
Researchers have discovered two vulnerabilities in Signal for desktop that could allow local attackers to access attachments sent by the user in the past or replace the files with poisoned clones.
The flaws are present on all Signal clients for desktop, including Windows, Linux, and macOS, since they all share the same codebase, and all versions up to the most recent, v6.2.0.
Flaw Details
The vulnerabilities, tracked as CVE-2023-24068 and CVE-2023-24069, were discovered by independent security researcher John Jackson, who laid out the process of finding them in a blog on his site.
Signal stores message attachments in unencrypted form in an unprotected directory on the computer, giving them a random alphanumeric name and an extension not associated with any software.
However, an attacker with local access to the device, either through physical access or after infecting the target with malware, could modify the extension to make it possible to open them with the proper application. For example, image files can be retrieved by adding the PNG extension, documents can be retrieved with PDF or DOC, etc.
Jackson also discovered that if the user wipes them from within the Signal client, it’s still possible to retrieve them and make them reappear in the said directory by replying to the attachment message.
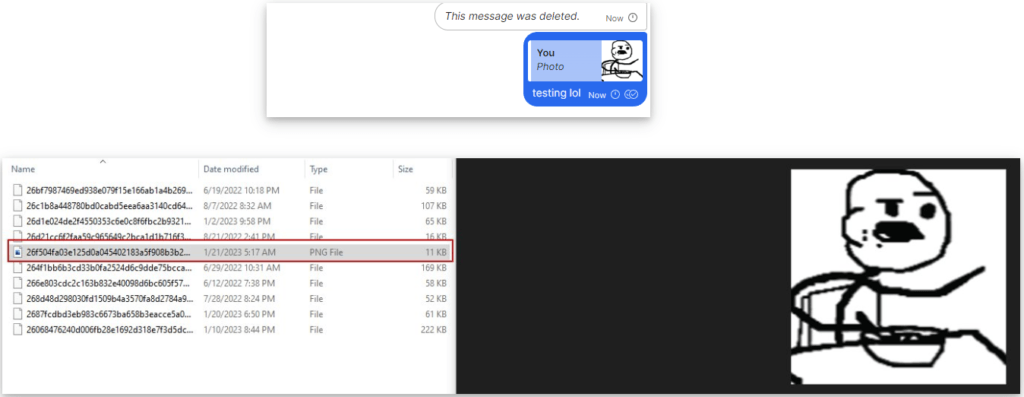
johnjhacking.com
This vulnerability received the identifier CVE-2023-24069 and does not have a severity rating yet.
The second flaw, tracked as CVE-2023-24068, concerns a lack of a validation mechanism in Signal desktop, which makes it impossible for users to determine if the locally stored attachments have been tampered with.
Theoretically, a local attacker could poison the files and wait for the victim to forward them to their peers, infecting them with malware/spyware.
The exploitation of the second flaw is more complicated and depends on several prerequisites, but it wouldn’t be unrealistic in certain settings where the victim frequently shares files with their colleagues.
Signal’s Response
Signal has rejected the importance of Jackson’s findings and disputed the assignment of the associated CVE-IDs on the CVE Program.
The president of Signal, Meredith Whittaker, stated on Twitter that it’s not within the software’s scope to protect users from such a level of compromise, where attackers have local access to the target systems.
Hence, it can be concluded that the developers of the secure instant messenger app do not plan to introduce additional security mechanisms to validate attachments or purge locally stored files properly.
If you’re overly worried about the exploitation scenarios described above, you may simply stick to the mobile version of Signal, which isn’t impacted by the newly discovered flaws.

 New ‘Album Stealer’ Attack Tricks Facebook Users Into Installing Malware
New ‘Album Stealer’ Attack Tricks Facebook Users Into Installing Malware
https://mullvad.net/en/blog/2023/2/1/eu-chat-control-law-will-ban-open-source-operating-systems/
How come Bronco has the privilege of posting links? Come on. Sven. Stop with the preferential treatment.
Signal does not, has never had, and has never planned to have on-device encryption. ‘Vulnerability’ 1 is a natural result of this that should be well known to anyone familiar enough with Signal. Hopefully, this adds pressure to Marlinspike et. al. to add support for this, but they seem pretty fixed on the current idea.
Vulnerability 2 is interesting, but surely a hacker with that level of access to the system could just send their own malicious image, no need for the user to forward one.
Thank you for pointing out the hypocrisy within these “privacy service providers” Instead of thanking someone for finding a flaw and wanting to work to address. “Just use mobile…” A complete cop out and slap in the face.
This isn’t Signal’s position, it’s Restore Privacy’s position. Actually, it won’t help you as vulnerability 1 is a well-known part of Signal’s design philosophy that affects mobile as well.
Seriously….why would anyone who has a sound and rational mind [continue] or sign up to use Signal given their current mindset? What makes you believe we can trust them in any form?
All these “free” services: Telegram, Signal, etc. are really not free. We should be skeptical and suspicious they’re not seeing our information or selling our private info.
The first reg flag (like with Telegram and ChatGPT) is they insist on a valid non VOIP including banning Google Voice numbers preventing you from signing up. Even WhatsApp allows VOIP numbers. Ditto with WeChat.
This all should be investigated. It’s privacy related, isn’t it? We shouldn’t have to wait for a breach or incident to read up on it on Restore Privacy.
In the meantime, telling yourself that “you have nothing to hide” is an ignorant mindset. These privacy issues have nothing to do with the content you share. It has everything to do with selling your information and your mobile number, so marketers and bots can target you. Make sense?
Why would we not?!
Chat isn’t about “being total anonymous”, it’s about confort as well. No one will ever use a no-name chat service if it is not easy to use, and having a phone number attached to the account is the easiest way to know who else in your contact list uses the app.
It’s naive to think that someone is going to talk to every person in his/her contact list “in-person” to share a key to be able to talk via certain chat, or even send the credential on an encrypted tunnel.
To Dude: thank you for proving you don’t have a rationale or sensible mind.