
Update: Atlas VPN released a security patch for the Linux client shortly after this story broke. The latest Linux update is not susceptible to this vulnerability.
An anonymous user has leaked a zero-day vulnerability on Reddit that can force-disconnect the Linux client of Atlas VPN and reveal the user’s actual IP address.
Atlas VPN is a budget VPN service with a good set of everyday-use features, albeit limited by a small server network and the fact that it is based in a “Five Eyes” country (United States), making it susceptible to data scrutiny from the authorities. To learn more about the product and its strengths and weaknesses, read our full review.
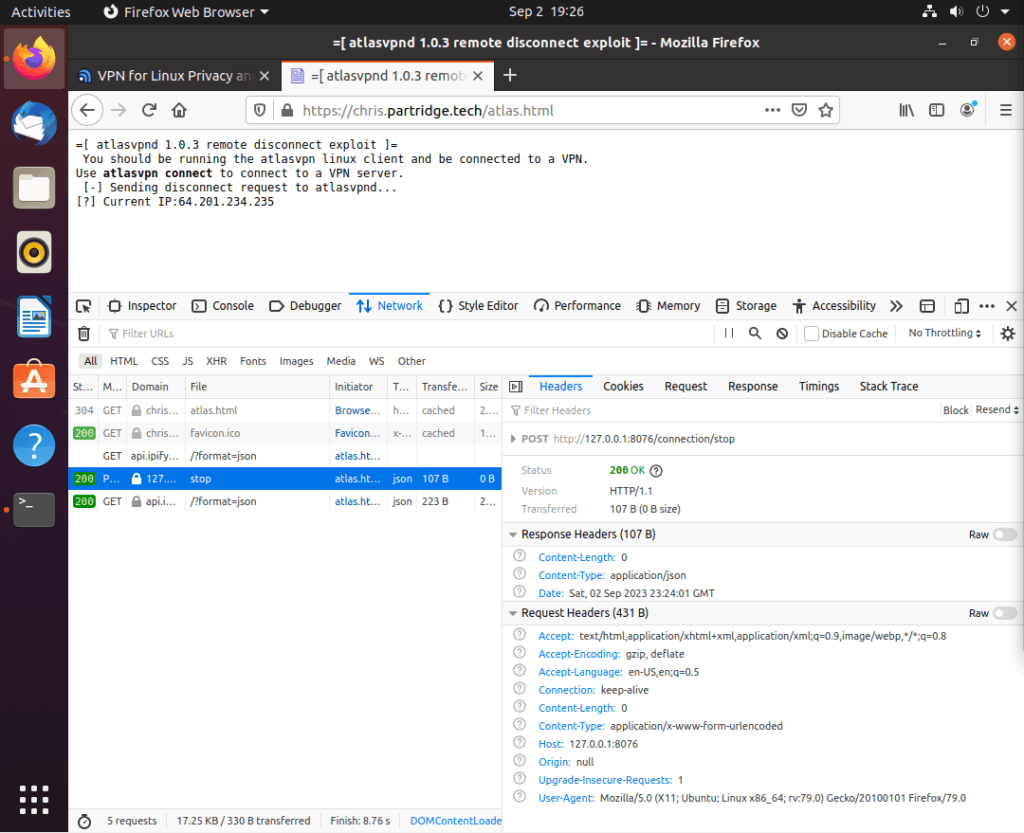
The Reddit user has posted a code snippet that can be uploaded to any web server, and if the target (Atlas VPN user) visits the website and their browser runs the code, the vulnerability is triggered.
The anonymous researcher said there are no reports of the disclosed method being used in the wild, but since the disclosure of the exploit code, this could change swiftly. The fact that this vulnerability is a zero-day means that Atlas VPN has not addressed the security problem, and hackers or anyone with malicious intentions can readily exploit it.
The researcher has provided a short explanation about the root cause of the vulnerability, which is a lack of authentication on the API exposed on the user’s localhost at port 8076. This allows any program, including the target’s web browser, to send requests to this port and interfere with Atlas VPN operation. The demonstrated malicious script forces the target’s browser to send a POST request to the port that stops the connection, followed by a second request that retrieves the user’s real IP address.
Compromising a user’s IP address is a critical flaw for a VPN, given its fundamental purpose is to conceal this information. By doing so, the user’s location and identity are exposed, especially since IP addresses can be traced back to individuals through their internet service providers.
