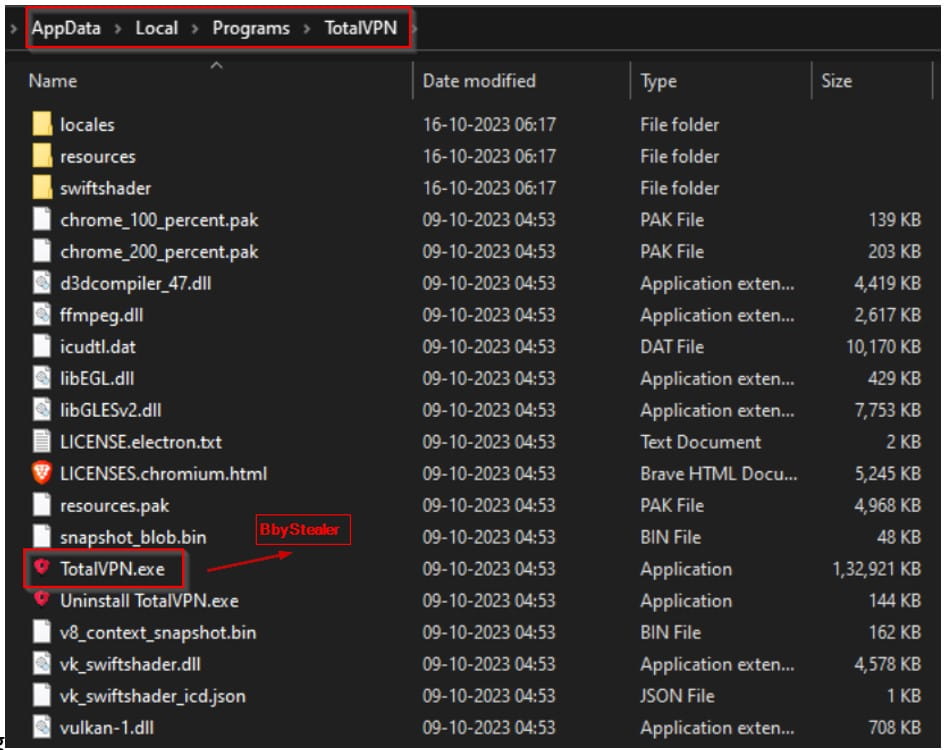
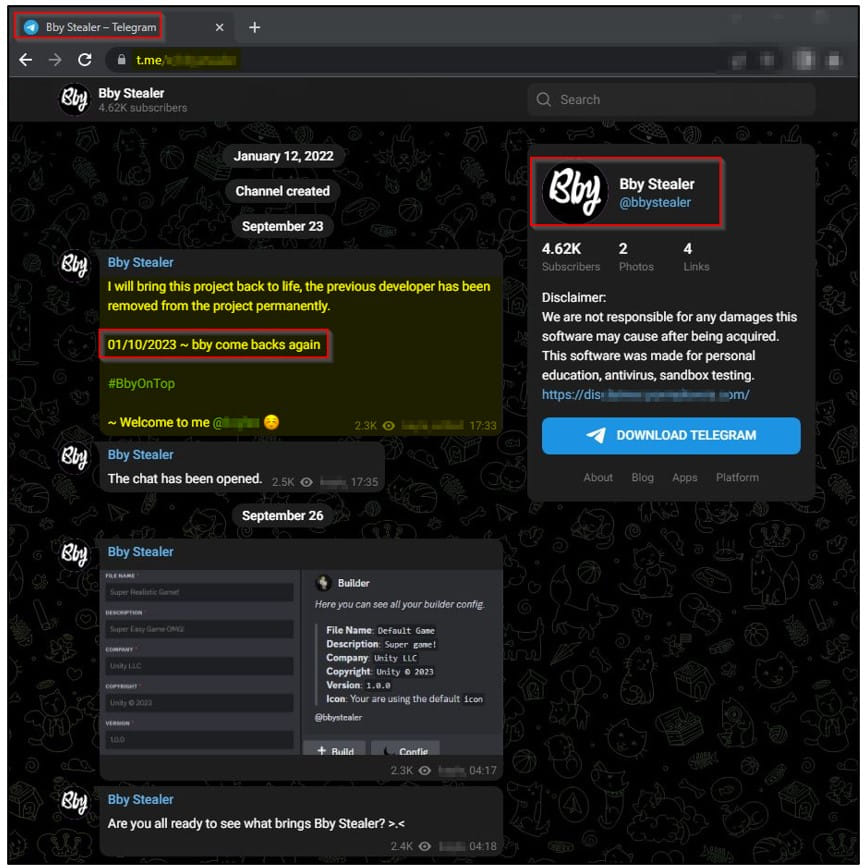
BbyStealer is a MaaS (malware-as-a-service) operation sold to cybercriminals via Telegram, where it counts over four thousand members. The particular family was first spotted in the wild last year and continues to be actively developed, with code optimizations and new features added periodically to make the proposal more alluring to interested buyers.
