
Phishing actors are now following a new attack approach, sending emails with HTML attachments that employ the ‘browser-in-the-browser’ technique.
A sample of such an email was captured by Jan Kopriva, who published the relevant write-up on the SANS Internet Storm Center site to raise awareness about the tricky threat.
Browser-in-the-browser is a technique that displays a simulated window inside the HTML page to trick a website visitor into thinking it’s a login pop-up. Because the URL bar of the fake window is rendered on the site, it can assume any legitimate domain name, making the victim believe they are about to enter their account credentials on the real platform.
This technique has been extensively employed in malicious websites that perform phishing. For example, this fairly recent report from Group-IB reveals how phishing actors use browser-in-the-browser to steal Steam accounts.
However, this is the first time that the technique appears directly in emails, which can make it even more deceptive and hard to distinguish.
As Kopriva explains in the report, the malicious email supposedly contains a proposal, urging the recipient to open the HTML attachment to read it.
Once opened, the victim will get options to log in with popular services like Gmail, Office 365, Outlook, Yahoo, AOL. There’s also a passepartout option under “Other.”
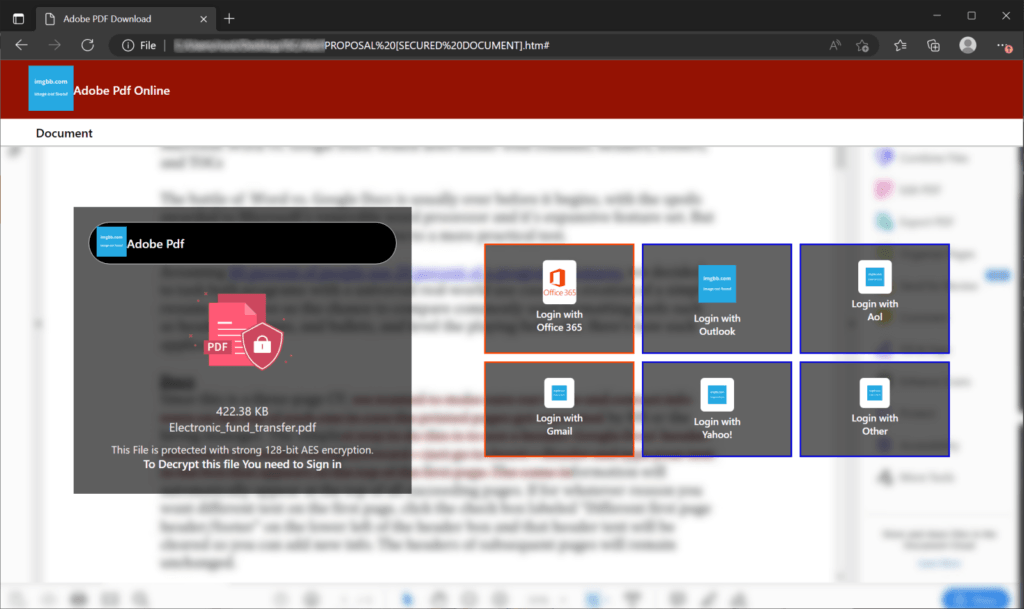
isc.sans.edu
Clicking on any these icons will generate the corresponding fake browser-in-the-browser pop-ups with valid URLs while also matching the appearance of the victim’s window bar theme.
