
A system log file on iOS devices like the Apple iPhone can help users determine if their devices have been infected by spyware like the Pegasus or other strains.
In a report published today, Kaspersky explains that the particular log file, named ‘Shutdown.log,’ stores entries for every reboot, documenting any processes that prevent normal rebooting. Malware running on the device, like sophisticated spyware that needs to activate its modules during the boot process, leaves traces on that log file, giving it a forensic value.
In practice, this means that examining a log file can oftentimes reveal key information about the infection status of a device, which would otherwise be attainable only by performing analysis on encrypted iOS backups, network traffic, and other time-consuming procedures that also require certain level of expertise.
Detection scripts
Kaspersky created and publicly shared three Python scripts to help automate the parsing and analysis of Shutdown.log, aiding in the detection of anomalies. The three scripts are summarized below:
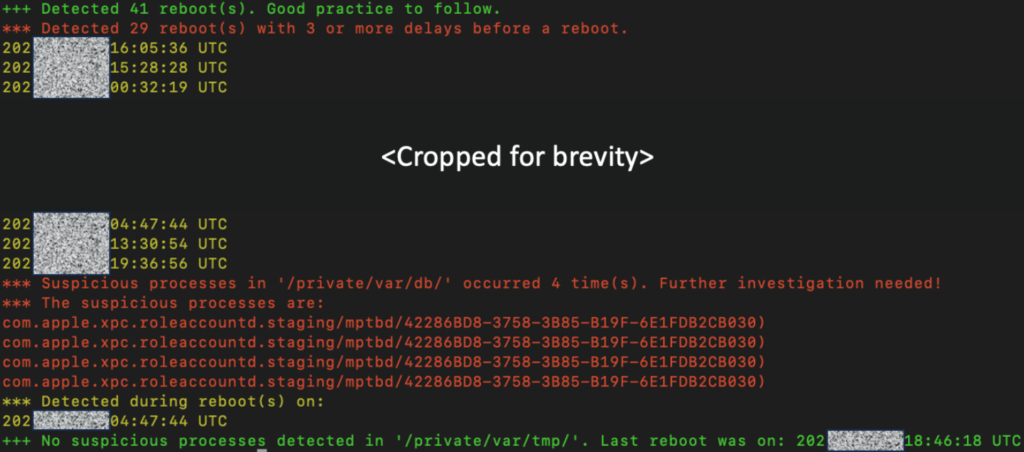
- iShutdown_detect: This script detects anomalies in the Shutdown.log file. It’s designed to identify unusual entries that might indicate malware infections.
- iShutdown_parse: This script extracts and parses the Shutdown.log file from a sysdiag archive.
- iShutdown_stats: This script provides statistics on the reboots of an iOS device based on the Shutdown.log file.
As it becomes evident from the above, users interested in running the Python scripts have to first generate a sysdiag dump from their device and extract the relevant log file. To do this, go to the Settings app on your iOS device, navigate to ‘Privacy & Security,’ find ‘Analytics & Improvements,’ and look for a ‘sysdiagnose’ option.
The generation of the sysdiag dump may take a few minutes as the device will collect various system logs and diagnostic information and package them into a file. Eventually, users need to transfer the dump from their iPhone device to a computer for analysis.
On the computer, use an extracting tool that supports ‘.tar. gz’ files to unpack the archive, locate the Shutdown.log file (usually under ‘\system_logs.logarchive\Extra’), and then use it as input for the Python scripts as per the instructions Kaspersky provides in the GitHub repository.
Kaspersky
While helpful, the scripts could be daunting for people without technical proficiency. Also, correctly interpreting the output of the scripts may require some understanding of iOS system behavior and malware indicators. Still, this is a fairly safe process for those willing to dive deeper and learn something about their device.
One thing to keep in mind, though, is that sysdiag dumps can contain sensitive information, so it is recommended to handle and store the files securely.
The effectiveness of this method hinges on the frequency of reboots by the user. The more frequent the reboots, the higher the chances of detecting malware. However, this method is not a comprehensive solution and works best when combined with other analysis techniques.
Still, Kaspersky suggests that Shutdown.log is an excellent place to start for most people, including regular iPhone users worried about their privacy and security.

 Hackers Claim to Have Stolen Source Code From McDonald’s Git Repo
Hackers Claim to Have Stolen Source Code From McDonald’s Git Repo
The last line in this article made me bust out laughing 😂😂😂
” iPhone users worried about their privacy ” …… 😂😂😂😂
That don’t exist . iPhone users are some of the MOST ignorant people about privacy and security .
And people who are not ignorant choose Android. They must be idiots then. By using Android knowing it’s the worst OS for privacy. 😉