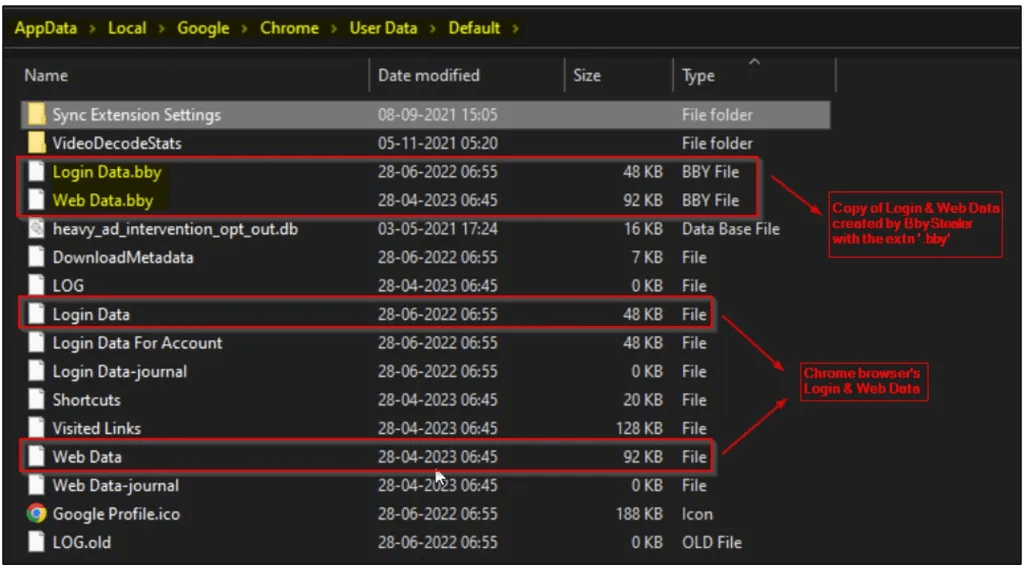
Upon launching the downloaded executable, the malware adds an entry in the Windows Start-up folder for persistence and executes commands to terminate running web browser processes. This frees up data stored in the browser’s database, such as account passwords, credit cards, cookies, and cryptocurrency wallet information (balance, transactions, addresses), for the malware to access and steal.
Cyble
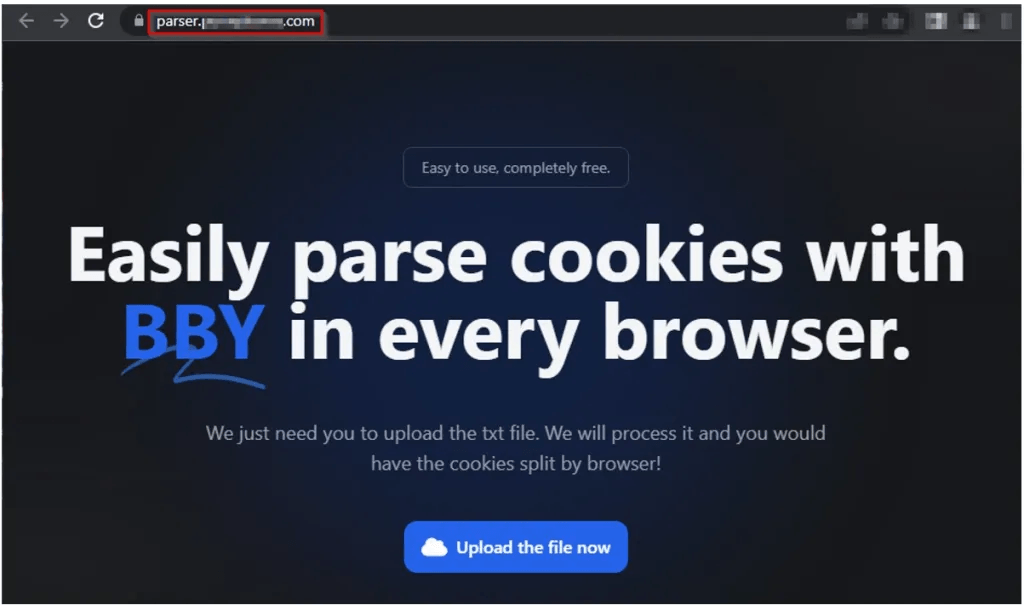
The BbyStealer platform also provides the cybercriminals using its malware a cookie parser. The malware operators can upload text files that hold the exfiltrated data from victimized systems, and the parser will identify and split usable cookies.
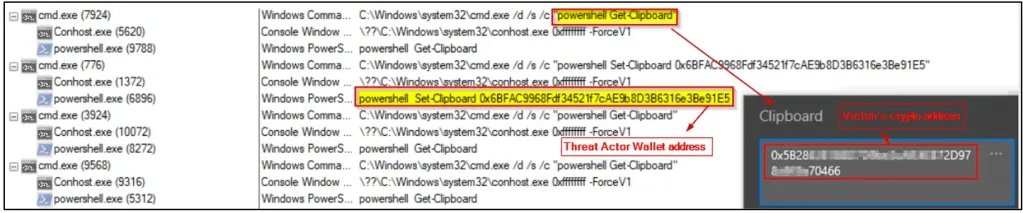
Additionally, BbyStealer features a clipper module, which monitors the system’s clipboard for copied cryptocurrency wallet addresses and swaps them with one set by the attacker to divert payments to them. The clipper supports 12 cryptocurrencies, including Bitcoin, Ethereum, Litcoin, Monero, Solana, Dash, and Dogecoin.
Cyble
VPN users under fire
This is not the first time cybercriminals have launched a malvertizing campaign themed after VPN apps. These tools are far too popular not to draw the attention of malware operators, so VPN users need to maintain an elevated level of heed.
Previously, we reported about a similar campaign impersonating the massively popular ExpressVPN brand to push RedLine info-stealer to users. In another case, we saw fake LetsVPN sites dropping banking trojans, keyloggers, and adware.
Users are recommended to upgrade their clients from within the apps instead of downloading new installers to avoid this risk. If you’re installing a VPN on a computer for the first time, skip promoted results on Google Search or use an ad-blocker that will automatically hide them.

 Signal Denies Existence of Zero-Day Vulnerability on the App
Signal Denies Existence of Zero-Day Vulnerability on the App
Leave a Reply