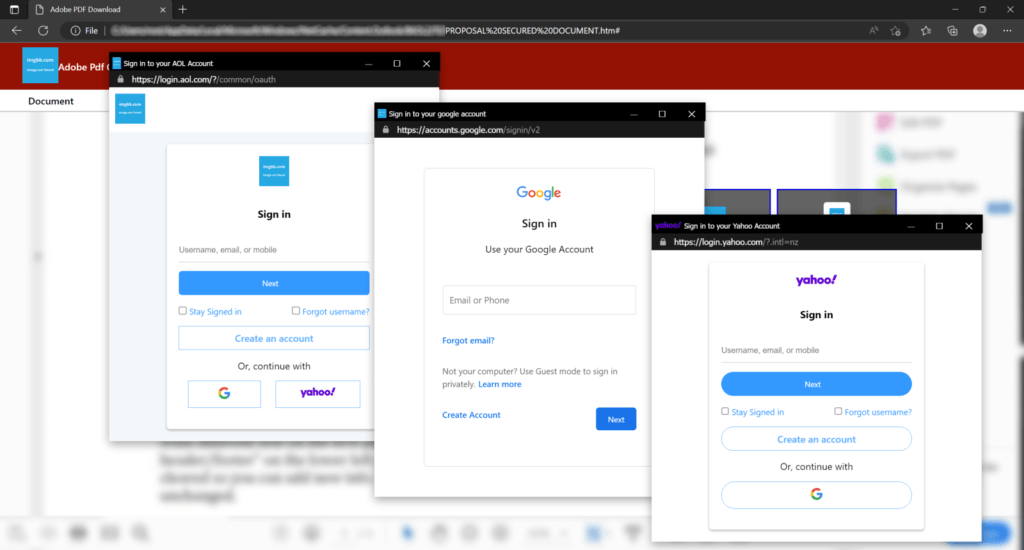
isc.sans.edu
The Office 365 and Outlook pop-ups even simulated the mouse hover color change that is to be expected on Windows, which is yet one more element that adds authenticity and increases the likelihood of victims entering their account credentials on the boxes.
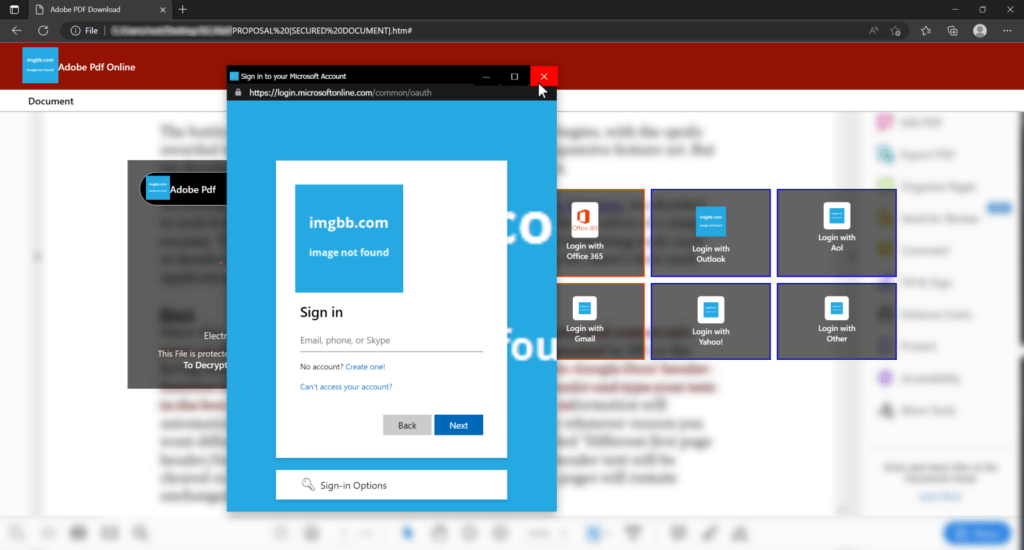
isc.sans.edu
Although this phishing attack is not yet widespread, threat actors may adopt it at more significant rates soon, use different themes depending on the accounts they’re after, and incorporate more sophisticated window rendering code for an even more realistic result. Users should be aware of this possibility and treat HTML attachments with suspicion.
Whether on an email or a website, if you suspect a pop-up window is fake, try to resize it or move it outside the frame of the active page. If those actions are impossible, it’s a simulated window that tries to steal your credentials.
Also, note that all new windows should have a corresponding entry on the taskbar and should be retrievable from there when minimized. On Windows 11, where windows of the same app are grouped together under a single icon, individual windows should generate separate previews upon mouse hovering over the taskbar icon.

 Google Rolls out Privacy Sandbox on Limited Android 13 Devices
Google Rolls out Privacy Sandbox on Limited Android 13 Devices
helpful and informative!!!
Great article Heinrich!