The vulnerability has been verified by other security researchers who explained that the security problem arises from “simple requests” being exempted from CORS (cross-origin resource sharing) checks on the browser to help maintain backward compatibility. Because the exploit proof of concept creates a request for the Atlas VPN daemon that mimics a form submission, it’s seen as a “simple request,” hence the browser’s security is bypassed, and the request is accepted and processed as normal.
Chris Partridge
Regarding why the Reddit user chose to publicly reveal the vulnerability rather than discreetly inform Atlas VPN, the individual claims they tried reaching out to the company without success. Moreover, their trust in Atlas VPN is shaky, as they expressed skepticism, stating, “It’s hard to believe this is a bug rather than a backdoor.”
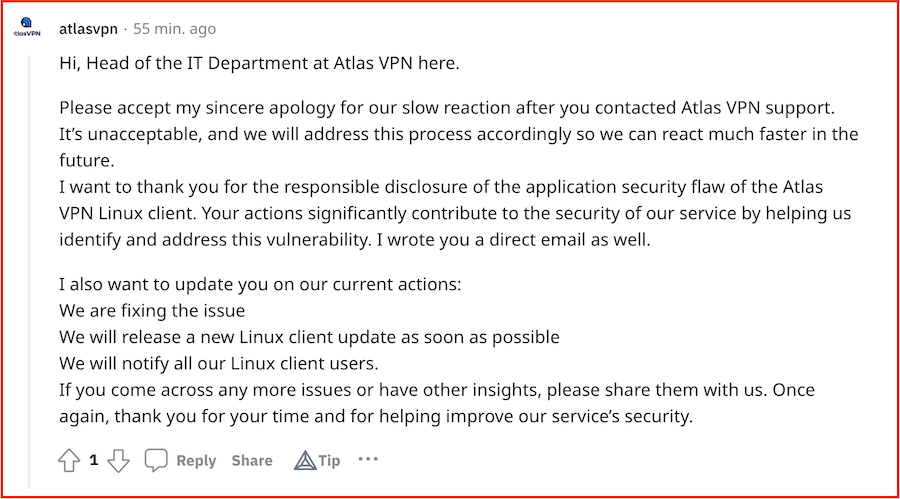
Atlas VPN’s Head of IT jumped on the Reddit thread to confirm the vulnerability and also explain what they’re doing about it.
RestorePrivacy has contacted Atlas VPN to request a comment on the disclosed exploit code and whether the VPN service provider plans a fixing update for its Linux clients soon, and a spokesperson has sent the following statement:
We’re aware of the security vulnerability that affects our Linux client. We take security and user privacy very seriously. Therefore, we’re actively working on fixing it as soon as possible. Once resolved, our users will receive a prompt to update their Linux app to the latest version.
The vulnerability affects Atlas VPN Linux client version 1.0.3. As the researcher stated, due to the vulnerability, the application and, hence, encrypted traffic between a user and the VPN gateway can be disconnected by a malicious actor. This could lead to the user’s IP address disclosure.
We greatly appreciate the cybersecurity researchers’ vital role in identifying and addressing security flaws in systems, which helps safeguard against potential cyberattacks, and we thank them for bringing this vulnerability to our attention. We will implement more security checks in the development process to avoid such vulnerabilities in the future. Should anyone come across any other potential threats related to our service, please contact us via security@atlasvpn.com.
– Atlas VPN statement to RestorePrivacy
Update: Atlas VPN releases latest patched version for Linux
Atlas VPN provided ResotrePrivacy with the following update:
As of September 18th, 2023, the vulnerability is no longer present on the Linux app since its latest version. Following this resolution, we informed our users to update their applications to the fixed 1.1 version. Moreover, the Linux application is now available for download again on our website. We are actively refining our internal communication processes and establishing a more structured vulnerability reporting mechanism. We are committed to ensuring that such oversights do not recur.
– Atlas VPN statement to RestorePrivacy

 Used Items Market Freecycle Suffers Data Breach Impacting 7 Million
Used Items Market Freecycle Suffers Data Breach Impacting 7 Million
Vulns are always going to be there and zero days are going to exist as long as computers exist. Their slow response is an obvious negative, but them acting on it now is a good thing.